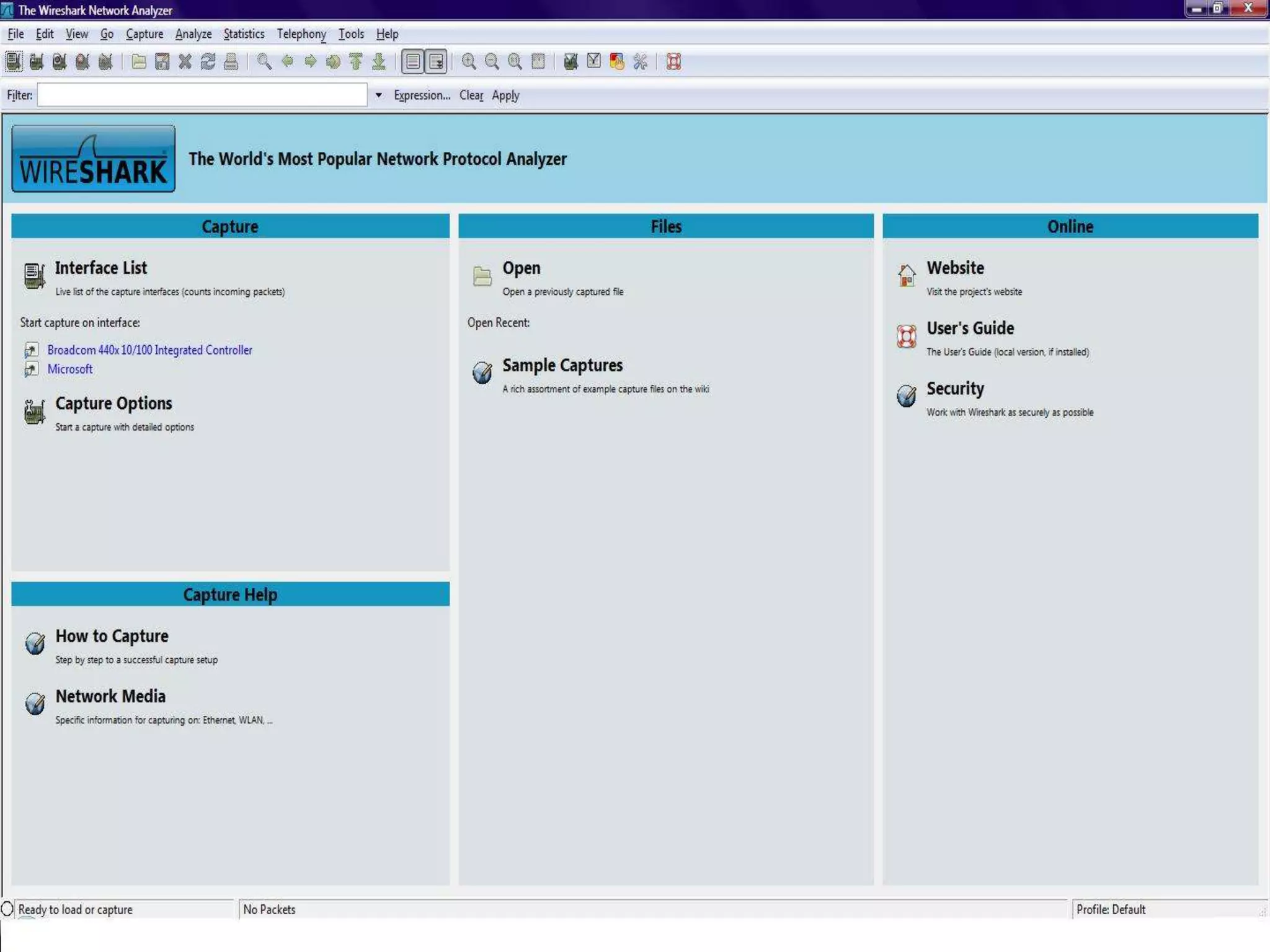
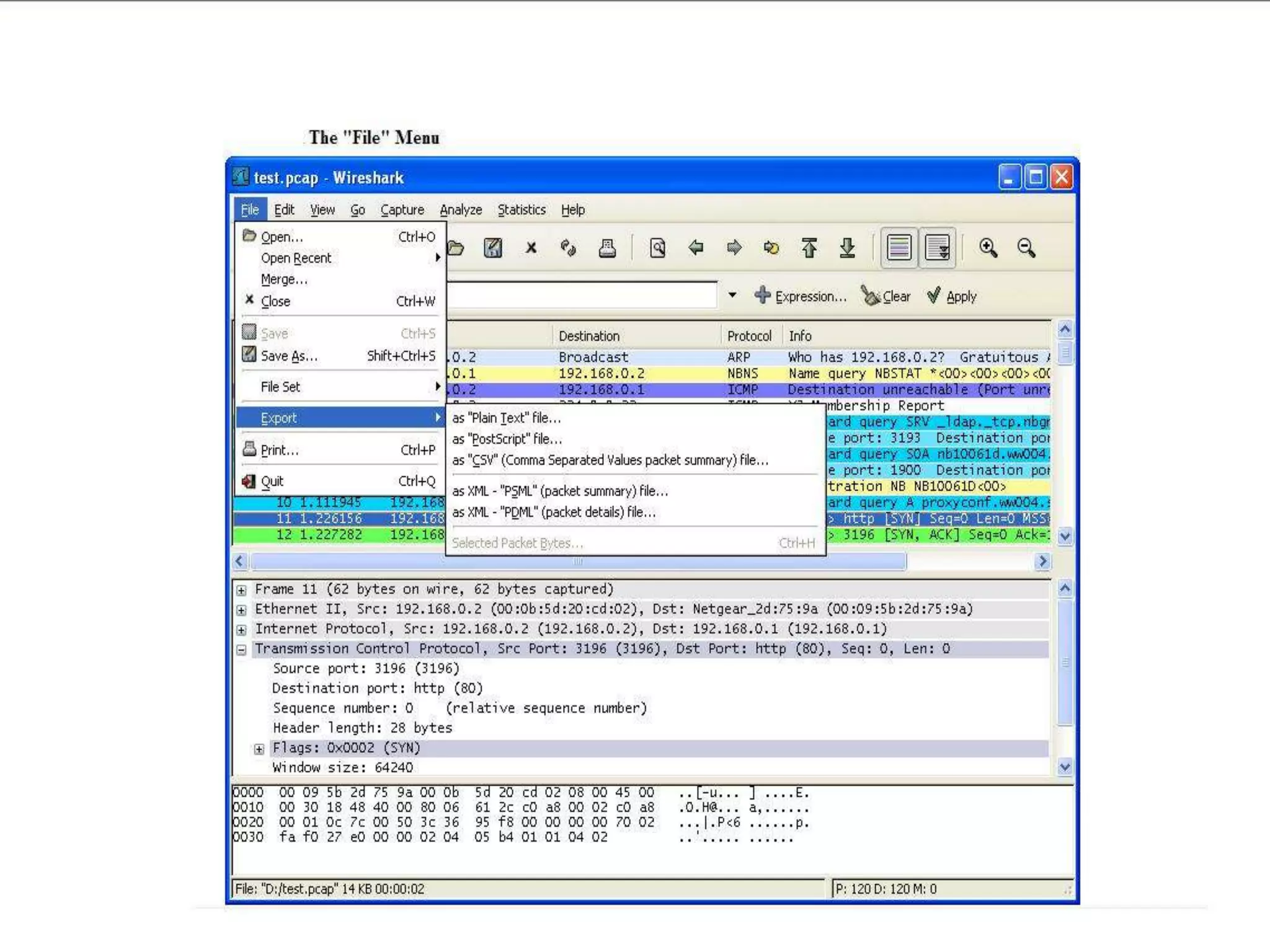
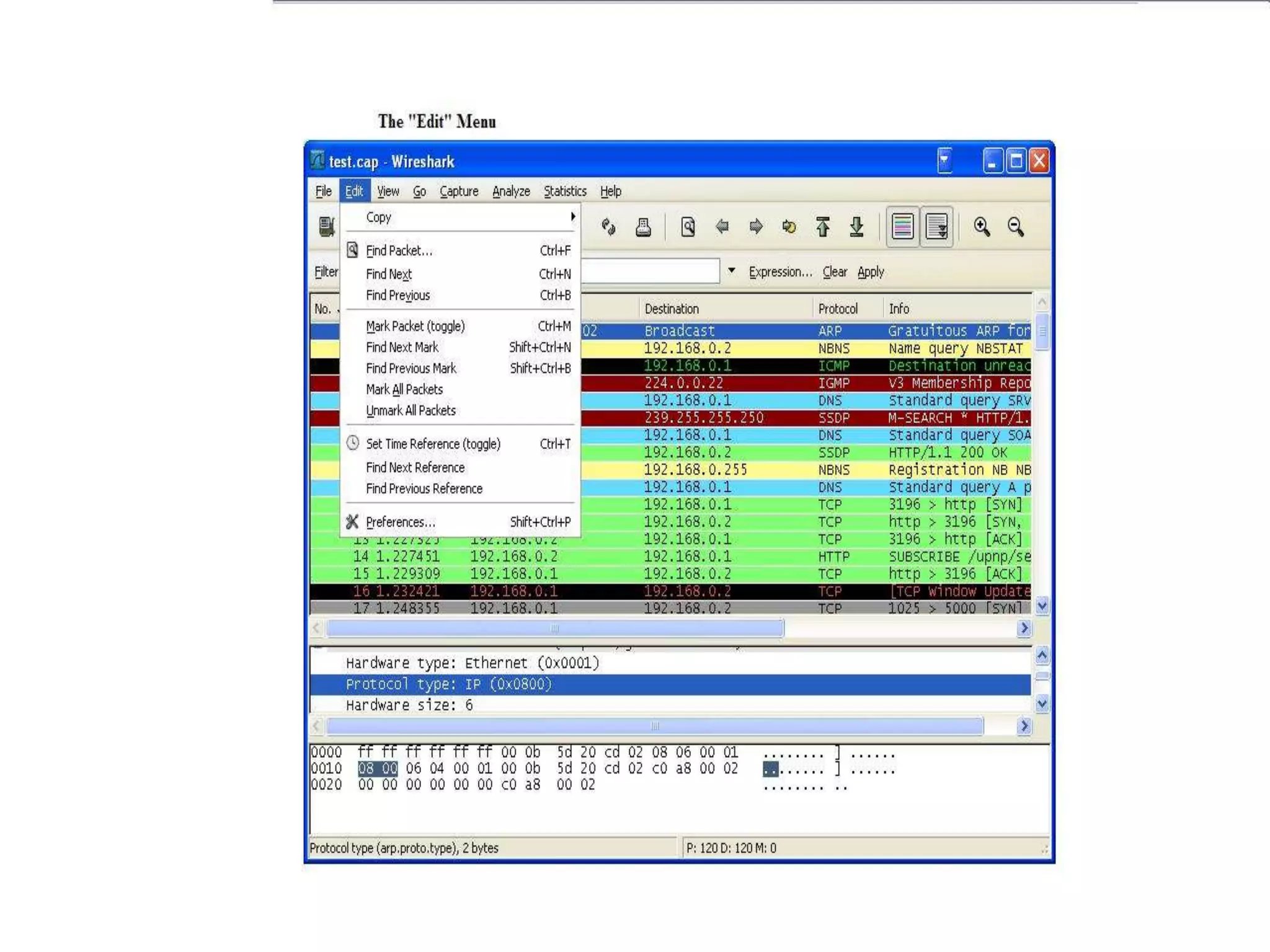
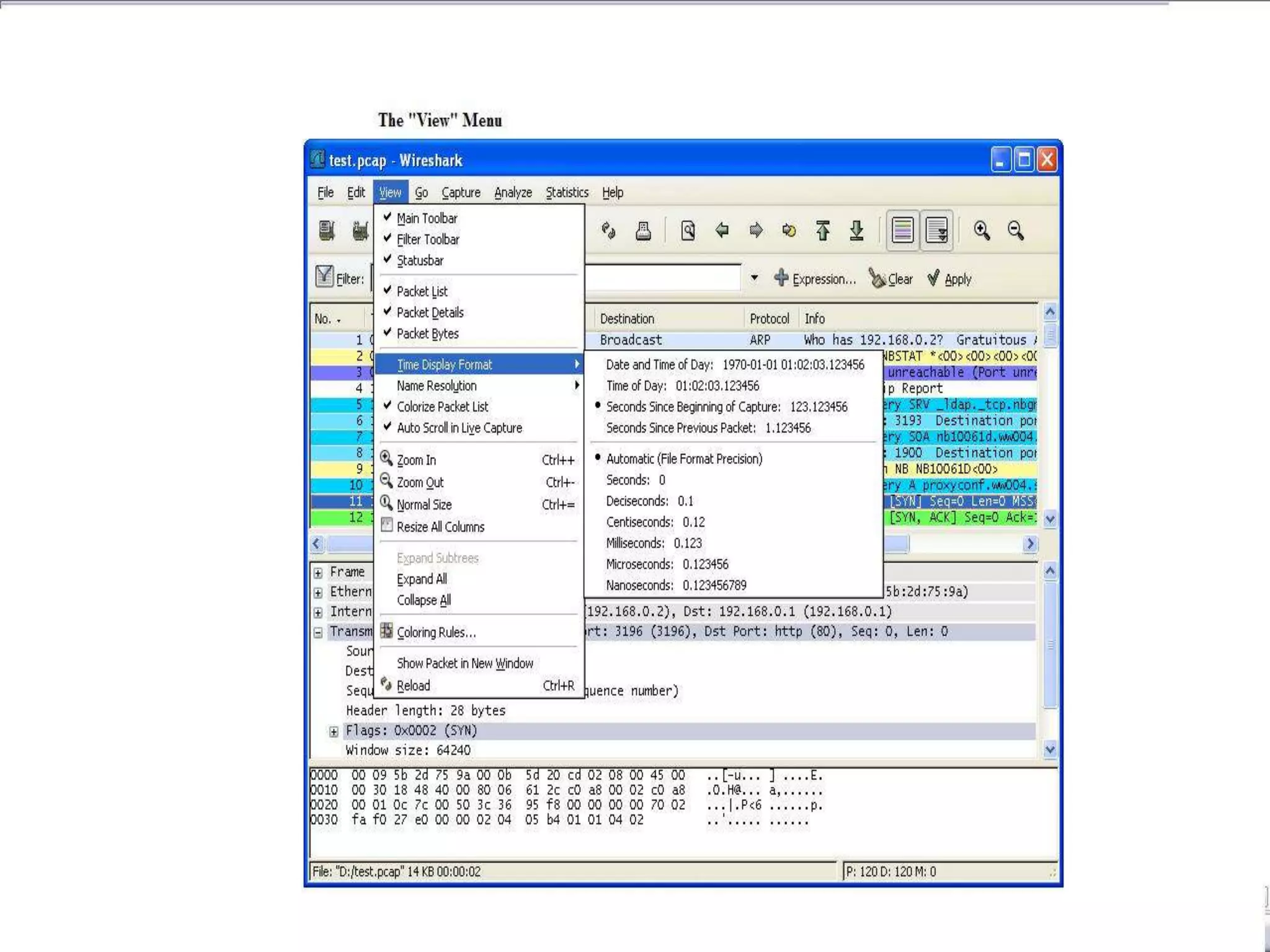
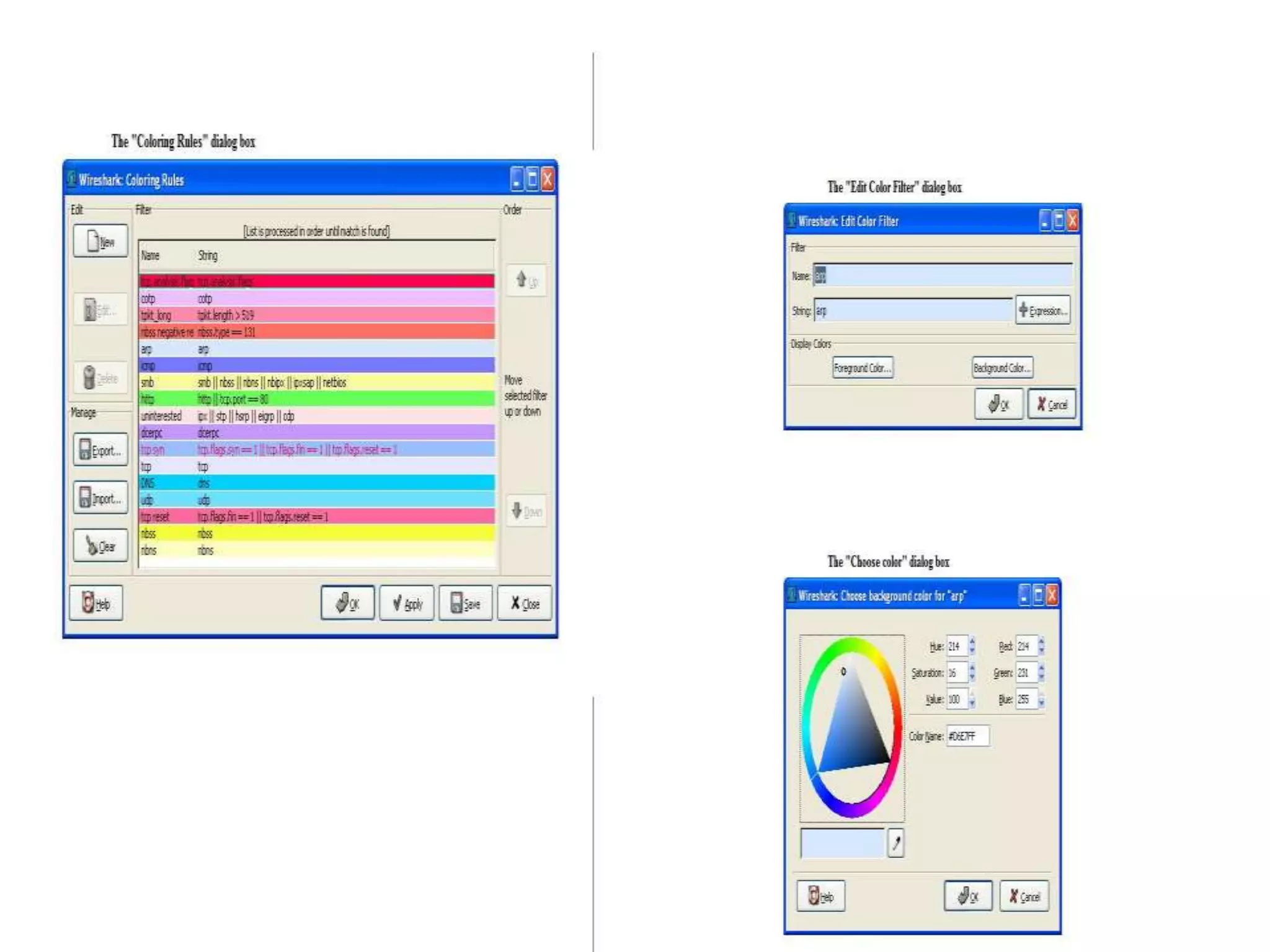
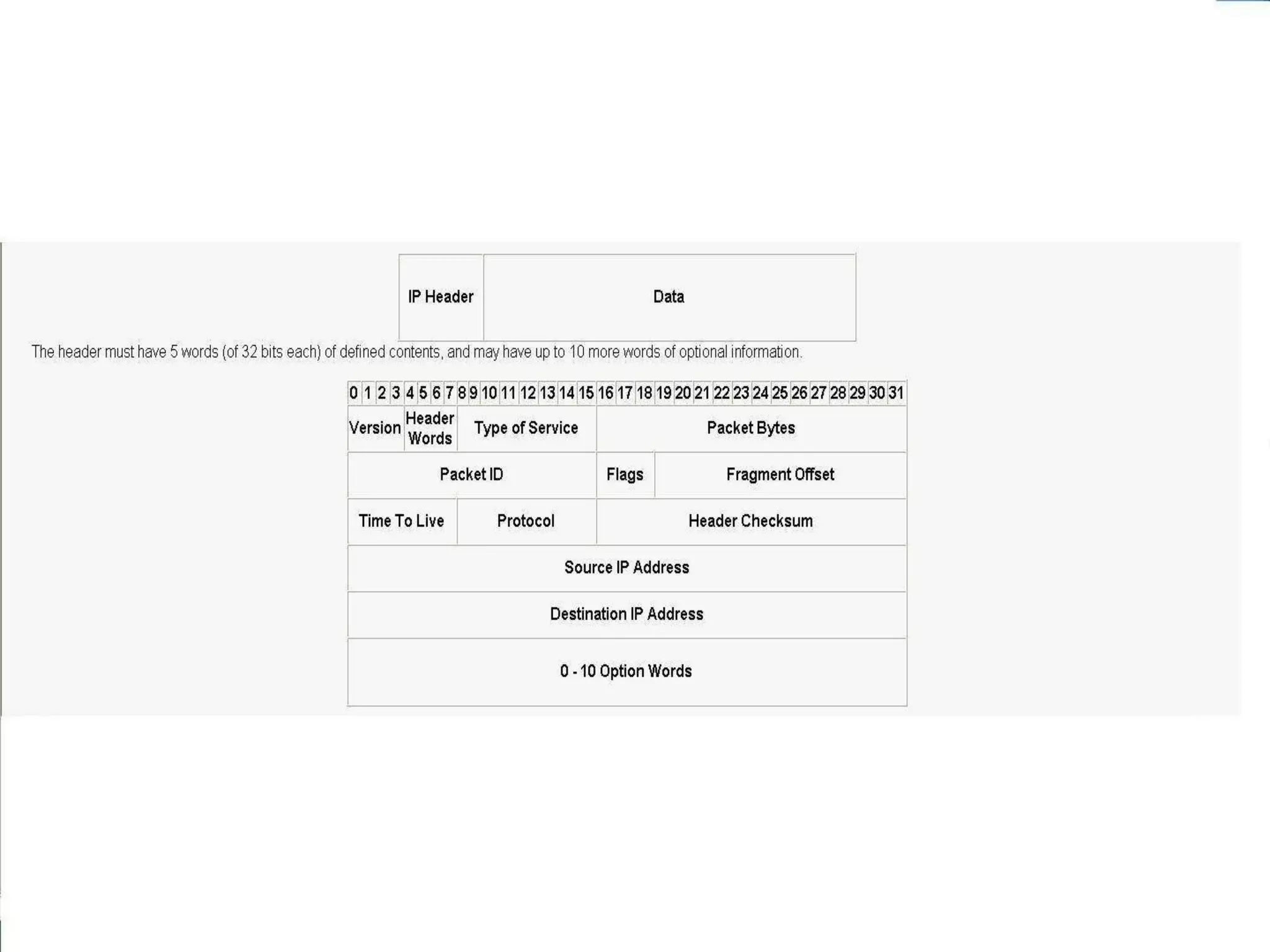
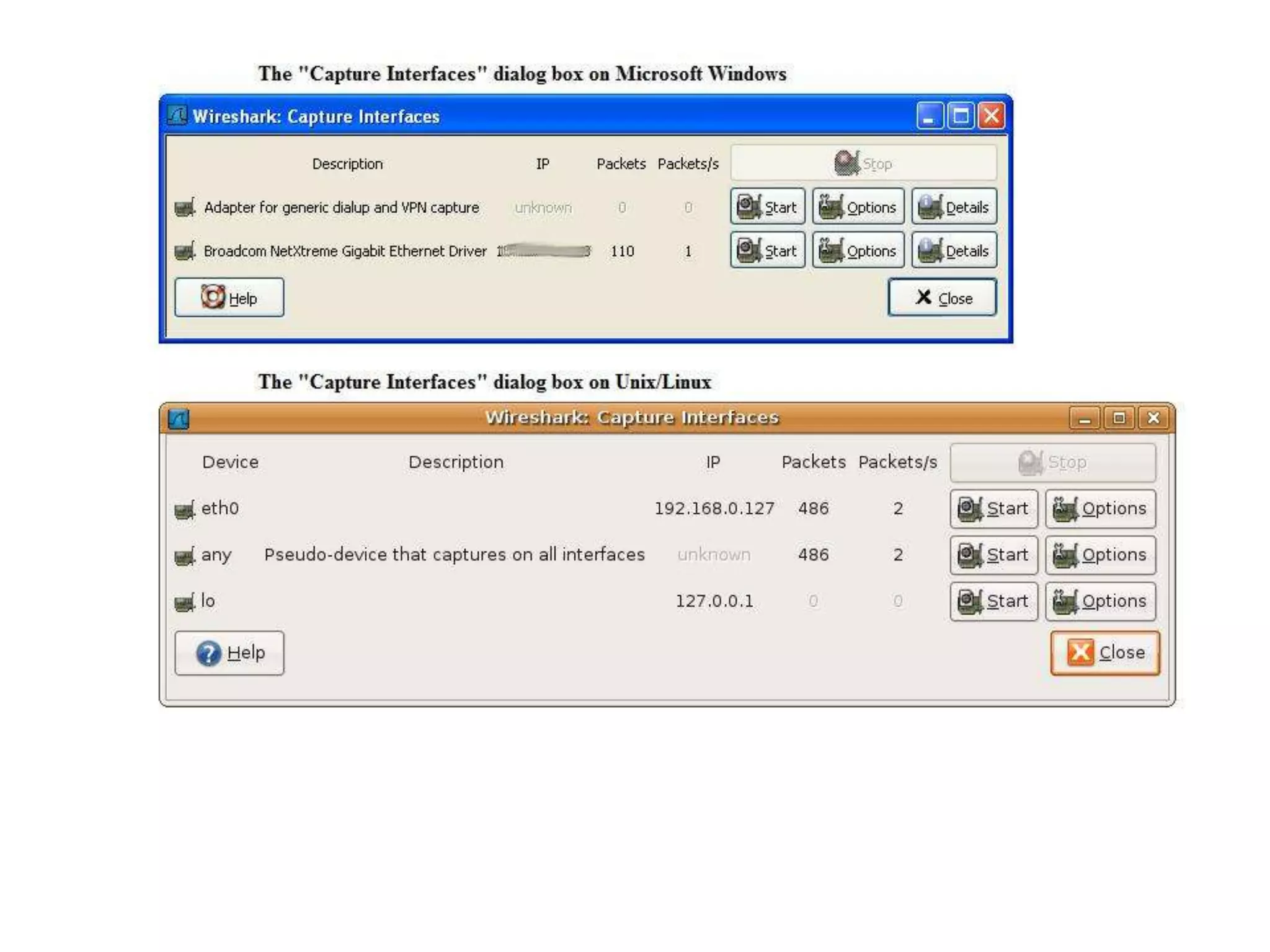
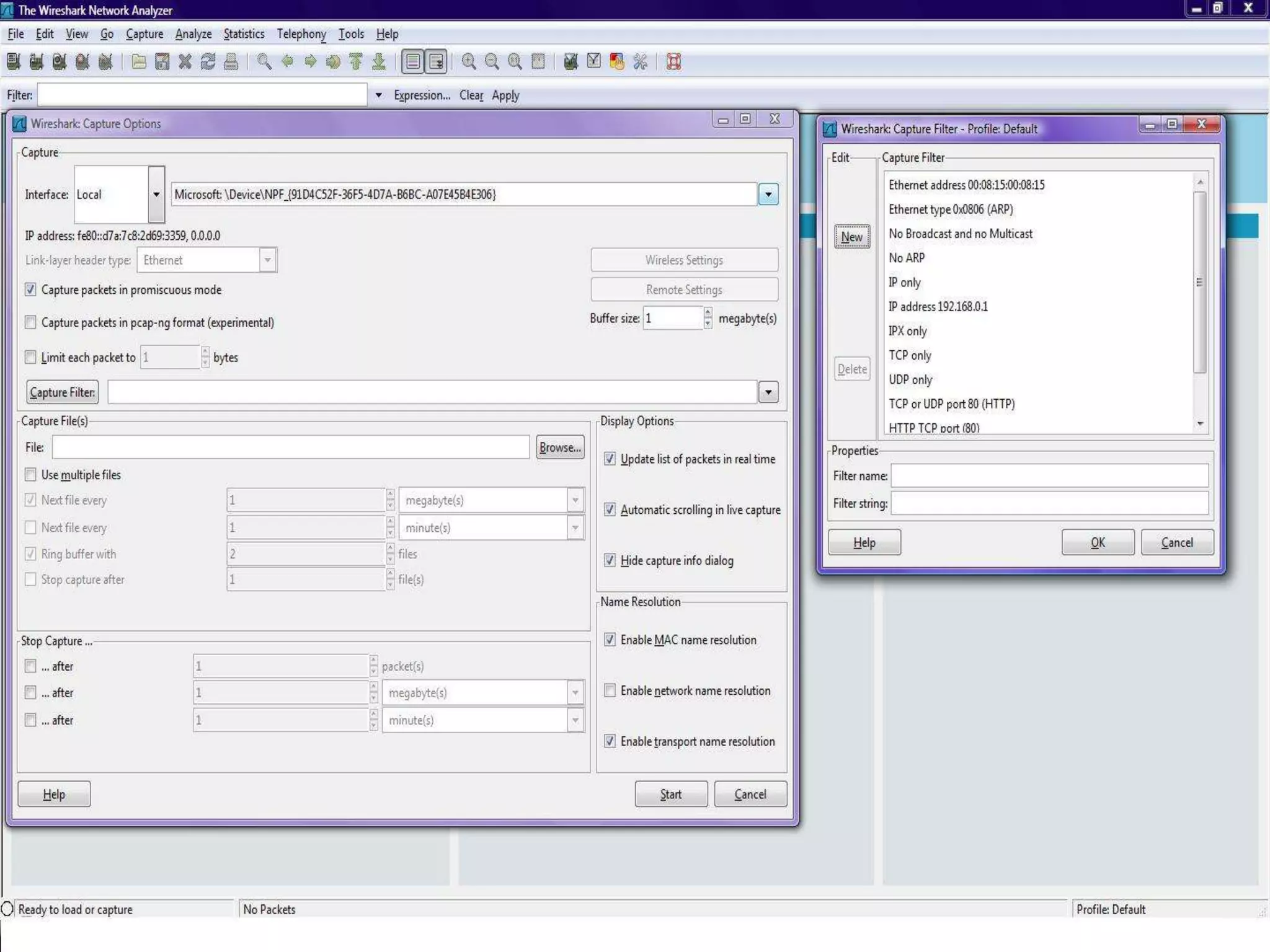
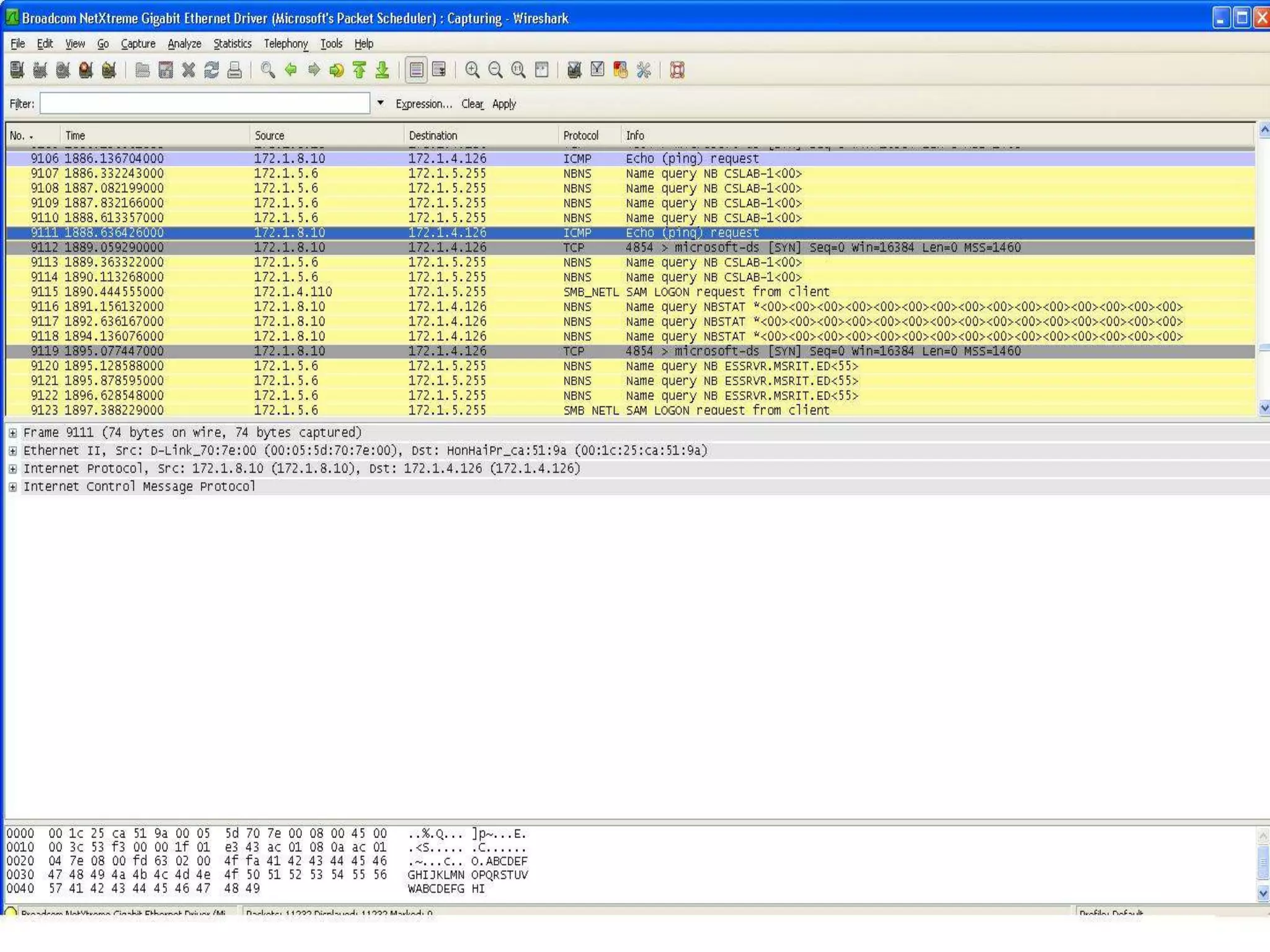
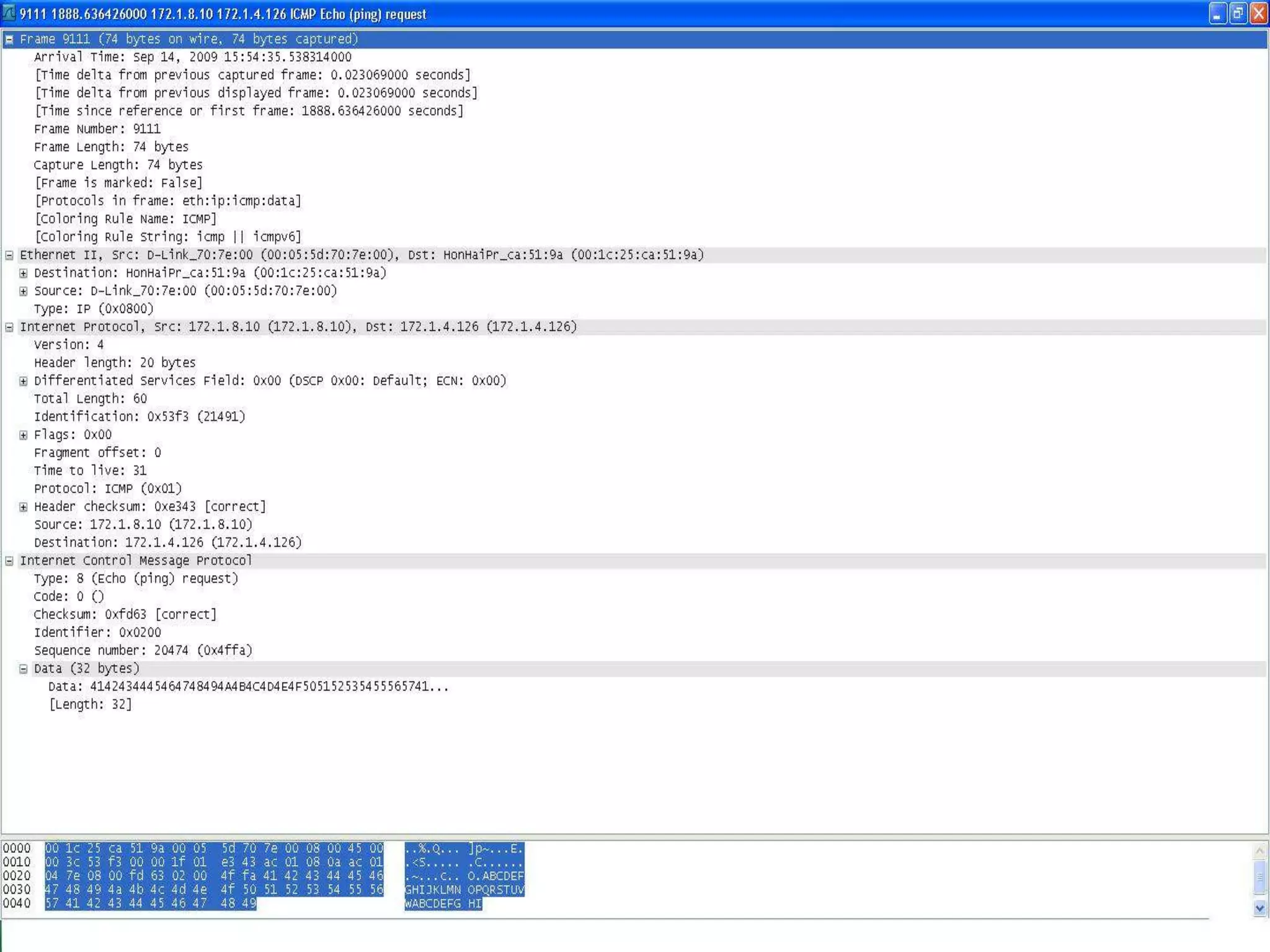
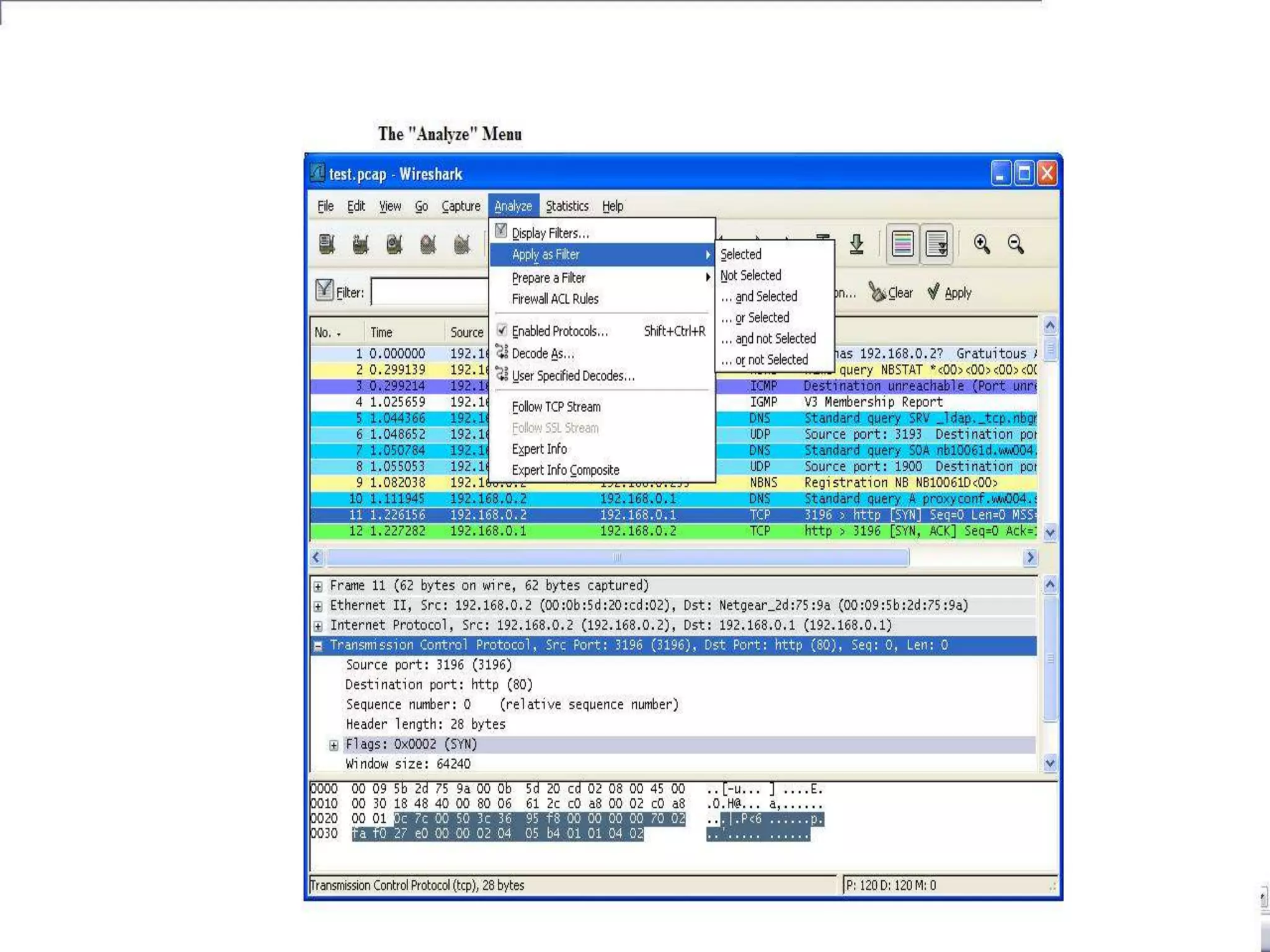
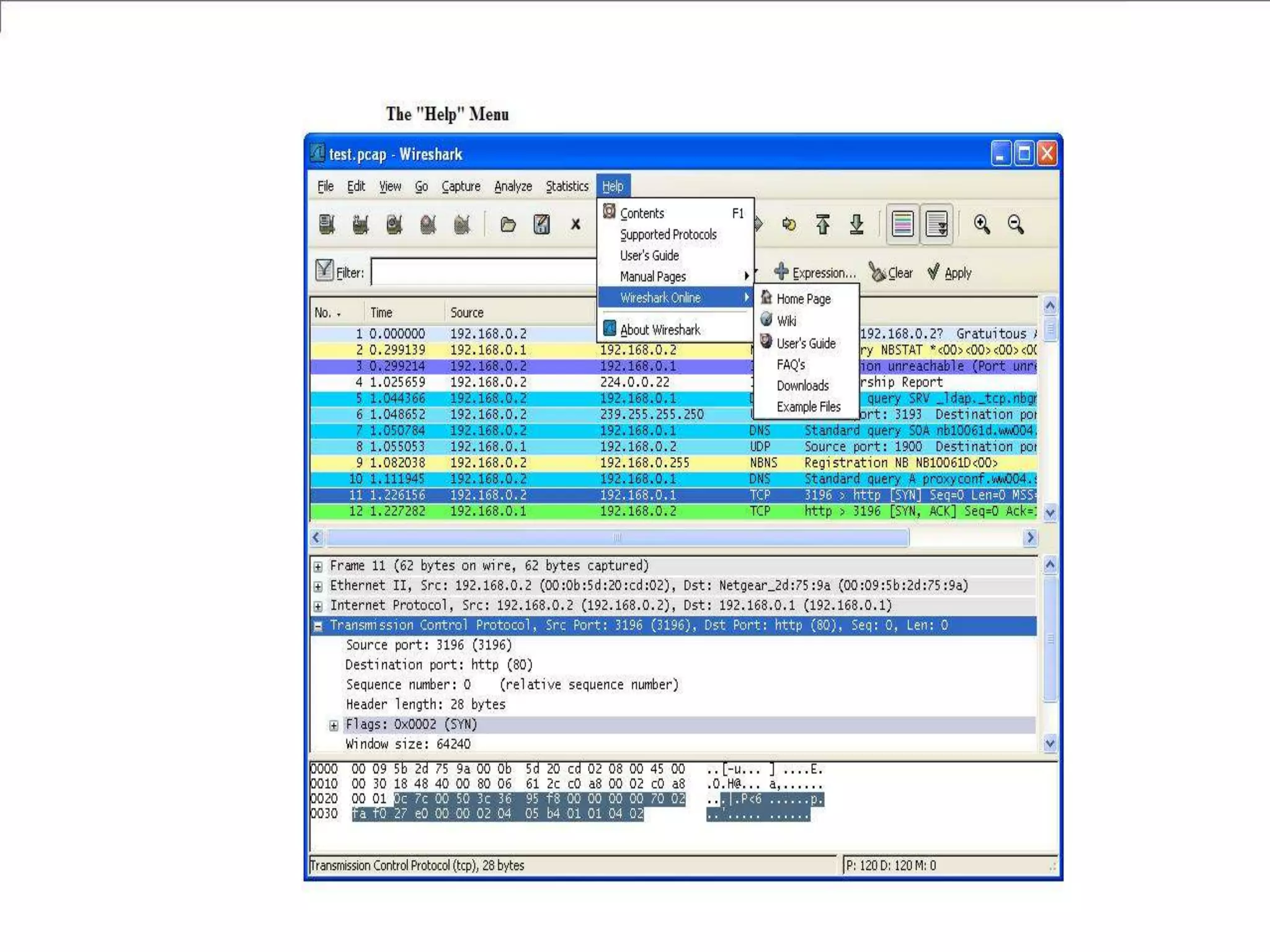
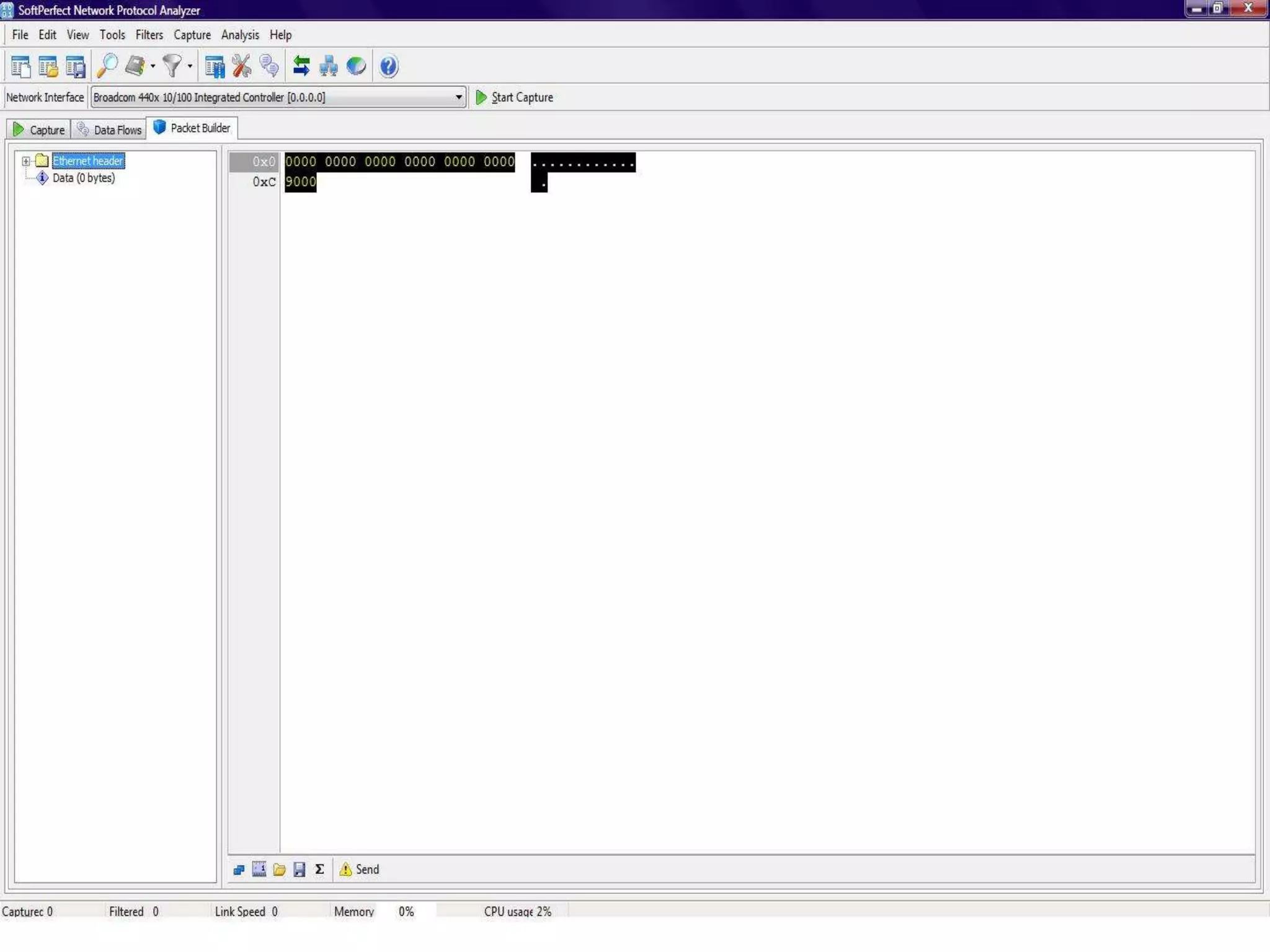
The document discusses Wireshark, an open source network packet analyzer software. It can be used for network troubleshooting, monitoring network traffic and analyzing protocol behavior. Key features include live packet capture from network interfaces, detailed packet display, capture file import/export and many filtering options. While useful for security, development and learning, it does not actively manipulate network traffic or detect intrusions. It requires a supported network card and is available for Windows, Mac and various Linux/Unix systems.