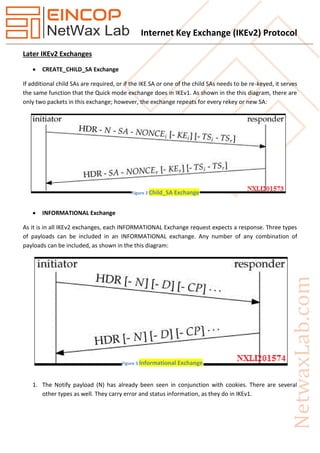
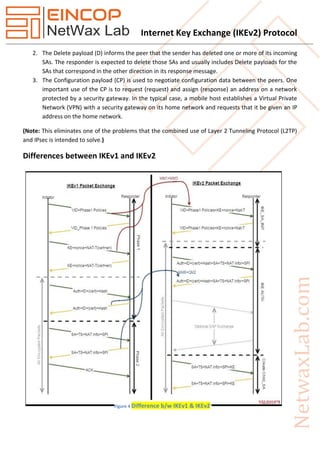
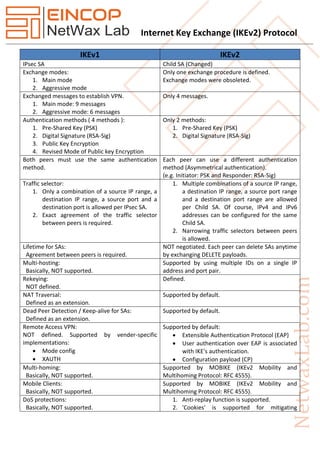
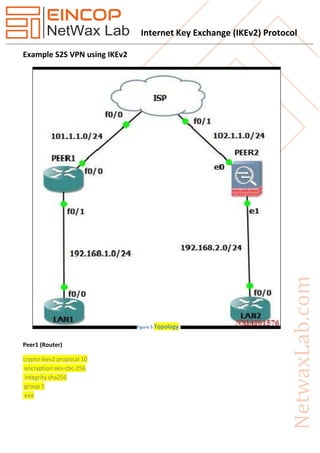
The document discusses the Internet Key Exchange version 2 (IKEv2) protocol, which is used to establish security associations in the IPsec protocol suite, highlighting its improvements over the original IKE protocol. Key enhancements include simpler configurations, standard support for mobility, better NAT traversal, and improved reliability and resilience against denial-of-service attacks. It also outlines the protocol's evolution through various RFCs, detailing initial exchanges, differences with IKEv1, and technical specifications for implementation.