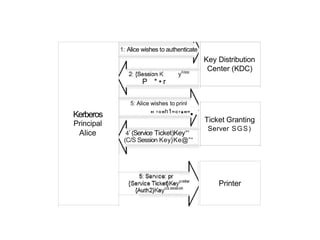
The document discusses various authentication methods in identity and access management, highlighting different types such as 'something you know,' 'something you have,' and 'something you are.' It explains the intricacies of password types, authentication challenges, and the importance of multi-factor authentication alongside technologies like Kerberos, RADIUS, and access control models. Additionally, it addresses the vulnerabilities found in traditional systems and emphasizes the need for robust password policies and access provisioning practices.













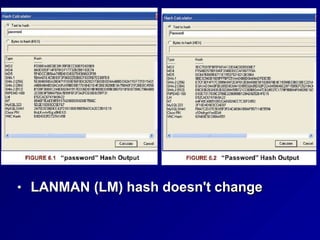





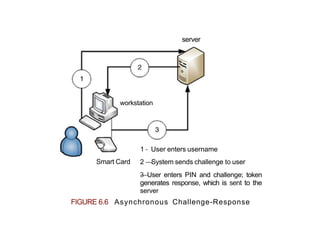

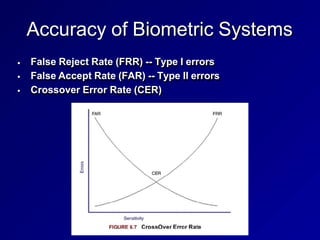
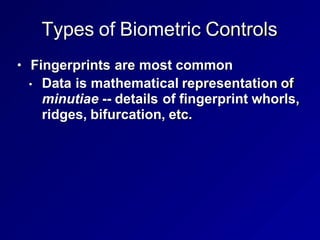
![FIGMRE 6.8 Fingerprint IVIInuflae {7]](https://image.slidesharecdn.com/authenticationmethods-240319213011-f20904cb/85/Authentication-Methods-authauthauthauthauthautha-25-320.jpg)