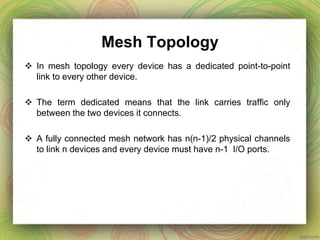
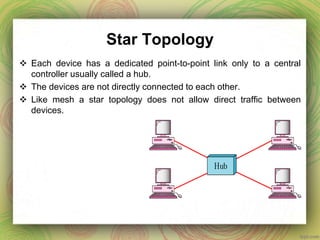
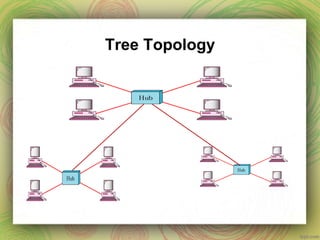
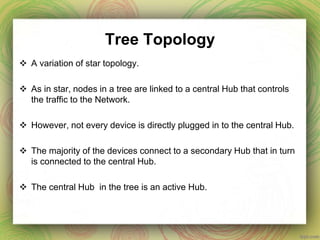
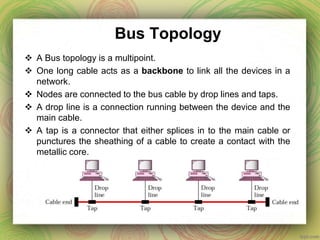
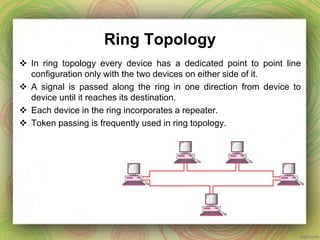
This document discusses different network topologies including mesh, star, tree, ring, and bus. It provides details on how each topology connects devices and the advantages and disadvantages of each. Mesh topology has every device directly connected to every other device. Star topology connects all devices to a central hub. Tree topology is a variation of star where secondary hubs are connected to a central hub. Ring topology connects devices in a continuous loop. Bus topology uses a single backbone cable to connect all devices. Hybrid topologies combine two or more topologies.