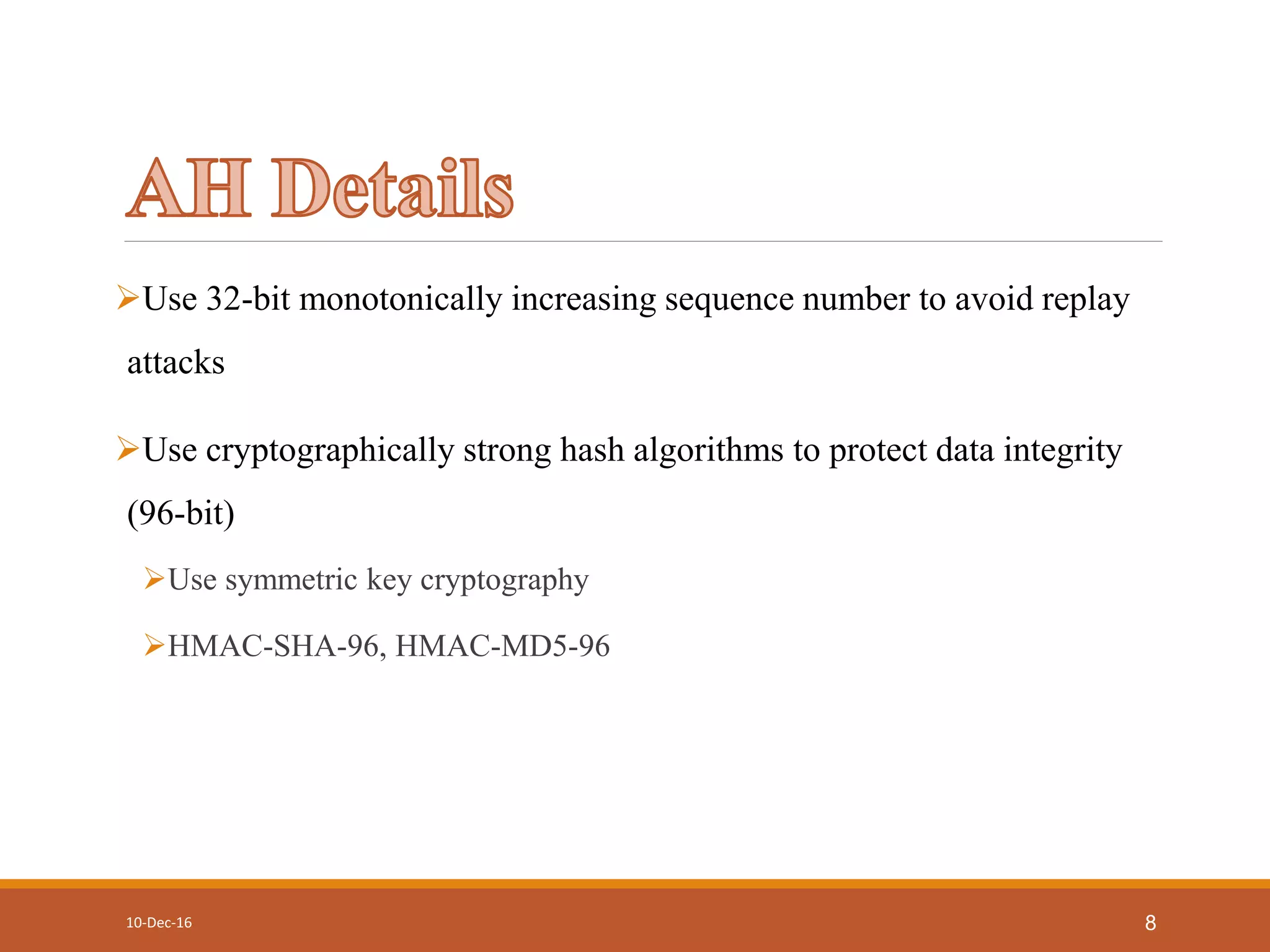
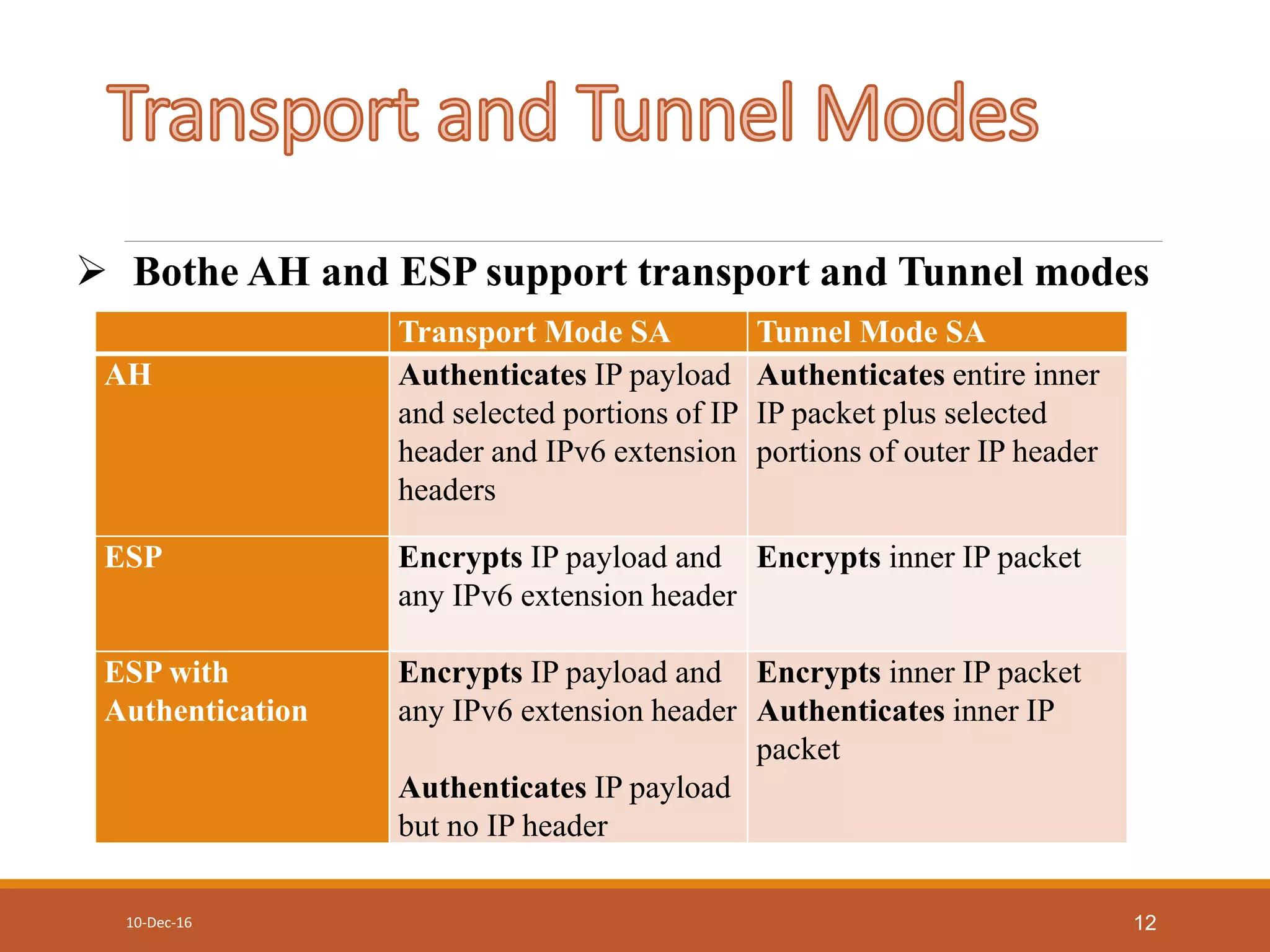
This document discusses IP security (IPSec) protocols. IPSec is used to secure IP communications by authenticating and encrypting IP packets. It provides data integrity, authentication, and confidentiality. IPSec includes protocols like Authentication Header (AH) and Encapsulating Security Payload (ESP) to provide security services like data integrity, data authentication, and confidentiality. It also uses the Internet Key Exchange (IKE) for automated key management and Security Associations (SAs) to identify security parameters for authenticated secure communication.