This document discusses different methods for key management in cryptography:
1. Fixed key - A single key is physically loaded onto a client device and used for all encryptions. The key must be replaced if compromised.
2. Master/session key - A master key is shared between host and client beforehand. The host generates session keys and encrypts them with the master key before each transaction.
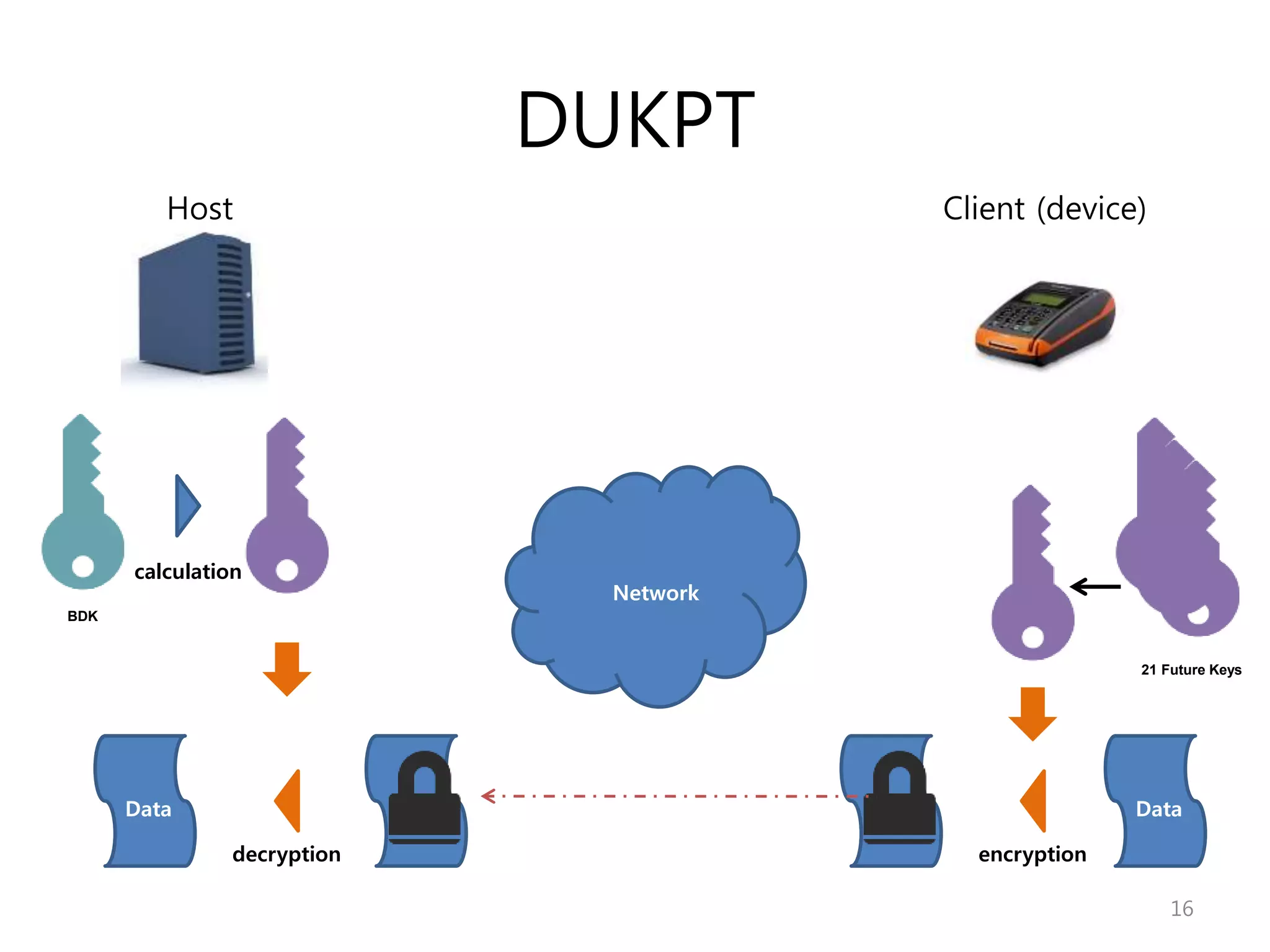
3. DUKPT - The host has a base derivation key (BDK) to generate an initial pin encryption key (IPEK) inserted into the client. The client then generates future keys for encrypting data and replaces used keys. The host decrypts by calculating keys from transmitted identifiers.