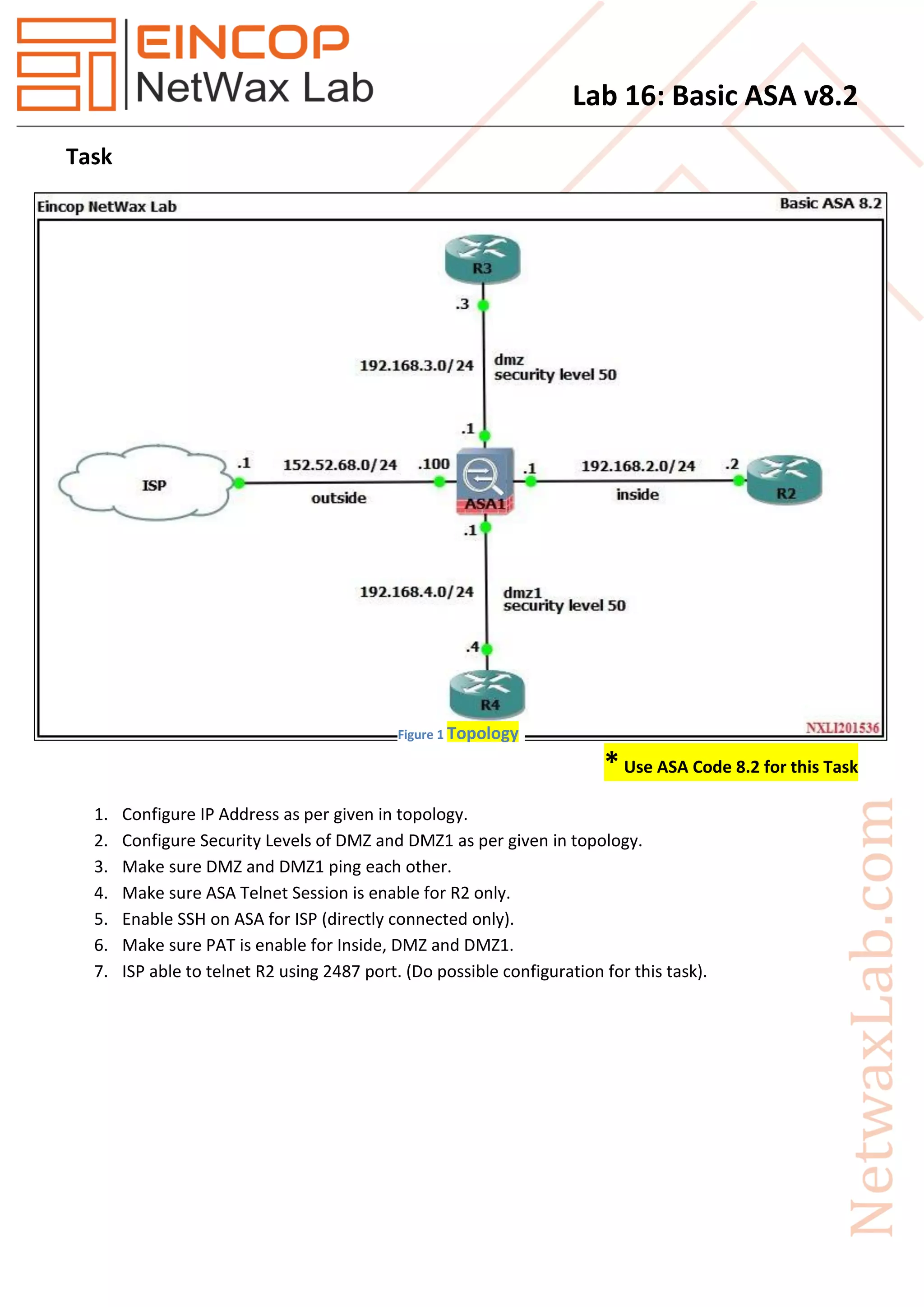
The document provides instructions for configuring an ASA firewall to:
1. Configure security levels and interfaces for DMZ and DMZ1 subnets.
2. Enable ping access between the DMZ and DMZ1 interfaces.
3. Restrict telnet access to the ASA to only the R2 host.
4. Enable SSH access to the ASA from the ISP subnet only.
5. Apply PAT for the Inside, DMZ and DMZ1 interfaces.
6. Allow the ISP to telnet to the R2 host using port 2487.