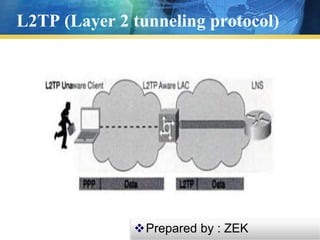
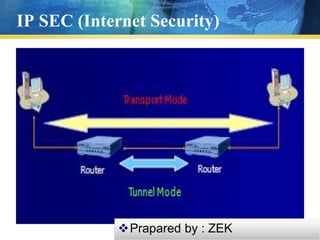
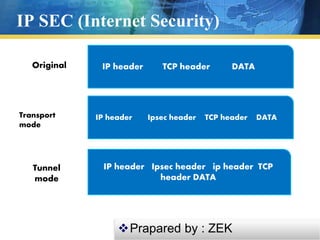
L2TP is a tunneling protocol that is used to support VPNs and does not provide encryption on its own. It relies on encryption protocols like IPsec to provide security. IPsec provides authentication, confidentiality and key management at the IP layer. It uses protocols like AH and ESP to provide integrity, authentication and encryption of IP packets. IPsec can operate in transport mode, encrypting only the payload, or tunnel mode, encrypting the entire IP packet. The combination of L2TP and IPsec is commonly used to secure VPN connections over the internet.