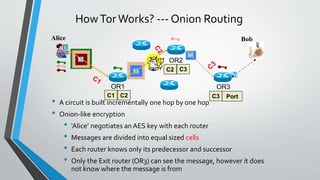
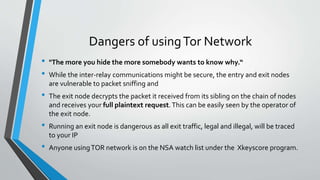
The document is a presentation on the Tor network, discussing its purpose of ensuring user anonymity while browsing the internet, how it operates through a layered encryption system called onion routing, and its functionalities including hidden services. It highlights various weaknesses of the network, such as vulnerabilities to eavesdropping and specific attacks. Lastly, it addresses the dual nature of Tor's use, being a tool for both privacy-seeking individuals and those engaging in illegal activities.