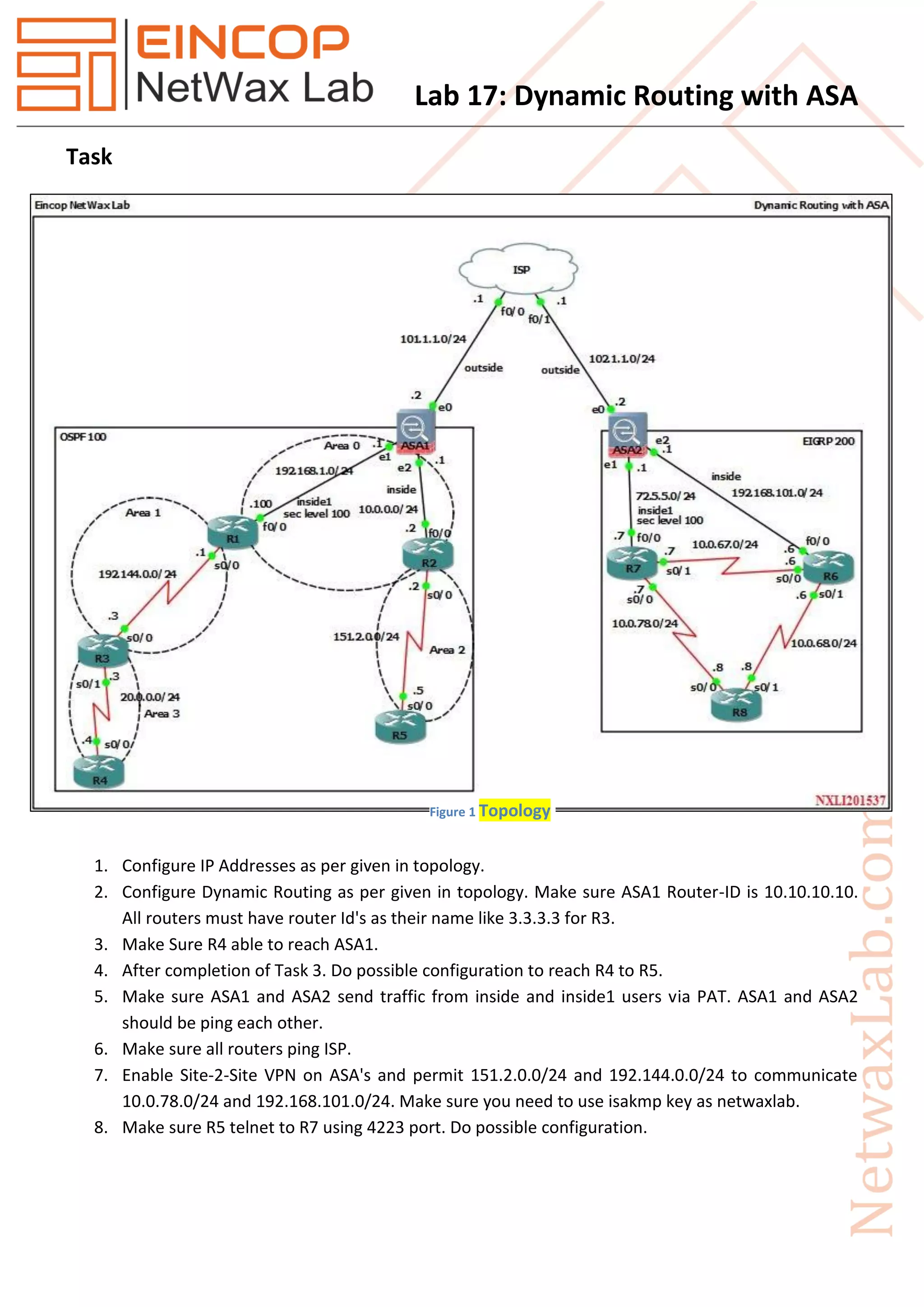
The document describes the steps to configure dynamic routing, site-to-site VPN, and network access between devices in a lab topology. The tasks include: 1) Configuring IP addresses and dynamic routing protocols on routers and firewalls, 2) Establishing connectivity between all devices, 3) Implementing NAT and VPN services on the firewalls to allow communication between specified subnets, and 4) Opening a non-standard port for remote access between two routers via one of the firewalls.