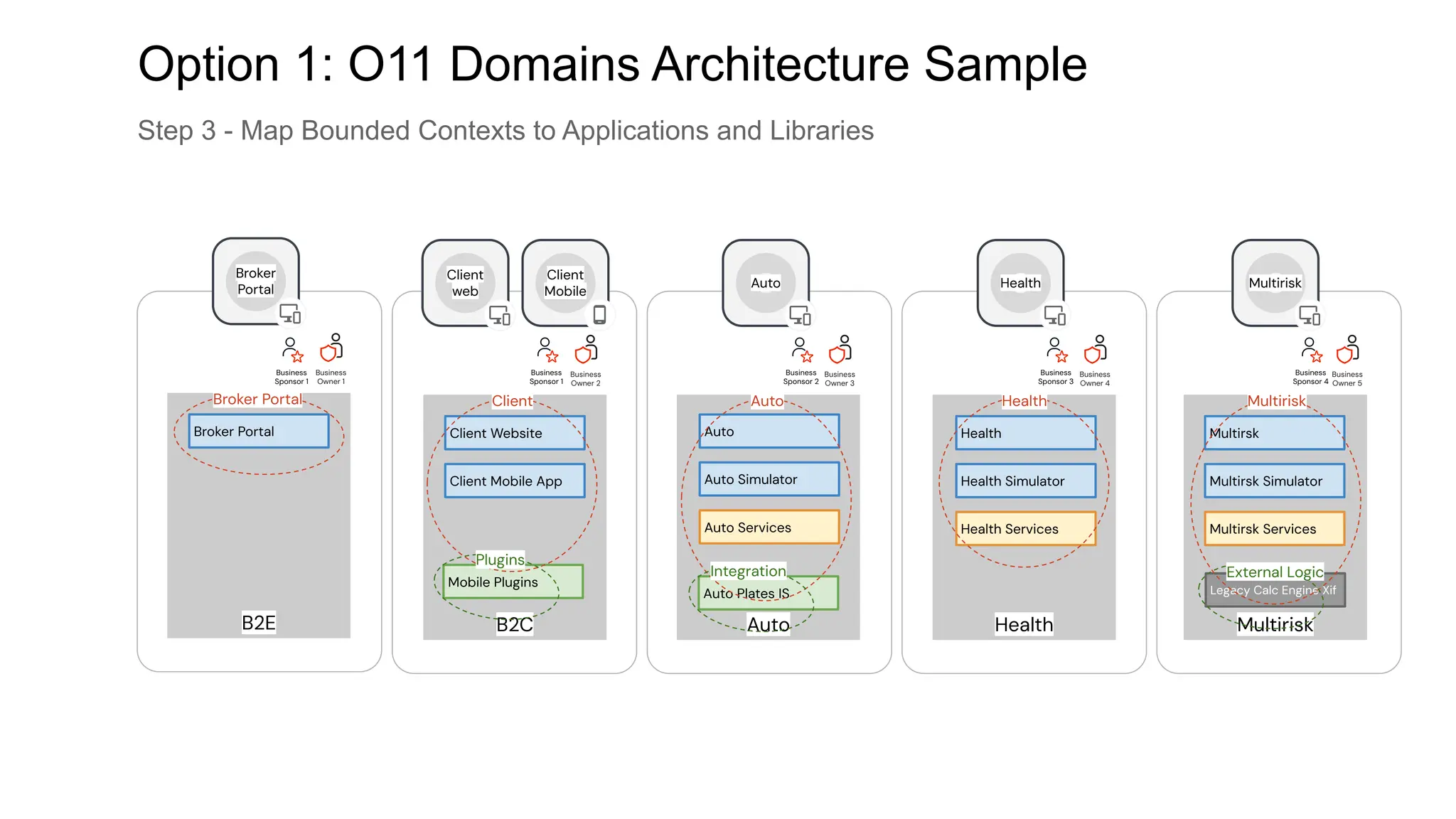
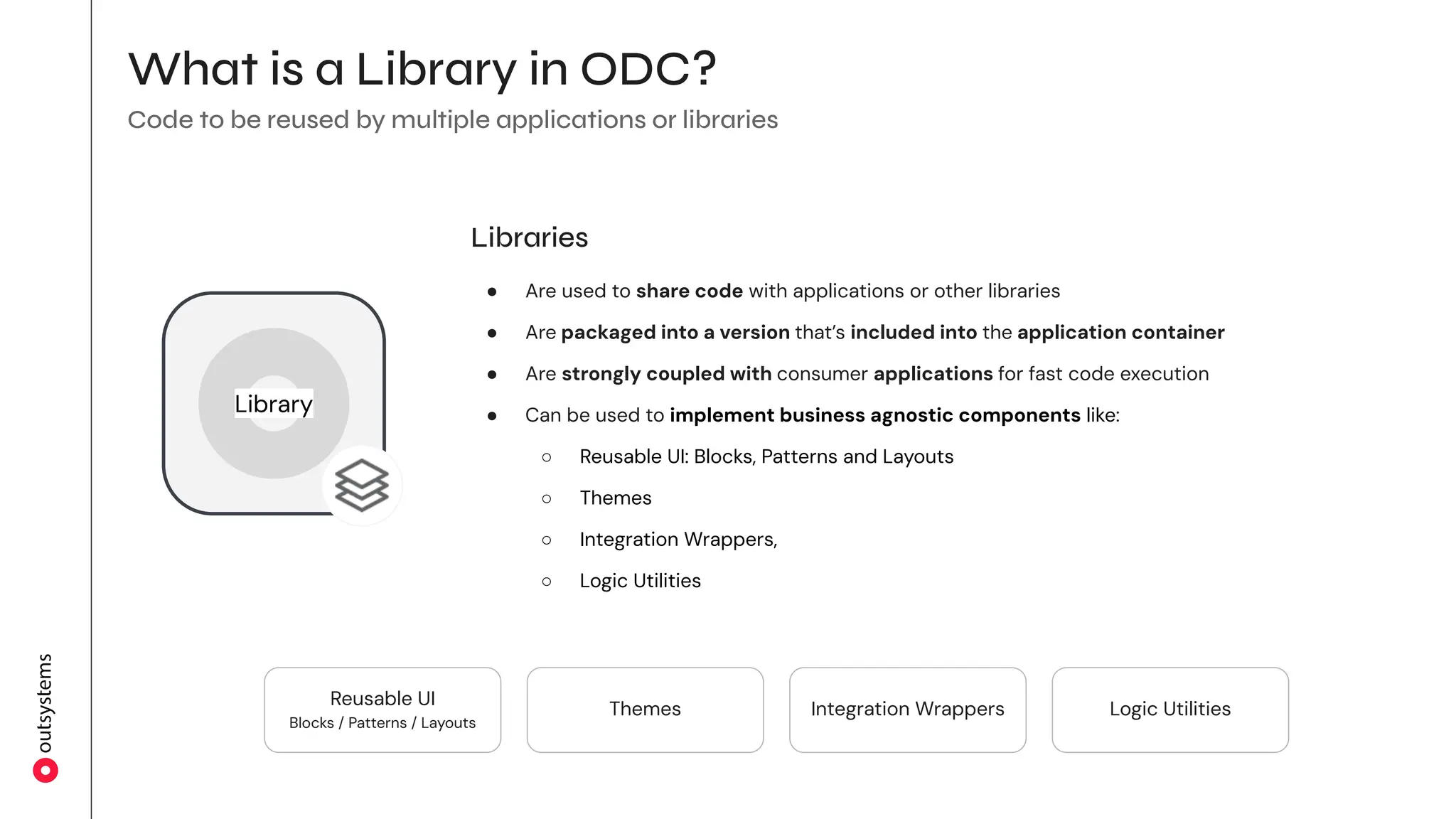
The document outlines the architecture and trade-offs of an internal system, focusing on the concepts of applications, libraries, and their interactions. It discusses the importance of decoupling parts of the system for agility while balancing team autonomy and integration concerns. Additionally, it emphasizes designing applications and libraries that encapsulate business logic, UI, and data, promoting reusability and maintaining independent life cycles.