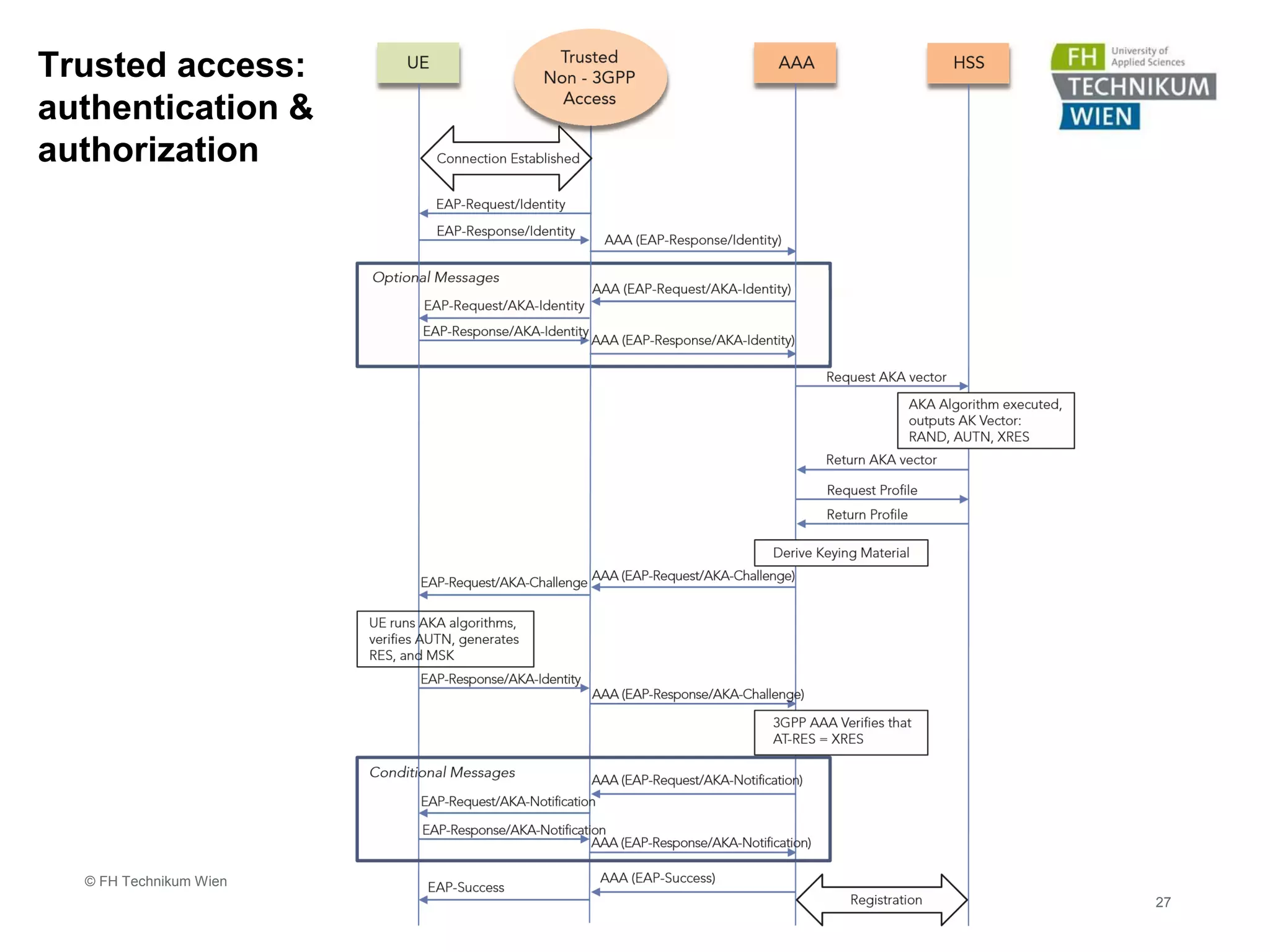
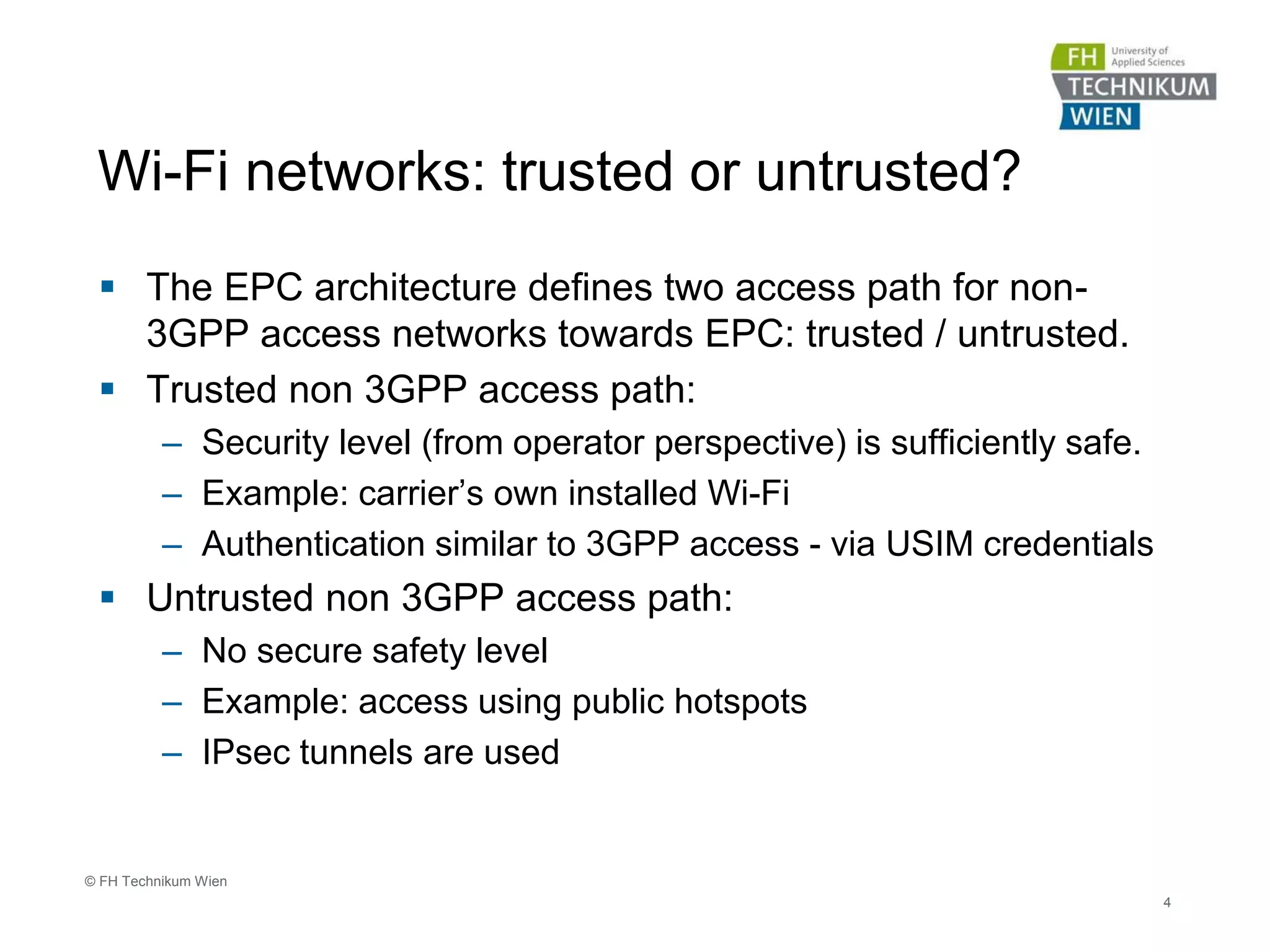
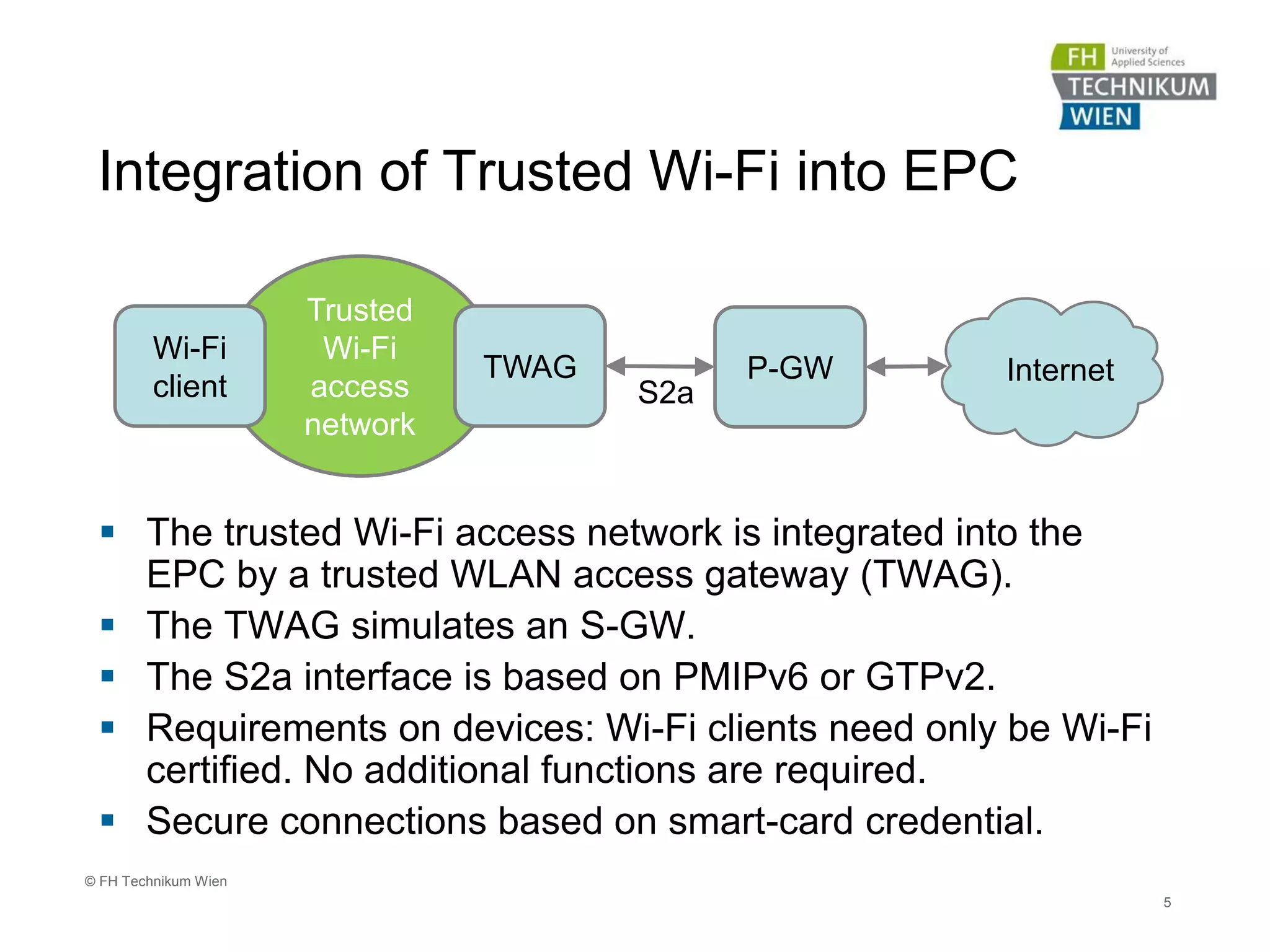
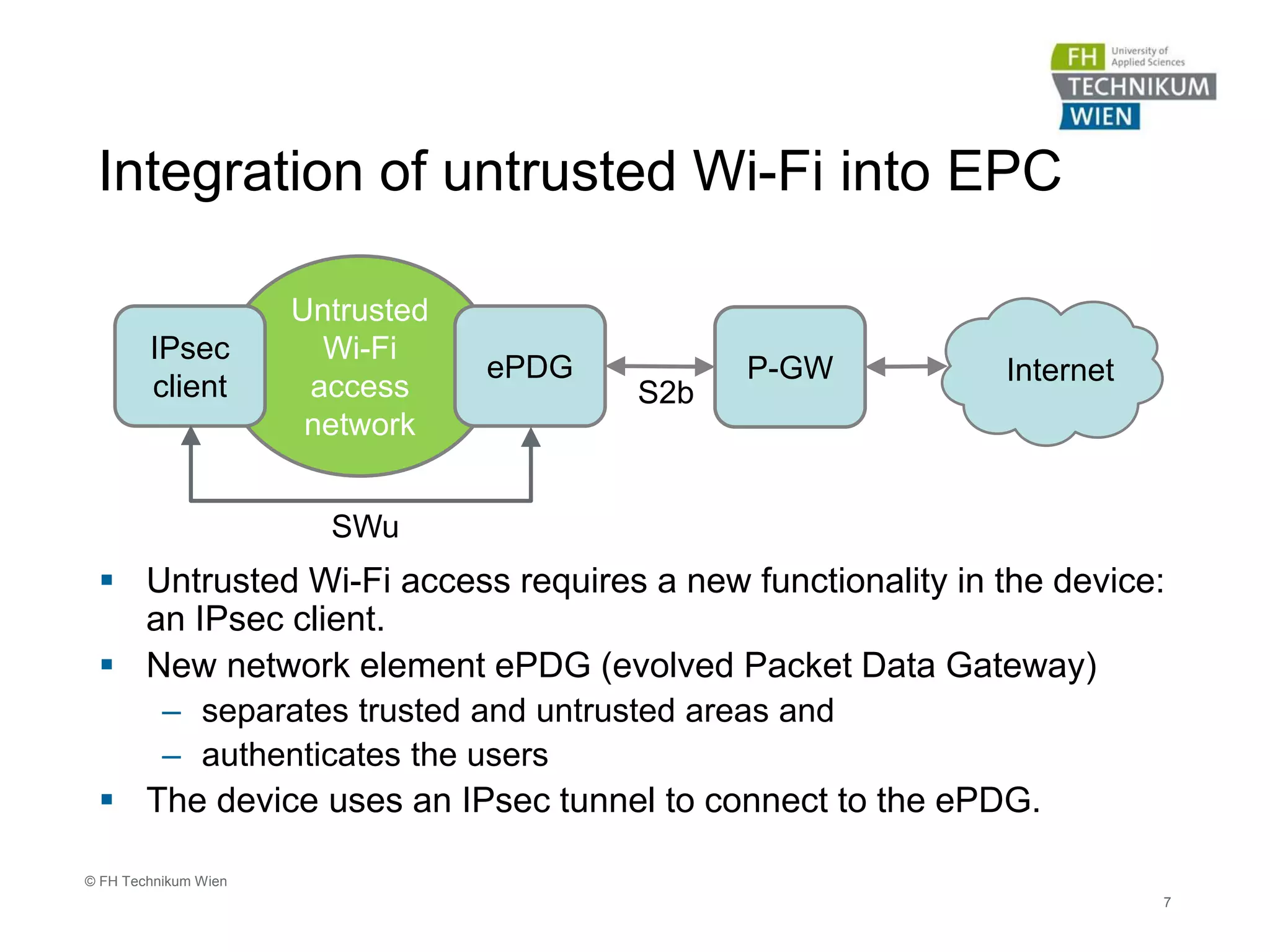
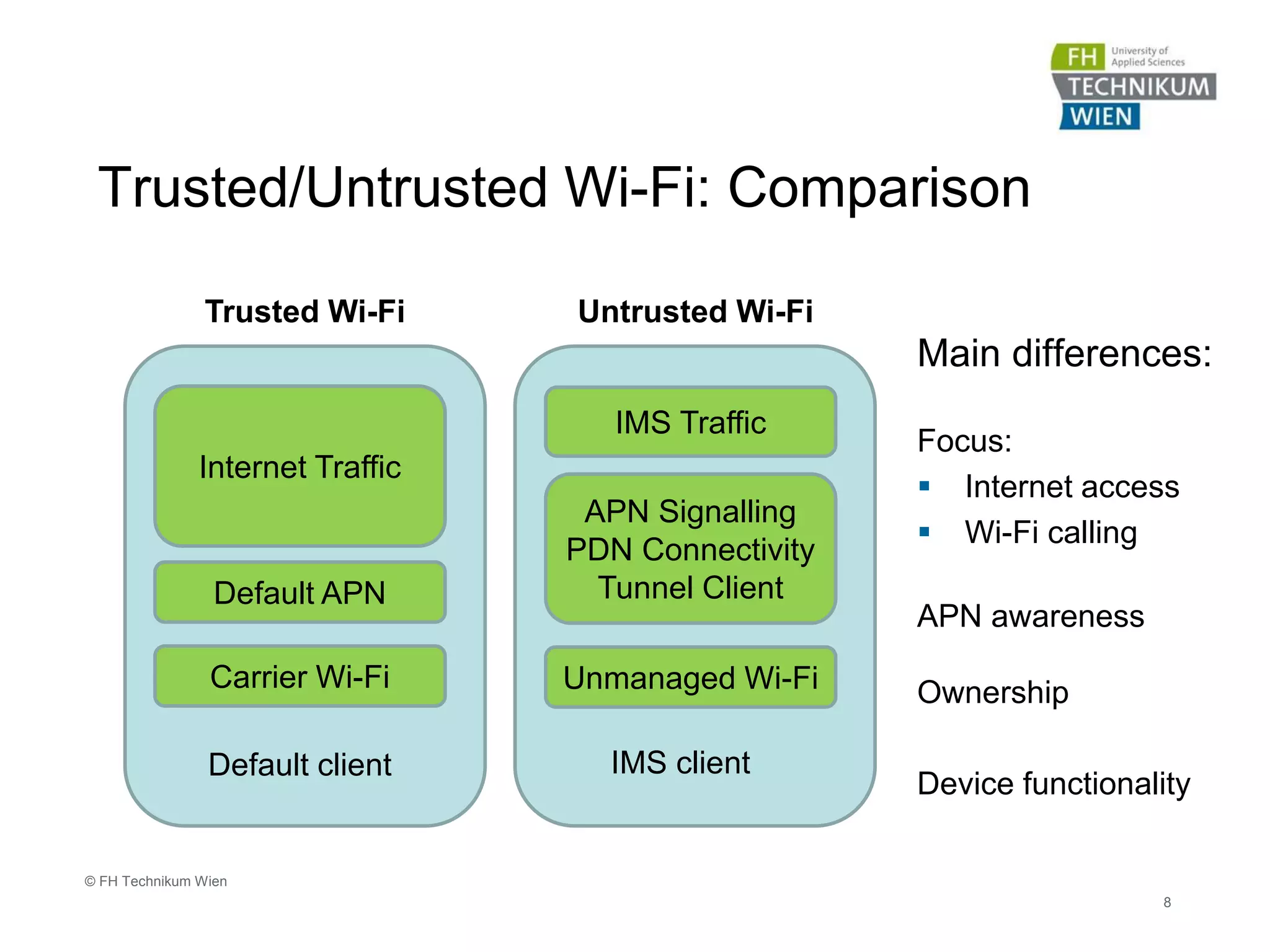
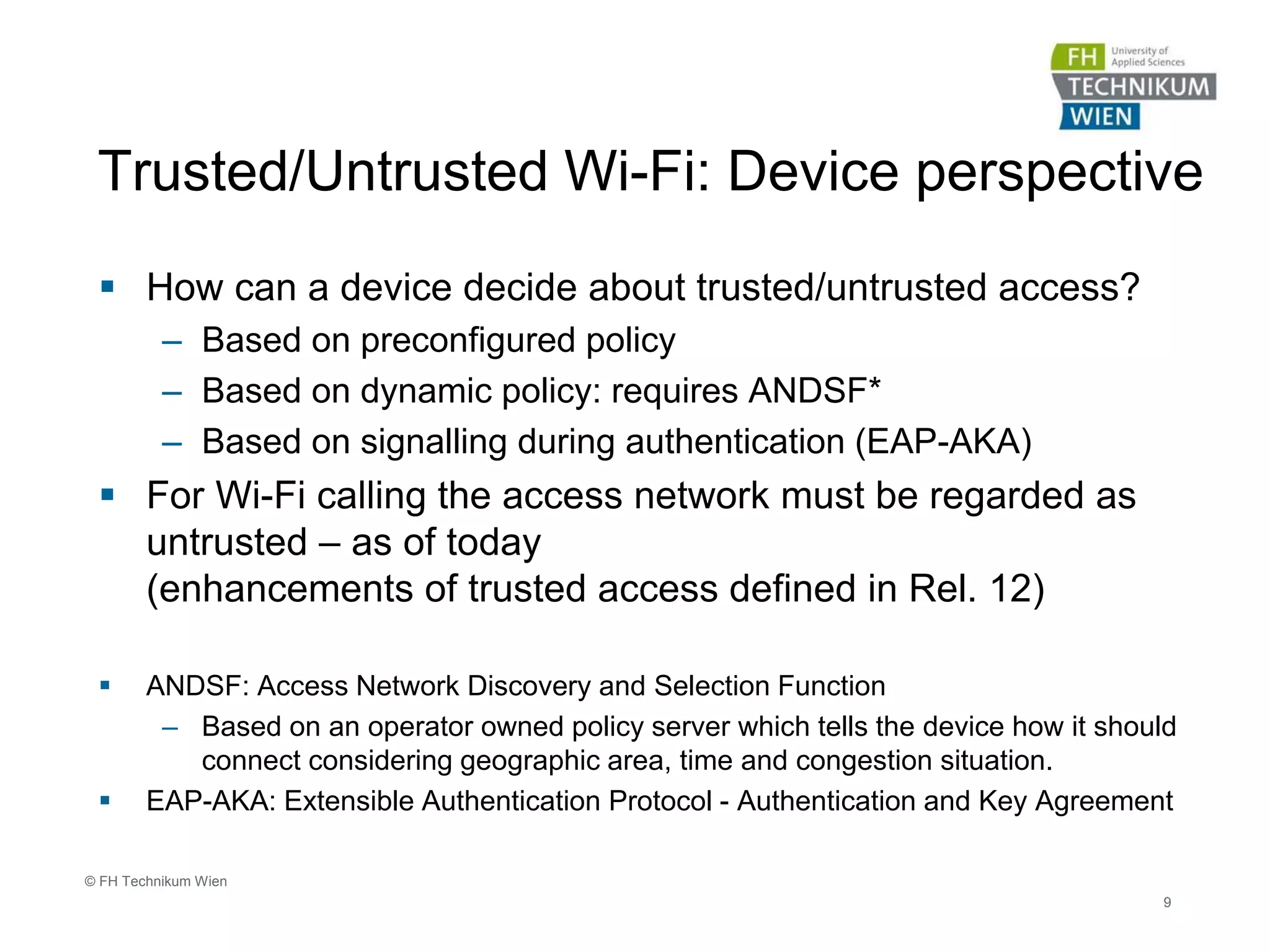
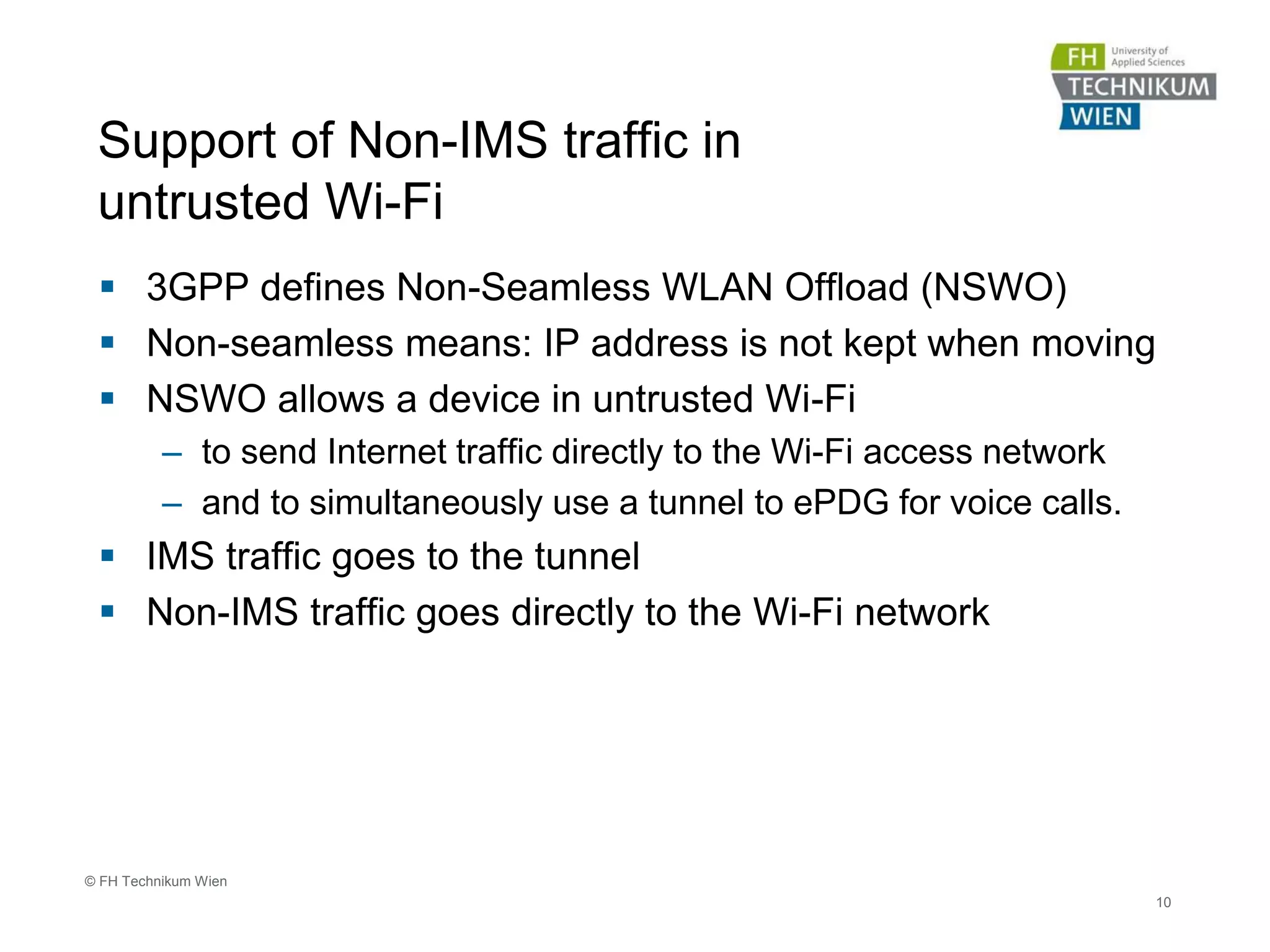
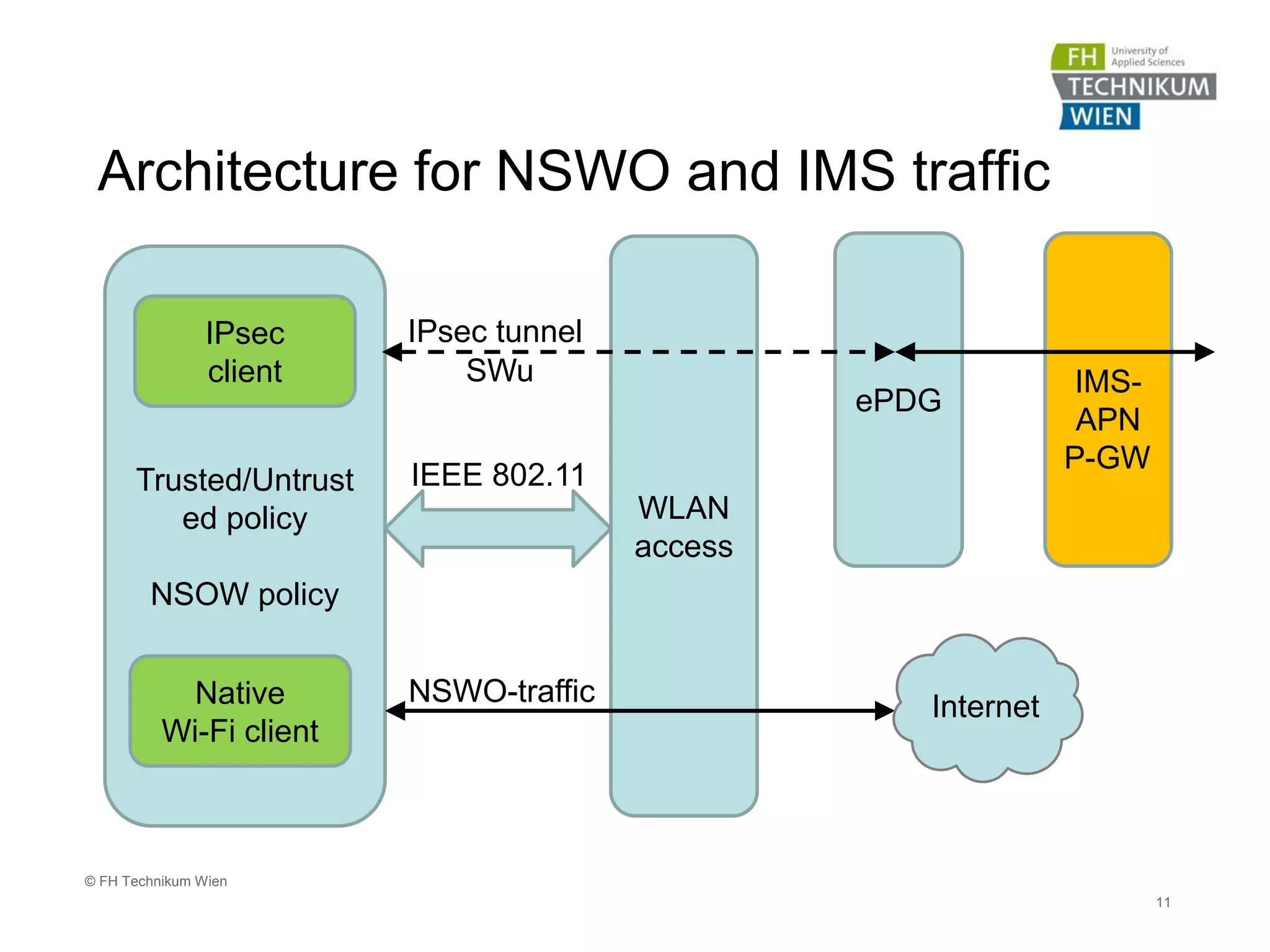
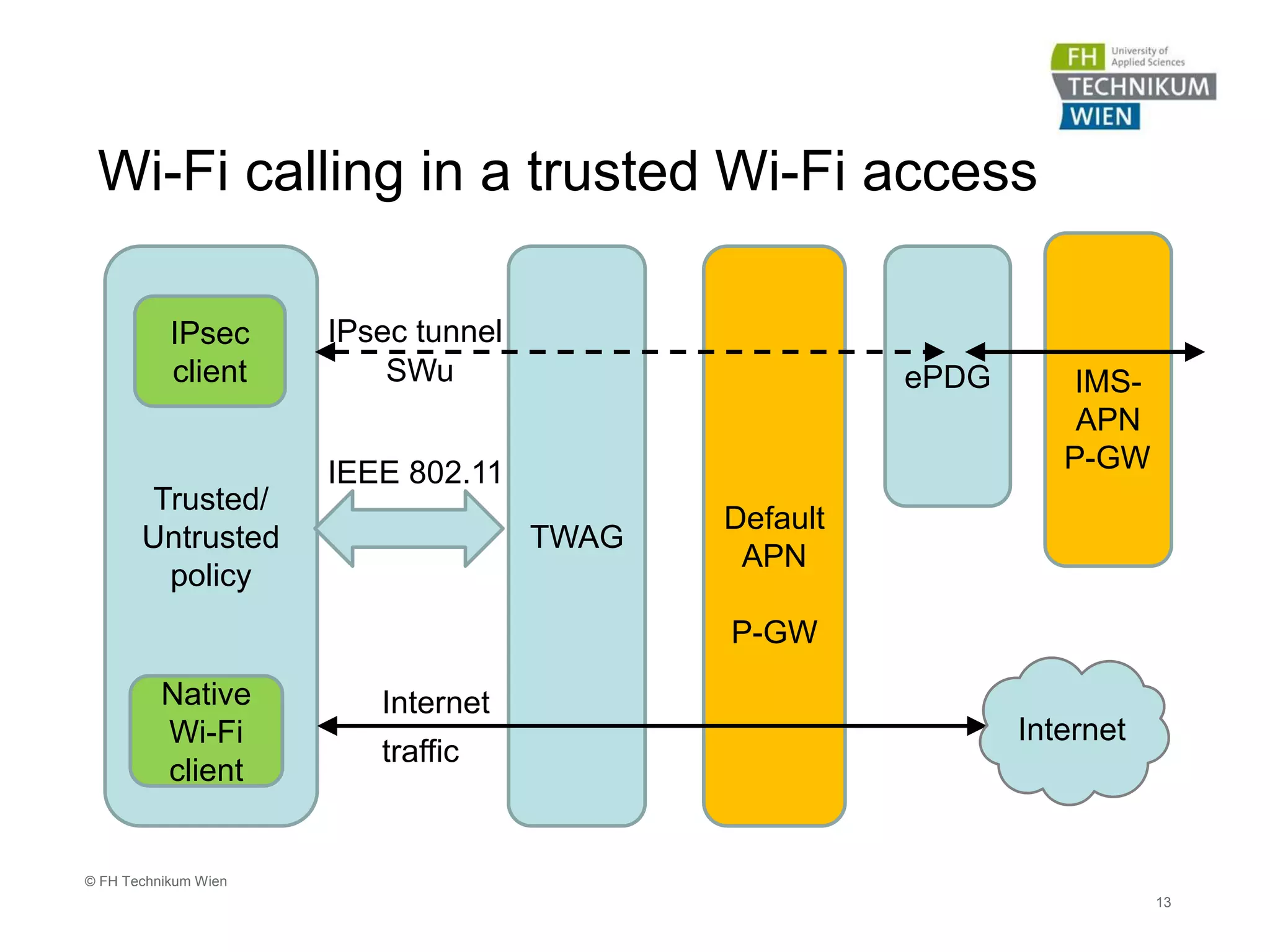
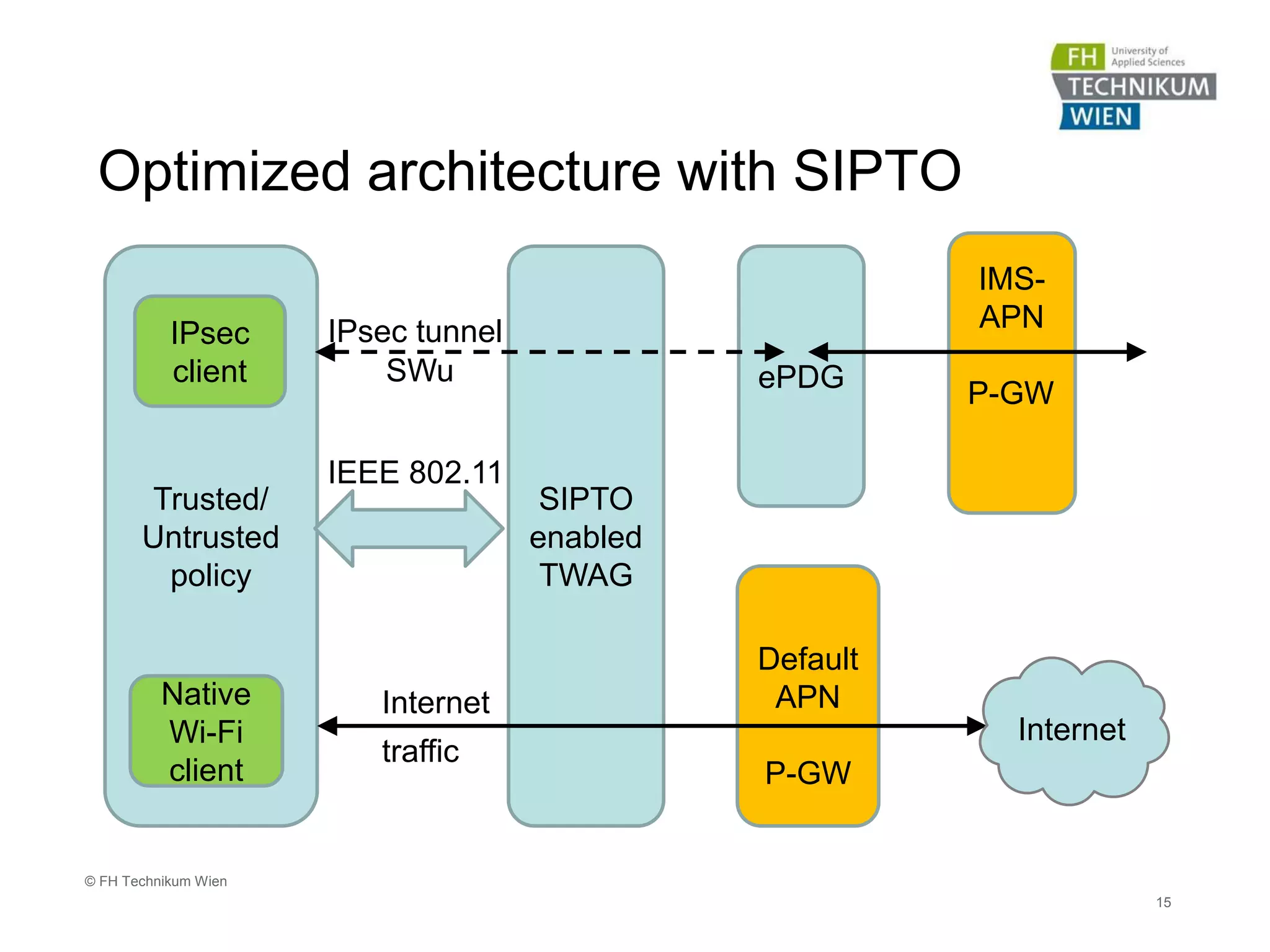
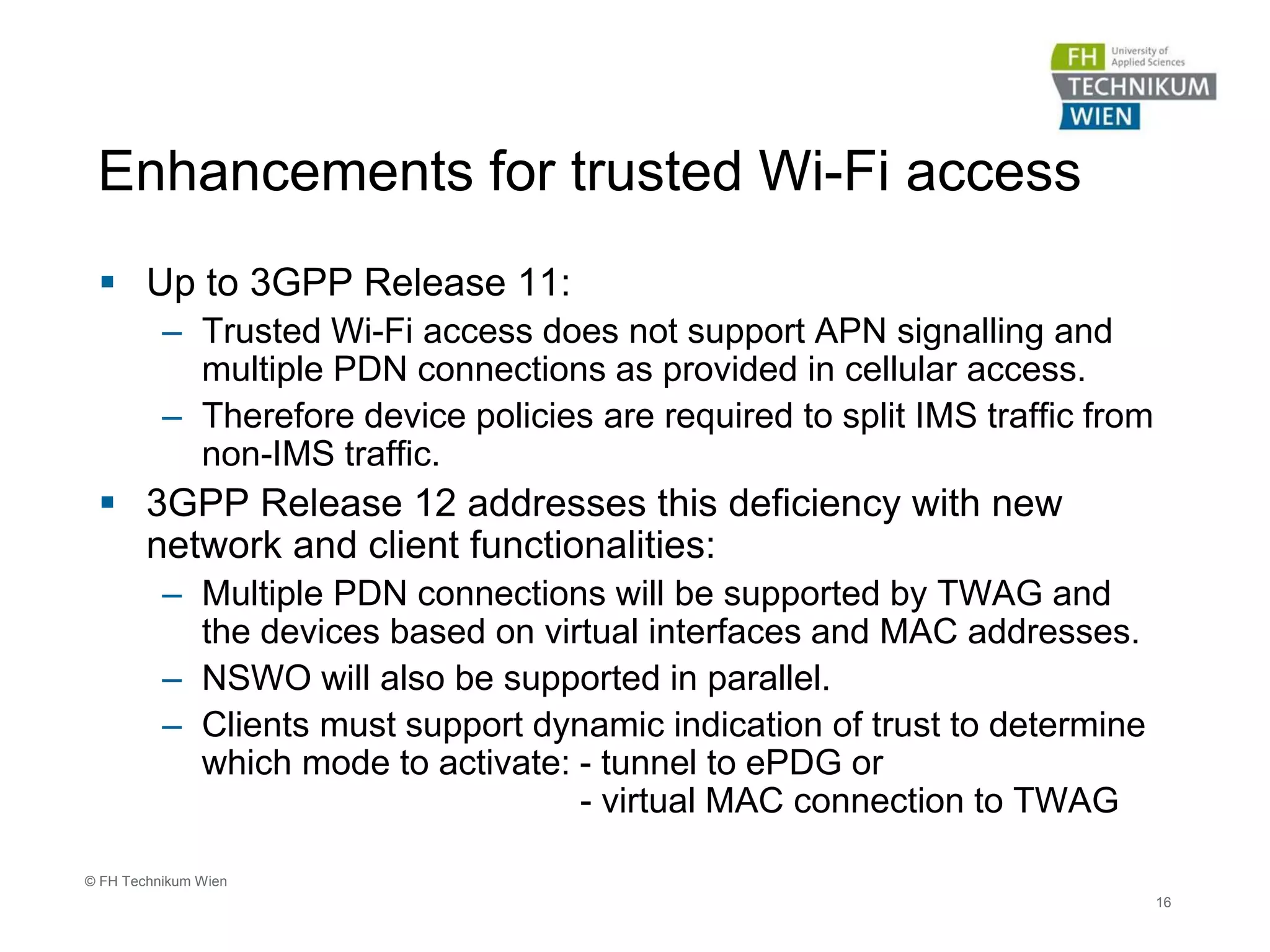
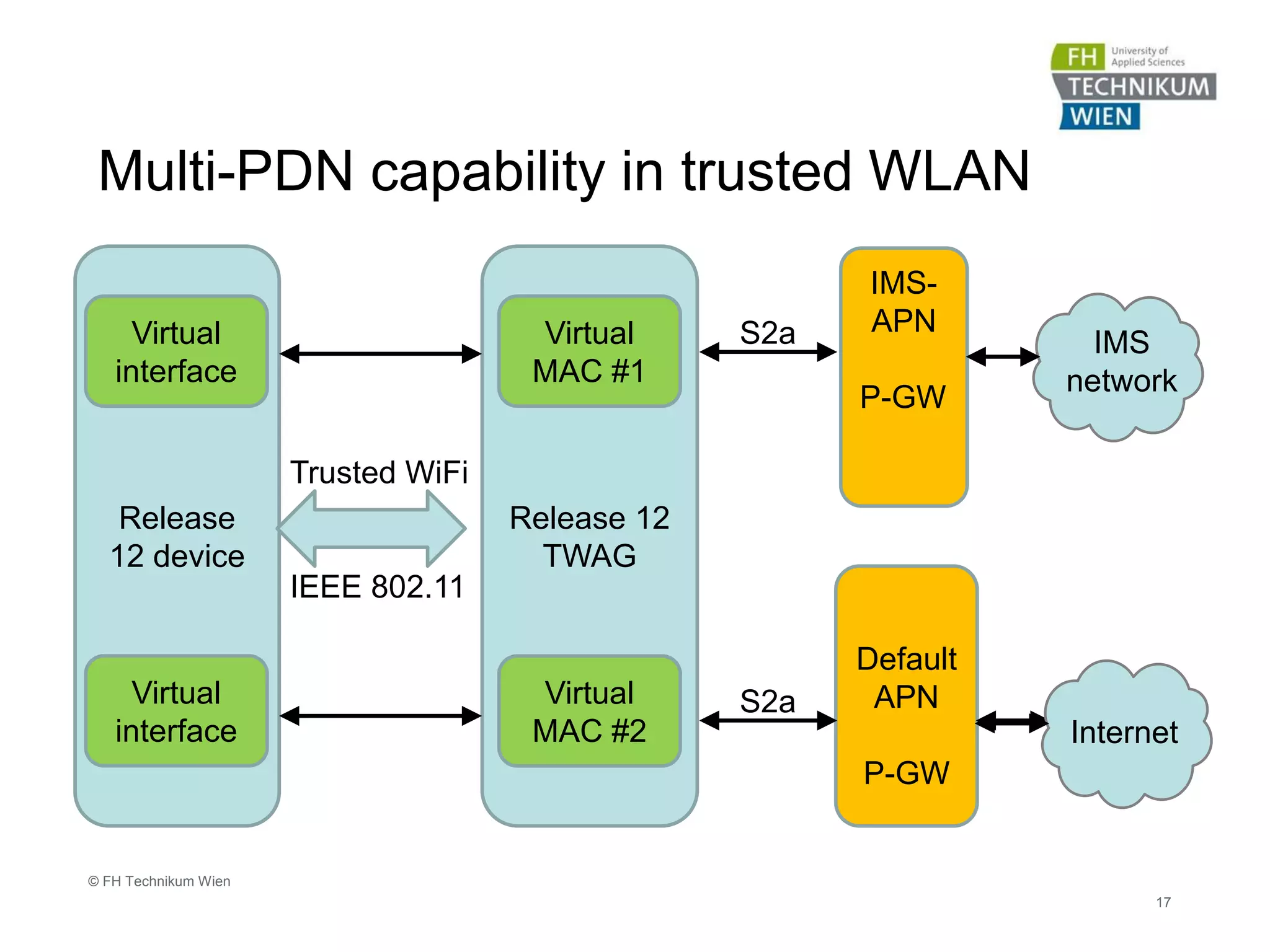
The document discusses the integration of Wi-Fi access networks into the Evolved Packet Core (EPC) mobile network. It describes how Wi-Fi can be used to offload data traffic from licensed 3GPP networks using both trusted and untrusted Wi-Fi connections. For trusted connections, the Wi-Fi access network is directly integrated into the EPC using a Trusted WLAN Access Gateway. For untrusted connections, an IPsec tunnel is established between the user device and the Evolved Packet Data Gateway for authentication. The document also discusses various enhancements to support Wi-Fi calling and multiple concurrent connections over both cellular and Wi-Fi.






![25
© FH Technikum Wien
Conditional Messages
UE ePDG
3GPP
AAA-Serv
HSS / HLR
1. IKE_SA_INIT
4. AVs retrieval if needed
(i.e. if not available in the AAA)
14. Calculate AUTH
8a. 3GPP AAA Server verifies
If AT_RES = XRES
[Headers, Sec. associations, D-H values, Nonces]
2. IKE_AUTH Request
[Header, User ID, Configuration Pyload, Sec. associations, Traffic selectors, APN info]
3. Authentication & Authorization Req [EAP-
Payload(EAP-Resp/Identity), User ID, APN info]
5. A&A-Answer [EAP-Request/AKA-Challenge]
6. IKE_AUTH Response
[Header, ePDG ID, Certificate, AUTH, EAP-Request/AKA-Challenge]
7. IKE_AUTH Request
[Header, EAP-Request/AKA-Challenge]
8. A&A-Request [EAP-Response/AKA-Challenge]
9. AA-Answer [EAP-Success, key material, IMSI]
11. IKE_AUTH Response
[Header, EAP-Success]
12. IKE_AUTH Request [AUTH]
13. Check AUTH correctness
15. IKE_AUTH Response
[Header, AUTH, Configuration Payload, Sec. Associations, Traffic Selectors]
6.a UE runs AKA
algorithms, verifies AUTN,
generates RES and MSK
8b. A&AA-Answer [EAP-Req/AKA-Notification]
8c. IKE_AUTH Response [Header, EAP-Req/AKA-Notification]
8d. IKE_AUTH Request [Header, EAP-Resp/AKA-Notification]
8e. A&A-Request [EAP-Resp/AKA-Notification]
10. AUTH payload is computed
using the keying material (MSK)
8A. Profile Retrieval and
Registration
Untrusted Wi-Fi
• Setup of IPsec connection
(Diffie-Hellman exchange)
• Identification and retrieval
of authentication data
• Calculate and send
response
• Verify result
• Optional step
(dynamic selection of
mobility mode)
• Retrieval of user-profile
(3GPP TS 33.403 § 8.2)](https://image.slidesharecdn.com/eps-wifi-integrationintoepc-160311052555/75/WiFi-integration-into-EPC-25-2048.jpg)