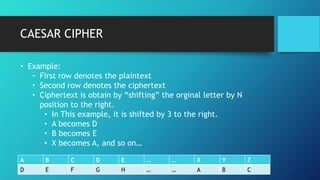
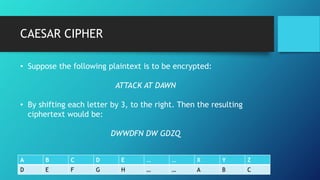
The Caesar cipher is one of the earliest known substitution ciphers. It works by shifting each letter in a plaintext message by a set number of positions (the key) in the alphabet to encrypt it. For example, with a key of 3, A would be replaced by D, B by E, and so on. Decryption simply requires shifting letters in the opposite direction by the same key. While simple, the Caesar cipher has some mathematical properties and was allegedly used by Julius Caesar to communicate with his army. However, it is also easy to break through brute force by trying all 26 possible keys.