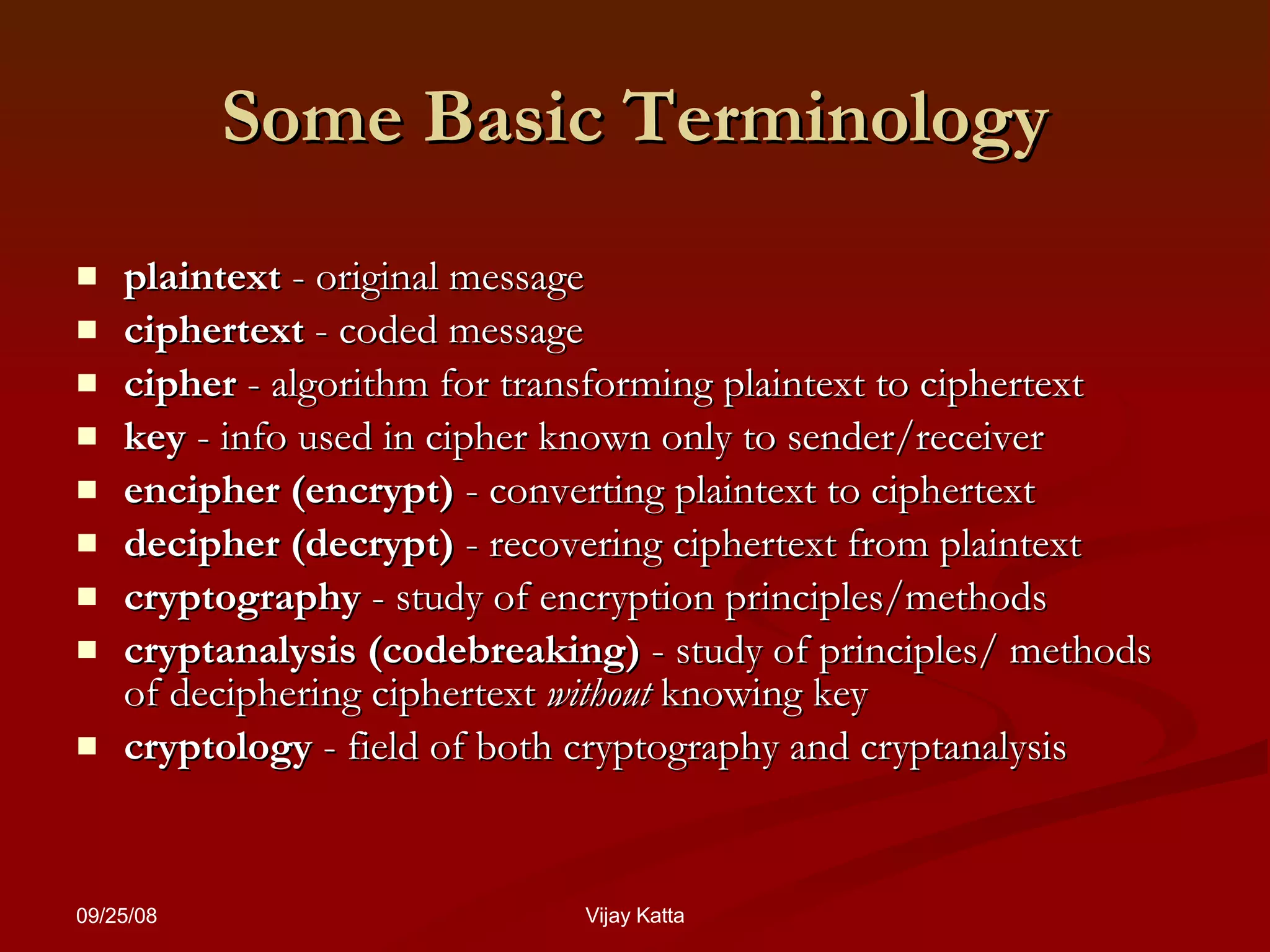
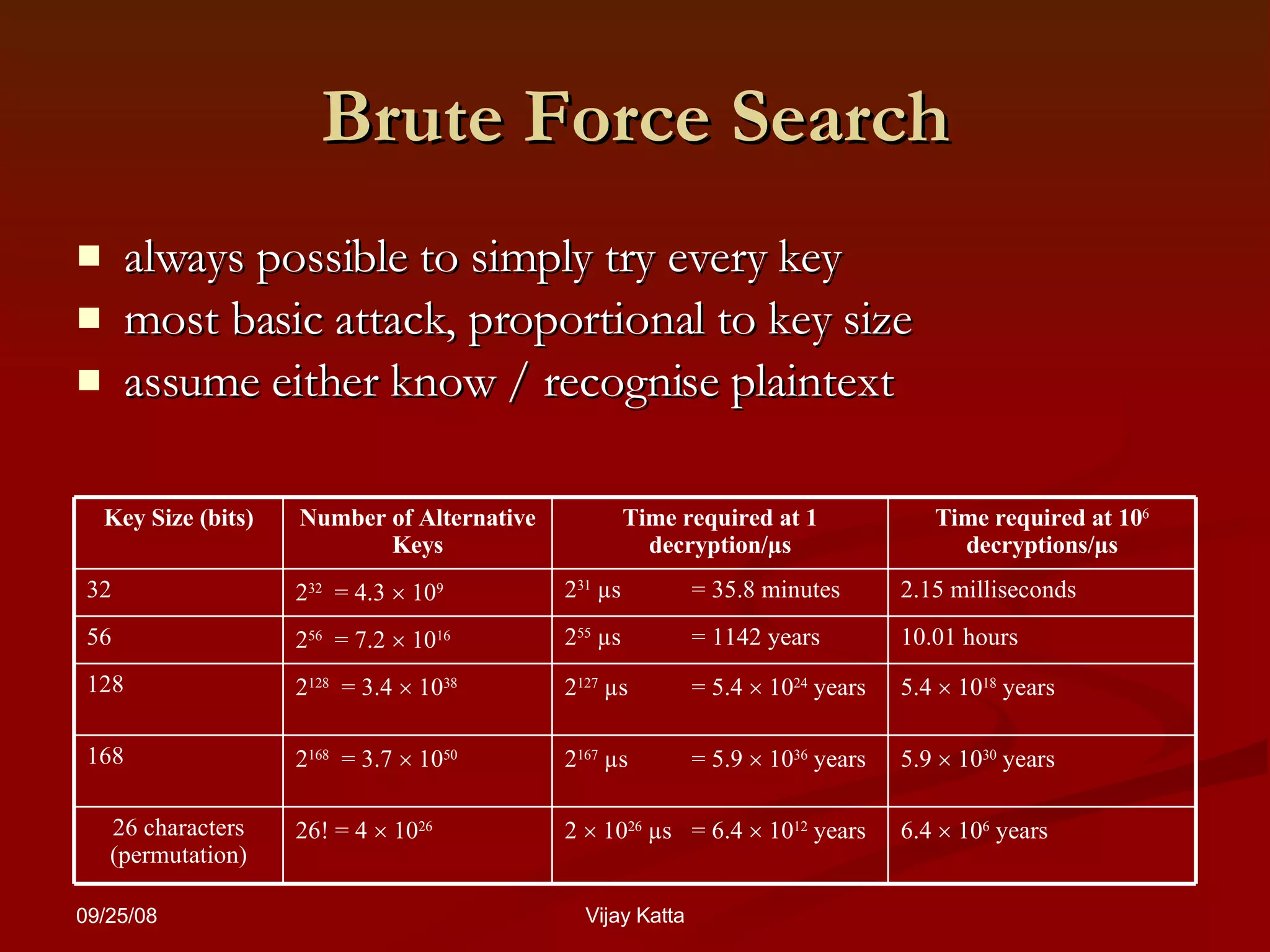
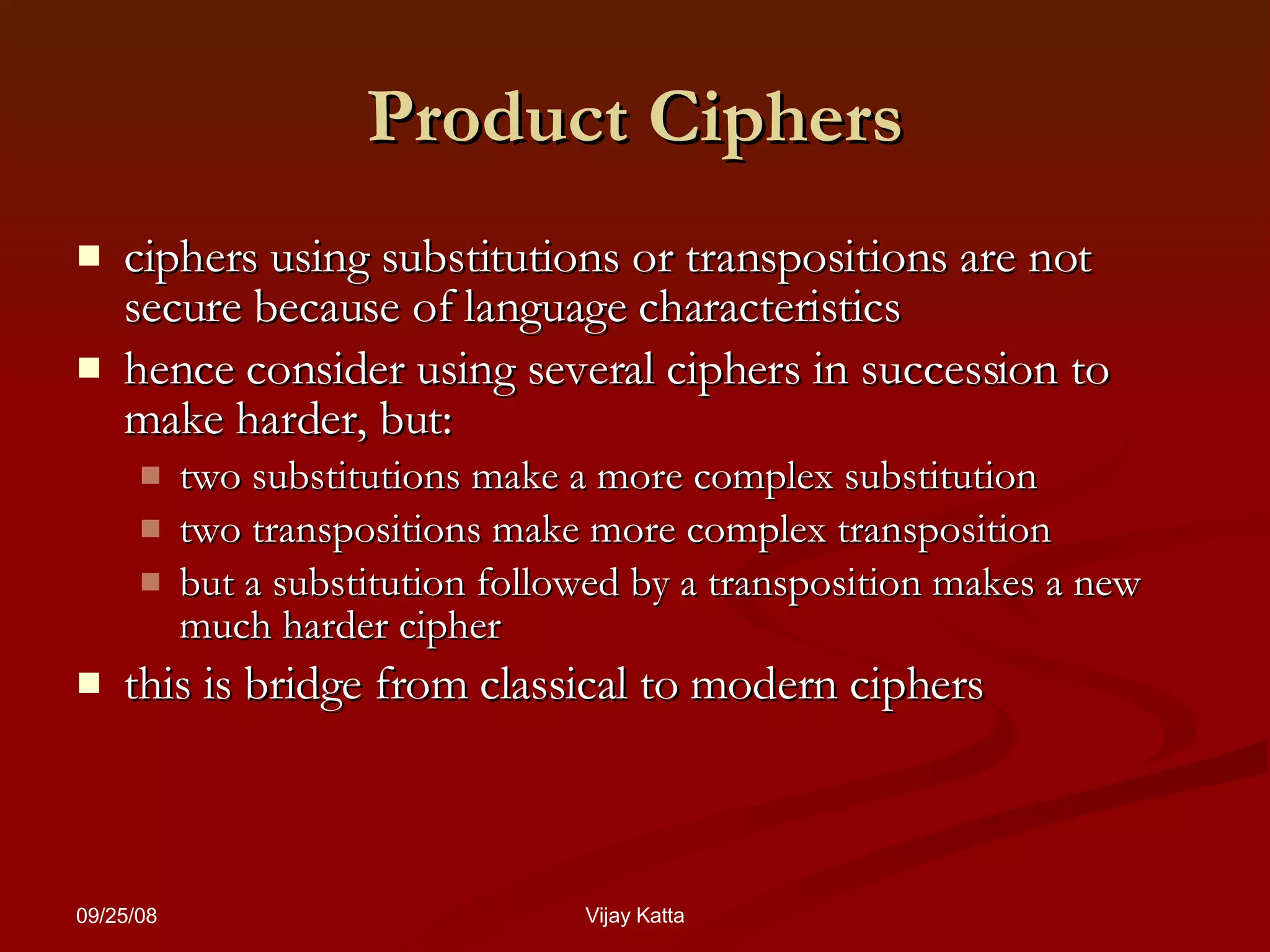
The document summarizes classical encryption techniques, including:
- Symmetric encryption uses a shared key between sender and receiver for encryption/decryption.
- Early techniques included the Caesar cipher (shifting letters), monoalphabetic cipher (mapping each letter to another), and Playfair cipher (encrypting letter pairs).
- The Vigenère cipher improved security by using a keyword to select different Caesar ciphers for successive letters, making it a polyalphabetic cipher.