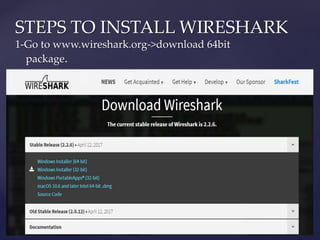
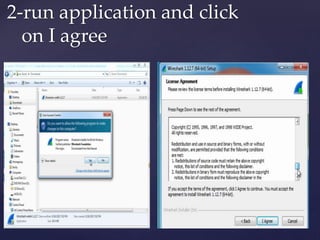
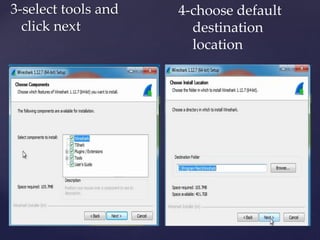
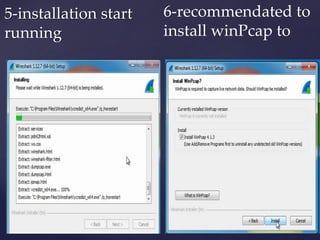
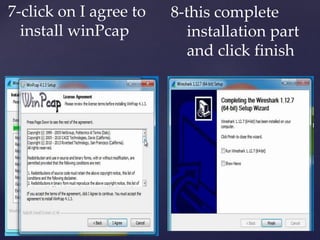
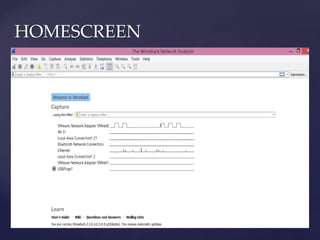
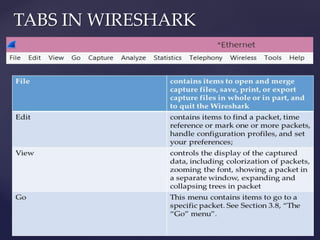
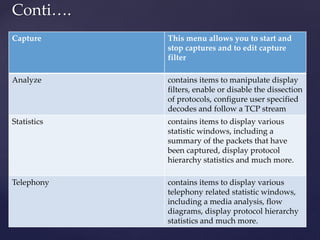
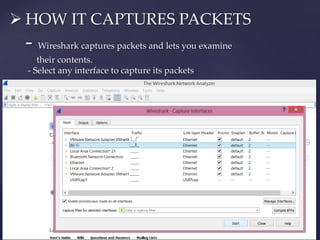
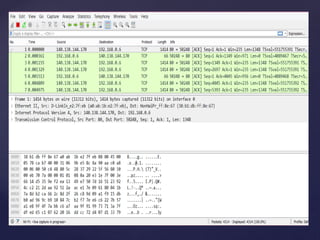
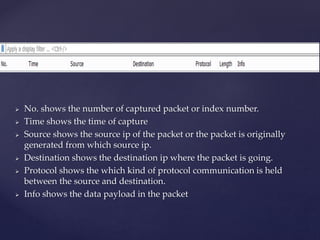
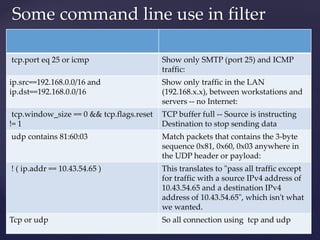
Wireshark is a network packet analyzer that allows users to examine network packet data and traffic in detail. It can capture live packet data from interfaces, open saved capture files, and display packets with detailed protocol information. Network administrators, security engineers, and developers use Wireshark to troubleshoot network issues, examine security problems, and debug protocol implementations.