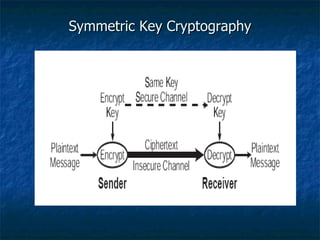
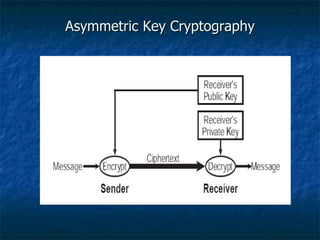
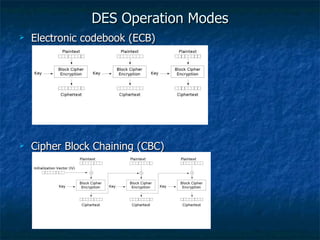
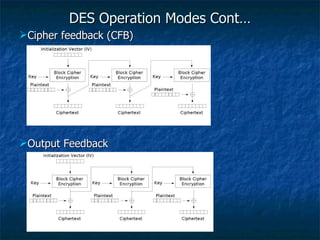
The document discusses cryptography concepts such as encryption algorithms, key management, digital signatures, and cryptanalysis attacks. It covers symmetric and asymmetric cryptographic systems as well as specific algorithms like DES, RSA, and elliptic curve cryptography. The document also examines requirements for secrecy, authenticity and properties of cryptographic systems.