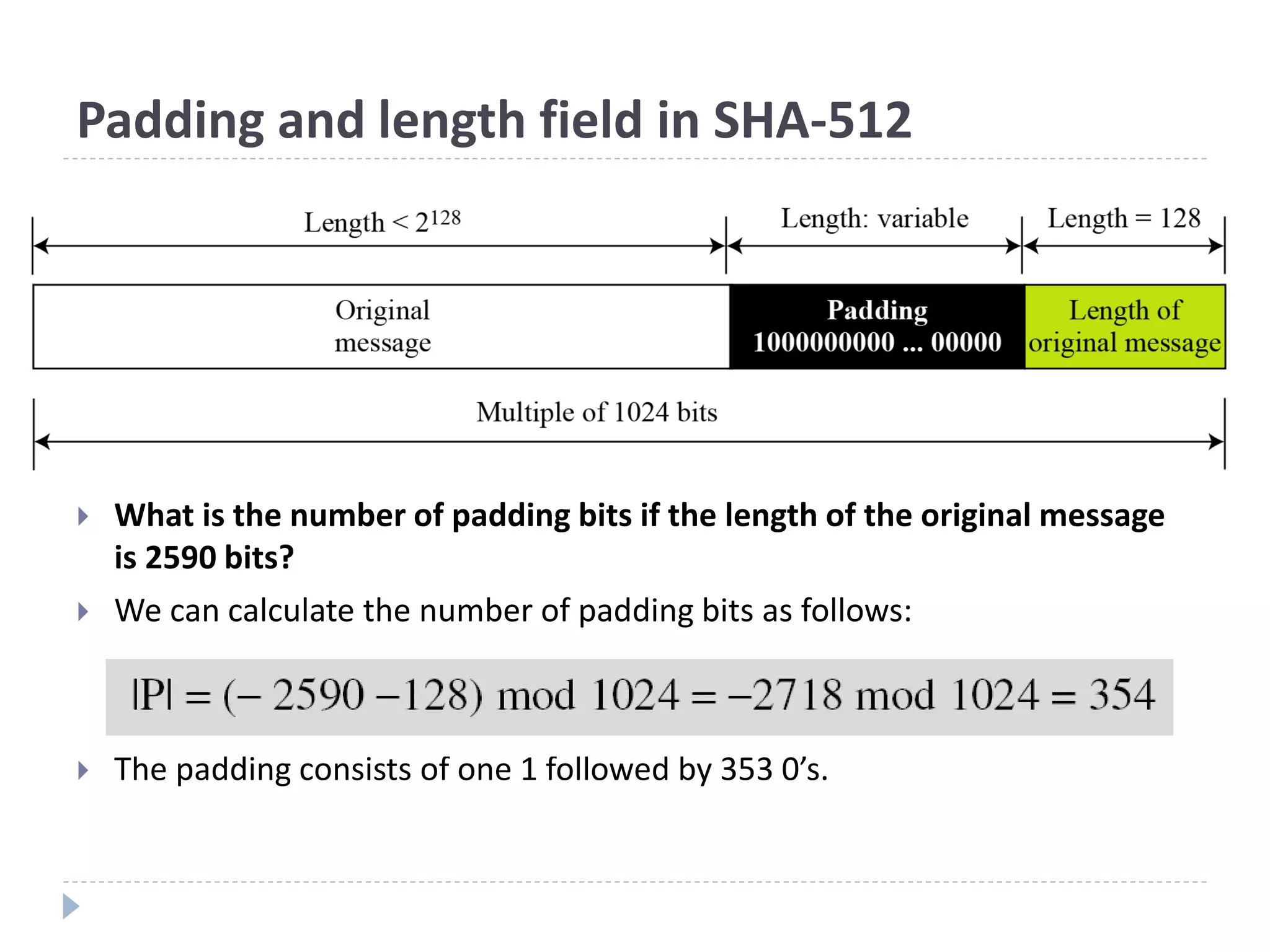
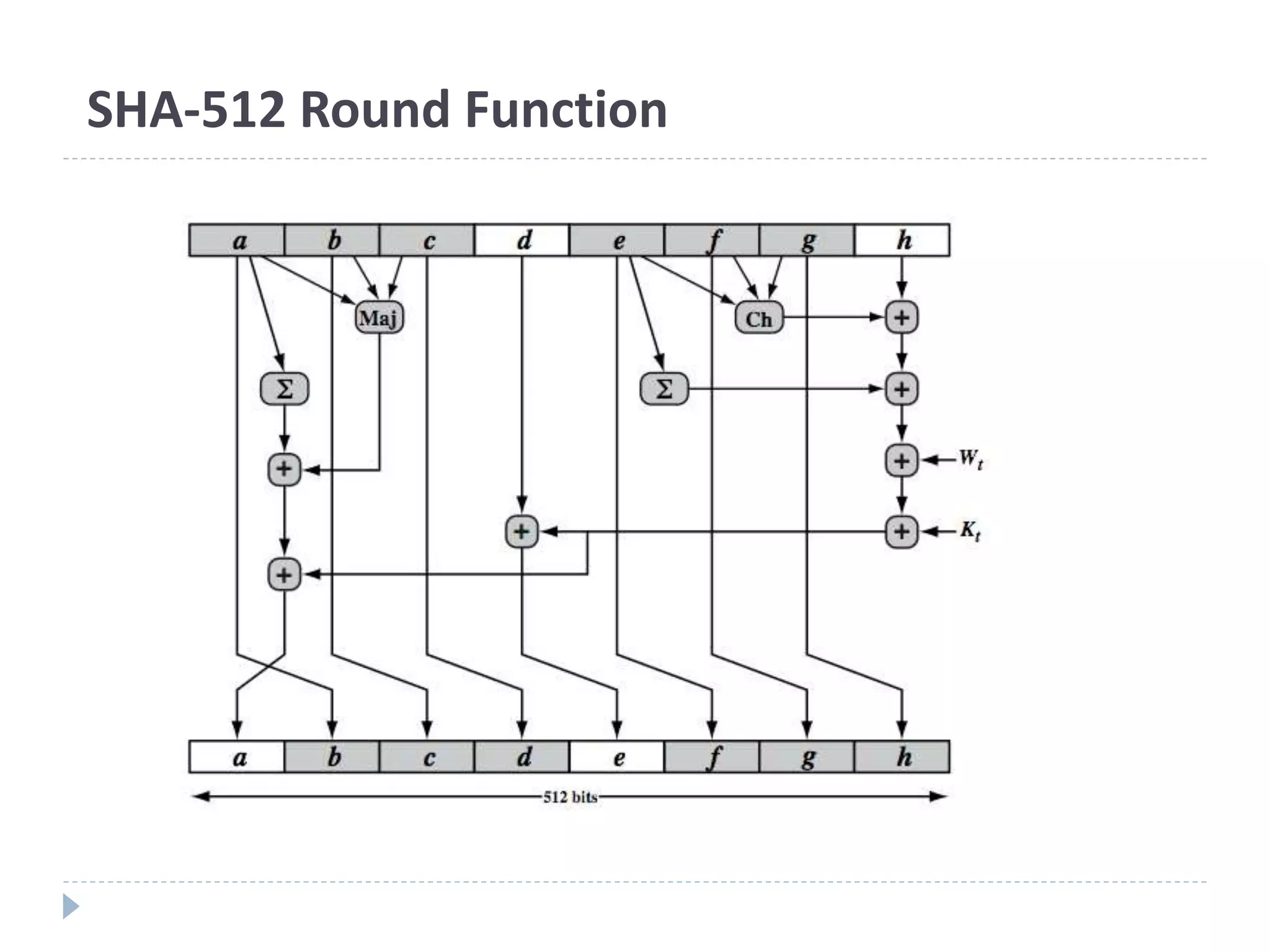
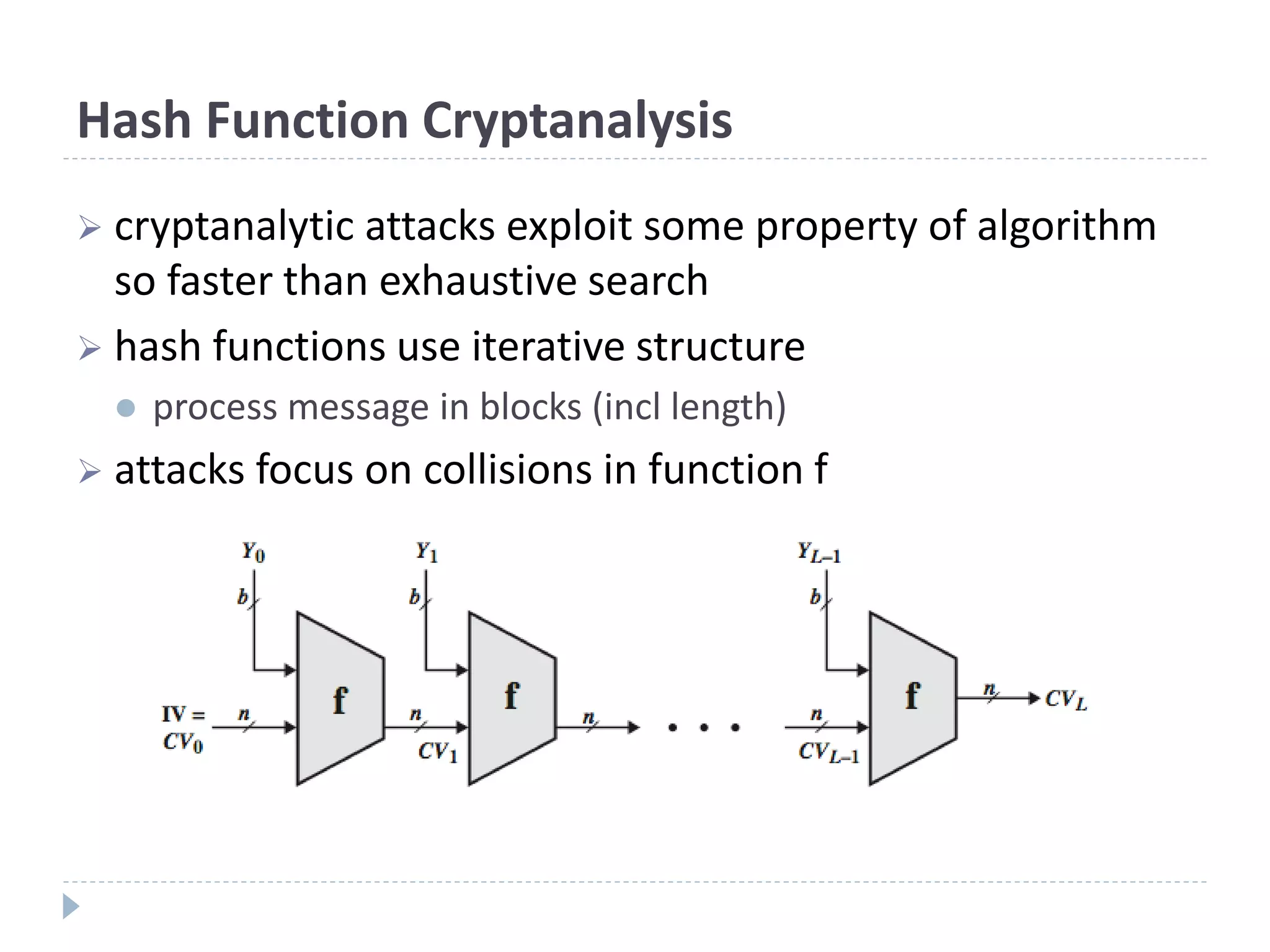
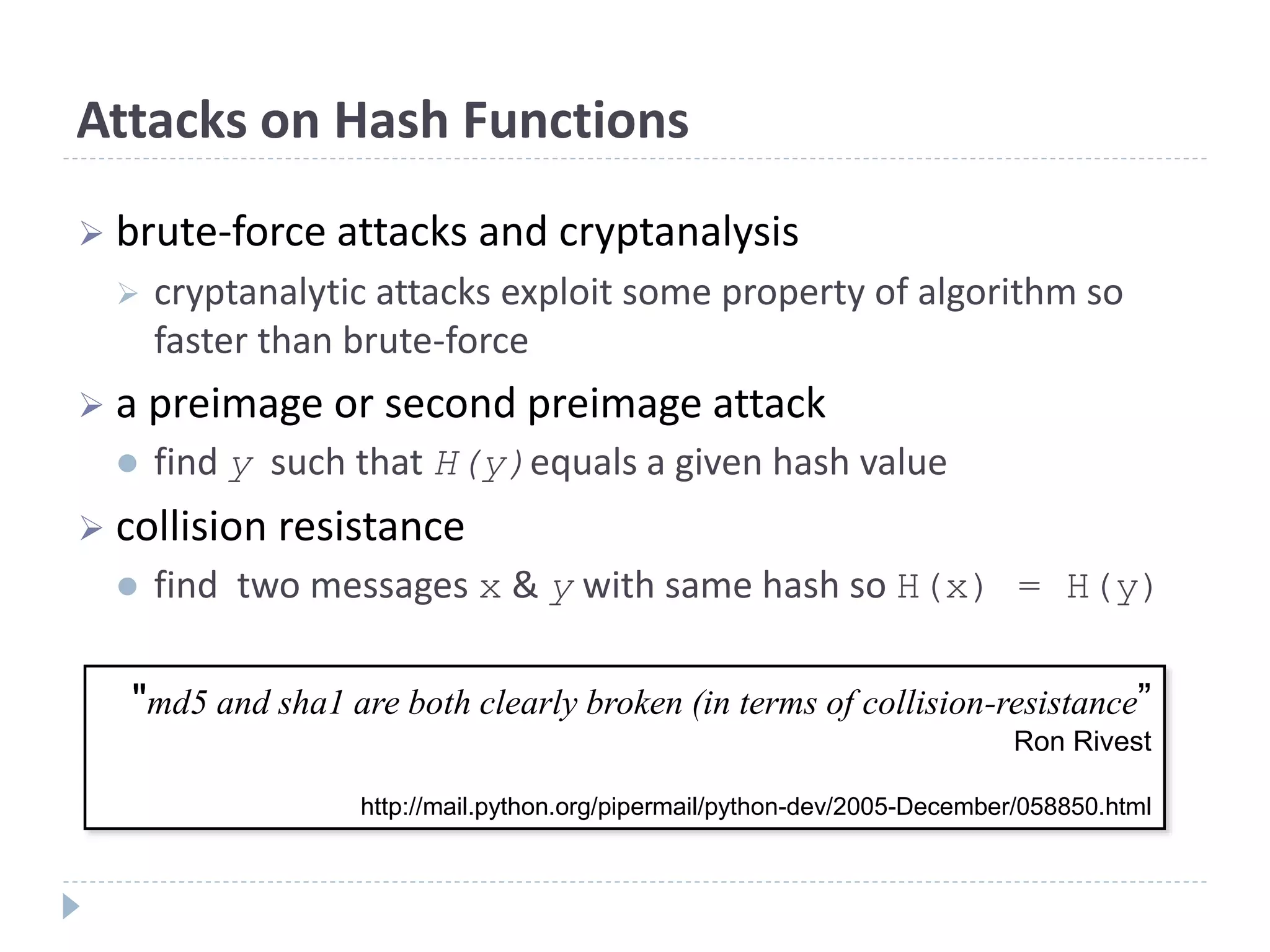
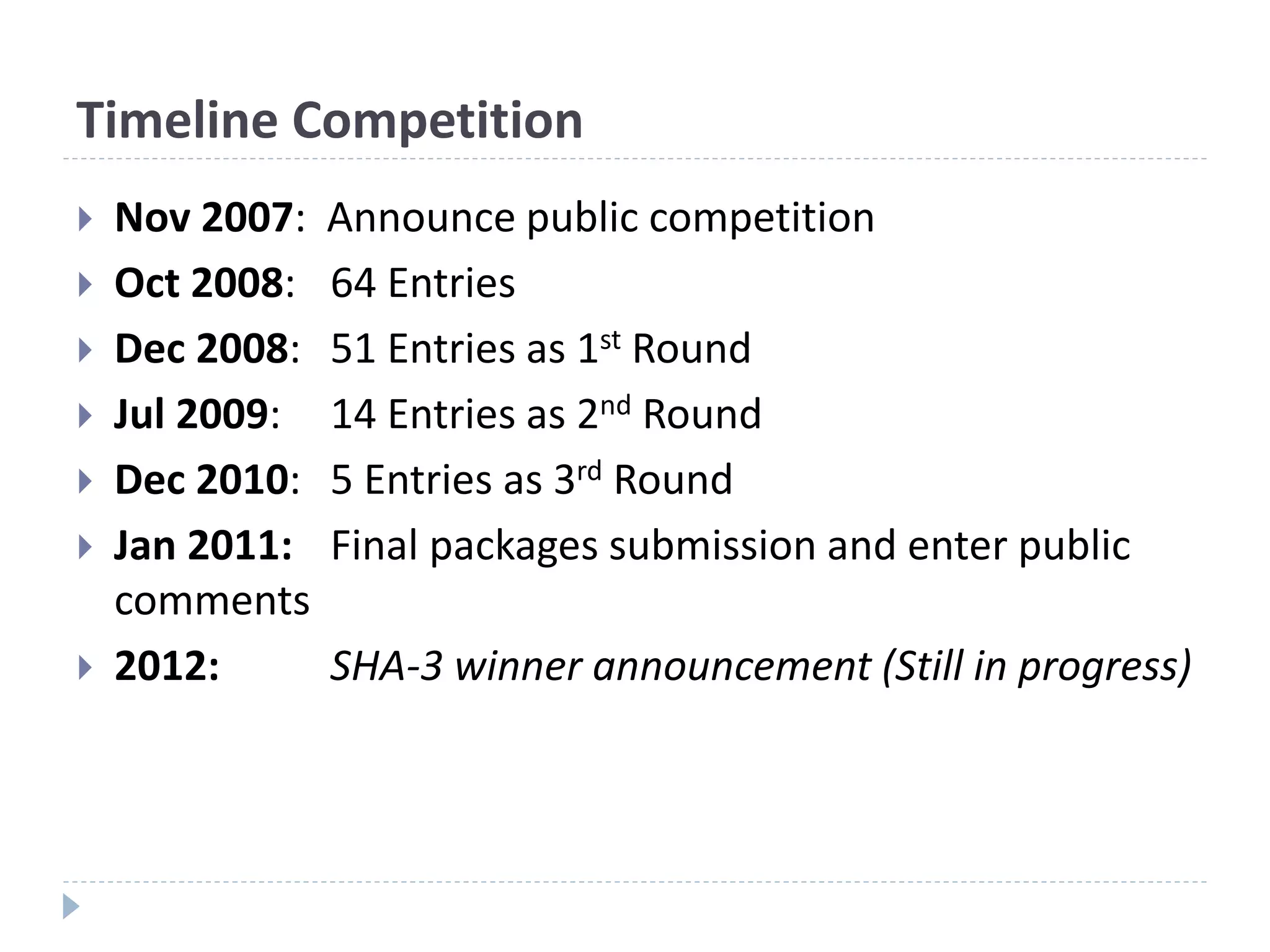
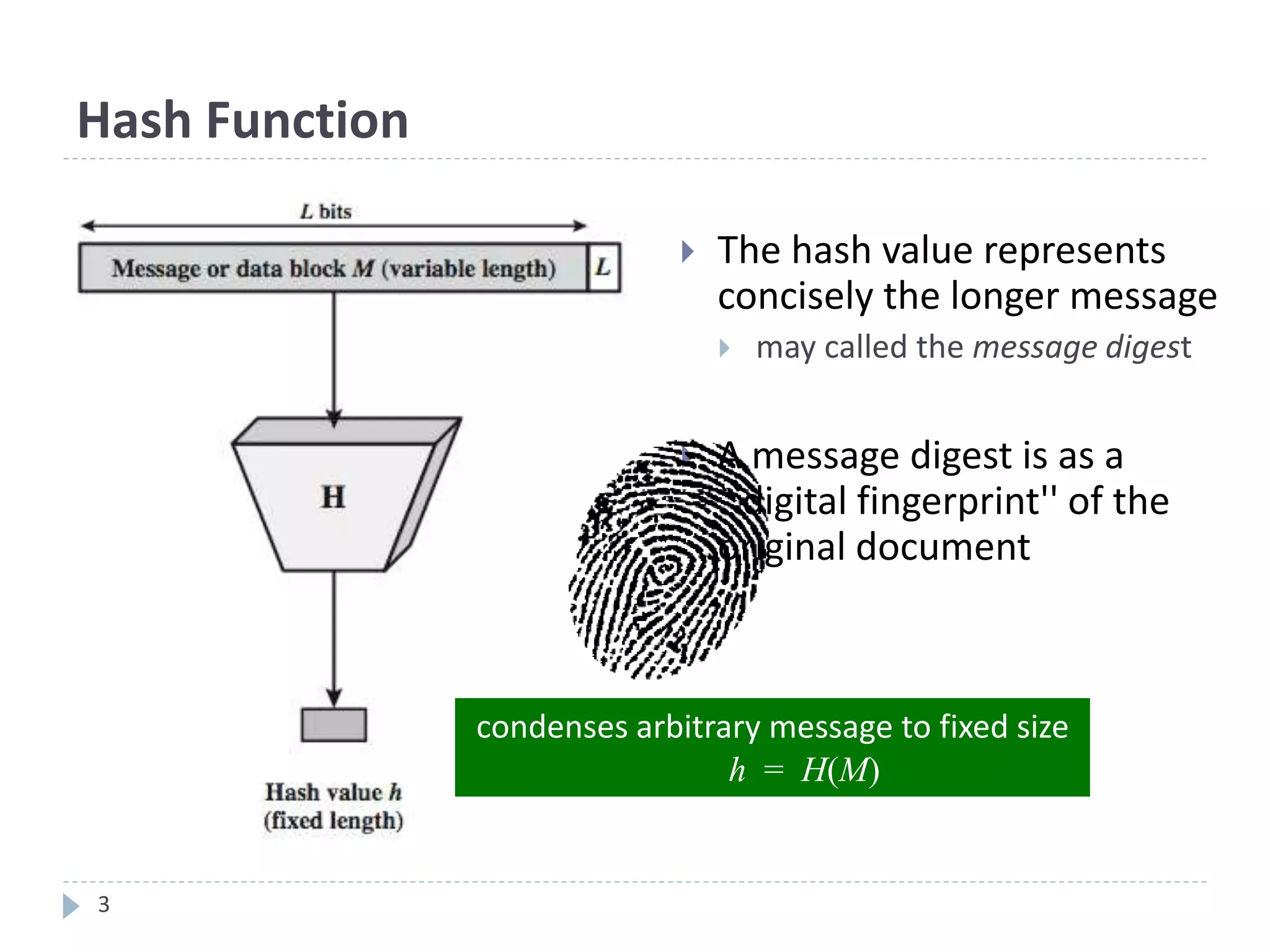
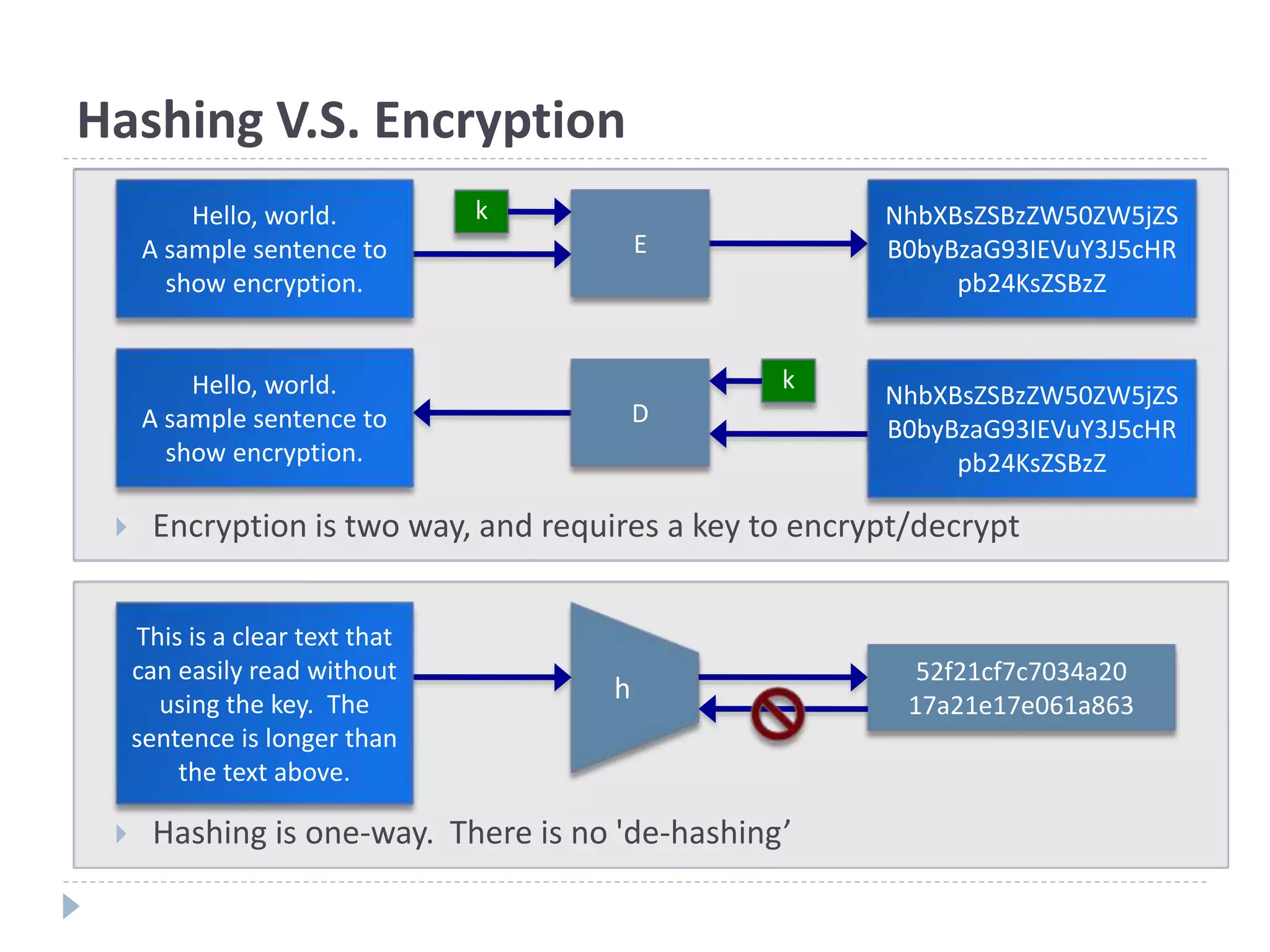
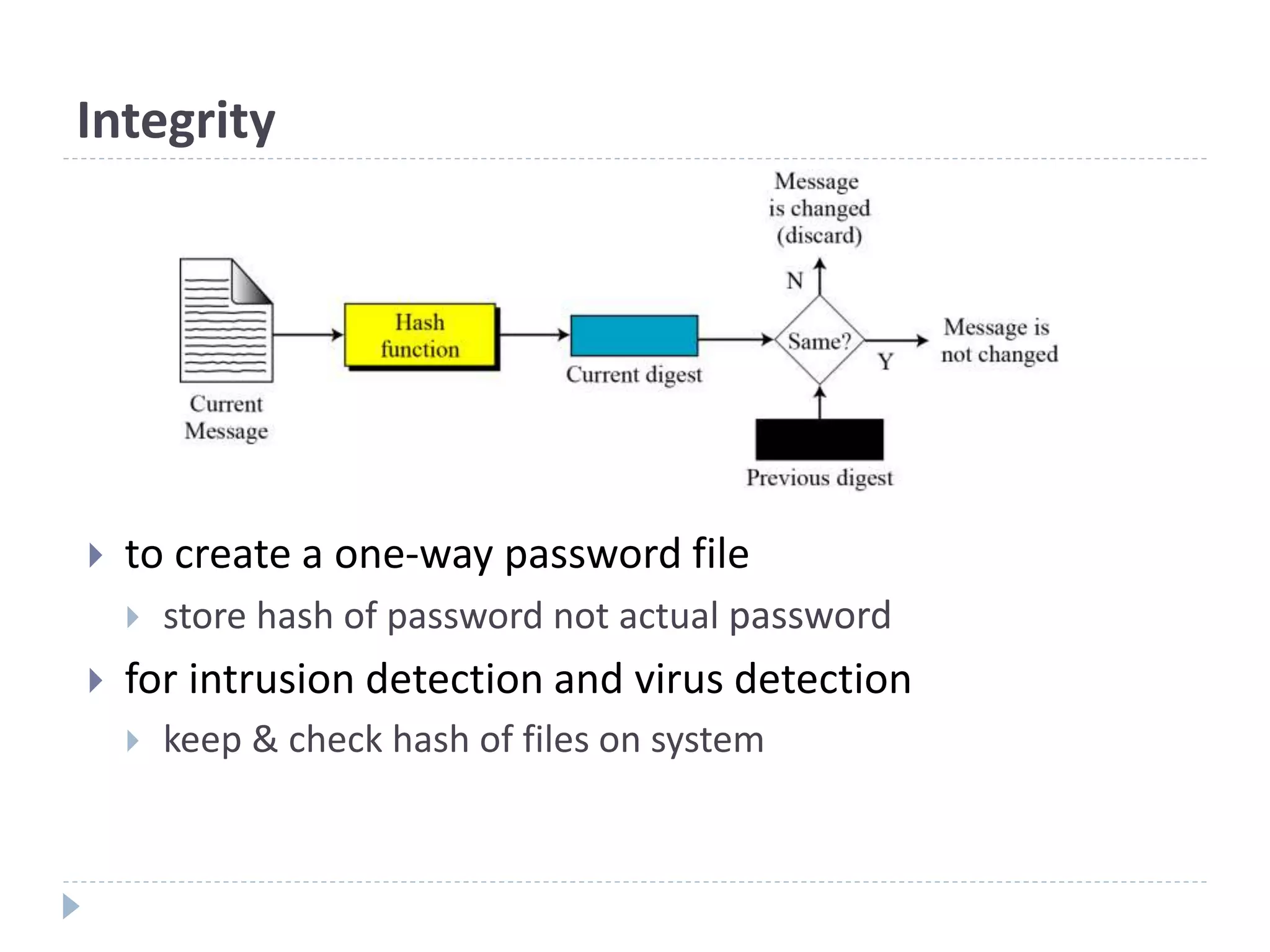
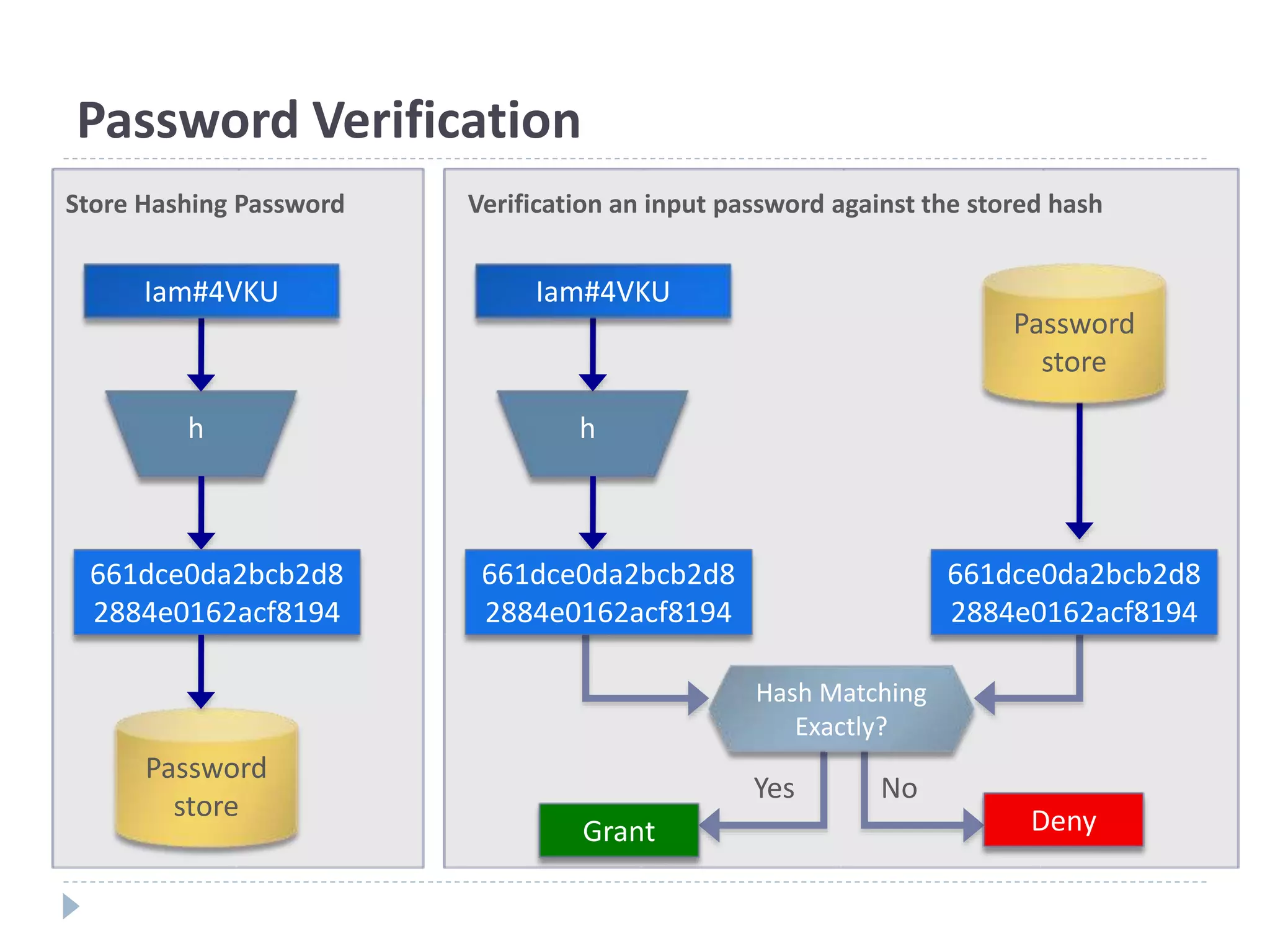
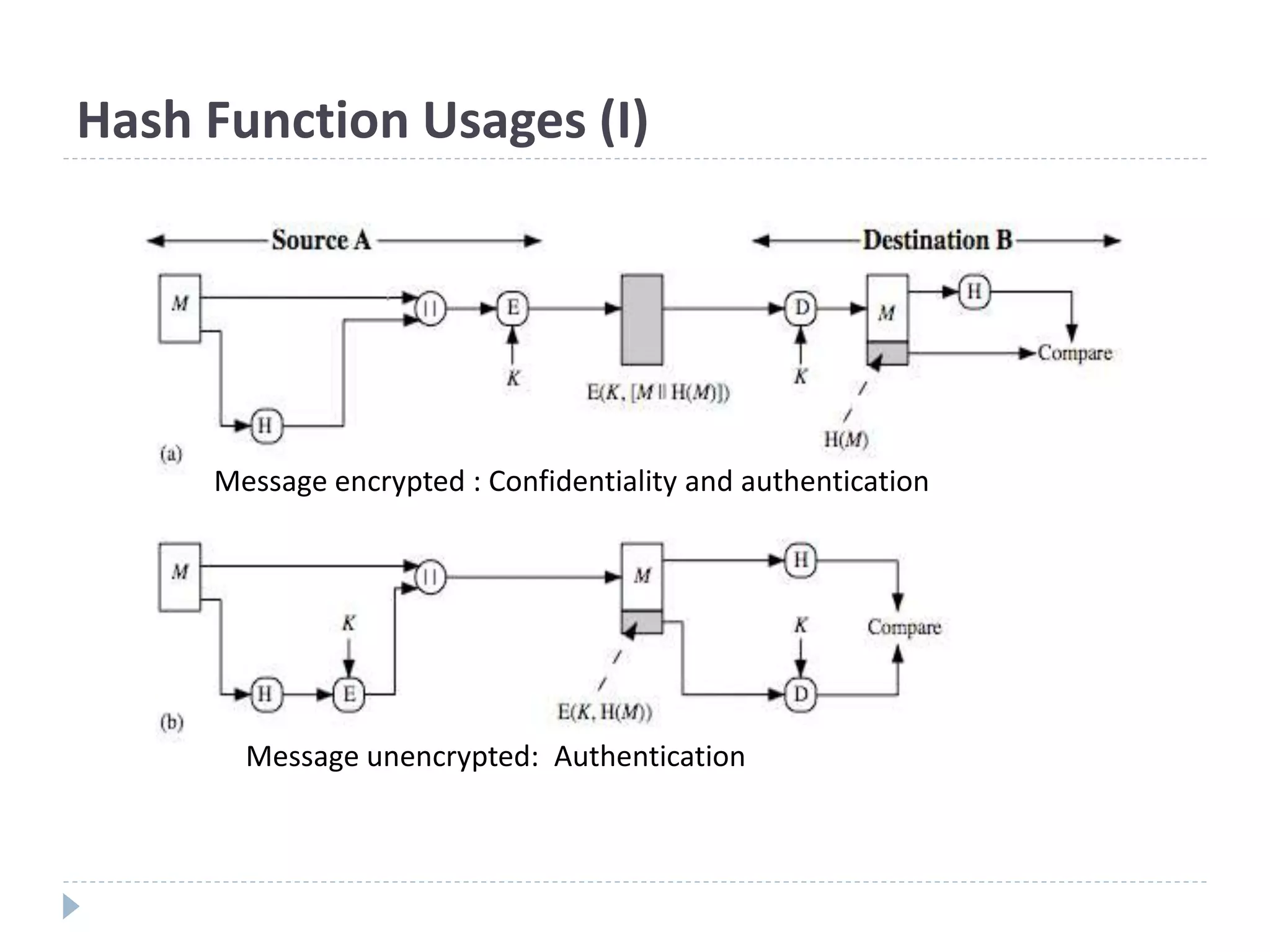
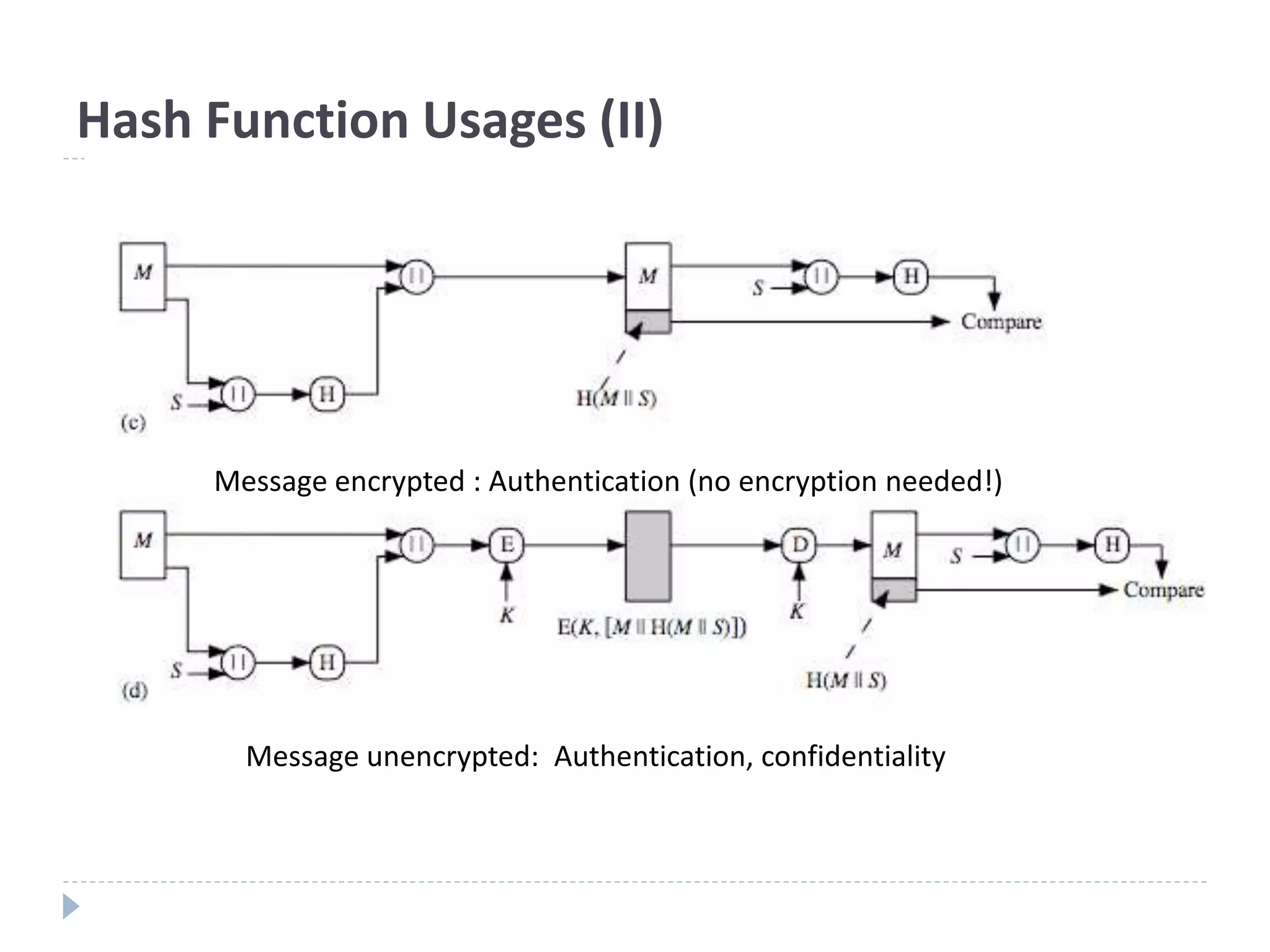
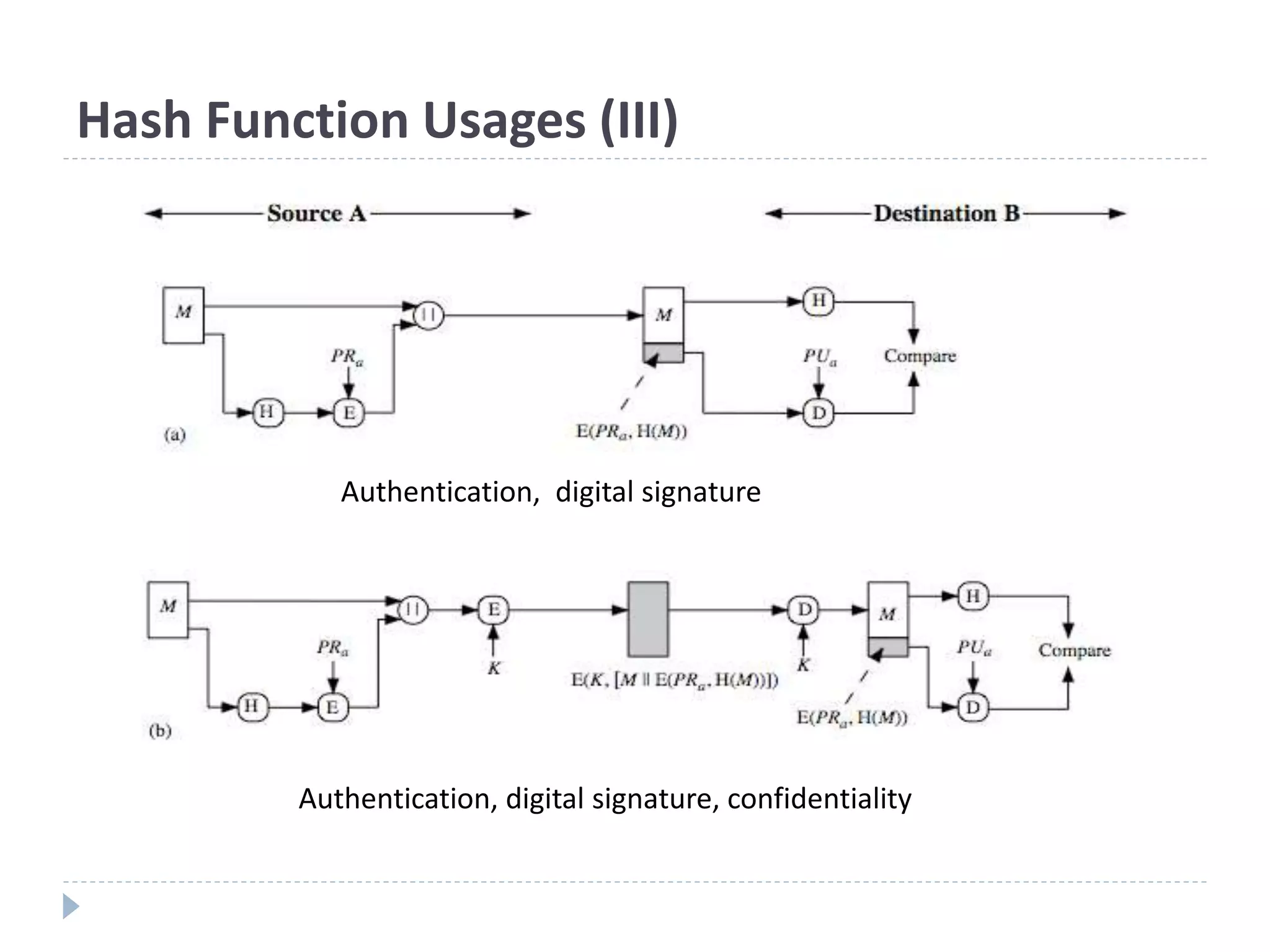
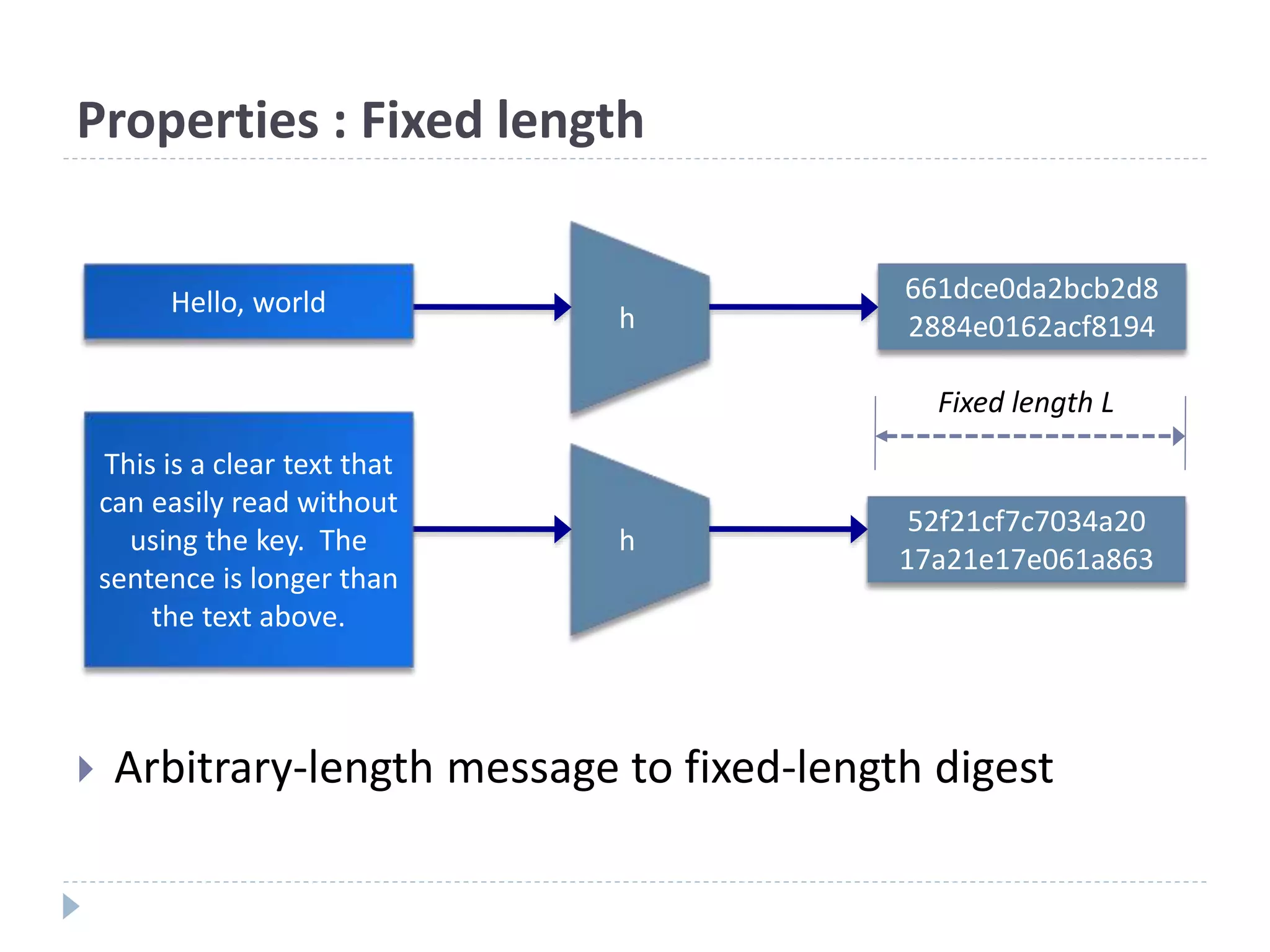
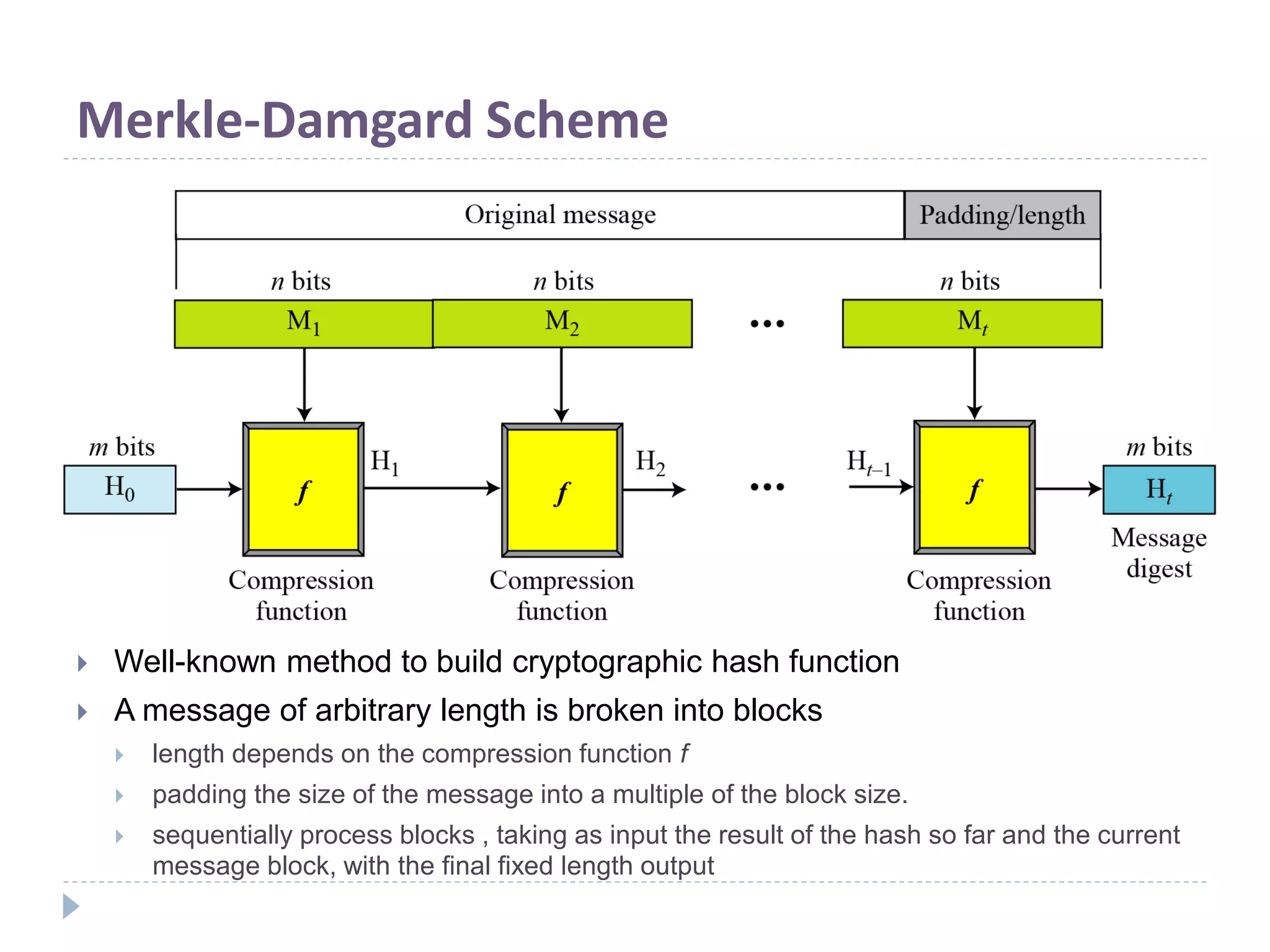
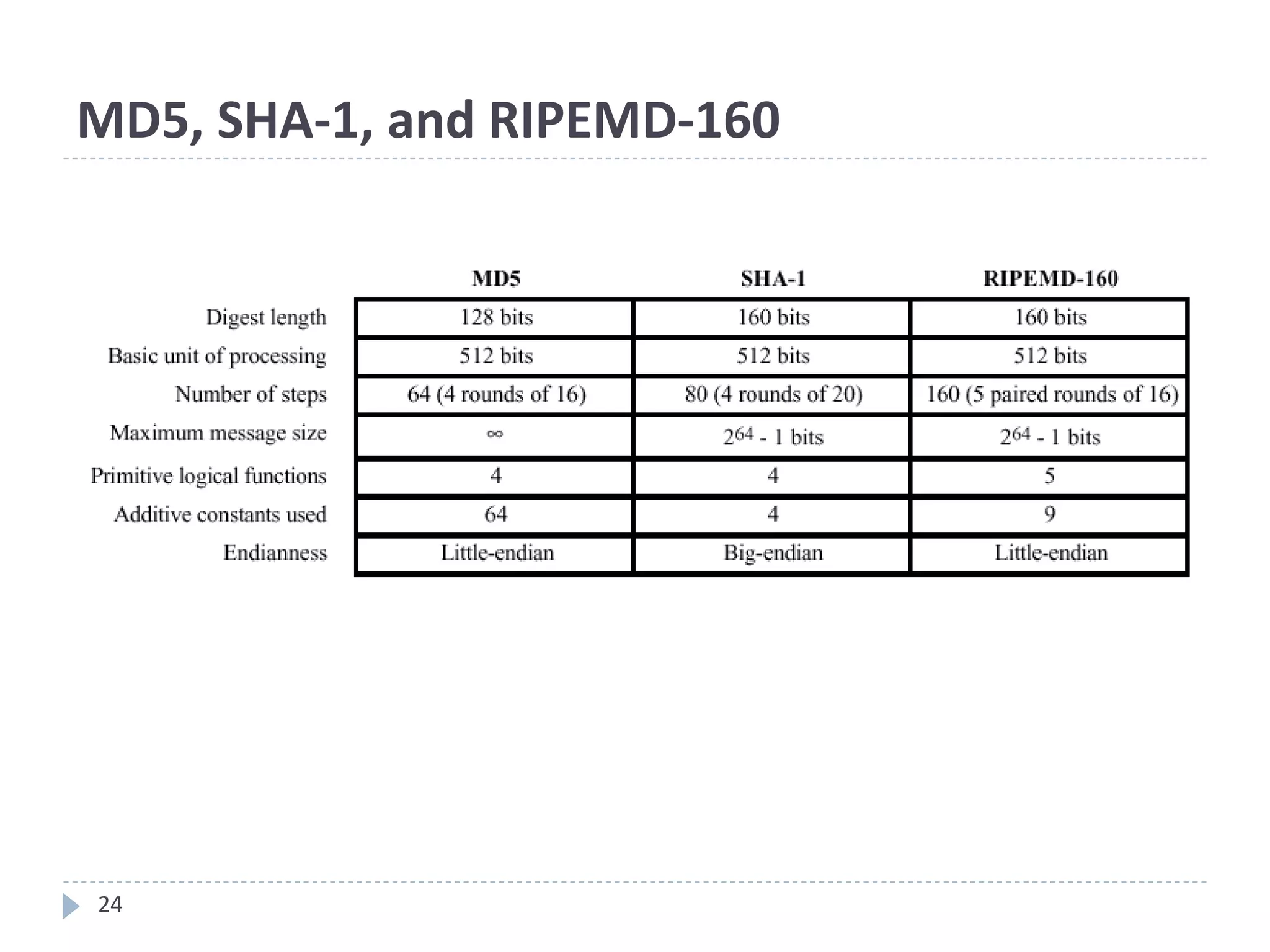
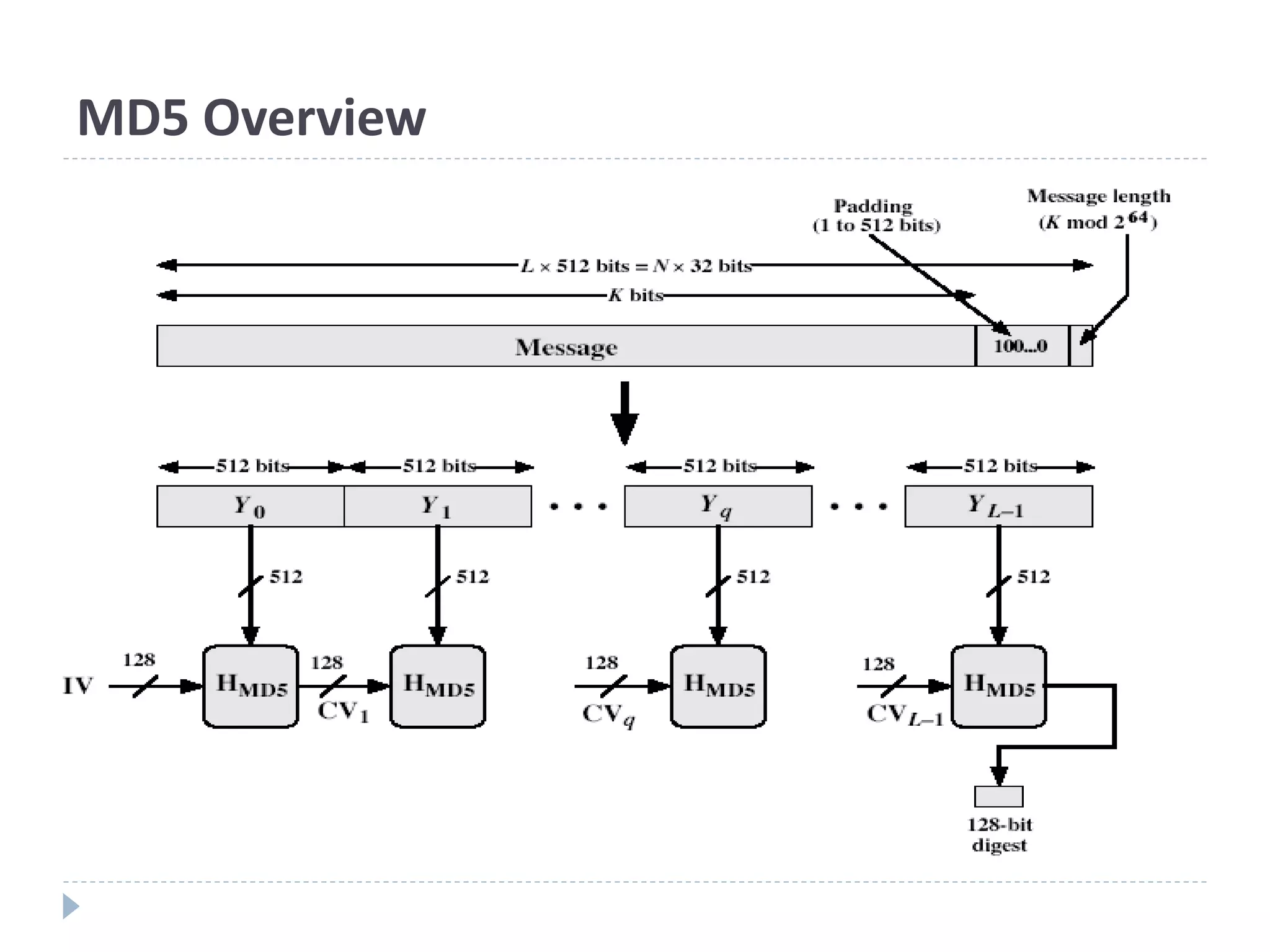
This document discusses cryptographic hash functions. It provides an overview of hash functions and their properties like producing a fixed-length digest from an arbitrary-length message. It describes common hash functions like MD5, SHA-1 and SHA-2 and their structures. It also discusses attacks on hash functions and the need for a new secure hash standard to replace insecure functions like MD5 and the soon-to-be insecure SHA-1, leading to the NIST SHA-3 competition to select a new standard.



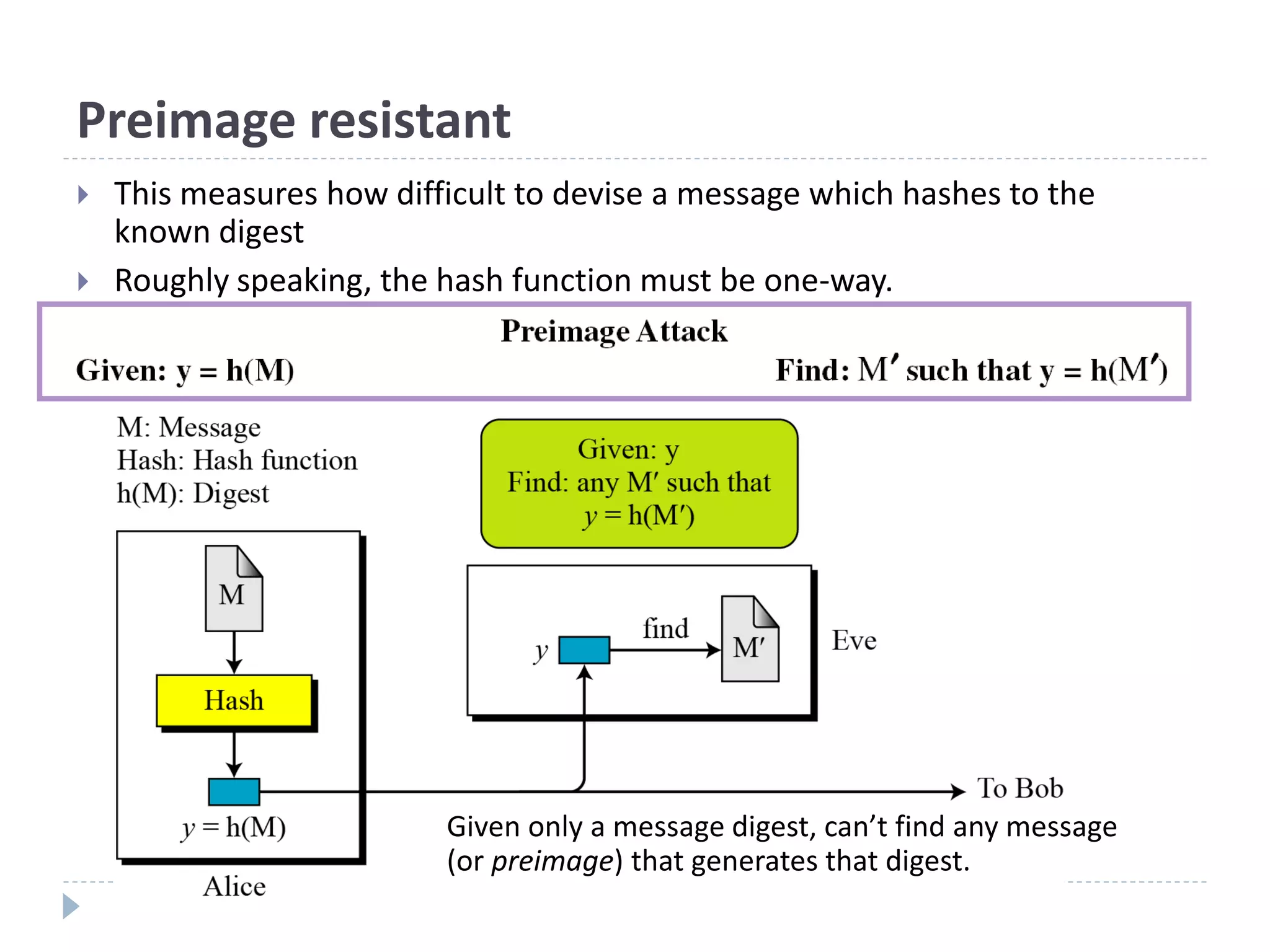
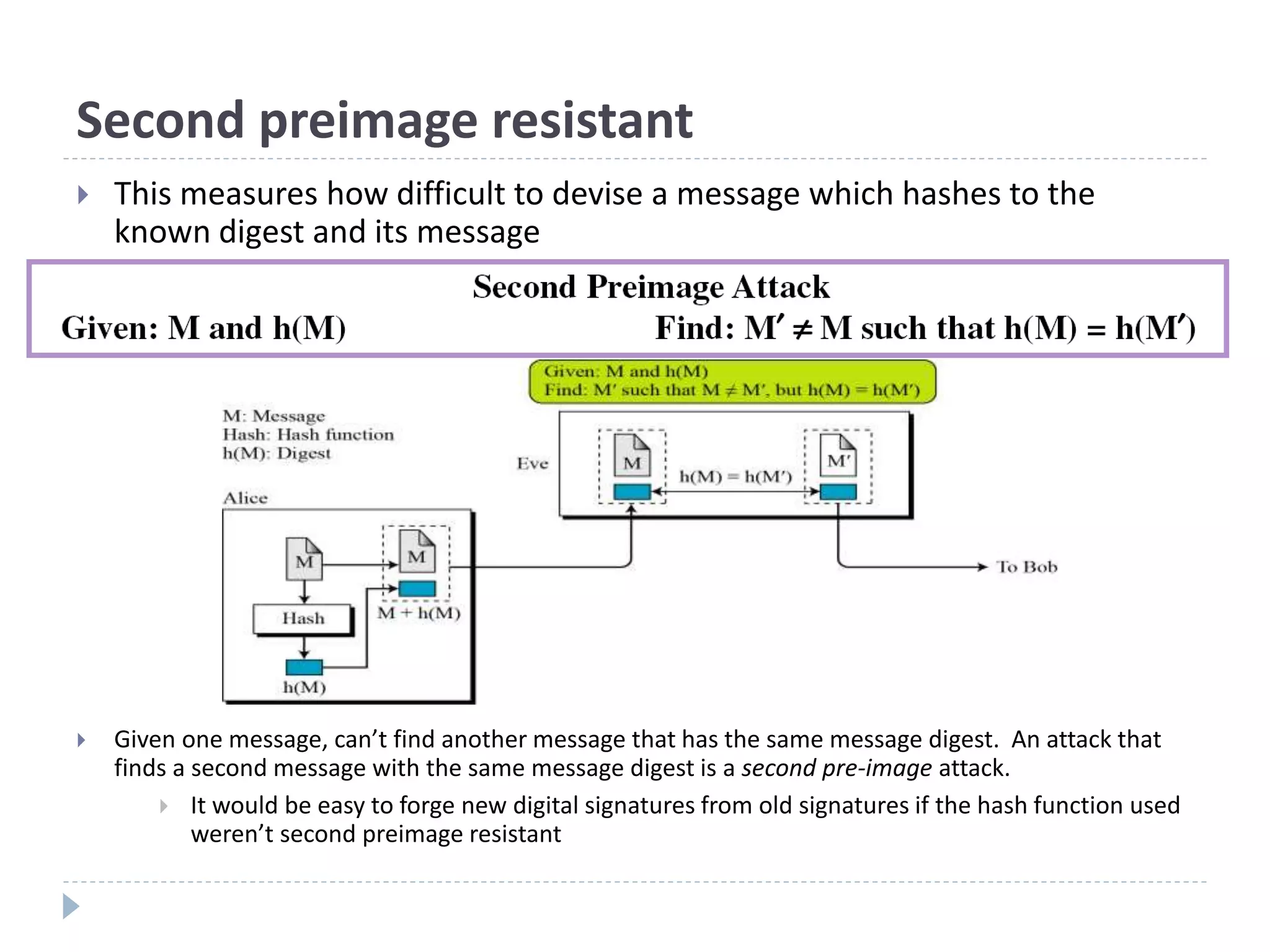
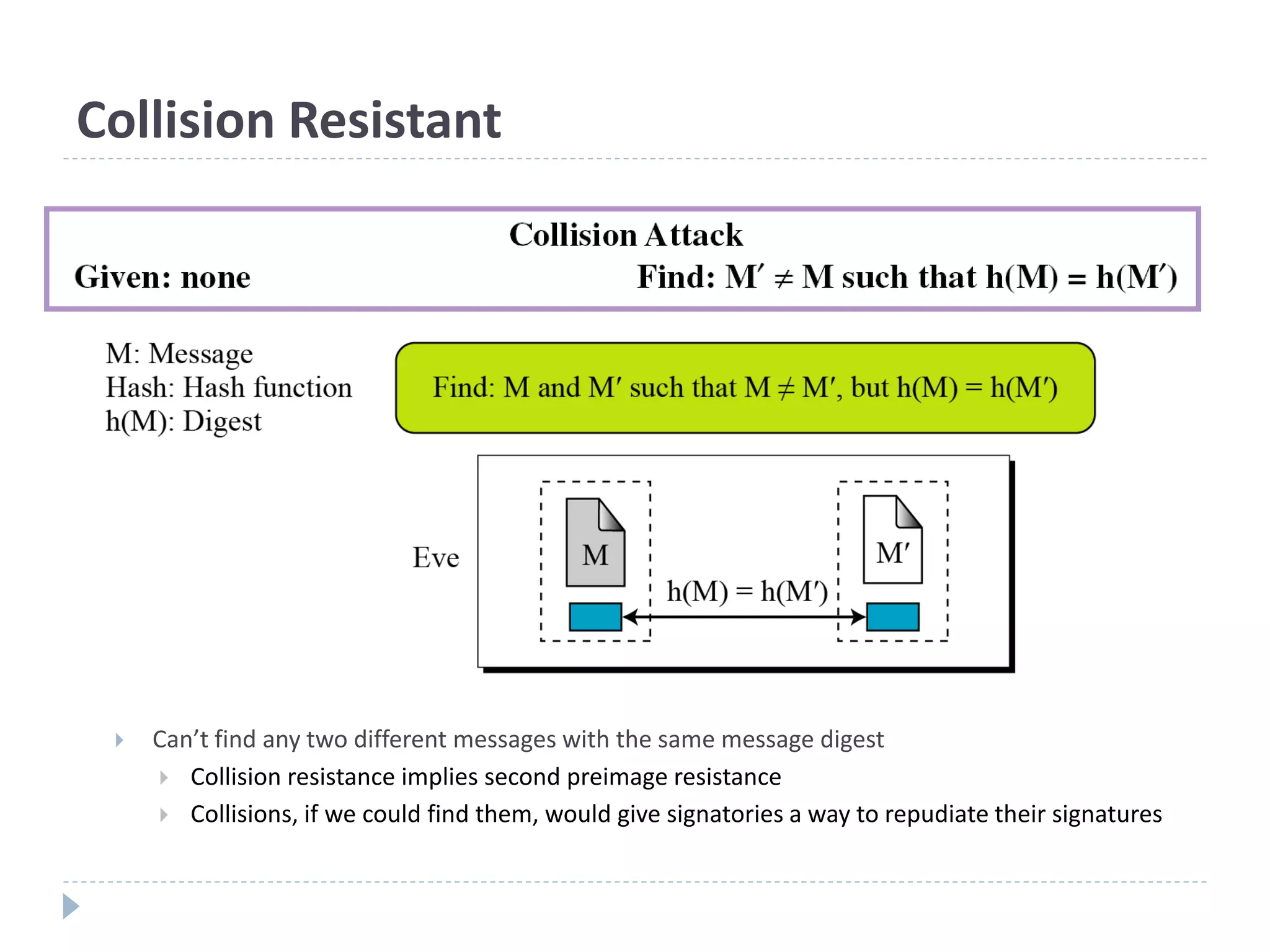


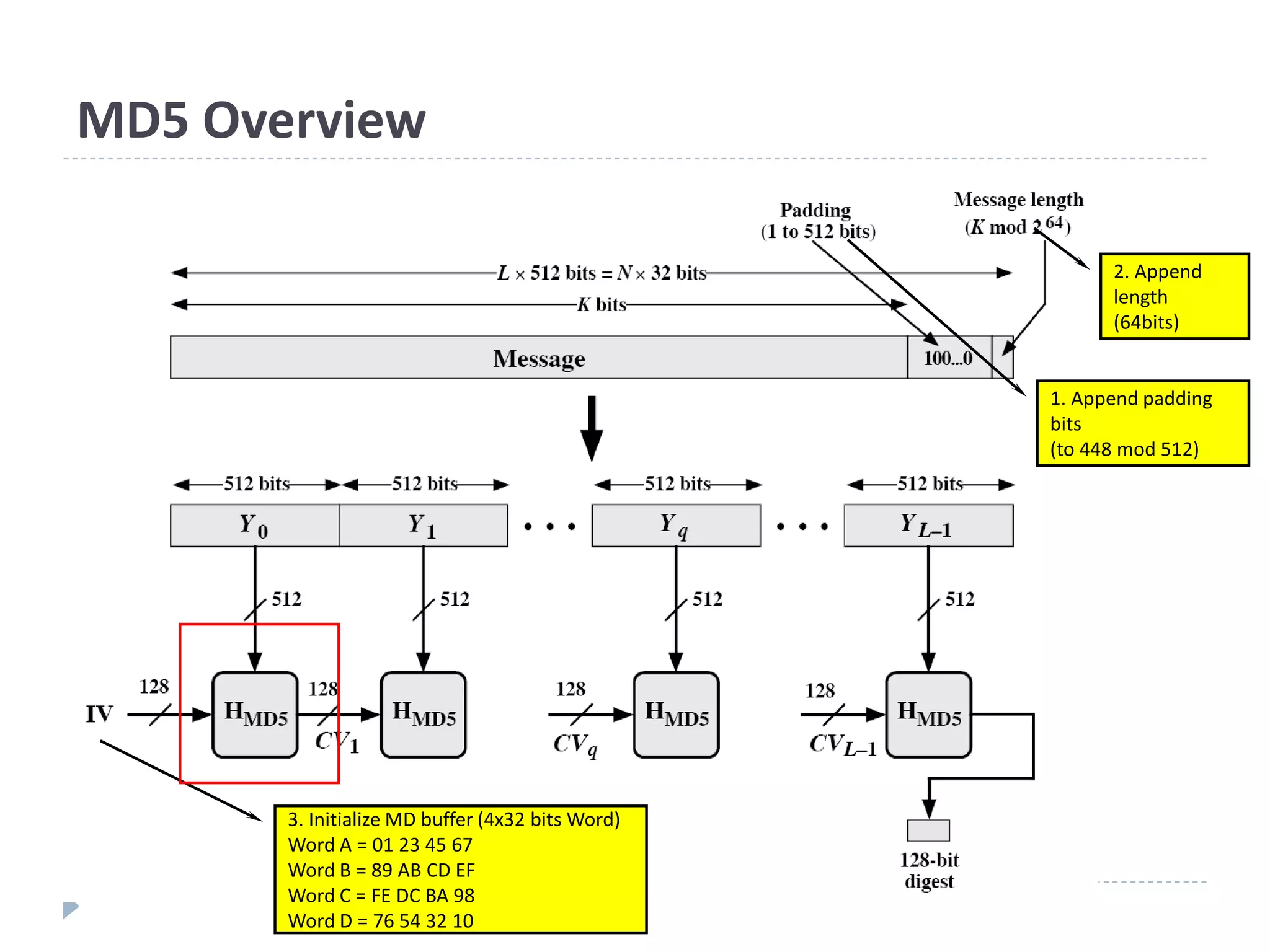
![Hash Algorithm Design – MD5
16 steps
Constructed from sine function
X[k] = M [q*16+k] (32 bit)](https://image.slidesharecdn.com/01204427-hashcrypto1-220323034522/75/01204427-Hash_Crypto-1-ppt-29-2048.jpg)
![The ith 32-bit word in matrix T, constructed from the sine function
M [q*16+k] = the kth 32-bit word from the qth 512-bit block of the msg
Single step](https://image.slidesharecdn.com/01204427-hashcrypto1-220323034522/75/01204427-Hash_Crypto-1-ppt-30-2048.jpg)