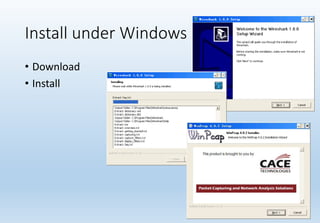
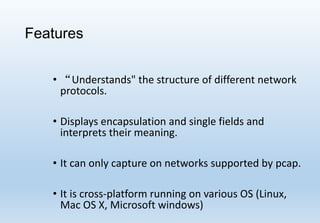
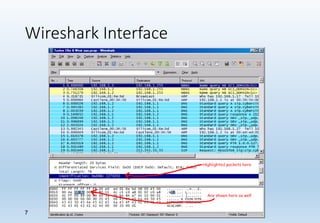
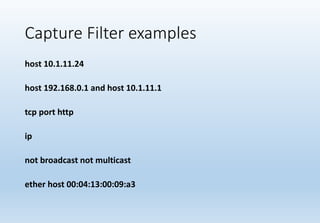
Wireshark is a network packet and protocol analyzer widely used by network administrators, security engineers, and developers for troubleshooting and debugging network issues. It captures network packets and displays detailed information about various protocols, operating across multiple platforms such as Unix and Windows. While not an intrusion detection system, it is essential for measuring network activity and examining protocol internals.