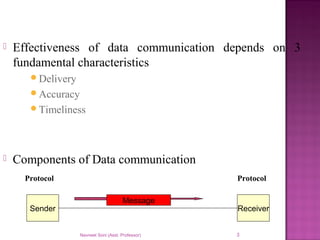
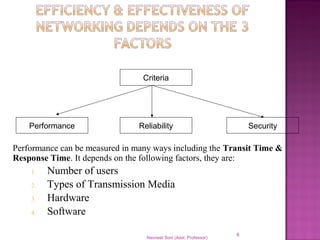
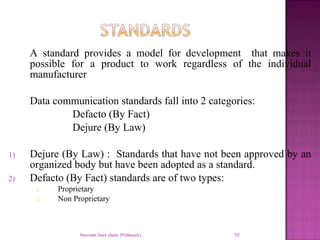
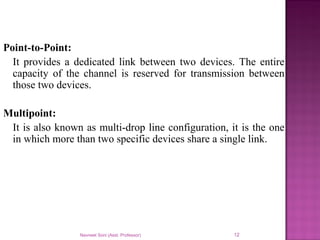
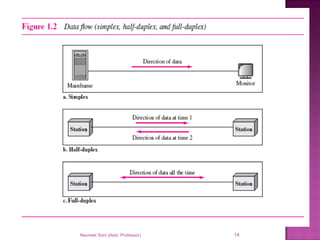
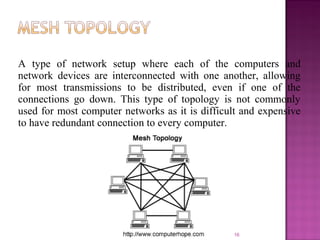
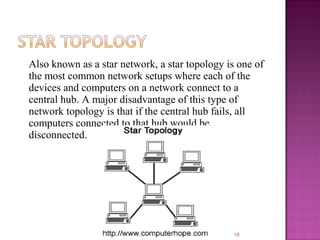
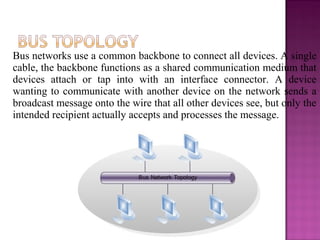
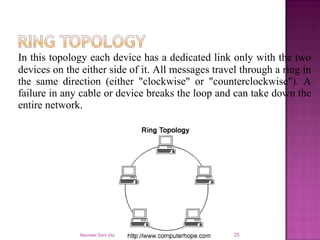
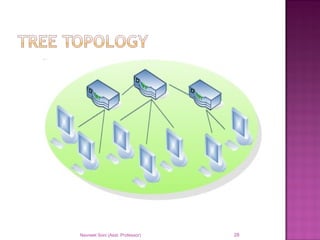
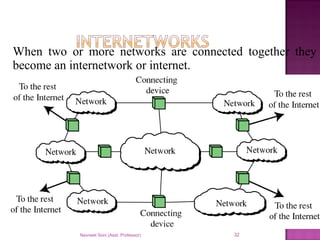
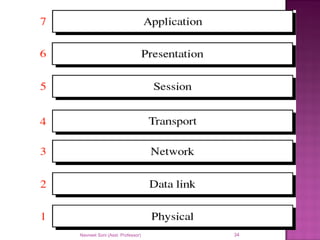
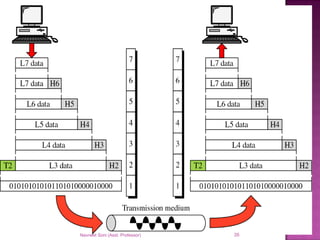
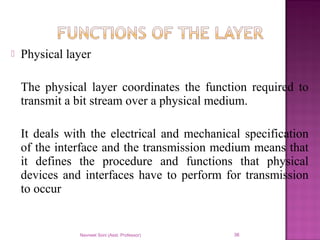
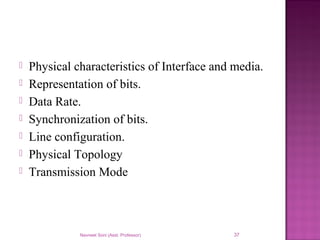
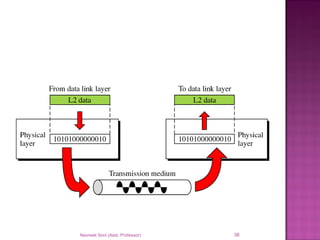
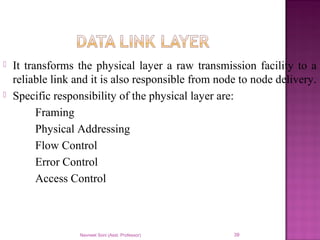
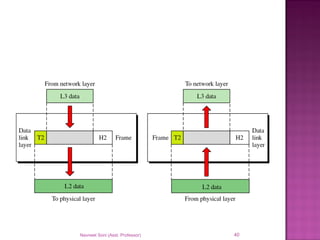
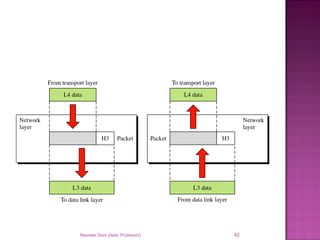
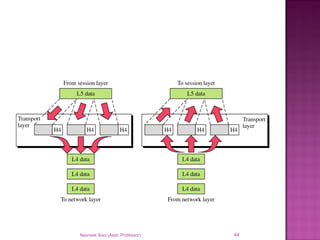
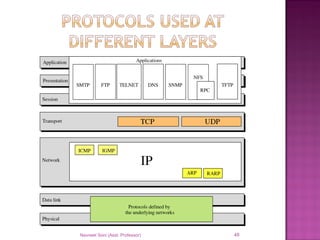
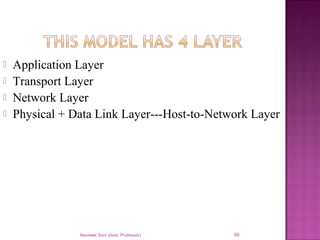
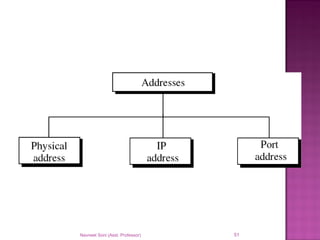
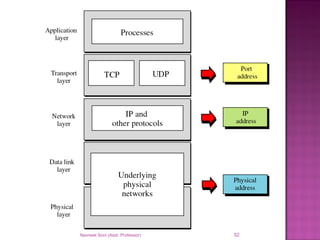
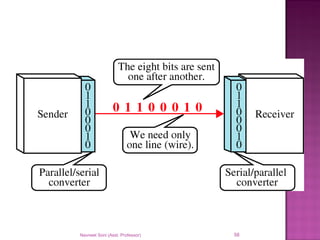
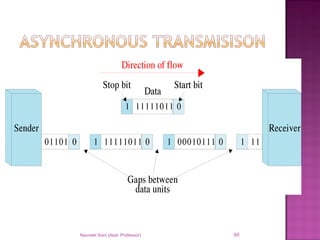
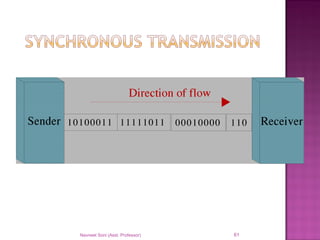
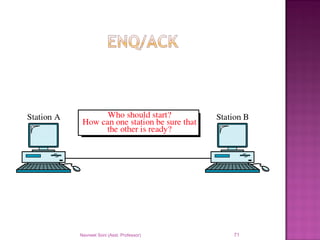
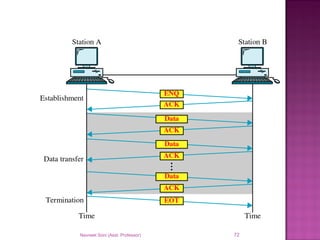
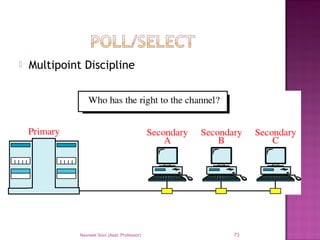
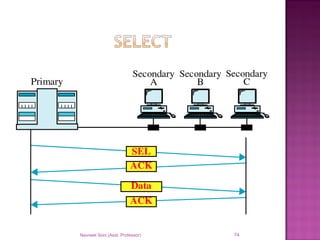
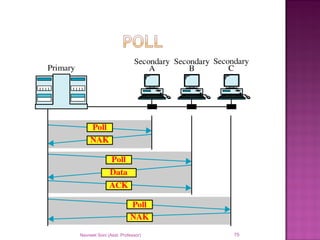
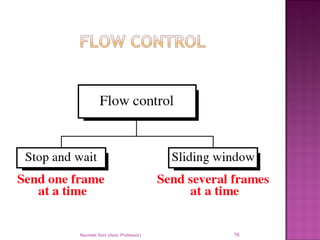
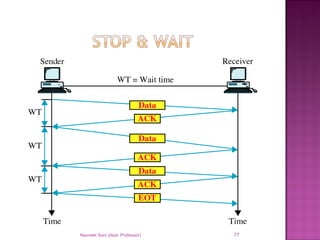
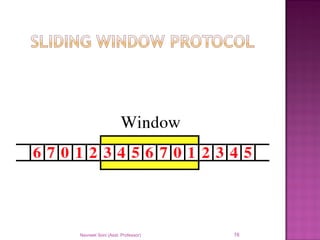
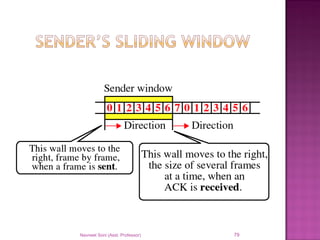
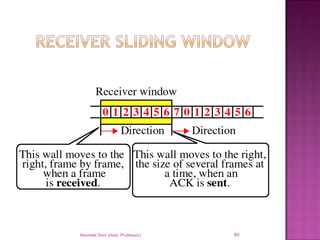
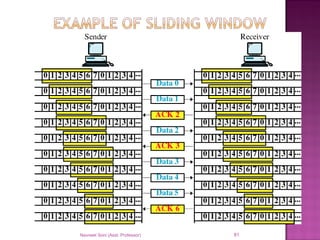
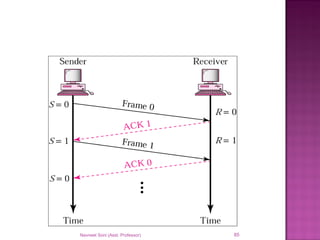
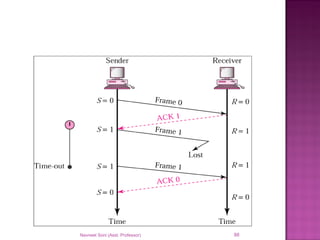
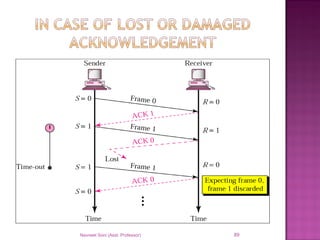
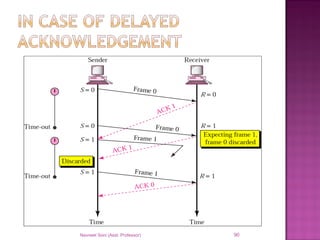
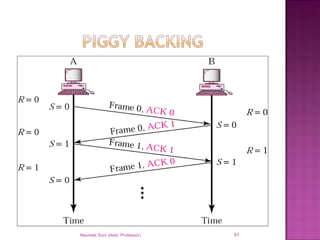
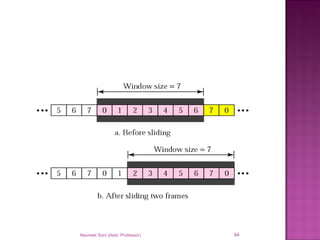
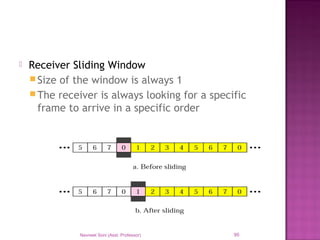
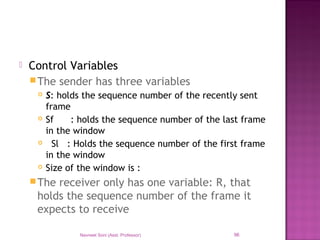
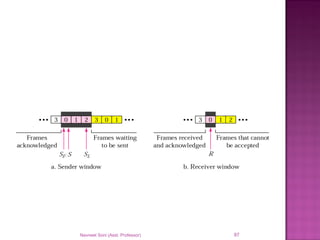
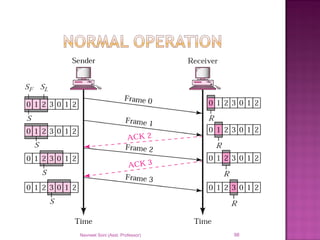
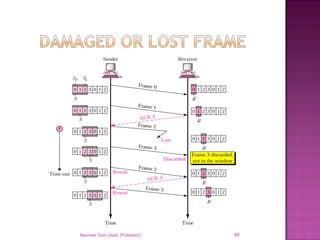
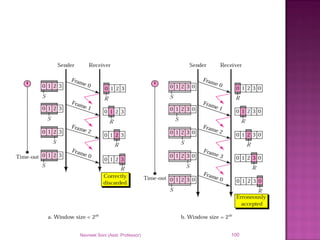
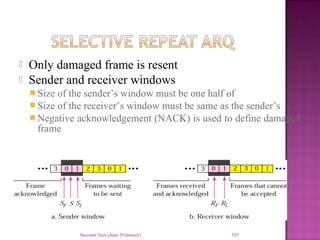
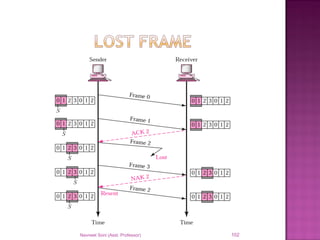
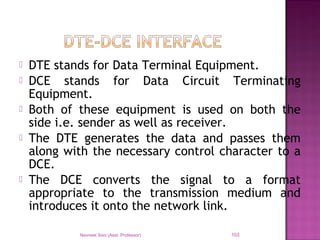
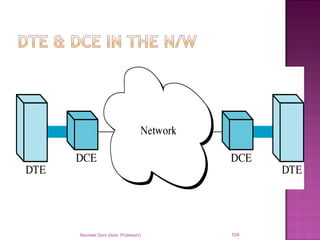
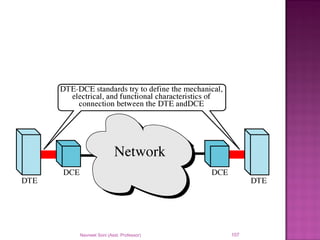
The document provides an overview of data communication, including its types, characteristics, and the OSI model's seven layers. It discusses protocols, network topologies like star, bus, ring, and mesh, and the role of each layer in facilitating communication. Key factors affecting performance include reliability, security, and various transmission methods in communicating networks.