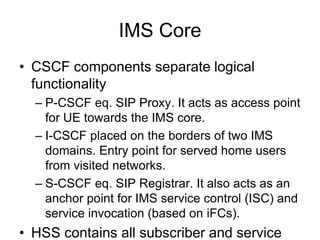
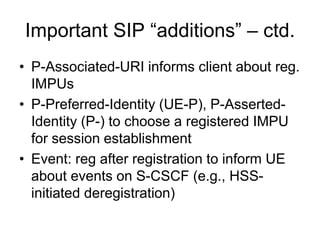
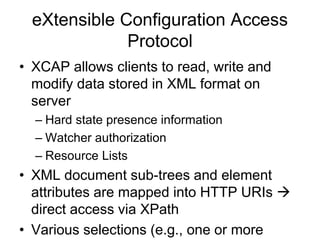
The document provides an overview of IMS (IP Multimedia Subsystem) architecture, highlighting key components such as CSCF (Call Session Control Function) and HSS (Home Subscriber Server), along with the processes for IMS registration and session establishment. It emphasizes the layered structure of IMS, detailing the interaction between application and service control layers and describing the role of user identities in managing communication services. Additionally, the document covers SIP (Session Initiation Protocol) additions and introduces the Extensible Configuration Access Protocol (XCAP) for data management within the IMS framework.