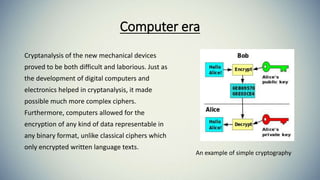
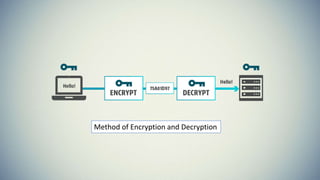
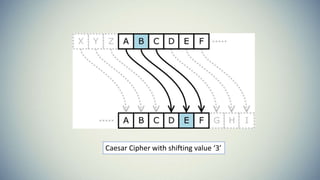
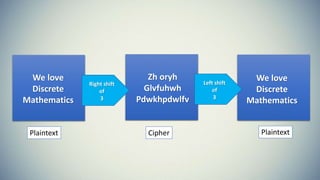
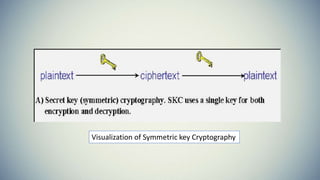
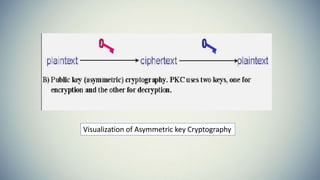
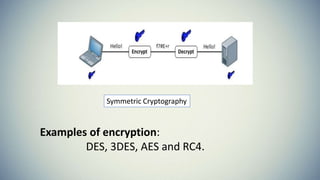
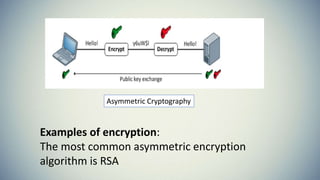
Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.