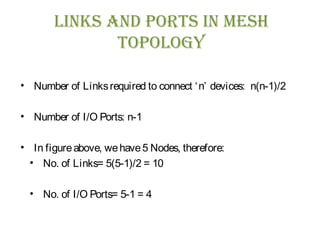
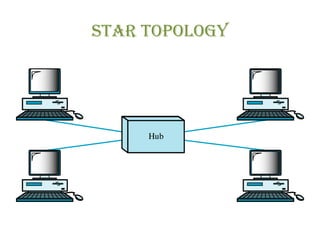
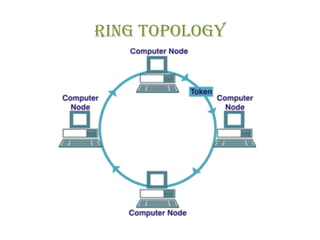
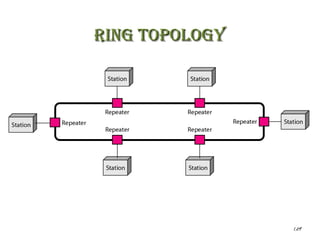
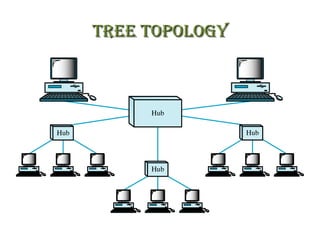
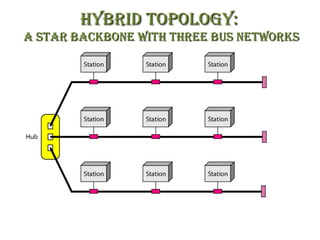
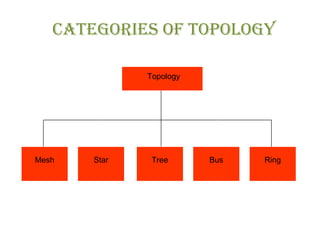
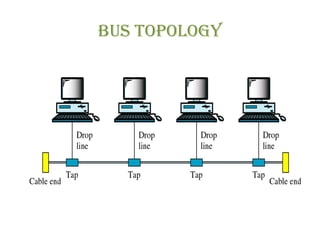
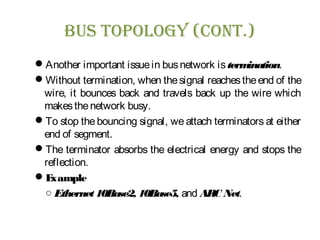
The document discusses various physical network topologies including bus, mesh, star, ring, tree, and hybrid. It provides detailed descriptions of how each topology is structured and how data is transmitted. For example, it explains that a bus topology uses a single cable as a backbone to connect all devices and that collisions can occur when multiple devices transmit simultaneously. The document also compares advantages and disadvantages of the different topologies.








![Mesh Topology (ConT.)
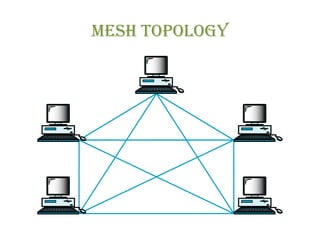
• TRUEMESH
• A true Mesh has a link between each device in the
network.
• It meansthat network isfully connected.
• A true mesh of six devices requires fifteen connections (5
x 6)/2 = 15 links and that for seven devices requires 21
links.
• The formula for finding total links in a true mesh is [n *
(n– 1)] /2, wherenistotal number of workstations.](https://image.slidesharecdn.com/dc-lec-03topologies-150513143944-lva1-app6892/85/Dc-lec-03-topologies-17-320.jpg)