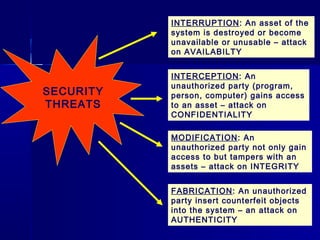
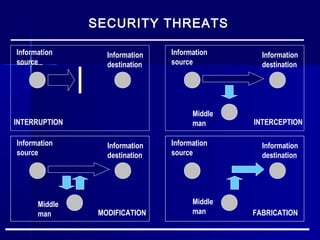
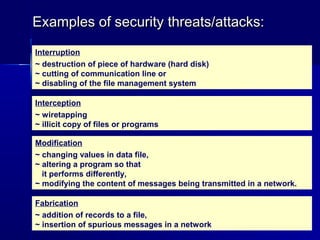
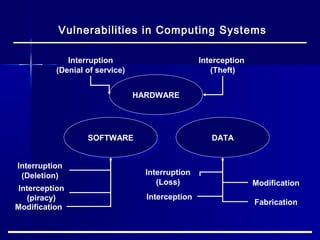
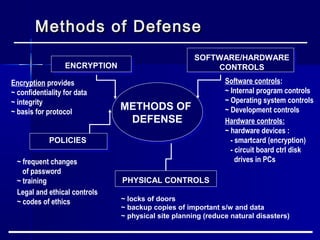
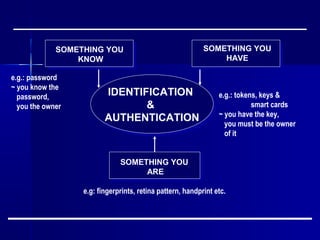
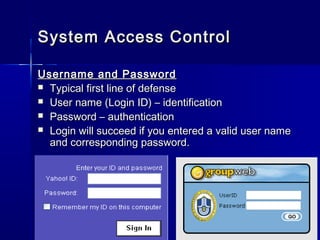
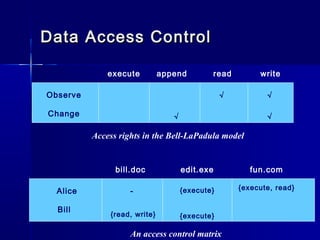
This document discusses basic security concepts, including definitions of security, assets, and the principle of easiest penetration. It describes three classifications of protection: prevention, detection, and reaction. Examples are given for physical and cyber security. The goals of security are defined as integrity, confidentiality, and availability. Common security threats are interruption, interception, modification, and fabrication. Vulnerabilities in computing systems can occur in data, software, hardware, and exposed assets. Methods of defense include encryption, software/hardware controls, policies, and physical controls. System access control and data access control are important methods for making systems secure using identification, authentication, and access authorization.