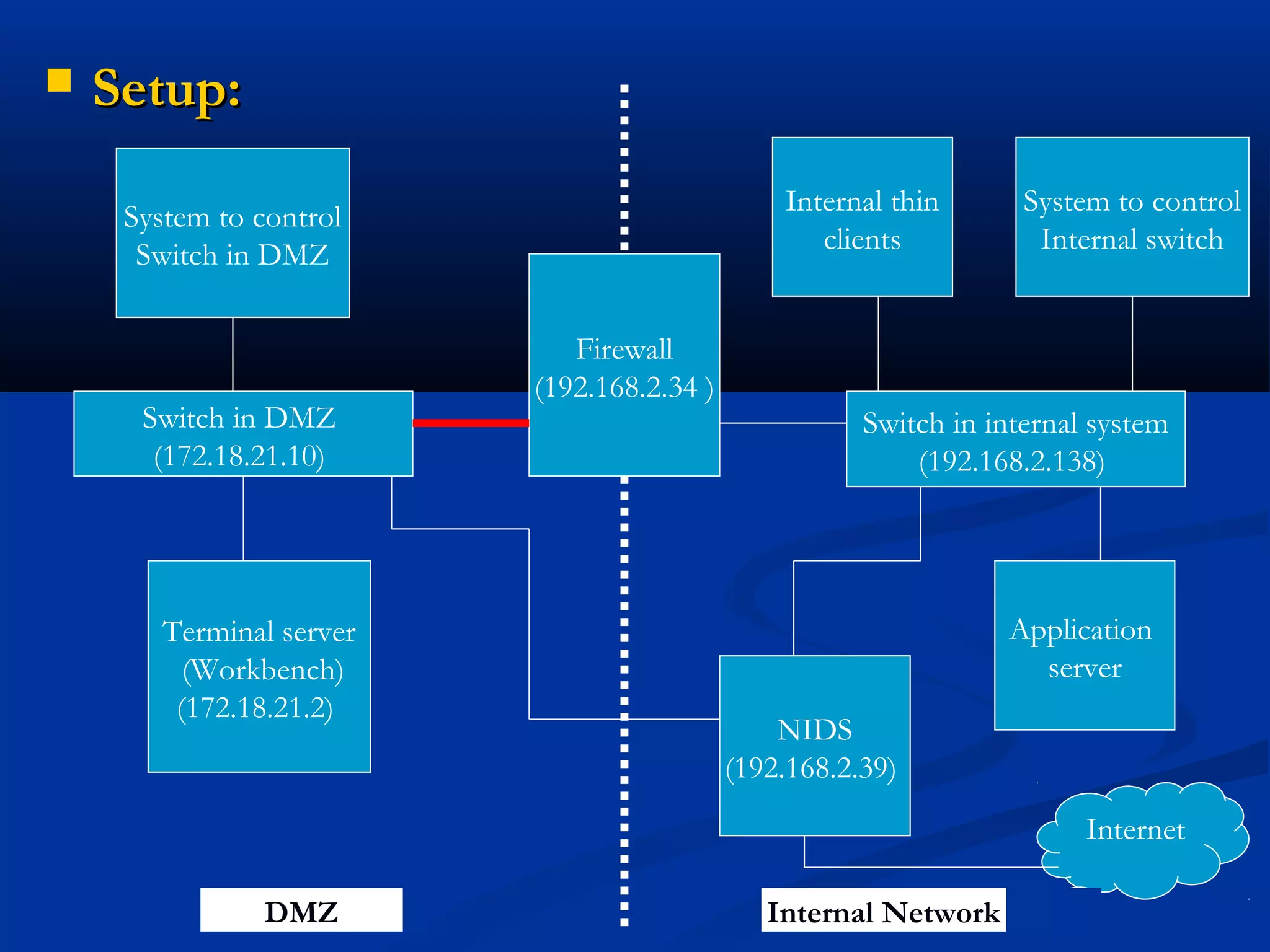
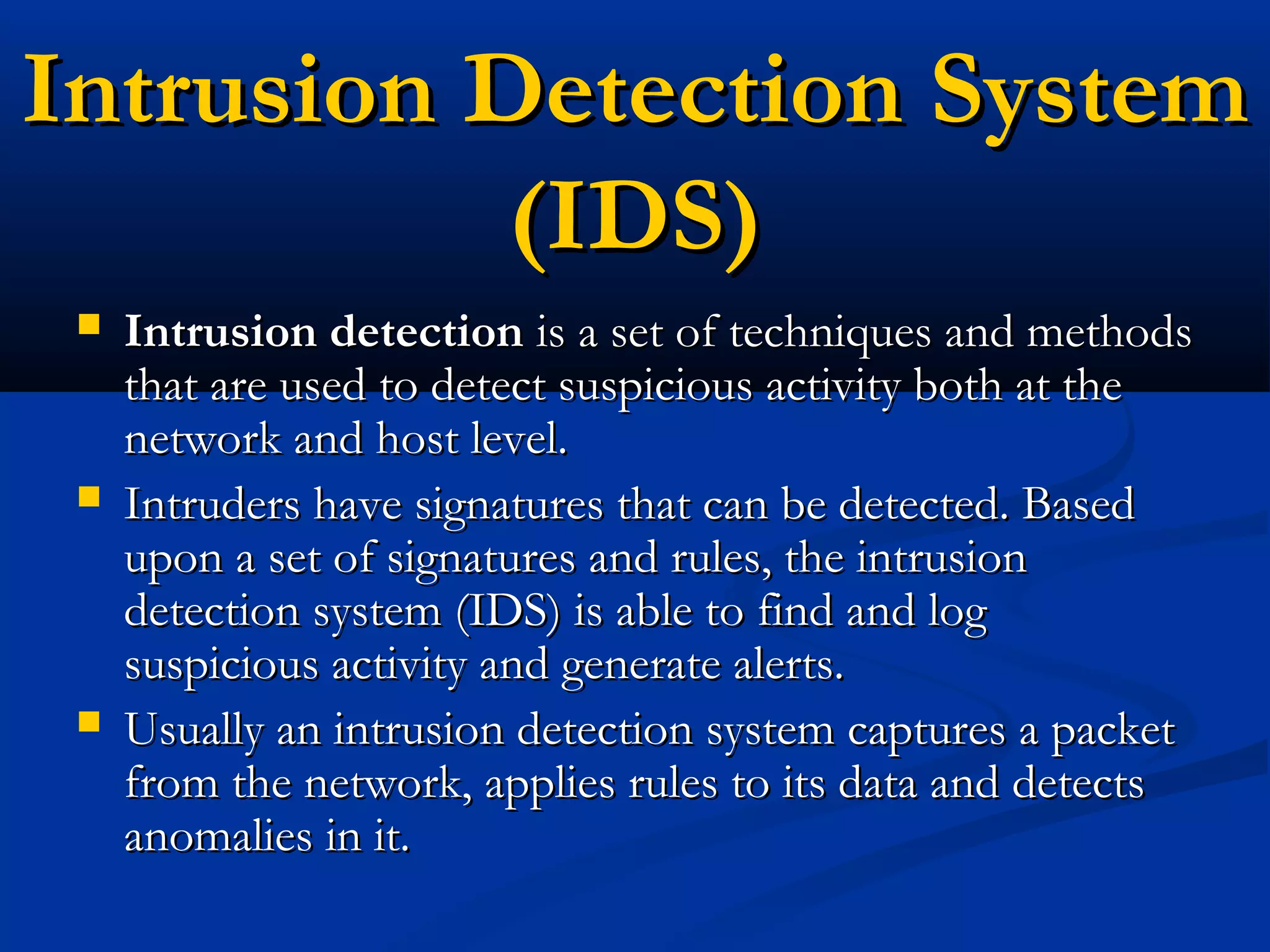
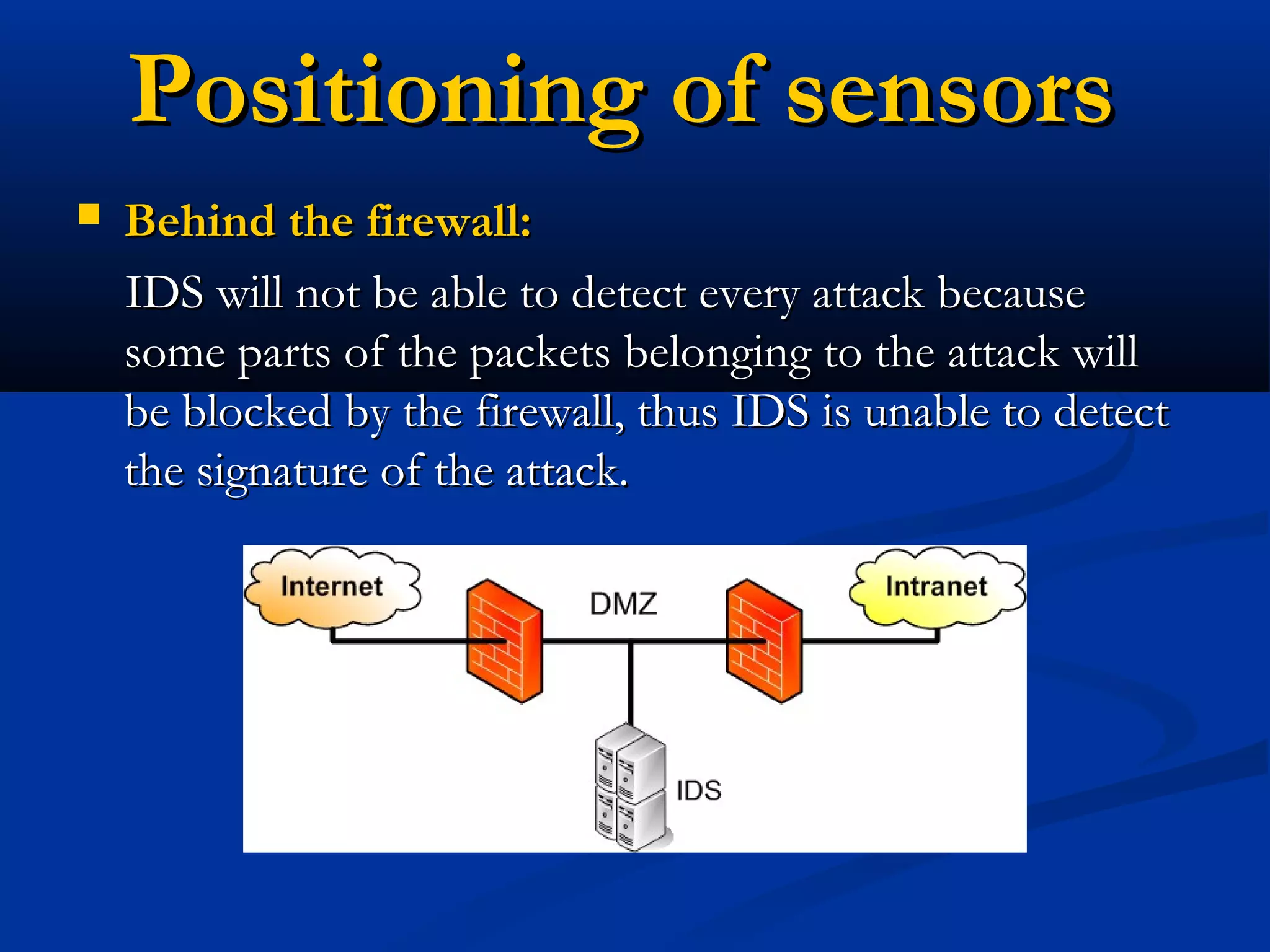
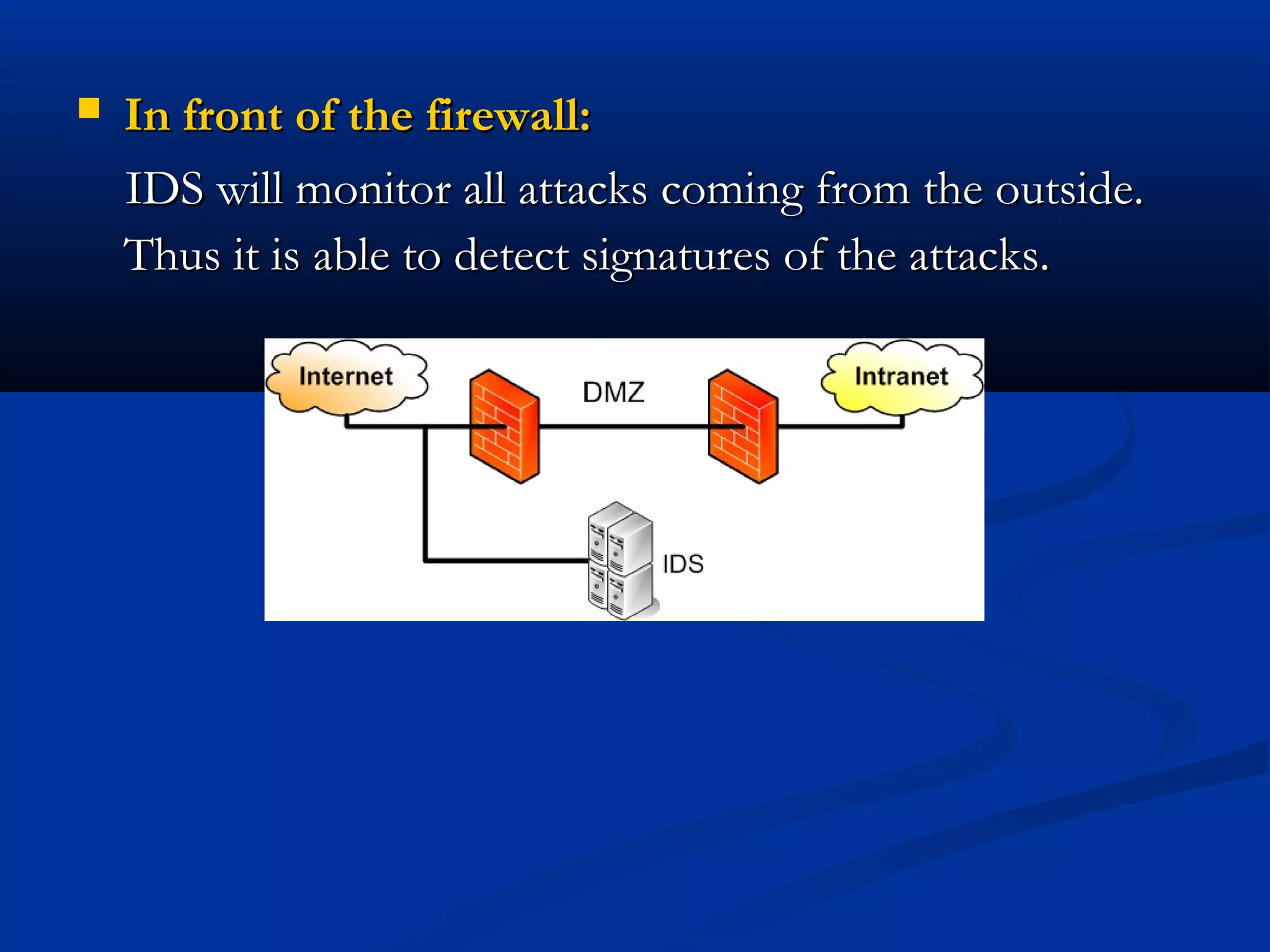
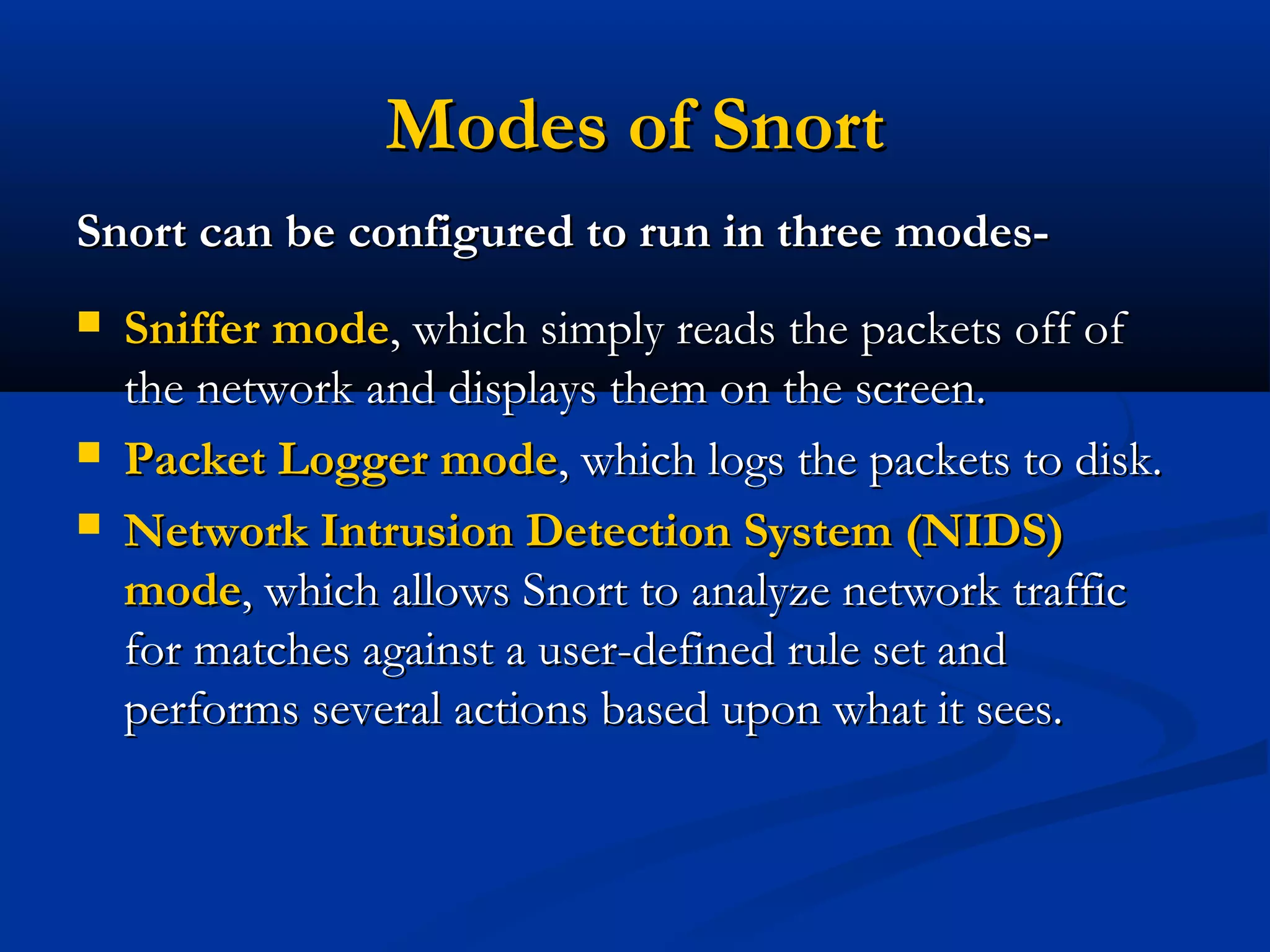
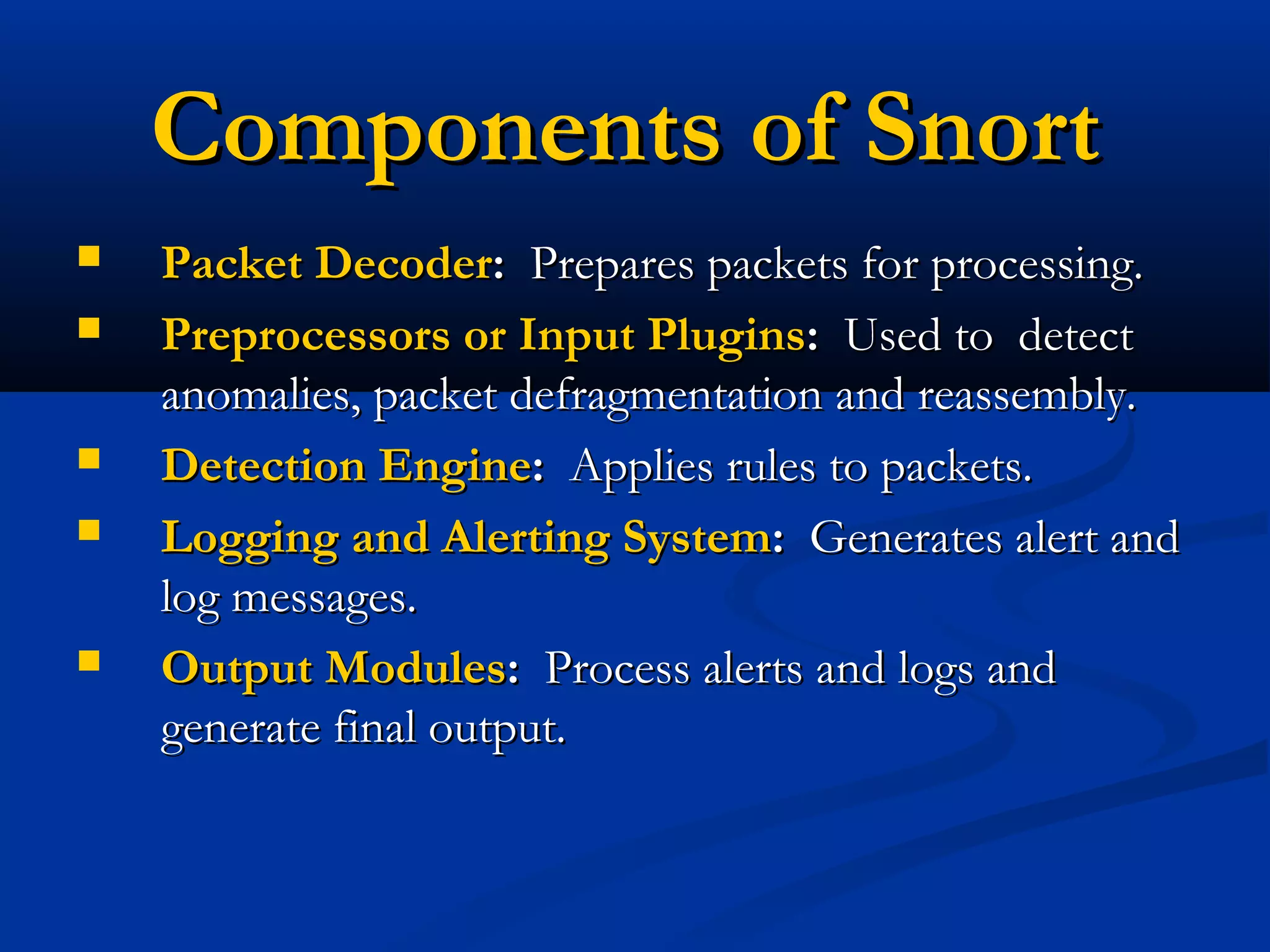
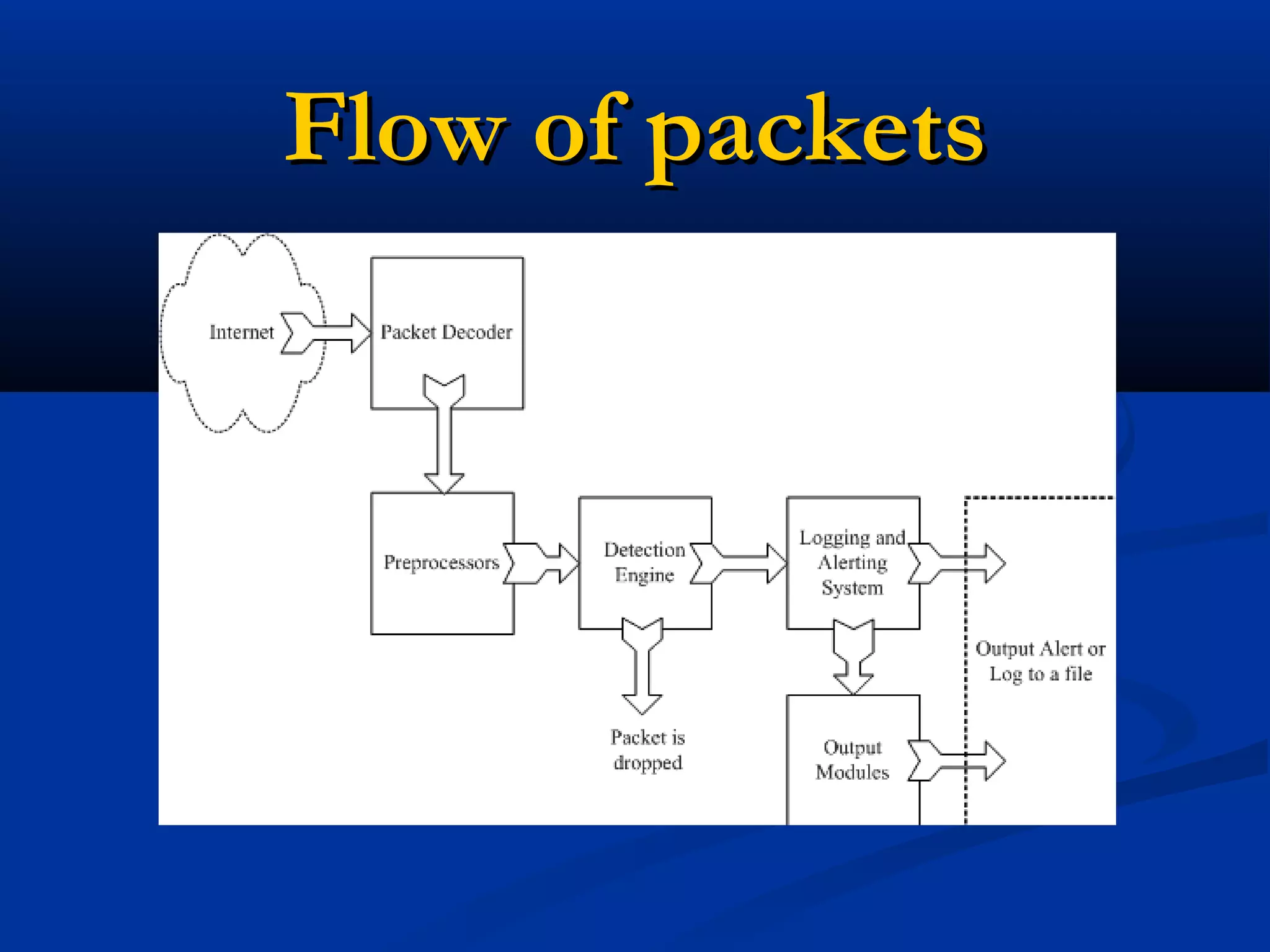
The document discusses the development of a rule-based network intrusion detection system (IDS) using Snort, BASE, and Wireshark to enhance network security for Siemens' SPPA-T3000 system. It details the architecture and components of IDS, including types, detection engines, and Snort's functionalities, along with implementation steps and configurations. The project ultimately aims to monitor network traffic for suspicious activities, generate alerts, and provide a web interface for analysis.









![Use of VariablesUse of Variables
Three types of variables may be defined in Snort:Three types of variables may be defined in Snort:
•• var • portvar • ipvarvar • portvar • ipvar
Defining variables:Defining variables:
var RULES_PATH /snort/rules/var RULES_PATH /snort/rules/
portvar MY_PORTS [22,80,1024:1050]portvar MY_PORTS [22,80,1024:1050]
ipvar MY_NET [192.168.1.0/24,10.1.1.0/24]ipvar MY_NET [192.168.1.0/24,10.1.1.0/24]
Implementing variables:Implementing variables:
alert tcp any any -> $MY_NET $MY_PORTS ( msg:"SYNalert tcp any any -> $MY_NET $MY_PORTS ( msg:"SYN
packet";)packet";)
include $RULE_PATH/example.ruleinclude $RULE_PATH/example.rule](https://image.slidesharecdn.com/2-nids-snort-150904163235-lva1-app6892/75/Network-Intrusion-Detection-System-Using-Snort-17-2048.jpg)