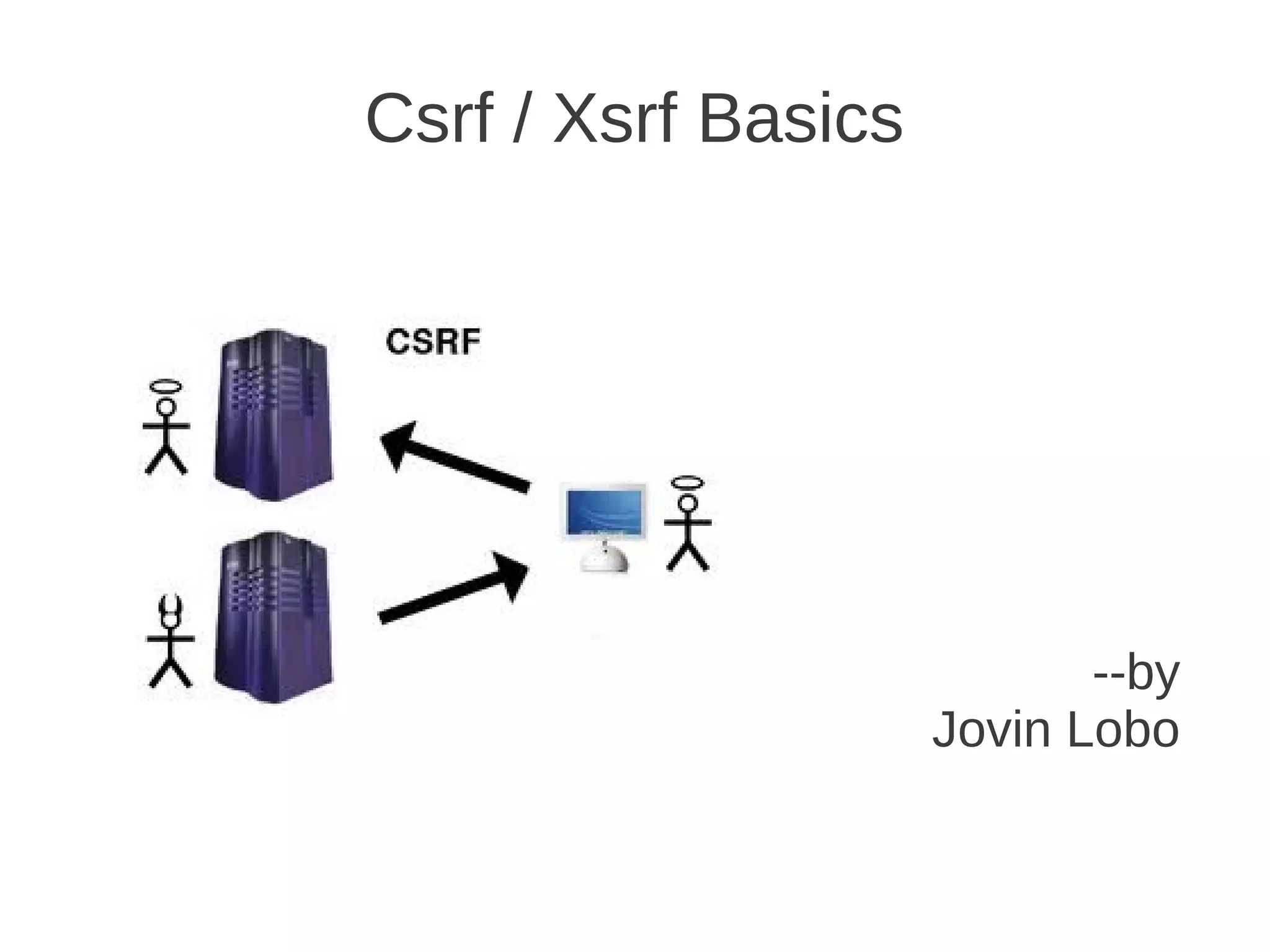
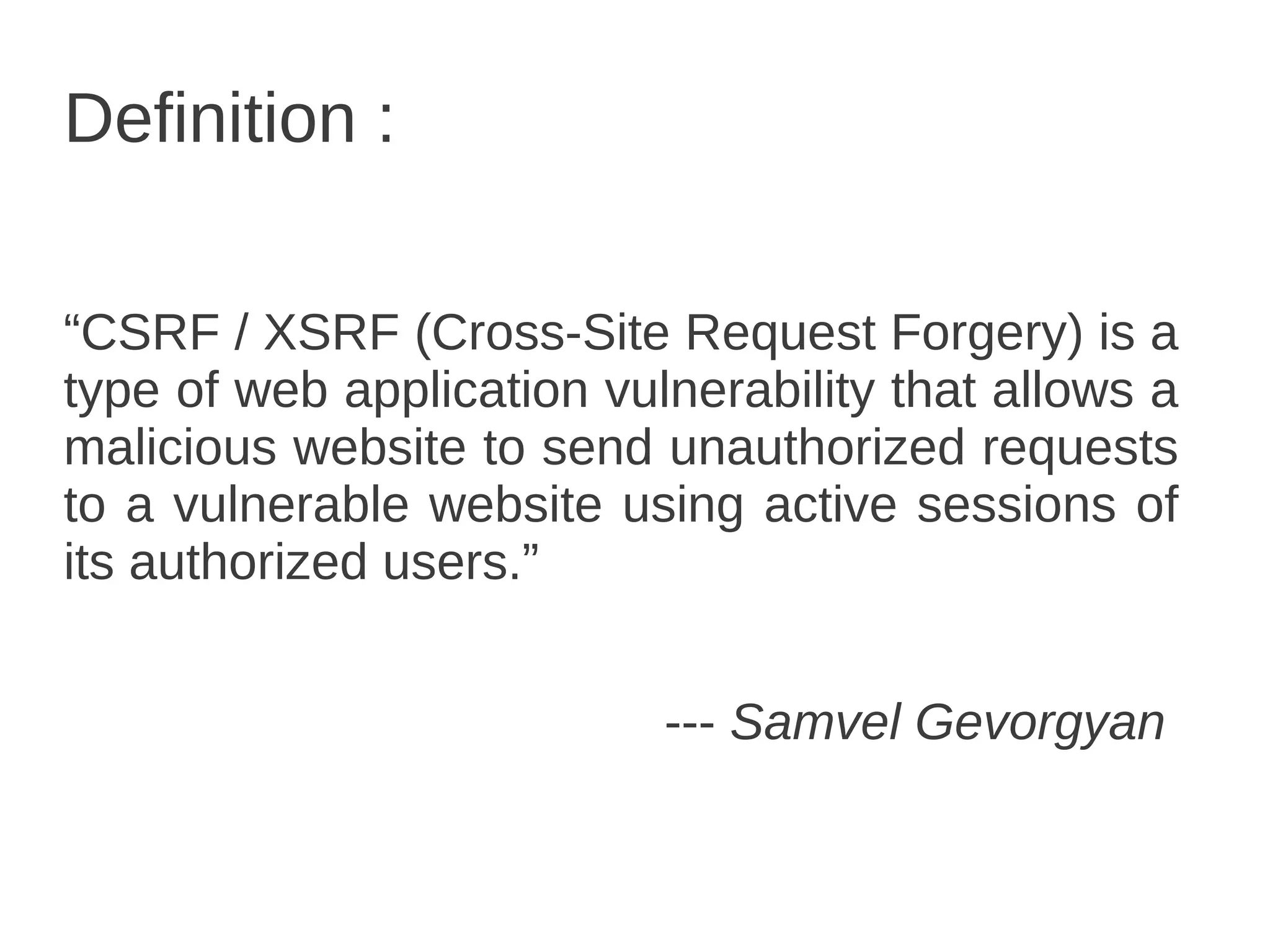
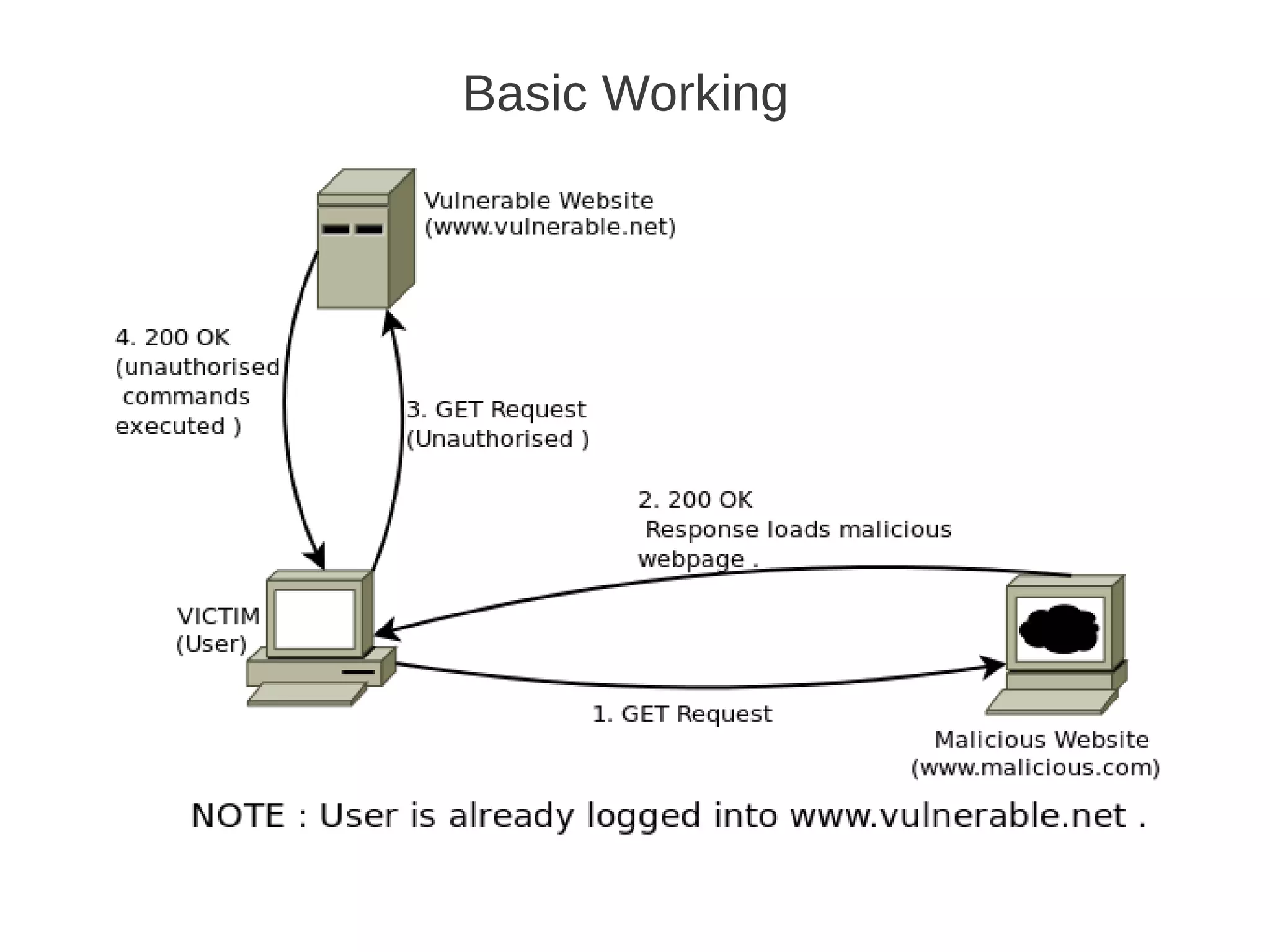
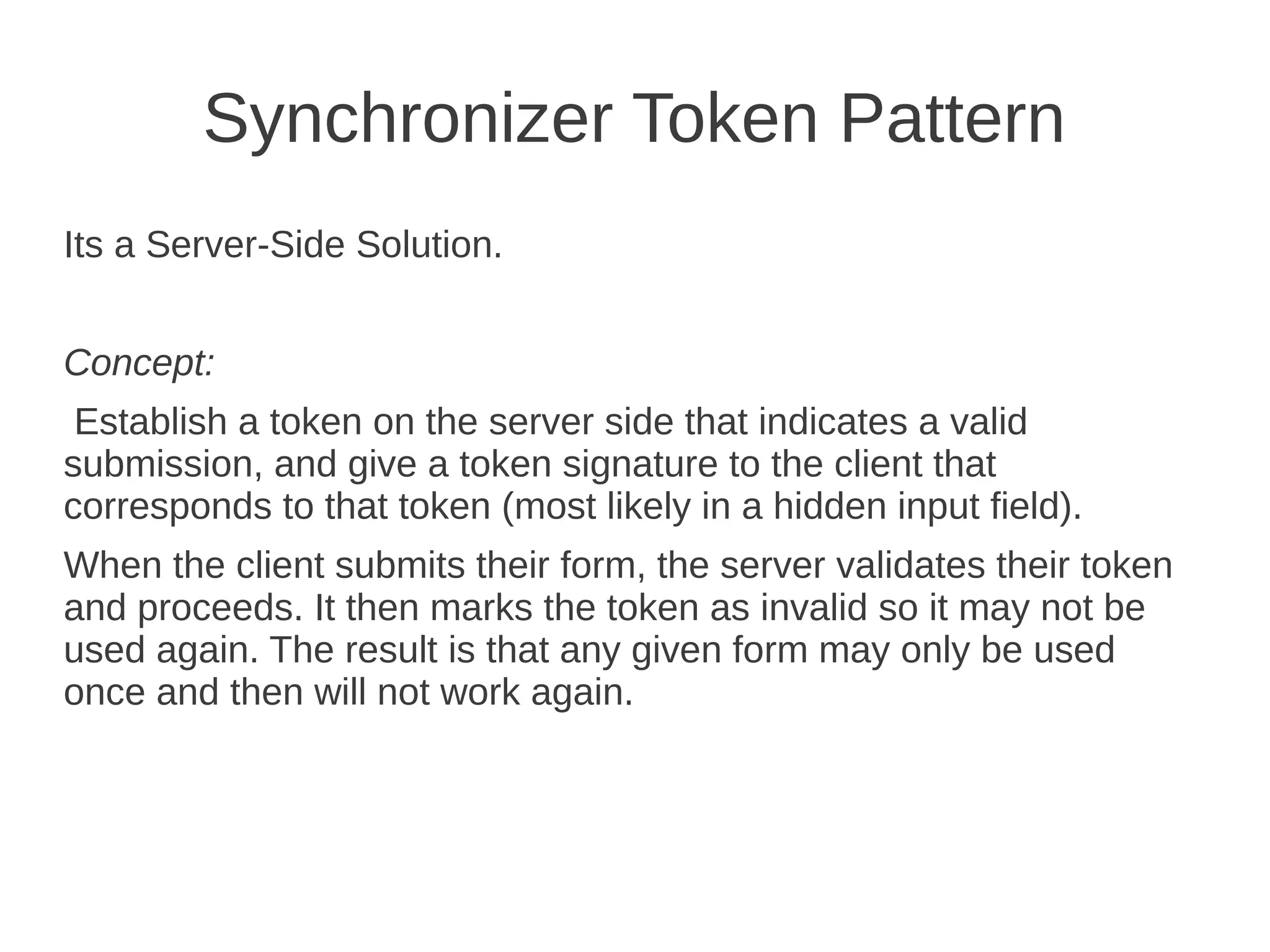
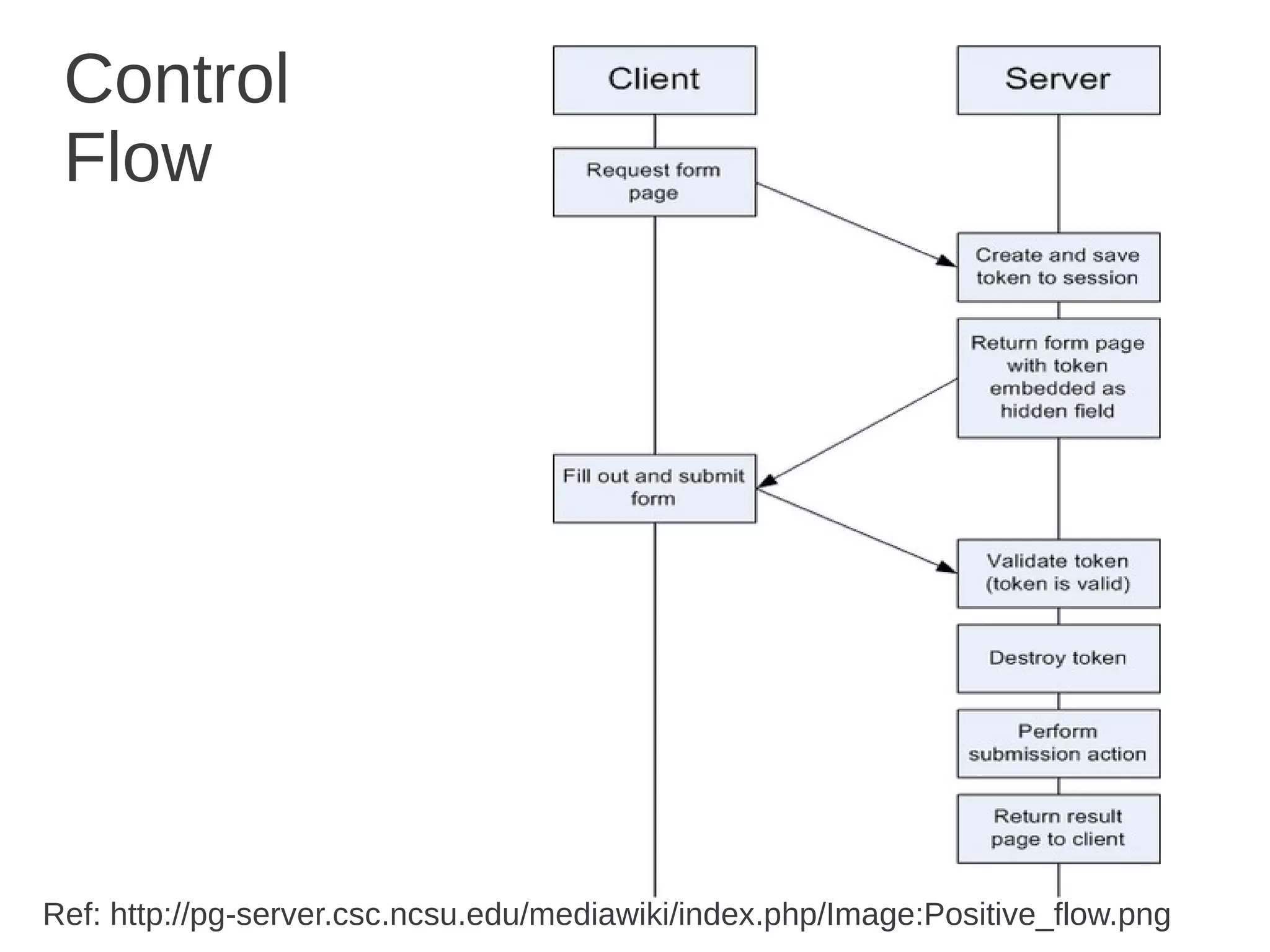
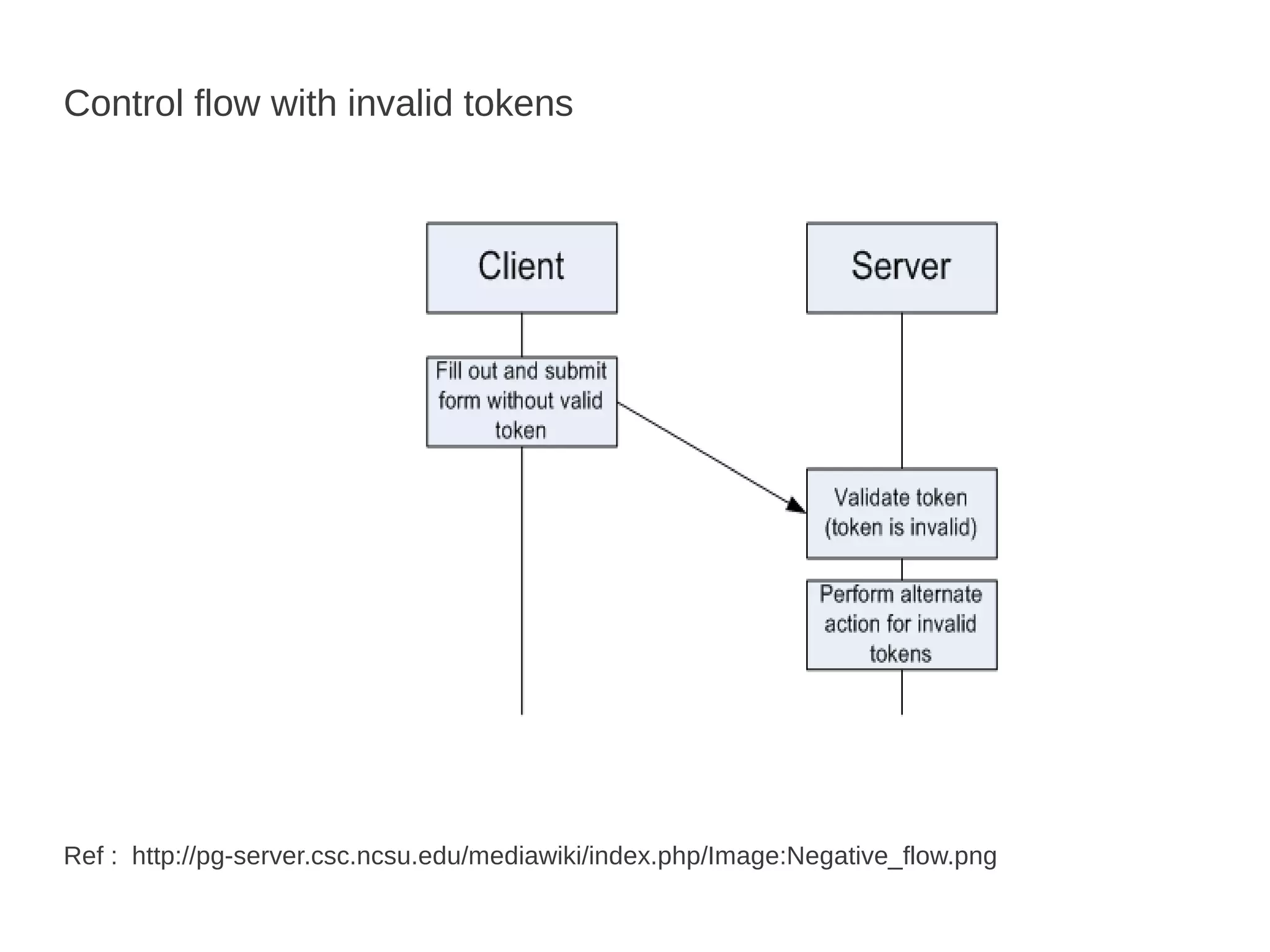
Csrf / Xsrf Basics defines CSRF as a type of web application vulnerability that allows a malicious website to send unauthorized requests to a vulnerable website using active sessions of its authorized users. CSRF tricks the victim into loading a page that contains a malicious request, which inherits the victim's identity and privileges to perform an undesired function like changing passwords. CSRF attacks target functions that cause state changes on the server but can also access sensitive data. The synchronizer token pattern is a server-side prevention technique that establishes a token on the server to validate submissions through a corresponding token in a hidden form field, marking tokens as invalid after single use.