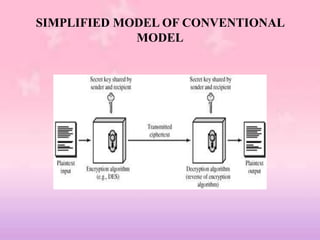
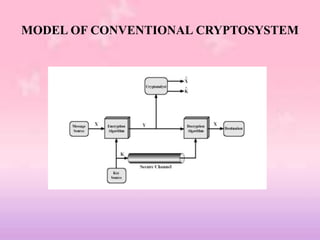
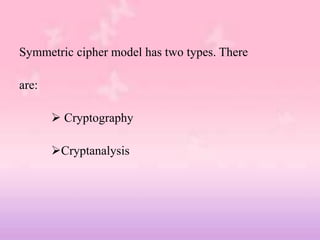
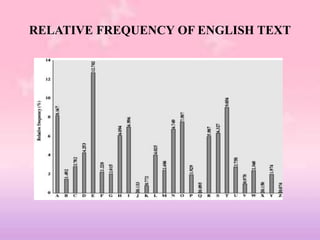
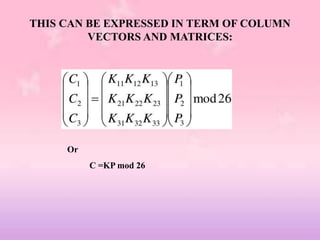
This document provides an overview of classical encryption techniques. It begins with definitions of key terms like plaintext, ciphertext, encryption, and decryption. It then describes the symmetric cipher model and simplifies it. The document outlines areas of cryptography and cryptanalysis. It explains techniques like substitution ciphers, the Caesar cipher, monoalphabetic ciphers, the Playfair cipher, the Hill cipher, polyalphabetic ciphers, and the one-time pad cipher. For each technique, it provides a brief description and encryption algorithm.