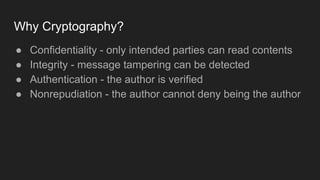
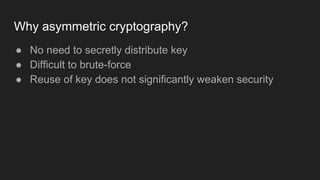
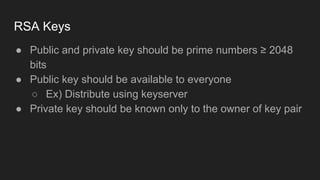
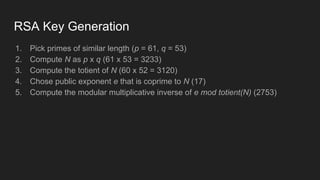
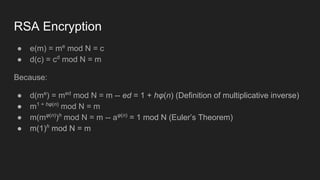
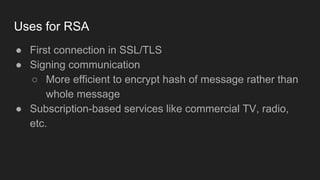
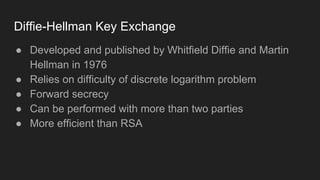
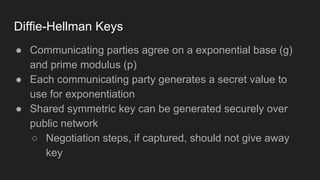
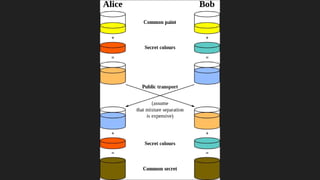
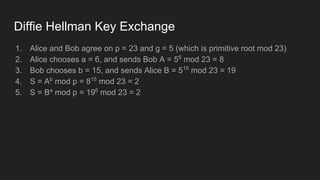
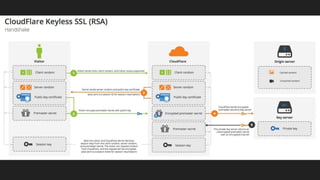
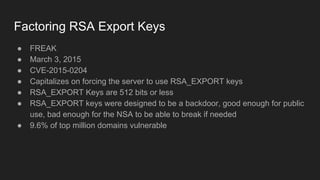
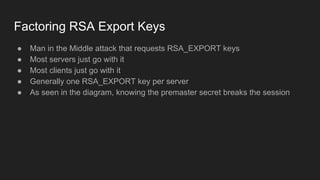
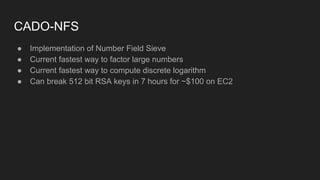
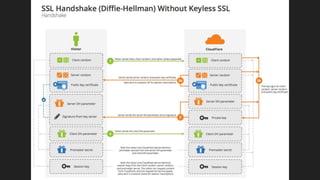
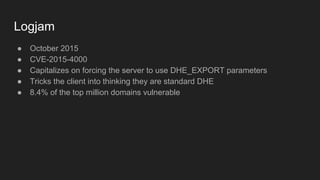
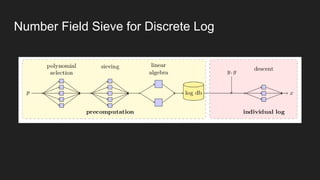
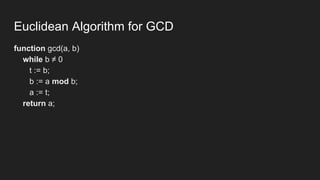
The document provides an overview of asymmetric cryptography, detailing its importance for confidentiality, integrity, authentication, and nonrepudiation. It focuses on RSA and Diffie-Hellman key exchange methods, their key generation processes, uses, and the vulnerabilities associated with public key cryptography. Additionally, it discusses historical milestones in cryptography, notable attacks, and future events related to pentesting and capture-the-flag competitions.