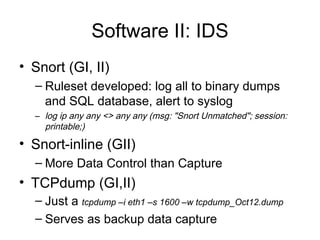
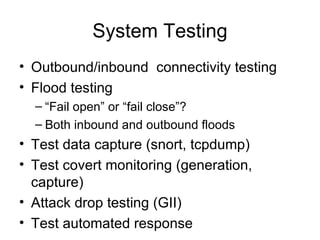
The document discusses the implementation, deployment, and maintenance of honeypots, providing an overview of their purpose, types, and strategic considerations for capturing and studying attacks. It outlines various technical aspects, including policies, network placements, and platforms required for effective honeypot operation. The document emphasizes the importance of honeypots in improving security by offering insights into attacker methodologies and enhancing incident response capabilities.