This document provides an overview of IPSec, including:
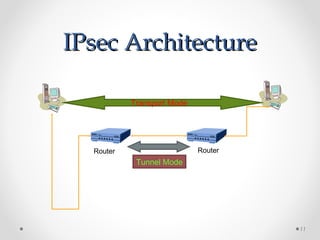
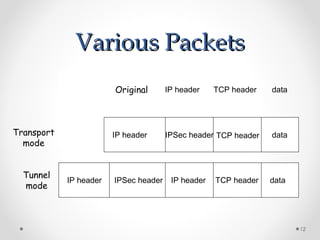
- IPSec aims to secure IP communications by providing authentication, integrity, and confidentiality. It operates in transport and tunnel modes.
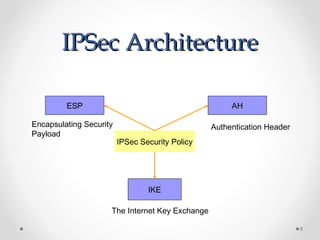
- The Internet Key Exchange (IKE) negotiates and establishes security associations to secure communications between two endpoints.
- IPSec policy defines which encryption, hashing, and authentication methods apply to different network traffic using protection suites and proposals.























![PPhhaassee 11 ((MMaaiinn MMooddee))
29
Initiator Responder
[Header, SA1]](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-29-320.jpg)
![PPhhaassee 11 ((MMaaiinn MMooddee))
30
Initiator Responder
[Header, SA1]
[Header, SA2]
Establish vocabulary for further communication](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-30-320.jpg)
![PPhhaassee 11 ((MMaaiinn MMooddee))
31
Initiator Responder
[Header, SA1]
[Header, SA2]
[Header, KE, Ni, {Cert_Reg} ]](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-31-320.jpg)
![PPhhaassee 11 ((MMaaiinn MMooddee))
32
Initiator Responder
Header, SA1
[Header, SA1]
[Header, KE, Ni { , Cert_Req} ]
[Header, KE, Nr {, Cert_Req}]
Establish secret key using Diffie-Hellman key exchange
Use nonces to prevent replay attacks](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-32-320.jpg)
![PPhhaassee 11 ((MMaaiinn MMooddee))
33
Initiator Responder
[Header, SA1]
[Header, SA1]
[Header, KE, Ni {,Cert_Req} ]
[Header, KE, Nr {,Cert_Req}]
[Header, IDi, {CERT} sig]](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-33-320.jpg)
![PPhhaassee 11 ((MMaaiinn MMooddee))
34
Initiator Responder
[Header, SA1]
[Header, SA1]
[Header, KE, Ni {, Cert_req}]
[Header, KE, Nr {, Cert_req}]
[Header, IDi, {CERT} sig]
[Header, IDr, {CERT} sig]
Signed hash of IDi (without Cert_req , just send the hash)](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-34-320.jpg)
![PPhhaassee 11 ((QQuuiicckk MMooddee))
35
Initiator Responder
[Header, SA1, KE, Ni, IDi]](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-35-320.jpg)
![PPhhaassee 11 ((QQuuiicckk MMooddee))
36
Initiator Responder
[Header, SA1, KE, Ni, IDi]
[Header, SA2, KE, Nr,
IDr, [Cert]sig]
[Header, [Cert]sig]
First two messages combined into one
(combine Hello and DH key exchange)](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-36-320.jpg)







![IIPPSSeecc PPoolliiccyy EExxaammppllee
• In English:
o All traffic to 128.104.120.0/24 must be:
• Use pre-hashed key authentication
• DH group is MODP with 1024-bit modulus
• Hash algorithm is HMAC-SHA (128 bit key)
• Encryption using 3DES
• In IPSec:
o [Auth=Pre-Hash;
DH=MODP(1024-bit);
HASH=HMAC-SHA;
ENC=3DES]
44](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-44-320.jpg)
![IIPPsseecc PPoolliiccyy EExxaammppllee
• In English:
o All traffic to 128.104.120.0/24 must use one of the
following:
• AH with HMAC-SHA or,
• ESP with 3DES as encryption algorithm and
(HMAC-MD5 or HMAC-SHA as hashing algorithm)
• In IPsec:
o [AH: HMAC-SHA] or,
o [ESP: (3DES and HMAC-MD5) or
(3DES and HMAC-SHA)]
45](https://image.slidesharecdn.com/ipsec-140917021733-phpapp01/85/Ipsec-45-320.jpg)




