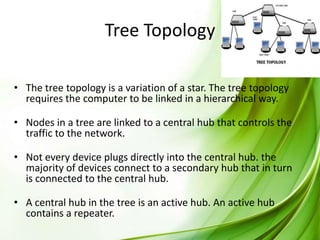
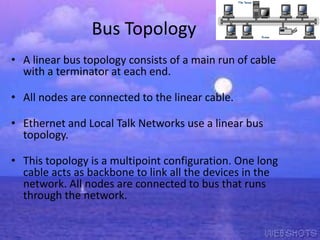
The document discusses various types of network topologies including mesh, star, tree, bus, and ring topologies, detailing their configurations, advantages, and disadvantages. It explains how physical topology pertains to the physical layout of network components, while logical topology refers to data flow methods. Each topology serves different organizational needs and has unique characteristics affecting installation, cost, and reliability.