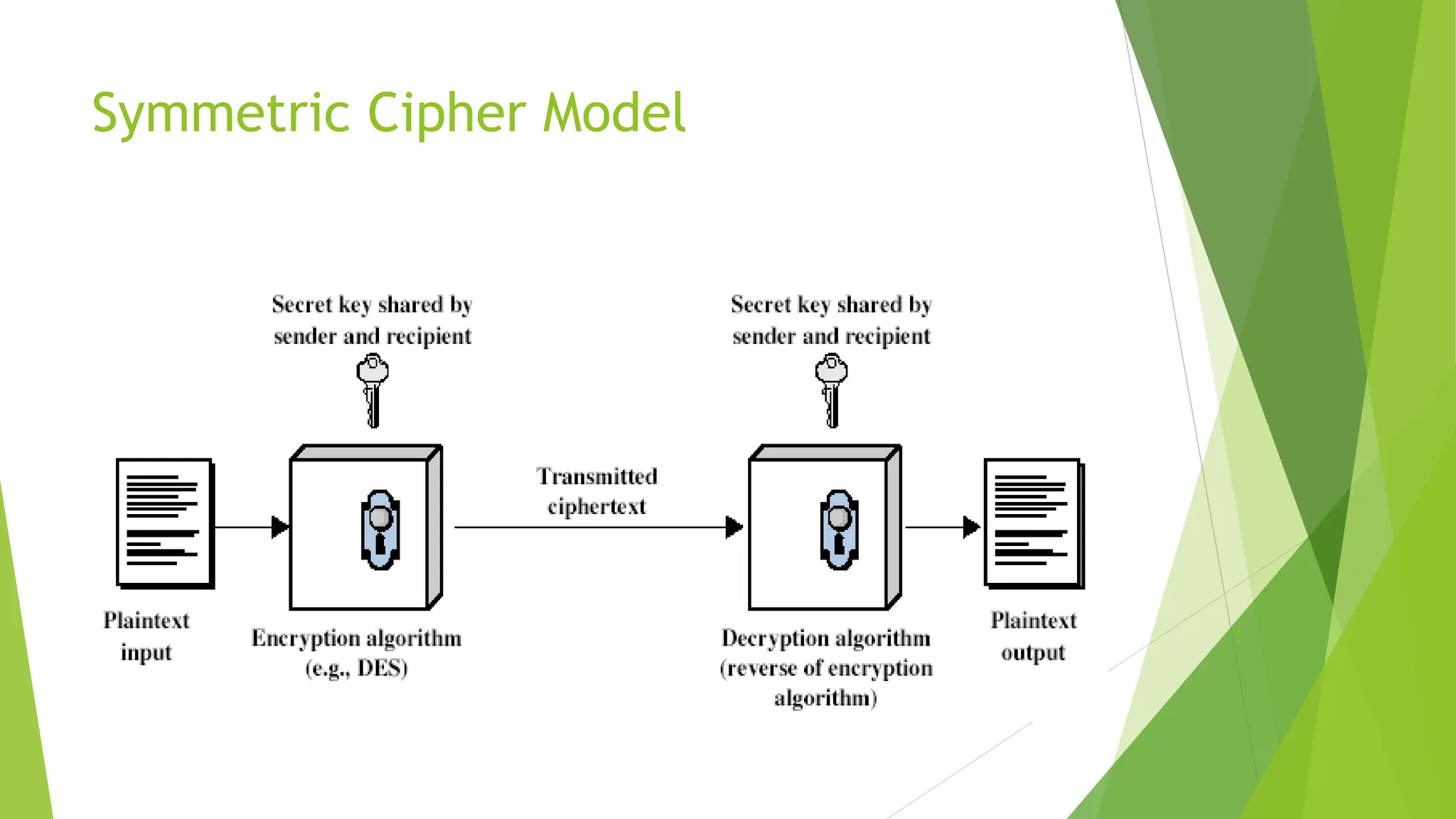
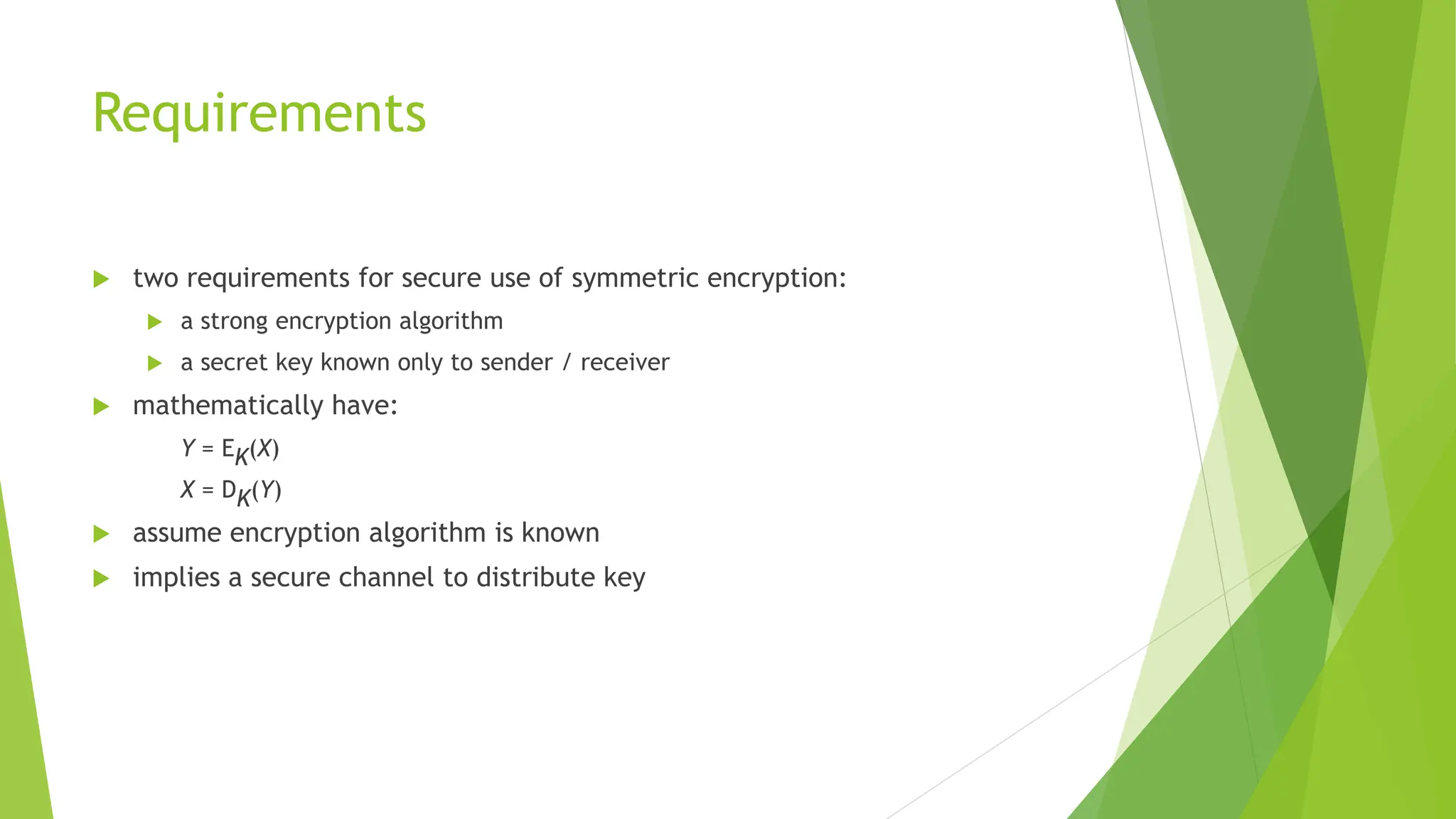
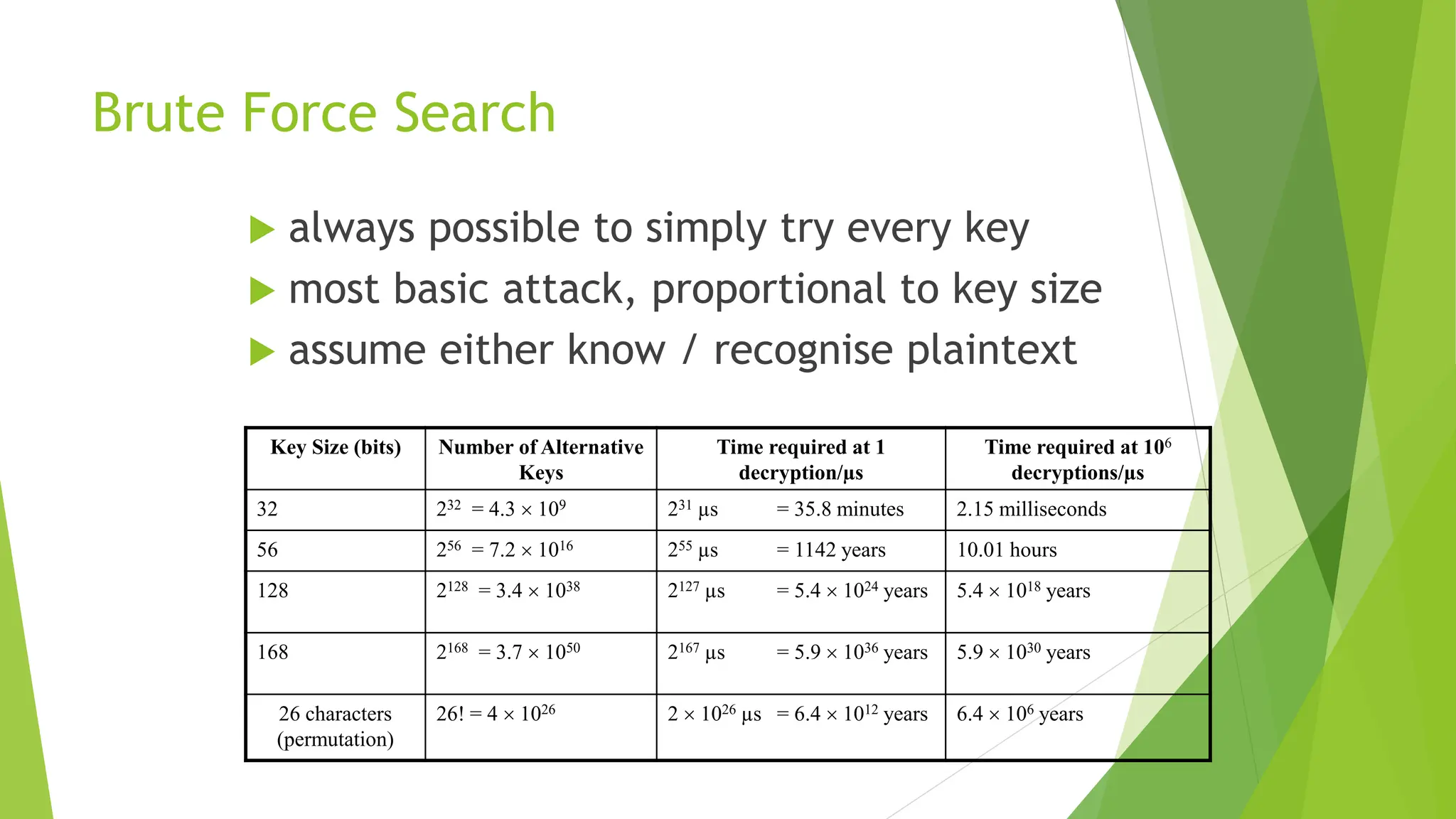
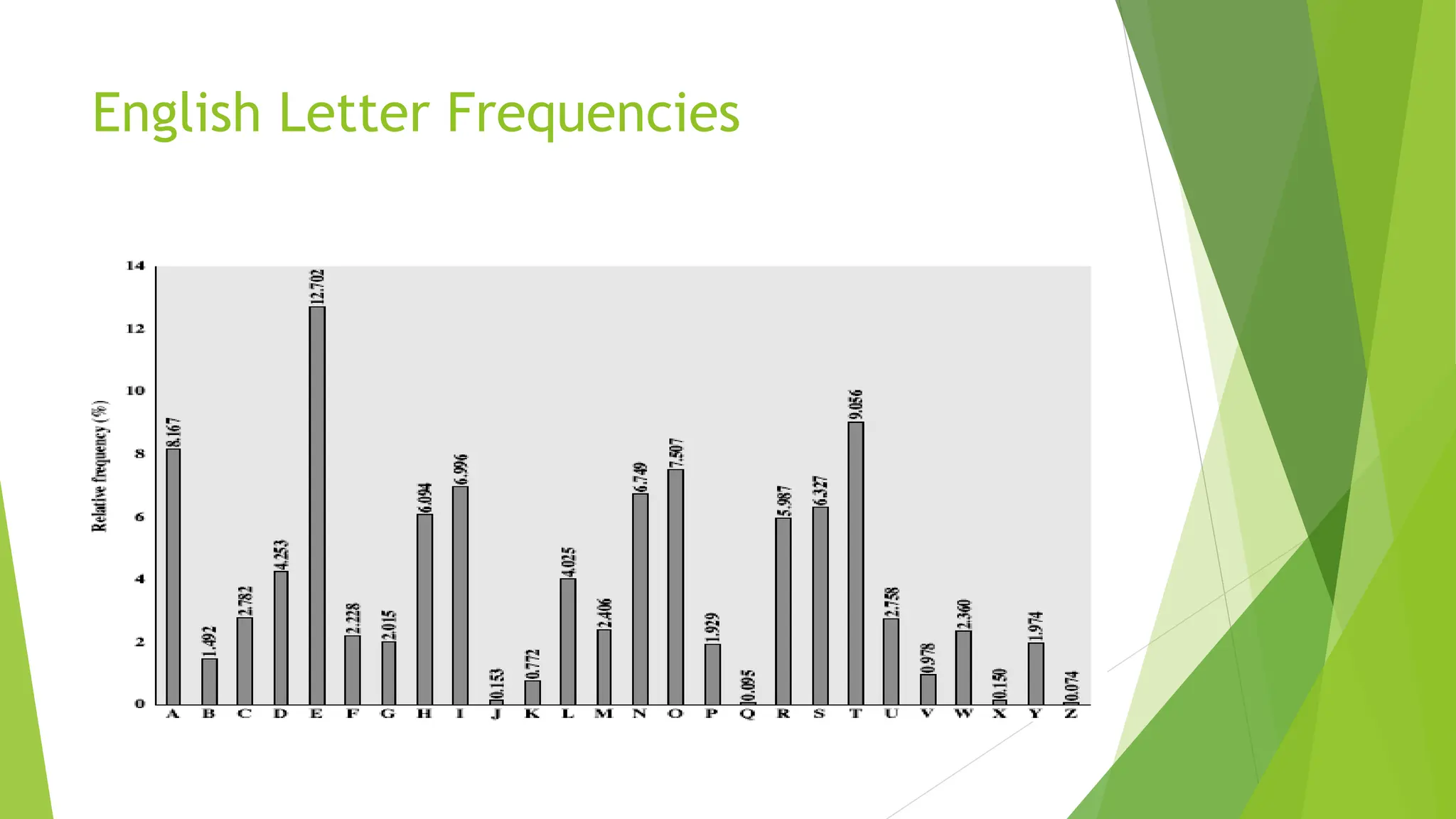
The document discusses classical encryption techniques, focusing on symmetric encryption methods where a shared key is utilized for encoding and decoding messages. It outlines various concepts, including encryption algorithms, types of attacks, and types of ciphers such as substitution and transposition ciphers. Furthermore, it addresses the need for secure key distribution and the challenges associated with cryptanalysis, emphasizing advancements in cryptographic methods over time.