- Snort is an open source network intrusion detection system (IDS) that was created in 1998 and has continued to evolve, with a focus on detection capacity, speed and output plugin functionality.
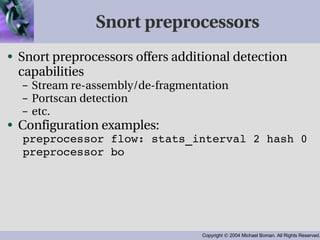
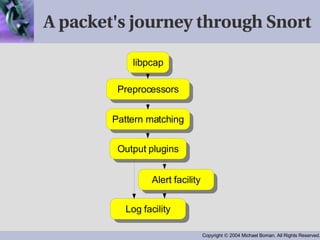
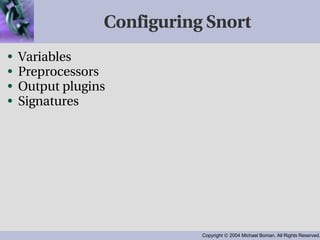
- Snort examines packet flows and compares them to configured rule sets, utilizing variables, preprocessors and output plugins. Common preprocessors perform functions like stream reassembly and portscan detection.
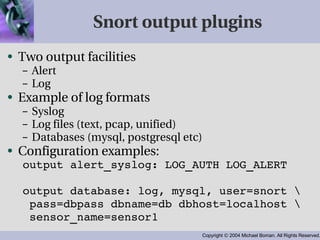
- Output is configured through plugins to perform actions like logging to files or databases. Signatures use a standardized language to define common network attacks and anomalies.
- Unified log files were created to offload alerting from Snort to other applications, improving performance for detection. Compatible spool readers like Barnyard and Mudpit can



![Snort variables Variables can be specified both in the configuration file and from the command line. snort.conf syntax: var HOME_NET [192.168.0.0/24] var EXTERNAL_NET !$HOME_NET Command line syntax (escape it properly): -S HOME_NET=[192.168.0.0/24] Variables are usually specified in snort.conf](https://image.slidesharecdn.com/snort861/85/Snort-11-320.jpg)