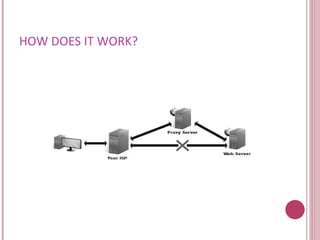
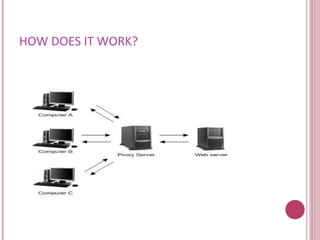
A proxy server acts as an intermediary between a client and the internet. It allows enterprises to ensure security, administrative control, and caching services. There are different types of proxy servers such as caching proxies, web proxies, content filtering proxies, and anonymizing proxies. Proxy servers can operate in either a transparent or opaque mode. They provide benefits like security, performance improvements through caching, and load balancing but also have disadvantages like creating single points of failure.