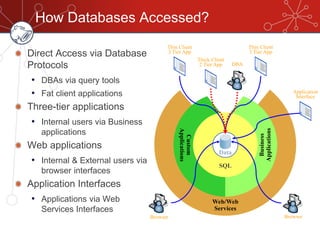
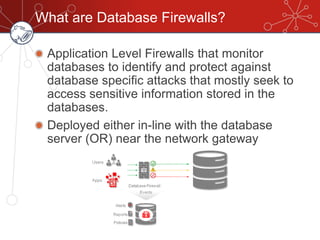
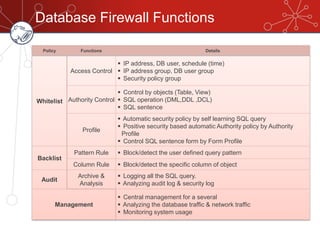
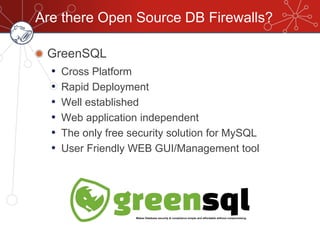
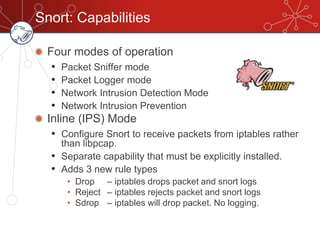
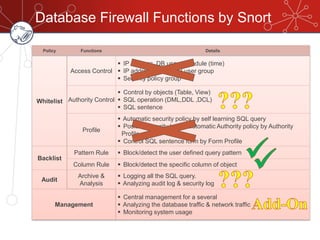
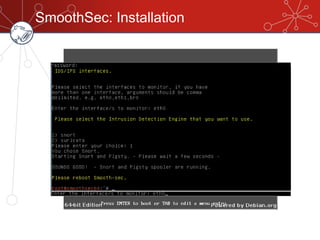
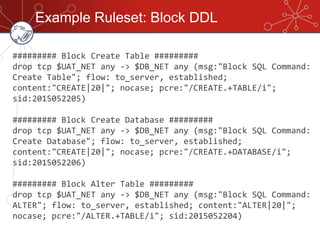
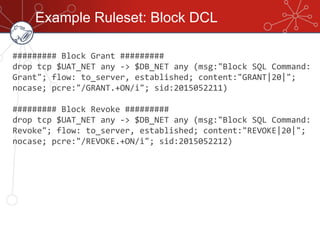
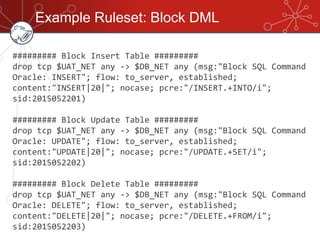
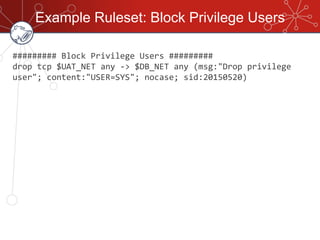
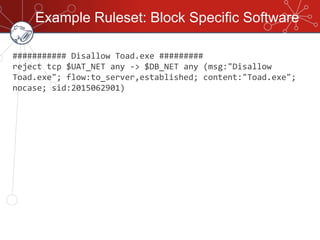
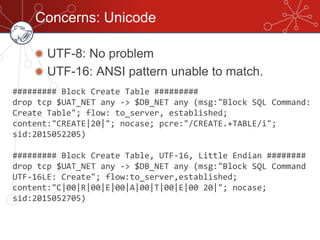
The document discusses database firewalls, specifically focusing on snort as an open-source solution for protecting databases from specific attacks. It outlines the functionality of database firewalls, including access control, auditing, and performance monitoring, while also detailing the capabilities and configurations of snort. Additionally, it provides examples of rulesets to block unauthorized SQL commands and addresses concerns regarding implementation and compatibility.