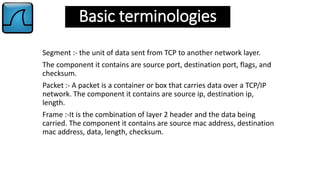
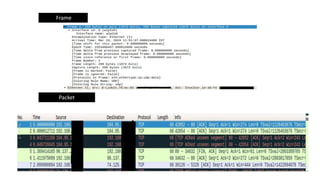
Wireshark is a graphical network protocol analyzer that allows users to examine network packets in detail, supporting various types of network traffic. The document covers installation instructions for both Linux and Windows, basic terminologies like segment, packet, and frame, and highlights features of the Wireshark GUI such as the flow graph and display filters. Additionally, it provides comparisons to similar tools like tcpdump and tshark.