Wireshark network analysing software
•Download as PPTX, PDF•
1 like•836 views
it is a PPT on cyber security. one software Wireshark witch is use for the analyse the network protocols or packages.
Report
Share
Report
Share
Recommended
Wireshark

Powerpoint presentation which covers the basic concepts of Wireshark GUI and Command Line (Tshark).
Packet analysis using wireshark

Brief introduction about wireshark and practical usecases of packet analysis
Wireshark Tutorial

Become Wireshark Certified - https://www.udemy.com/wireshark-tutorial/?couponCode=CEWS Understand Wireshark and how this network analyzer tool can help you succeed in your Wireshark job!
Wireshark

Wireshark is the graphical network protocol analyzer tool.
The ppt covers all the basics which will help you to kick start with wireshark.
Wireshark Basic Presentation

Wireshark is a open source Network Packet Analyzer. It is used for capturing network packets and to display that packet data as detailed as possible.
Recommended
Wireshark

Powerpoint presentation which covers the basic concepts of Wireshark GUI and Command Line (Tshark).
Packet analysis using wireshark

Brief introduction about wireshark and practical usecases of packet analysis
Wireshark Tutorial

Become Wireshark Certified - https://www.udemy.com/wireshark-tutorial/?couponCode=CEWS Understand Wireshark and how this network analyzer tool can help you succeed in your Wireshark job!
Wireshark

Wireshark is the graphical network protocol analyzer tool.
The ppt covers all the basics which will help you to kick start with wireshark.
Wireshark Basic Presentation

Wireshark is a open source Network Packet Analyzer. It is used for capturing network packets and to display that packet data as detailed as possible.
Network Packet Analysis with Wireshark

Presented @ ISA Safety & Security Symposium 2012
Aneheim, CA, April 2012
Wireshark is the de facto network packet analysis tool used in the industry today. It is an easily extensible open–source tool that provides a large number of capabilities for users. It’s not just for IT–based protocols either. Many industrial protocols have created packet decoders for Wireshark. This tutorial will provide the user with:
* An introduction to protocol layering
* A basic overview of packet capture and analysis
* A demonstration of how Wireshark can be used for packet capture and analysis
* Examples of some industrial protocol in Wireshark
* An explanation of some more advanced features available in Wireshark
wireshark

What is Wireshark?
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communication protocol development, and education.
Wireshark perhaps one of the best open source packet analyzer available for Windows and LINX
Some Important Purpose
Network Administrator used for troubleshoot network problem.
Network security engineer used for examine security problem.
Developer used for debug protocol implementation.
People used for learn protocol protocol internals.
Practical Packet Analysis: Wireshark 

Introduction to Wireshark and how it can be used to analyze packets.
Best Network Performance Monitoring Tool

Latest information about basic of Network Performance monitoring and best network monitoring tool with it's key features. I hope this information helps you to choose best network monitoring tools for your enterprise.
Network monitoring system

This presentation helps the beginners understand the network monitoring system.
Network Monitoring System and Alert System

Network Monitoring by cacti
and alert via email(gmail/hotmail smart host), sms, twitter
for completed lab file go to http://goo.gl/6QnHK
Workshop Wireshark 

Wireshark workshop with basic functions and tips for troubleshooting network problems.
Understanding NMAP

This is the basic document related to NMAP. This was present during the Defense Saturday 8. Defense Saturday is one of the initiative by SecuDemy.com
Packet analyzing with wireshark-basic of packet analyzing - Episode_01

Packet analyzing with Wireshark - basic of packet analyzing
More Related Content
What's hot
Network Packet Analysis with Wireshark

Presented @ ISA Safety & Security Symposium 2012
Aneheim, CA, April 2012
Wireshark is the de facto network packet analysis tool used in the industry today. It is an easily extensible open–source tool that provides a large number of capabilities for users. It’s not just for IT–based protocols either. Many industrial protocols have created packet decoders for Wireshark. This tutorial will provide the user with:
* An introduction to protocol layering
* A basic overview of packet capture and analysis
* A demonstration of how Wireshark can be used for packet capture and analysis
* Examples of some industrial protocol in Wireshark
* An explanation of some more advanced features available in Wireshark
wireshark

What is Wireshark?
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communication protocol development, and education.
Wireshark perhaps one of the best open source packet analyzer available for Windows and LINX
Some Important Purpose
Network Administrator used for troubleshoot network problem.
Network security engineer used for examine security problem.
Developer used for debug protocol implementation.
People used for learn protocol protocol internals.
Practical Packet Analysis: Wireshark 

Introduction to Wireshark and how it can be used to analyze packets.
Best Network Performance Monitoring Tool

Latest information about basic of Network Performance monitoring and best network monitoring tool with it's key features. I hope this information helps you to choose best network monitoring tools for your enterprise.
Network monitoring system

This presentation helps the beginners understand the network monitoring system.
Network Monitoring System and Alert System

Network Monitoring by cacti
and alert via email(gmail/hotmail smart host), sms, twitter
for completed lab file go to http://goo.gl/6QnHK
Workshop Wireshark 

Wireshark workshop with basic functions and tips for troubleshooting network problems.
Understanding NMAP

This is the basic document related to NMAP. This was present during the Defense Saturday 8. Defense Saturday is one of the initiative by SecuDemy.com
What's hot (20)
Network Forensics: Packet Analysis Using Wireshark

Network Forensics: Packet Analysis Using Wireshark
Similar to Wireshark network analysing software
Packet analyzing with wireshark-basic of packet analyzing - Episode_01

Packet analyzing with Wireshark - basic of packet analyzing
Analysis of network traffic by using packet sniffing tool wireshark

With recent technologies, the growth network is highly increased. The number of network user are rapidly increasing
day by day which reflects the growth of network traffic also. So it’s very important to monitor networks traffic as well as its user’s
activities to keep the network smooth and efficient. For large network it’s very complicated task to monitor the network, because
large amount of packets are available. For this purpose packet sniffing is used. Packet sniffing is important in network
monitoring to watch network activities which help network administrators to find out weakness of network. This paper focuses
on sniffing network traffic working in different environment. Working of Network sniffing tool Wireshark .By using this packet
sniffer we can capture traffic as well as we analyzed capture traffic. We can generate reports on the basis of analyzed traffic.
Many protocol like TCP, IP, UDP etc. are implemented and filtering on basis of protocol is also done. Alerts generated on the occurring of suspected activities.
Wireshark Tool - Features & Benefits.pdf

Wireshark tool has been a staple favourite of cybersecurity engineers for reasons more than one. This open-source network analyser helps in packet sniffing, troubleshooting network problems, and investigating security incidents. If you want to know more about Wireshark this blog here is perfect for you since it offers a detailed account of the major features of the tool. Alongside, the blog also talks about the interfaces supported by Wireshark and its multiple benefits. You will even get to know about the top competitors of the tool from this article.
For your final step, you will synthesize the previous steps and la

For your final step, you will synthesize the previous steps and labs to summarize the major findings from this project.
Specifically, you will prepare a technical report that summarizes your findings including:
1. Provide a table of common ports for protocols we studied. Discuss how security devices can be used to within a larger network to control subnets and devices within those subnets.
2. Discuss network diagnostic tools you used in this lab. Summarize their functionality and describe specifically how you used each tool. Discuss the results you used to assist in both the discovery phase and protocol analysis of the sites you analyzed. What tools impressed you the most and would be most useful for an analyst to employ in the daily activities? What other functionality do you think would be useful to cyber operations analysts?
3. Research and discuss the ethical use of these tools. For example, if you discover a serious vulnerability, what you should you do? What communications should you have with site owners prior to conducting vulnerability scans?
The report should include a title page, table of contents, list of tables and figures (as applicable), content organized into sections. Be sure to properly cite your sources throughout, and include a list of references, formatted in accordance with APA style.
Final Technical Report
31 January 2022
Llyjerylmye Amos
COP 620 Project 1 Final Technical Report
Well-known ports range from 0 to 1023, and are assigned by Internet Assigned Numbers Authority
(IANA) base on the default services that are associated with the assigned ports. Administrators may
obfuscate services that are running on well-known ports by configuring services to be utilized on unused
ephemeral ports. However, the default configuration of well-known ports allow tech savvy personnel
and software vendors to speak a common language when configuring networking devices, information
systems (IS)s and or software applications. Within this lesson, 22-SSH, 23- Telnet, 25-SMTP, 53-DNS, 80-
HTTP, 110-POP3 and 443-HTTPS were the common ports and protocols that were reviewed, table 1.
Port Protocol
22 SSH
23 Telnet
25 SMTP
53 DNS
80 HTTP
110 POP3
443 HTTPS
Table 1. Common ports studies.
Firewalls are the most common network security devices installed on information systems (IS).
According to Cisco (n.d.), “a firewall is a network security device that monitors incoming and outgoing
network traffic and decides whether to allow or block specific traffic based on a defined set of security
rules”. Security rules may be applied to specific ISs, host-based firewalls, or to the entire network,
network-based firewalls to scan emails, hard drives for malware or to allow traffic on certain sections of
the subnet. Firewalls are also categorized into specific type such as, proxy firewalls, stateful inspection
firewalls, unified threat management firewalls, next-generation firewalls (NGFW), ...
ANALYZING NETWORK PERFORMANCE PARAMETERS USING WIRESHARK

Network performance can be a prime concern for network administrators. The performance of the network depends on many factors. Some of the issues faced in the network performance are - Slow Internet, Bottlenecks, Loss of packets and/or retransmissions, and Excessive bandwidth consumption. For troubleshooting a network, an in-depth understanding of network protocols is required. The main objective of this research is to analyze the performance and various other parameters related to the integrity of a network in a home-based network environment using Wireshark. Network traffic is captured for different devices. The captured traffic is then analysed using Wireshark’s basic statistical tools and advanced tools for various performance parameters.
Practical 7 - Using Wireshark Tutorial and Hands-on

Practical 7 - Using Wireshark Tutorial and Hands-on
Similar to Wireshark network analysing software (20)
Packet analyzing with wireshark-basic of packet analyzing - Episode_01

Packet analyzing with wireshark-basic of packet analyzing - Episode_01
Analysis of network traffic by using packet sniffing tool wireshark

Analysis of network traffic by using packet sniffing tool wireshark
For your final step, you will synthesize the previous steps and la

For your final step, you will synthesize the previous steps and la
ANALYZING NETWORK PERFORMANCE PARAMETERS USING WIRESHARK

ANALYZING NETWORK PERFORMANCE PARAMETERS USING WIRESHARK
Practical 7 - Using Wireshark Tutorial and Hands-on

Practical 7 - Using Wireshark Tutorial and Hands-on
More from dharmesh nakum
Braking and multi-quadrant operation of VSI drives,Cycloconverter based indu...

Cycloconverter based induction motor drive;
Braking and multi-quadrant operation of VSI drives;
Variable frequency control from a current source;
Analysis of unsymmetrical faults using the bus impedance matrix, Faults throu...

Analysis of unsymmetrical faults using the bus impedance matrix, Faults through impedance, Computer calculations of fault currents
Dc to Dc Converter (chopper)

it is the power electronics subject topic. fix dc to variable dc converter.
UNDER GROUND CABLE (TYPES OF CABLE)

it is a ppt on the subject of engineering study. ELECTRICAL POWER SYSTEM. cables type witch is use for the high voltage transmission. in this ppt only under ground cables types are present.
Micro controller 8051 Interrupts

it is the presentation on micro controller 8051 interrupts. from laxmi institute of technology(Gujarat)
More from dharmesh nakum (7)
Braking and multi-quadrant operation of VSI drives,Cycloconverter based indu...

Braking and multi-quadrant operation of VSI drives,Cycloconverter based indu...
Analysis of unsymmetrical faults using the bus impedance matrix, Faults throu...

Analysis of unsymmetrical faults using the bus impedance matrix, Faults throu...
Recently uploaded
6th International Conference on Machine Learning & Applications (CMLA 2024)

6th International Conference on Machine Learning & Applications (CMLA 2024) will provide an excellent international forum for sharing knowledge and results in theory, methodology and applications of on Machine Learning & Applications.
一比一原版(IIT毕业证)伊利诺伊理工大学毕业证成绩单专业办理

IIT毕业证原版定制【微信:176555708】【伊利诺伊理工大学毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
An Approach to Detecting Writing Styles Based on Clustering Techniques

An Approach to Detecting Writing Styles Based on Clustering Techniques
Authors:
-Devkinandan Jagtap
-Shweta Ambekar
-Harshit Singh
-Nakul Sharma (Assistant Professor)
Institution:
VIIT Pune, India
Abstract:
This paper proposes a system to differentiate between human-generated and AI-generated texts using stylometric analysis. The system analyzes text files and classifies writing styles by employing various clustering algorithms, such as k-means, k-means++, hierarchical, and DBSCAN. The effectiveness of these algorithms is measured using silhouette scores. The system successfully identifies distinct writing styles within documents, demonstrating its potential for plagiarism detection.
Introduction:
Stylometry, the study of linguistic and structural features in texts, is used for tasks like plagiarism detection, genre separation, and author verification. This paper leverages stylometric analysis to identify different writing styles and improve plagiarism detection methods.
Methodology:
The system includes data collection, preprocessing, feature extraction, dimensional reduction, machine learning models for clustering, and performance comparison using silhouette scores. Feature extraction focuses on lexical features, vocabulary richness, and readability scores. The study uses a small dataset of texts from various authors and employs algorithms like k-means, k-means++, hierarchical clustering, and DBSCAN for clustering.
Results:
Experiments show that the system effectively identifies writing styles, with silhouette scores indicating reasonable to strong clustering when k=2. As the number of clusters increases, the silhouette scores decrease, indicating a drop in accuracy. K-means and k-means++ perform similarly, while hierarchical clustering is less optimized.
Conclusion and Future Work:
The system works well for distinguishing writing styles with two clusters but becomes less accurate as the number of clusters increases. Future research could focus on adding more parameters and optimizing the methodology to improve accuracy with higher cluster values. This system can enhance existing plagiarism detection tools, especially in academic settings.
NUMERICAL SIMULATIONS OF HEAT AND MASS TRANSFER IN CONDENSING HEAT EXCHANGERS...

Power plants release a large amount of water vapor into the
atmosphere through the stack. The flue gas can be a potential
source for obtaining much needed cooling water for a power
plant. If a power plant could recover and reuse a portion of this
moisture, it could reduce its total cooling water intake
requirement. One of the most practical way to recover water
from flue gas is to use a condensing heat exchanger. The power
plant could also recover latent heat due to condensation as well
as sensible heat due to lowering the flue gas exit temperature.
Additionally, harmful acids released from the stack can be
reduced in a condensing heat exchanger by acid condensation. reduced in a condensing heat exchanger by acid condensation.
Condensation of vapors in flue gas is a complicated
phenomenon since heat and mass transfer of water vapor and
various acids simultaneously occur in the presence of noncondensable
gases such as nitrogen and oxygen. Design of a
condenser depends on the knowledge and understanding of the
heat and mass transfer processes. A computer program for
numerical simulations of water (H2O) and sulfuric acid (H2SO4)
condensation in a flue gas condensing heat exchanger was
developed using MATLAB. Governing equations based on
mass and energy balances for the system were derived to
predict variables such as flue gas exit temperature, cooling
water outlet temperature, mole fraction and condensation rates
of water and sulfuric acid vapors. The equations were solved
using an iterative solution technique with calculations of heat
and mass transfer coefficients and physical properties.
Final project report on grocery store management system..pdf

In today’s fast-changing business environment, it’s extremely important to be able to respond to client needs in the most effective and timely manner. If your customers wish to see your business online and have instant access to your products or services.
Online Grocery Store is an e-commerce website, which retails various grocery products. This project allows viewing various products available enables registered users to purchase desired products instantly using Paytm, UPI payment processor (Instant Pay) and also can place order by using Cash on Delivery (Pay Later) option. This project provides an easy access to Administrators and Managers to view orders placed using Pay Later and Instant Pay options.
In order to develop an e-commerce website, a number of Technologies must be studied and understood. These include multi-tiered architecture, server and client-side scripting techniques, implementation technologies, programming language (such as PHP, HTML, CSS, JavaScript) and MySQL relational databases. This is a project with the objective to develop a basic website where a consumer is provided with a shopping cart website and also to know about the technologies used to develop such a website.
This document will discuss each of the underlying technologies to create and implement an e- commerce website.
Water Industry Process Automation and Control Monthly - May 2024.pdf

Water Industry Process Automation and Control Monthly - May 2024.pdfWater Industry Process Automation & Control
Welcome to WIPAC Monthly the magazine brought to you by the LinkedIn Group Water Industry Process Automation & Control.
In this month's edition, along with this month's industry news to celebrate the 13 years since the group was created we have articles including
A case study of the used of Advanced Process Control at the Wastewater Treatment works at Lleida in Spain
A look back on an article on smart wastewater networks in order to see how the industry has measured up in the interim around the adoption of Digital Transformation in the Water Industry.Recycled Concrete Aggregate in Construction Part III

Using recycled concrete aggregates (RCA) for pavements is crucial to achieving sustainability. Implementing RCA for new pavement can minimize carbon footprint, conserve natural resources, reduce harmful emissions, and lower life cycle costs. Compared to natural aggregate (NA), RCA pavement has fewer comprehensive studies and sustainability assessments.
Water billing management system project report.pdf

Our project entitled “Water Billing Management System” aims is to generate Water bill with all the charges and penalty. Manual system that is employed is extremely laborious and quite inadequate. It only makes the process more difficult and hard.
The aim of our project is to develop a system that is meant to partially computerize the work performed in the Water Board like generating monthly Water bill, record of consuming unit of water, store record of the customer and previous unpaid record.
We used HTML/PHP as front end and MYSQL as back end for developing our project. HTML is primarily a visual design environment. We can create a android application by designing the form and that make up the user interface. Adding android application code to the form and the objects such as buttons and text boxes on them and adding any required support code in additional modular.
MySQL is free open source database that facilitates the effective management of the databases by connecting them to the software. It is a stable ,reliable and the powerful solution with the advanced features and advantages which are as follows: Data Security.MySQL is free open source database that facilitates the effective management of the databases by connecting them to the software.
DfMAy 2024 - key insights and contributions

We have compiled the most important slides from each speaker's presentation. This year’s compilation, available for free, captures the key insights and contributions shared during the DfMAy 2024 conference.
Nuclear Power Economics and Structuring 2024

Title: Nuclear Power Economics and Structuring - 2024 Edition
Produced by: World Nuclear Association Published: April 2024
Report No. 2024/001
© 2024 World Nuclear Association.
Registered in England and Wales, company number 01215741
This report reflects the views
of industry experts but does not
necessarily represent those
of World Nuclear Association’s
individual member organizations.
Modelagem de um CSTR com reação endotermica.pdf

Modelagem em função de transferencia. CSTR não-linear.
一比一原版(UofT毕业证)多伦多大学毕业证成绩单如何办理

UofT毕业证原版定制【微信:176555708】【多伦多大学毕业证成绩单-学位证】【微信:176555708】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
学历顾问:微信:176555708
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

K8sGPT is a tool that analyzes and diagnoses Kubernetes clusters. This presentation was used to share the requirements and dependencies to deploy K8sGPT in a local environment.
Governing Equations for Fundamental Aerodynamics_Anderson2010.pdf

Governing Equations for Fundamental Aerodynamics
Recently uploaded (20)
6th International Conference on Machine Learning & Applications (CMLA 2024)

6th International Conference on Machine Learning & Applications (CMLA 2024)
An Approach to Detecting Writing Styles Based on Clustering Techniques

An Approach to Detecting Writing Styles Based on Clustering Techniques
NUMERICAL SIMULATIONS OF HEAT AND MASS TRANSFER IN CONDENSING HEAT EXCHANGERS...

NUMERICAL SIMULATIONS OF HEAT AND MASS TRANSFER IN CONDENSING HEAT EXCHANGERS...
Final project report on grocery store management system..pdf

Final project report on grocery store management system..pdf
Water Industry Process Automation and Control Monthly - May 2024.pdf

Water Industry Process Automation and Control Monthly - May 2024.pdf
Recycled Concrete Aggregate in Construction Part III

Recycled Concrete Aggregate in Construction Part III
Water billing management system project report.pdf

Water billing management system project report.pdf
Planning Of Procurement o different goods and services

Planning Of Procurement o different goods and services
basic-wireline-operations-course-mahmoud-f-radwan.pdf

basic-wireline-operations-course-mahmoud-f-radwan.pdf
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions
Tutorial for 16S rRNA Gene Analysis with QIIME2.pdf

Tutorial for 16S rRNA Gene Analysis with QIIME2.pdf
Pile Foundation by Venkatesh Taduvai (Sub Geotechnical Engineering II)-conver...

Pile Foundation by Venkatesh Taduvai (Sub Geotechnical Engineering II)-conver...
Governing Equations for Fundamental Aerodynamics_Anderson2010.pdf

Governing Equations for Fundamental Aerodynamics_Anderson2010.pdf
Wireshark network analysing software
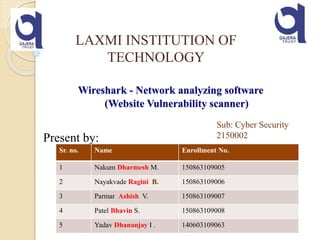
- 1. Wireshark - Network analyzing software (Website Vulnerability scanner) Present by: LAXMI INSTITUTION OF TECHNOLOGY Sr. no. Name Enrollment No. 1 Nakum Dharmesh M. 150863109005 2 Nayakvade Ragini B. 150863109006 3 Parmar Ashish V. 150863109007 4 Patel Bhavin S. 150863109008 5 Yadav Dhananjay I . 140603109063 Sub: Cyber Security 2150002
- 2. Content What is Wireshark Where it use How it works Some practical things
- 3. What is Wireshark? - Network packet/protocol analyzer - One of the best open source packet analyzers available today for UNIX and Windows
- 4. You could think of a network packet analyzer as a measuring device used to examine what’s going on inside a network cable, just like a voltmeter is used by an electrician to examine what’s going on inside an electric cable (but at a higher level, of course). Wireshark is perhaps one of the best open source packet analyzers available today.
- 5. Where it use? - Network Administrators use it to troubleshoot network problems - Network security engineers use it to examine security problems - Testers use it to detect defects :) - People use it to learn network protocol internals.
- 6. WireShark – Sample Demo
- 7. A vulnerability scanner is a computer program designed to assess computers, computer systems, networks or applications for weaknesses. They can be run either as part of vulnerability management by those tasked with protecting systems - or by black hat attackers looking to gain unauthorized access. Website Vulnerability Scanner:
- 8. The following are some of the many features Wireshark provides: •Available for UNIX and Windows. •Capture live packet data from a network interface. •Open files containing packet data captured with tcpdump / WinDump, •Wireshark, and a number of other packet capture programs. •Import packets from text files containing hex dumps of packet data. •Display packets with very detailed protocol information. •Save packet data captured. •Export some or all packets in a number of capture file formats. •Filter packets on many criteria. •Search for packets on many criteria. •Colorize packet display based on filters. •Create various statistics. ... and a lot more! . Features:
- 9. How it works? For Windows - download (http://www.wireshark.org/download.html) - install - use
- 11. Open Wireshark. Click the "Capture" menu, then click "Interfaces." A small window with all of your networking interfaces will appear. If you use any network traffic, you will start to see packets coming in.
- 15. Status Bar 15
- 16. HTTP Analysis
- 17. HTTP Analysis – Load Distribution Click “Create Stat” button You can add “filter” to only Show selected traffic
- 18. HTTP Analysis – Packet Counter
- 19. HTTP Analysis – Requests
- 20. Each line represents a packet, and there are 7 columns that provide information about it is number column shows the order of the packet when you start recording network traffic. This is to provide you with number reference so that you can easily identify particular packet. The time is in seconds, up to 6 decimals, when the packet was received after you started to record network traffic. The source includes the Internet Protocol (IP) address of the packet's origin. The destination IP records where a particular packet is going. The protocol the packet uses. The most common are TCP, UDP and HTTP. Examine each packet's information.
- 22. Video
- 23. The End