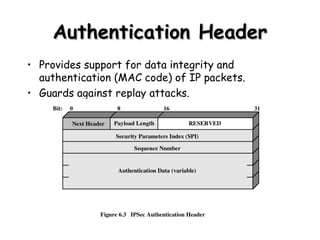
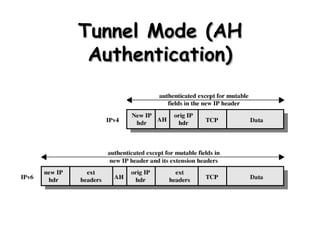
IPSec provides a framework for securing communications over IP networks by authenticating and encrypting IP packets. It includes protocols for authentication headers and encapsulating security payloads to provide integrity, authentication, and confidentiality. Key management protocols like Oakley and ISAKMP are used to securely establish security associations between communicating parties to protect data flows.






































![Oakley: Authentication Three authentication methods: Digital signatures Eks[ H [Nonces, ID]] Public-key encryption EKra [ ID, Nonces] Symmetric-key encryption Eksym [ ID, Nonces]](https://image.slidesharecdn.com/ipsec-090721044112-phpapp01/85/Ip-Sec-45-320.jpg)








