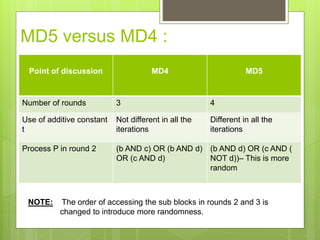
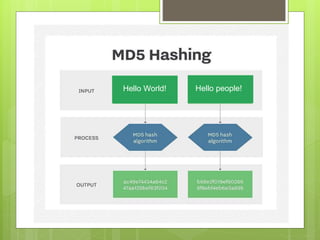
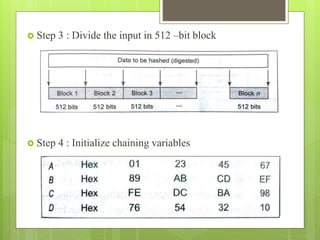
MD5 is a cryptographic hash function that produces a 128-bit hash value for a message of any length. It was originally designed to provide authentication of digital signatures but is no longer considered reliable for cryptography due to techniques that can generate collisions. MD5 operates by padding the input, appending the length, dividing into blocks, initializing variables, processing blocks through 4 rounds of operations with different constants each round, and outputting the hash value. While it was intended to be difficult to find collisions or recover the input, MD5 is no longer considered cryptographically secure due to attacks demonstrating collisions.







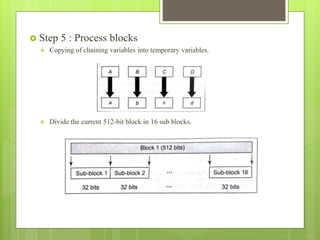
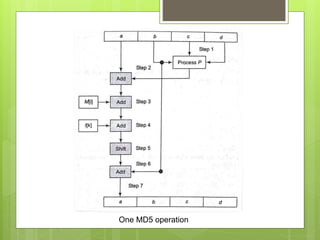
![ Conceptual process within a round.
We can mathematically express a single MD5 operation as follows:
a = b+((a + Process P (b,c,d)+M[i]+t[k])<<<s)
where,
a,b,c,d = Chaining variable
Process P = A non-linear operation
M[i] = M[q*16+i],which is the ith 32-bit word in the
qth 512-bit block of the message
t[k] = A constant
<<<s = Circular shift by s bits](https://image.slidesharecdn.com/messagedigest5-190205165229/85/Message-digest-5-11-320.jpg)