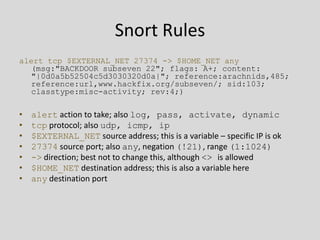
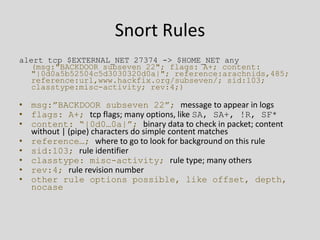
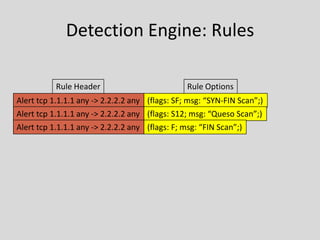
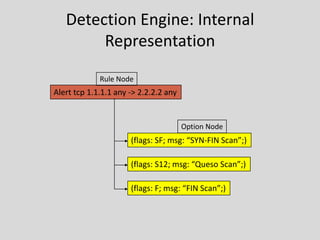
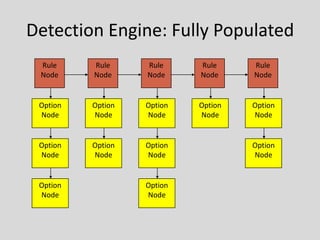
This document provides an overview of intrusion prevention systems (IPS). It defines IPS and their main functions, which include identifying intrusions, logging information, attempting to block intrusions, and reporting them. It also discusses terminology related to IPS like false positives and negatives. The document outlines different detection methods used by IPS like signature-based, anomaly-based, and stateful protocol analysis. It categorizes IPS based on deployment like network-based, host-based, and wireless. It provides Snort, an open-source IPS, as a case study and discusses its components, rules structure, and challenges.
![IPS
[Intrusion Prevention System]
Vishwanath Badiger
Avaya India](https://image.slidesharecdn.com/ipsv01-120911035731-phpapp01/75/Intrusion-Prevention-System-1-2048.jpg)


![Classifications
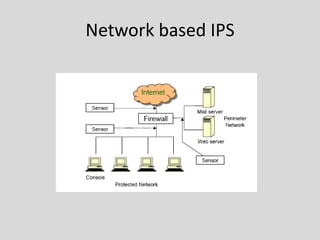
• Network based IPS [NIPS]
– Perform packet sniffing and analyze network traffic to
identify and stop suspicious activity
– They are typically deployed inline like a network
firewall
– They receive packets, analyze them, decide whether
they should be permitted, and allow acceptable
packets to pass through
– Most products use a combination of attack signatures
and analysis of network and application protocols
– Some products allow administrators to create and
deploy attack signatures](https://image.slidesharecdn.com/ipsv01-120911035731-phpapp01/85/Intrusion-Prevention-System-7-320.jpg)
![Classifications
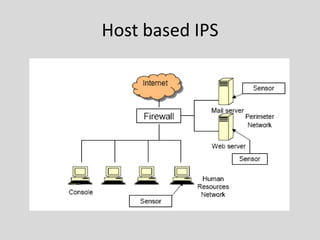
• Host based IPS [HIPS]
– HIPS are similar in principle and purpose to network-
based , except that a host-based product monitors the
characteristics of a single host and the events
occurring within that host, such as monitoring
network traffic (only for that host), system logs,
running processes, file access and modification, and
system and application configuration changes
– Host-based IDPSs are most commonly deployed on
critical hosts such as publicly accessible servers and
servers containing sensitive information](https://image.slidesharecdn.com/ipsv01-120911035731-phpapp01/85/Intrusion-Prevention-System-9-320.jpg)
![Classifications
• Network Behavior Analysis [NBA]
– Examines network traffic to identify threats that
generate unusual traffic flows, such as denial of
service (DoS) and distributed denial of service (DDoS)
attacks, certain forms of malware and policy violations
– NBA systems are most often deployed to monitor
flows on an organization’s internal networks and flows
between an organization’s networks and external
networks](https://image.slidesharecdn.com/ipsv01-120911035731-phpapp01/85/Intrusion-Prevention-System-11-320.jpg)
![Classifications
• Wireless IPS [WIPS]
– Monitors wireless network traffic and analyzes its
wireless networking protocols to identify suspicious
activity involving the protocols themselves
– It cannot identify suspicious activity in the application
or higher-layer network protocols (e.g., TCP, UDP) that
the wireless network traffic is transferring](https://image.slidesharecdn.com/ipsv01-120911035731-phpapp01/85/Intrusion-Prevention-System-12-320.jpg)