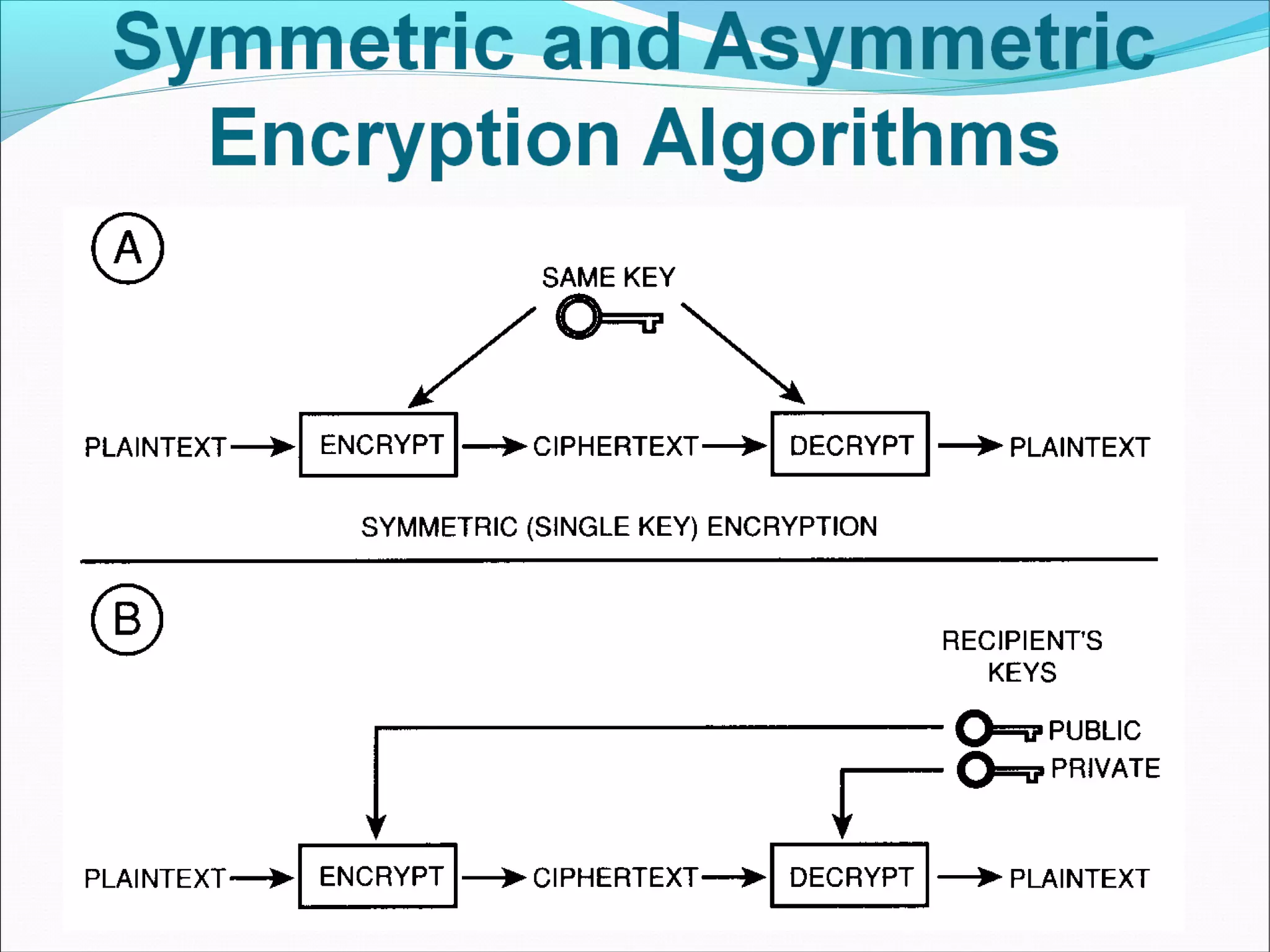
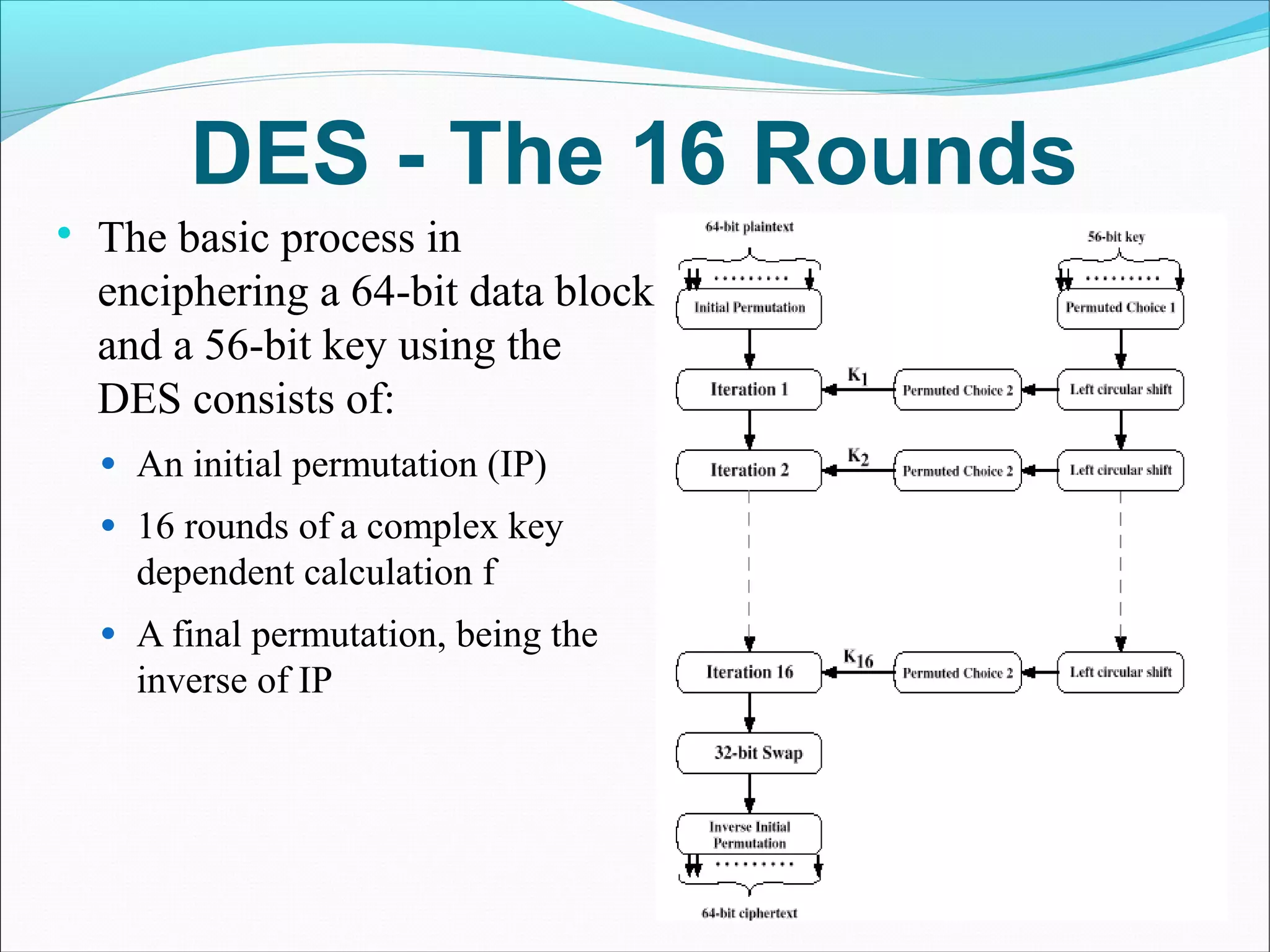
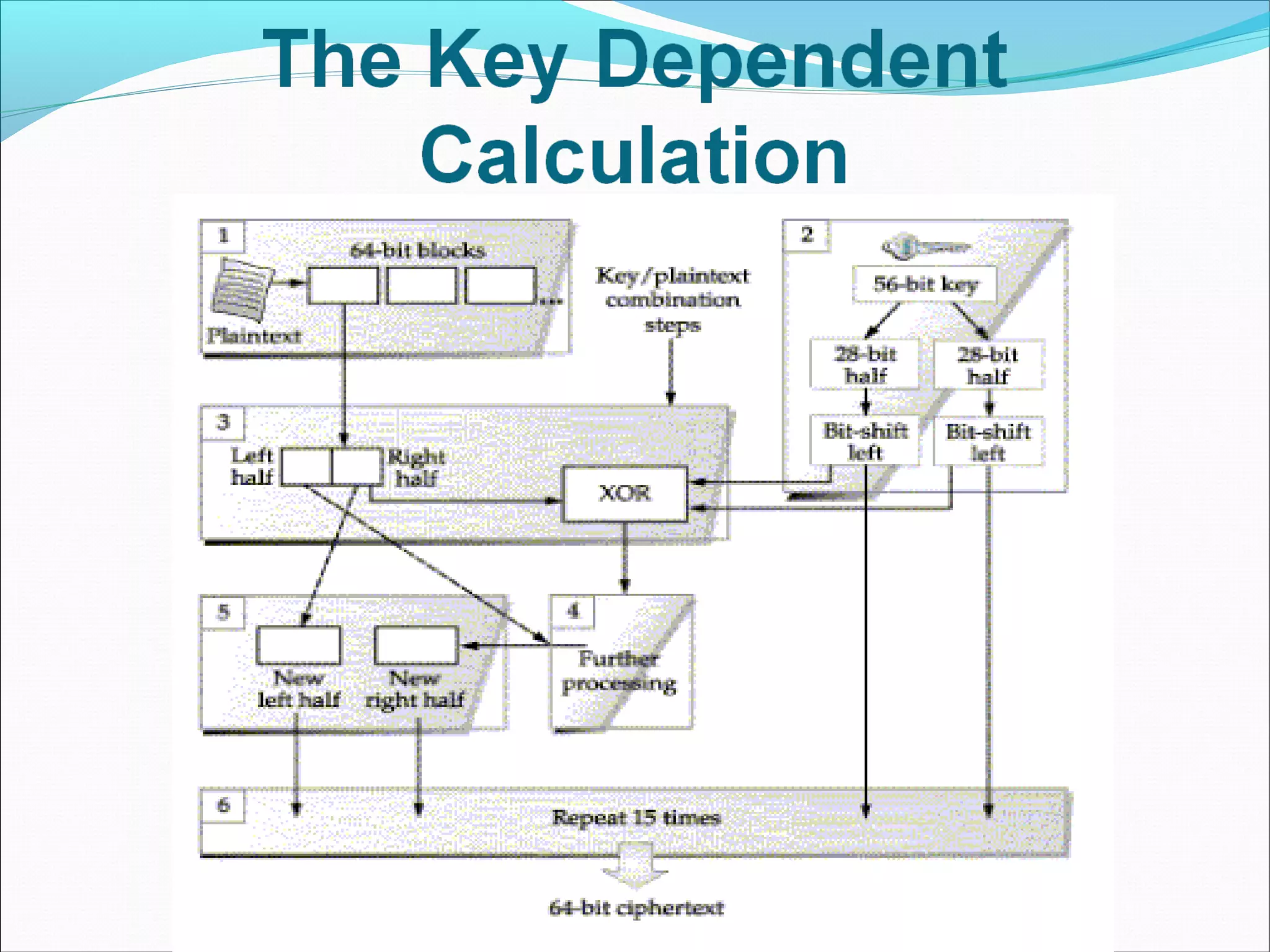
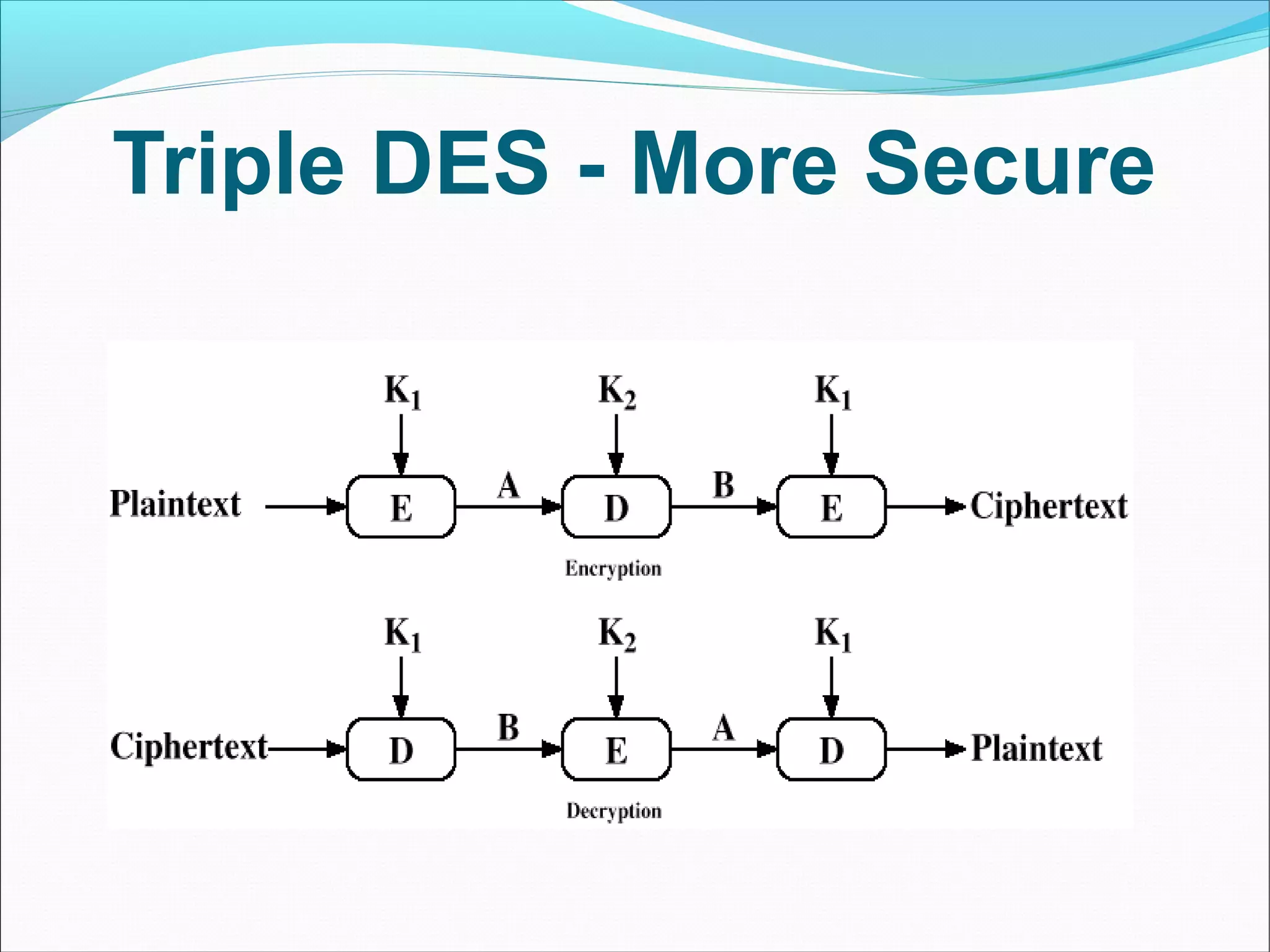
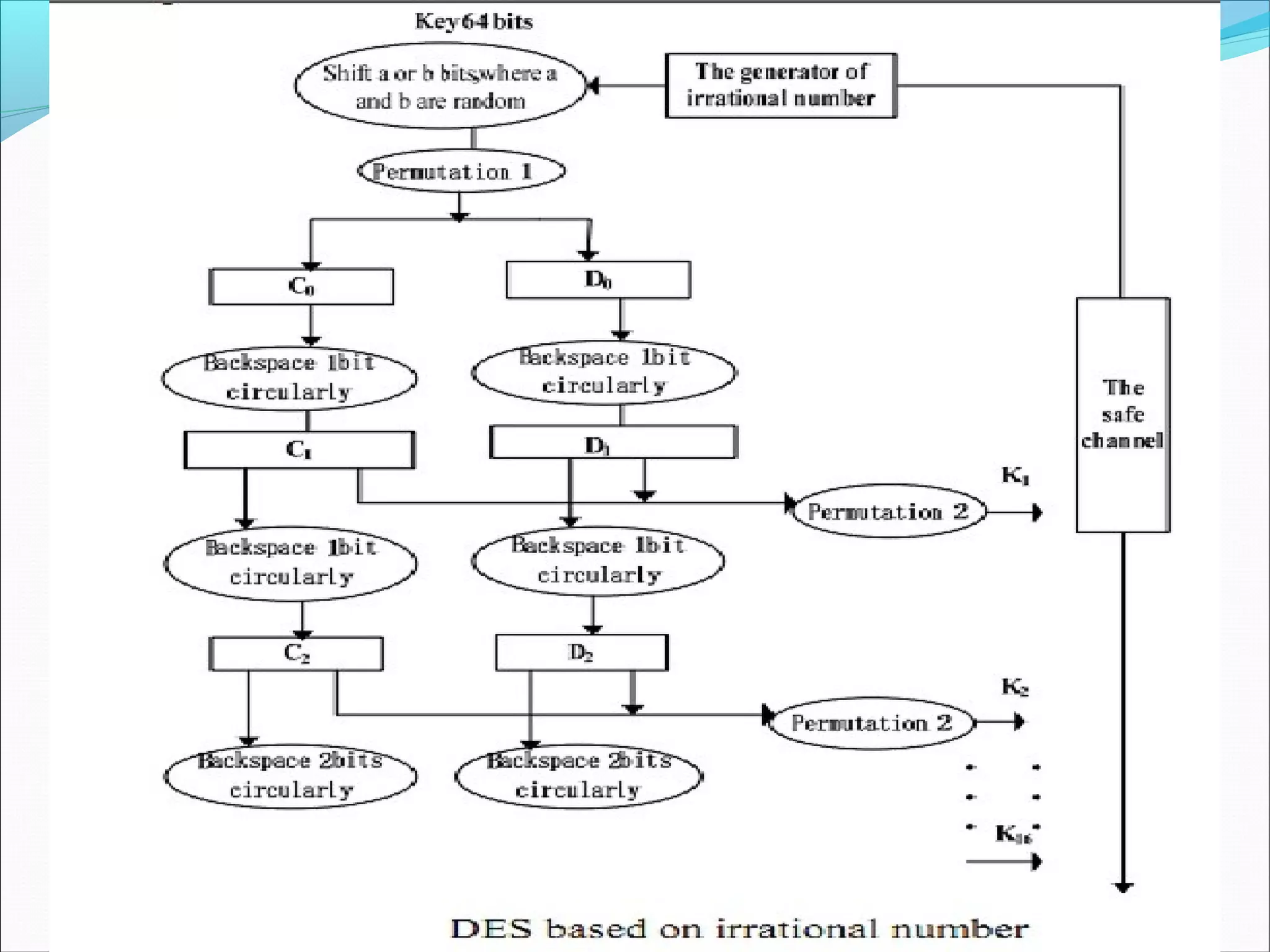
DES was developed as a standard for communications and data protection by an IBM research team in response to a request from the National Bureau of Standards (now called NIST). DES uses the techniques of confusion and diffusion achieved through numerous permutations and the XOR operation. The basic DES process encrypts a 64-bit block using a 56-bit key over 16 complex rounds consisting of permutations and key-dependent calculations. Triple DES was developed as a more secure version of DES.