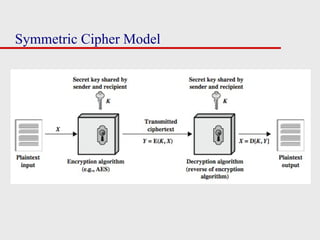
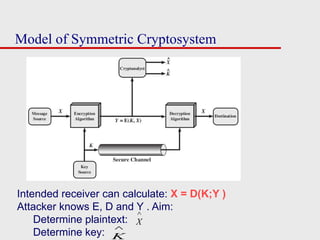
The document covers various cryptographic techniques, focusing on symmetric and asymmetric ciphers, and the principles behind encryption and decryption. It details classical methodologies such as substitution and transposition ciphers, specifically explaining the Caesar and Vigenère ciphers, along with insights on cryptanalysis methods. Additionally, it introduces concepts like rotor machines and steganography, highlighting the security measures and the weaknesses inherent in these systems.