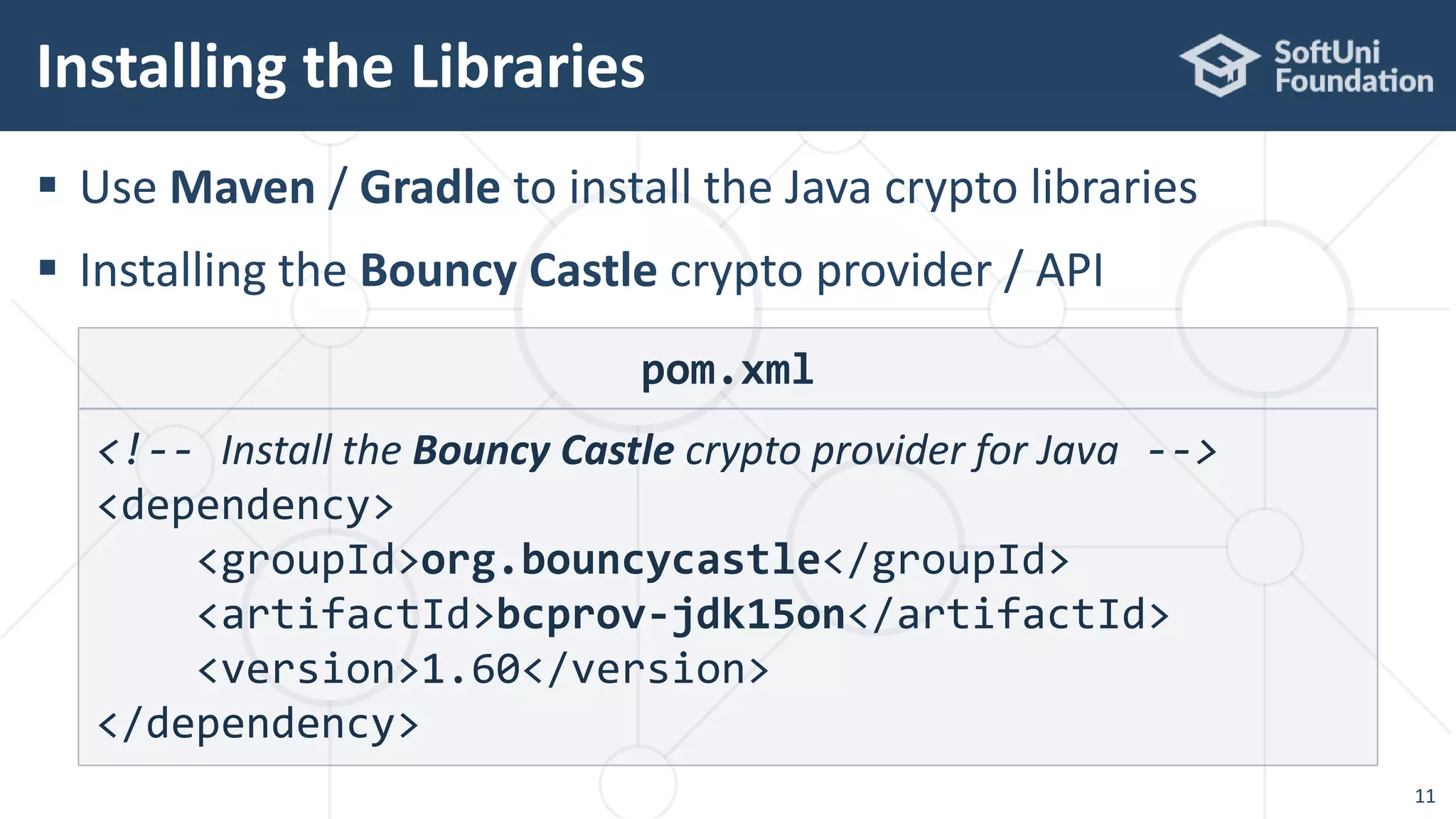
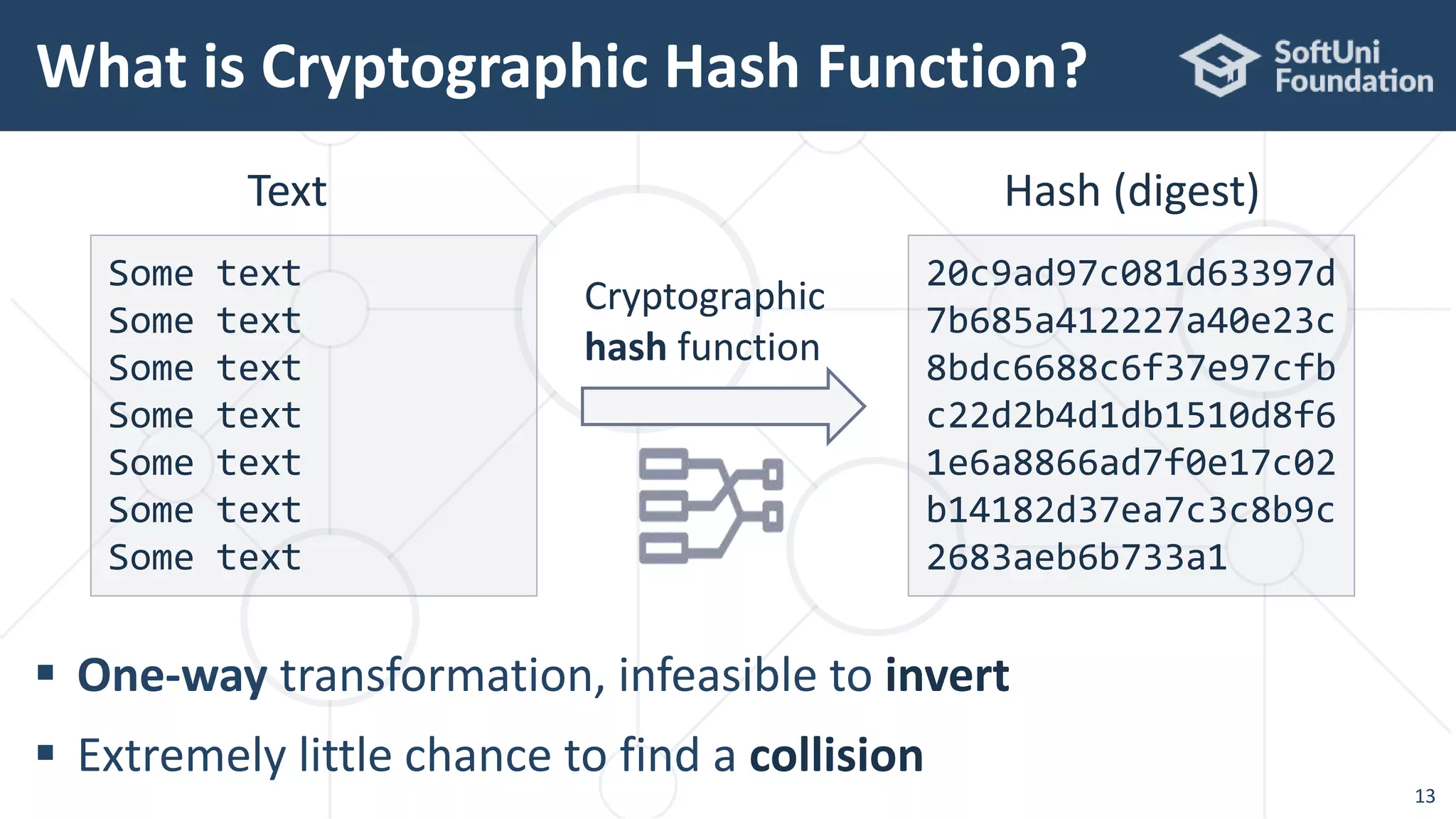
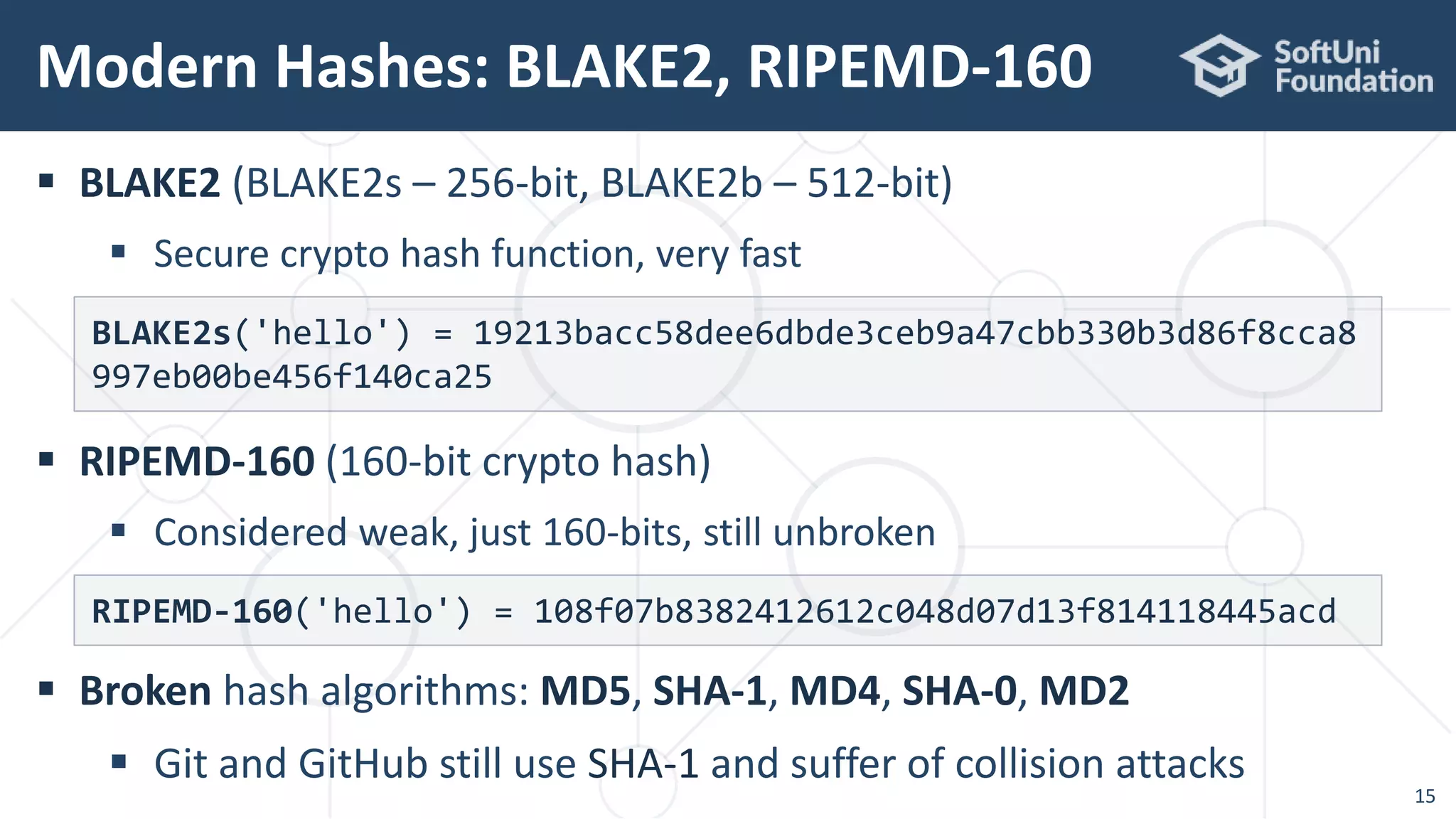
The document provides an in-depth overview of cryptography principles and practices specifically for Java developers, detailing topics such as hashing, MAC codes, symmetric encryption (AES), digital signatures, and key derivation functions. It emphasizes the importance of secure password encryption, recommending algorithms like Argon2, and the use of various cryptographic libraries (e.g., Bouncy Castle) available in Java. Additionally, the document includes practical code examples and highlights the implementations of cryptographic techniques within Java applications.







![ Calculate SHA-256 hash using the built-in JCA provider:
SHA-256 in Java – Example
16
var digest = MessageDigest.getInstance("SHA-256");
digest.update("hello".getBytes());
byte[] hash = digest.digest();
System.out.println("SHA-256('hello') = " +
Hex.toHexString(hash));
import java.security.MessageDigest;
import org.bouncycastle.util.encoders.Hex;
SHA-256('hello') =
2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-16-2048.jpg)
![ Calculate RIPEMD-160 hash using the Bouncy Castle provider:
RIPEMD-160 in Java – Example
17
var digest = MessageDigest.getInstance("RIPEMD160");
digest.update("hello".getBytes());
byte[] hash = digest.digest();
System.out.println("RIPEMD-160('hello') = " +
Hex.toHexString(hash));
import java.security.*;
import org.bouncycastle.util.encoders.Hex;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
// One-time registration of the "BouncyCastle" JCA provider
Security.addProvider(new BouncyCastleProvider());
108f07b8382412612c048d07d13f814118445acd](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-17-2048.jpg)
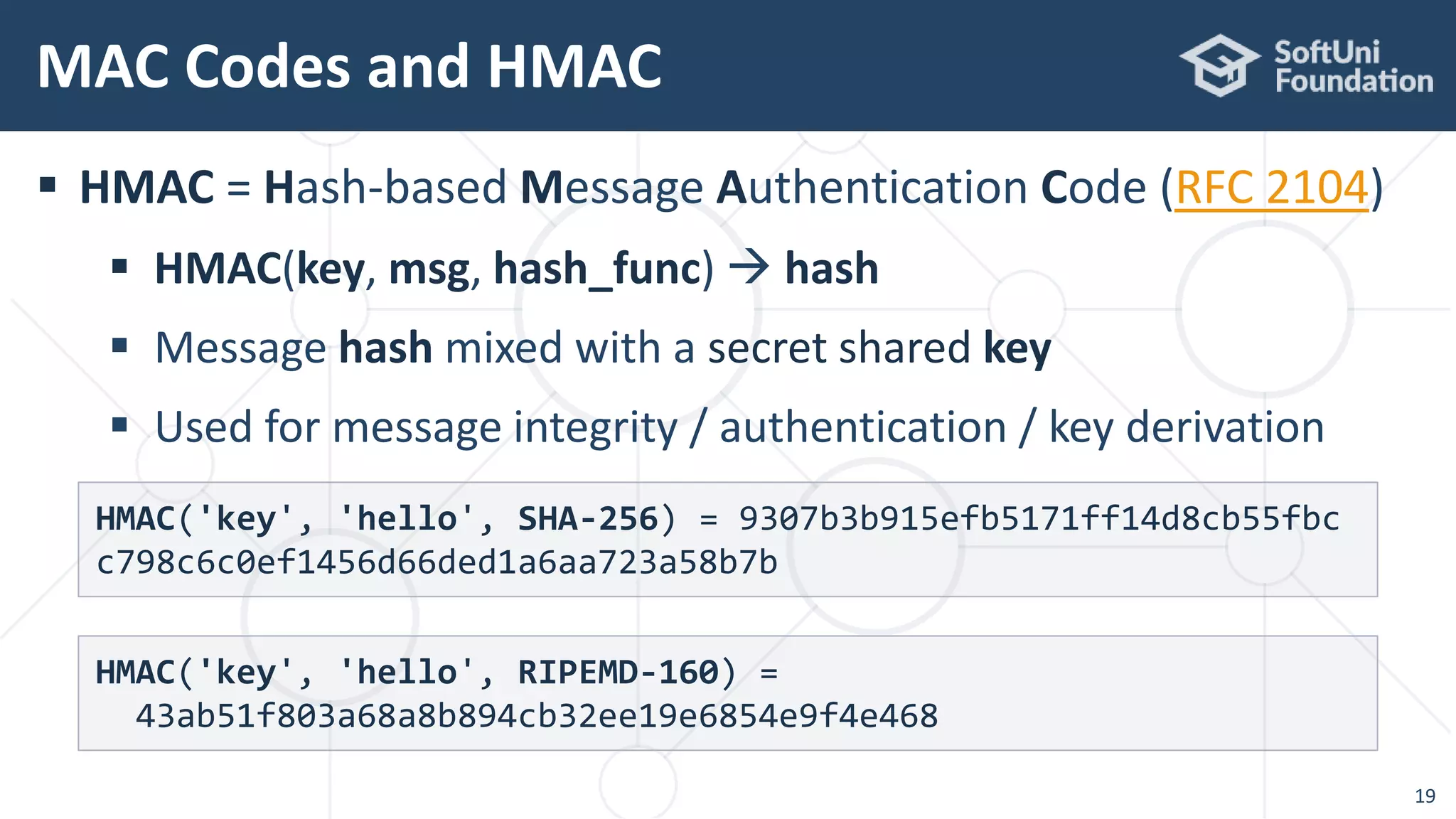
![ Calculate HMAC-SHA-256 hash using the built-in JCA provider:
HMAC in Java – Example
20
Mac mac = Mac.getInstance("HmacSHA256");
Key key = new SecretKeySpec("key".getBytes(), "HmacSHA256");
mac.init(key);
byte[] hash = mac.doFinal("hello".getBytes());
System.out.println("HMAC-SHA-256: " + Hex.toHexString(hash));
import javax.crypto.Mac;
import javax.crypto.spec.SecretKeySpec;
import java.security.Key;
import org.bouncycastle.util.encoders.Hex;
HMAC-SHA-256: 9307b3b915efb5171ff14d8cb55fbcc798c6c0ef1456d66ded1a6aa723a58b7b](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-20-2048.jpg)
![ Key derivation function (KDF) == function(password) key
PBKDF2 (Password-Based Key Derivation Function 2, RFC 2898)
Key Derivation Functions (KDF)
21
PBEKeySpec spec = new PBEKeySpec("password".toCharArray(),
"salt".getBytes(), 1000, 128);
SecretKeyFactory keyFactory =
SecretKeyFactory.getInstance("PBKDF2WithHmacSHA256");
byte[] derivedKey = keyFactory.generateSecret(spec).getEncoded();
System.out.println("PBKDF2 key: " + Hex.toHexString(derivedKey));
PBKDF2 derived key: 632c2812e46d4604102ba7618e9d6d7d](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-21-2048.jpg)
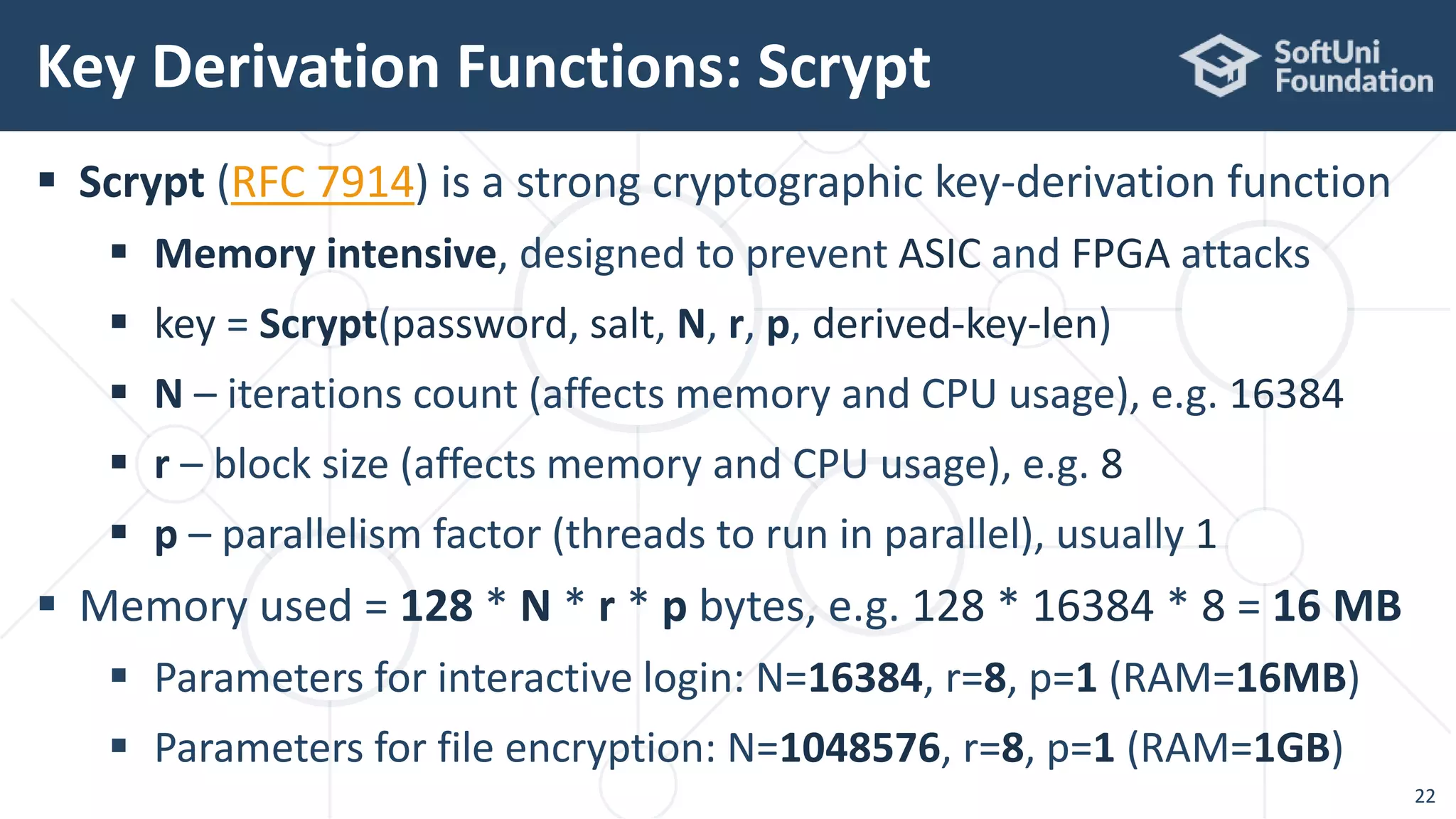
![Scrypt in Java – Example
23
// One-time registration of the "BouncyCastle" JCA provider
Security.addProvider(new BouncyCastleProvider());
ScryptKeySpec spec = new ScryptKeySpec(
"password".toCharArray(), "salt".getBytes(),
16384, 8, 1, 128);
var keyFact = SecretKeyFactory.getInstance("Scrypt");
byte[] derivedKey = keyFact.generateSecret(spec).getEncoded();
System.out.println("Scrypt: " + Hex.toHexString(derivedKey));
Scrypt: 745731af4484f323968969eda289aeee](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-23-2048.jpg)
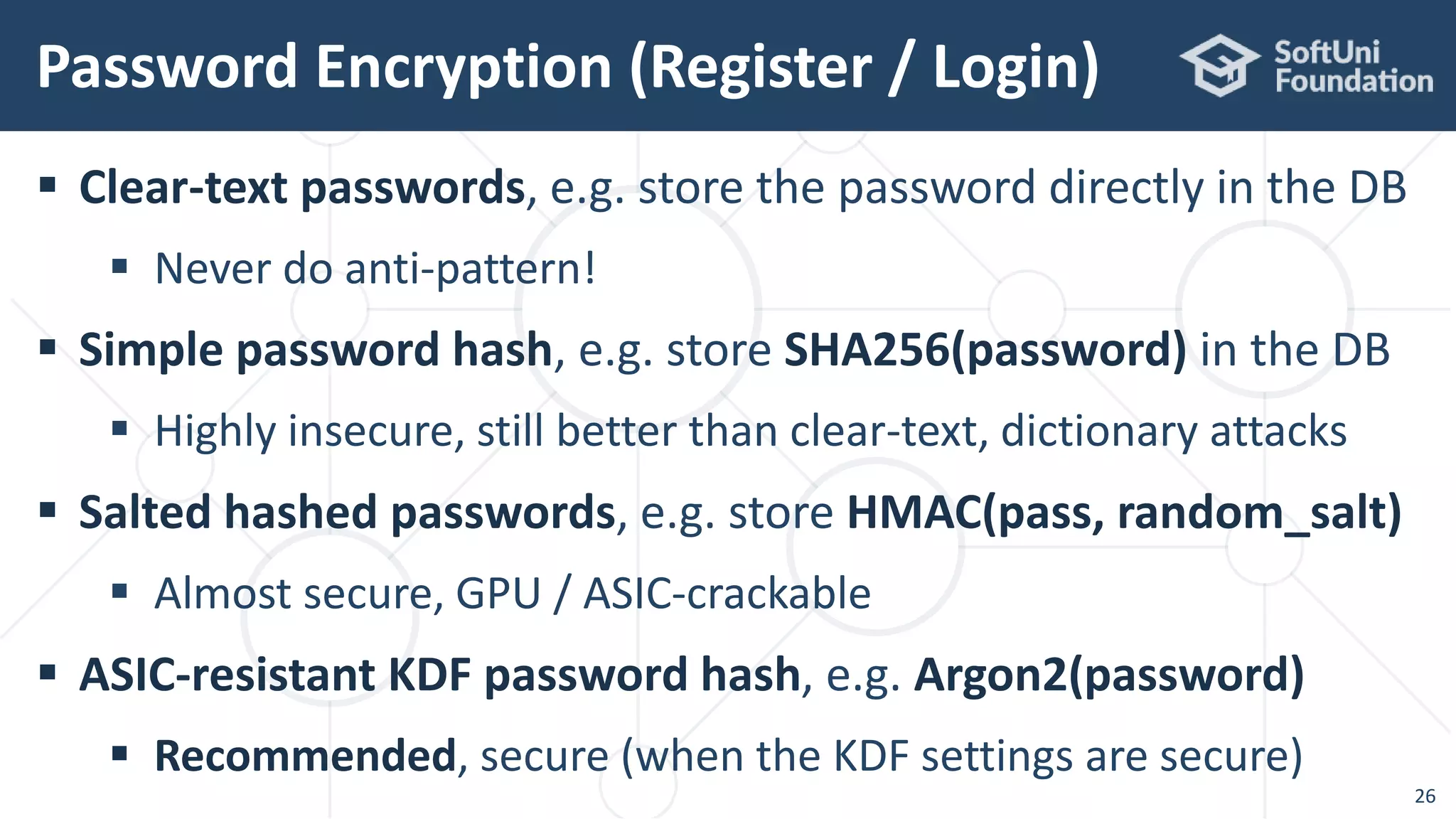
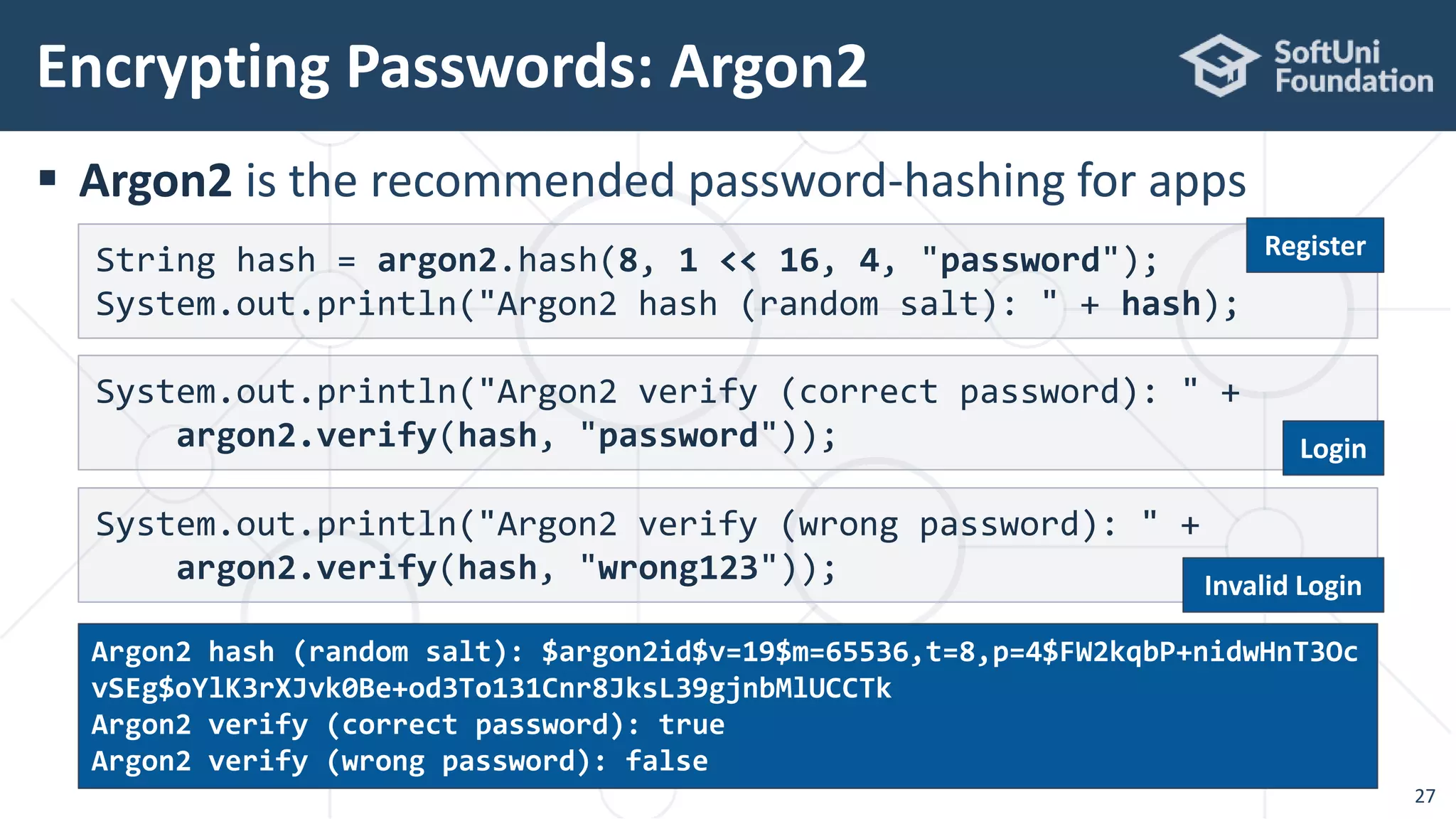
![Argon2 in Java – Example
25
import de.mkammerer.argon2.Argon2Advanced;
import de.mkammerer.argon2.Argon2Factory;
import org.bouncycastle.util.encoders.Hex;
Argon2Advanced argon2 = Argon2Factory.createAdvanced(
Argon2Factory.Argon2Types.ARGON2id);
byte[] hash = argon2.rawHash(16, 1 << 15,
2, "password", "some salt".getBytes());
System.out.println("Argon2 hash: " + Hex.toHexString(hash));
Argon2 hash:
157f21dd3fdf7bafb76d2923ccaffa0b7be7cbae394709474d2bc66ee7b09d3e](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-25-2048.jpg)
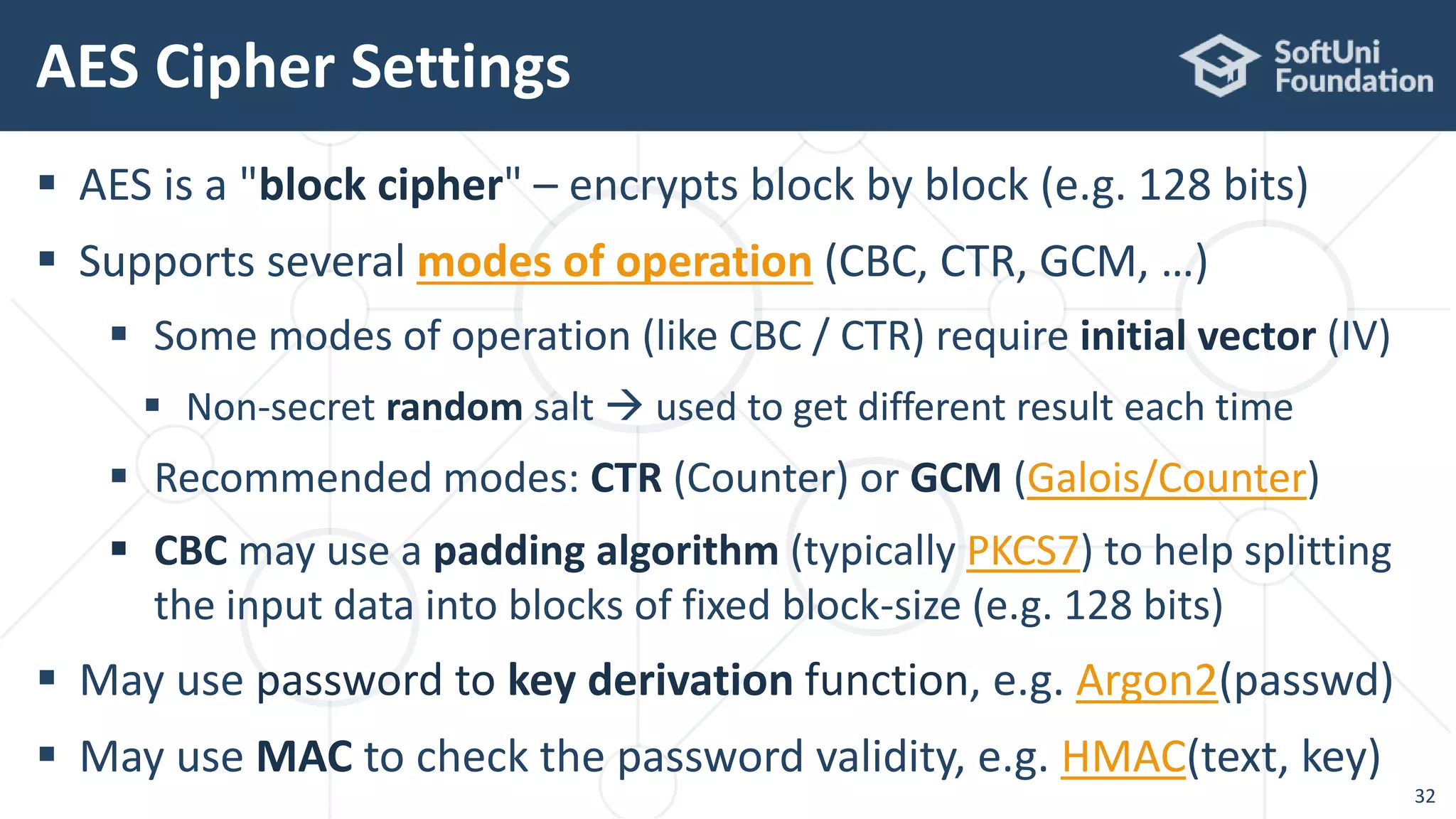
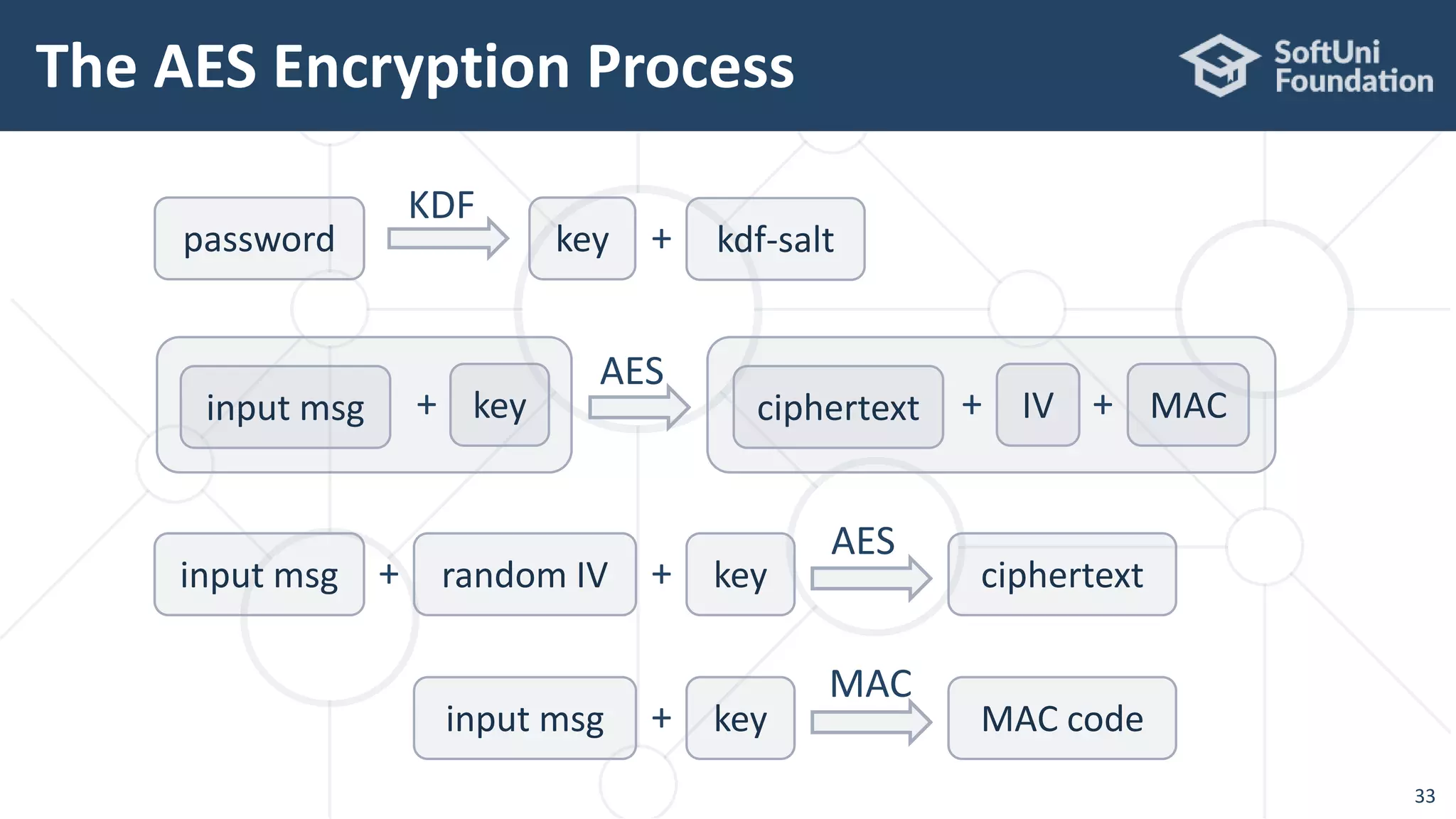
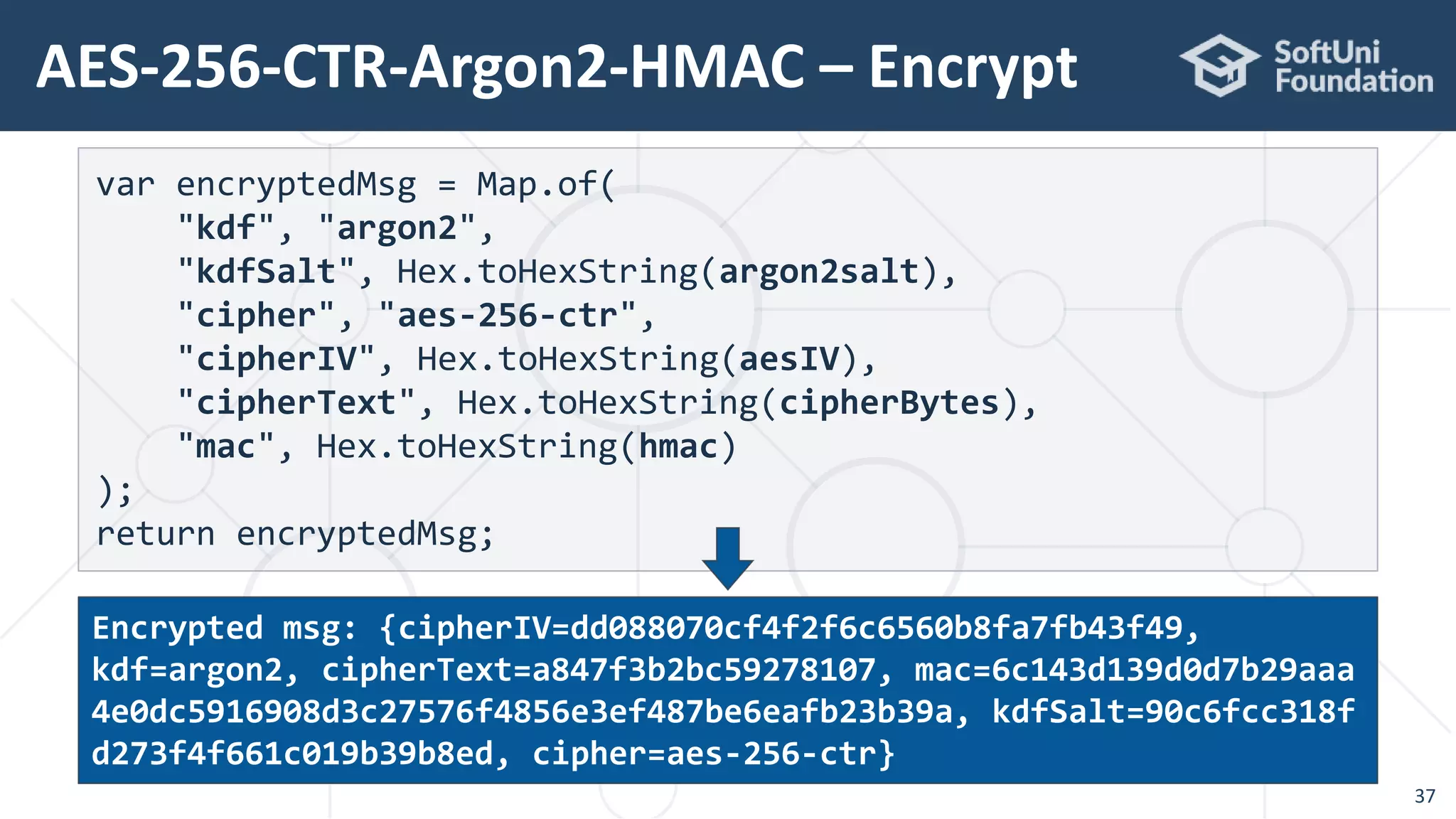
![AES-256-CTR-Argon2-HMAC – Encrypt
35
static Map<String, String> aes256CtrArgon2HMacEncrypt(
String plainText, String password) throws Exception {
// Derive a secret key from the encryption password
SecureRandom rand = new SecureRandom();
byte[] argon2salt = new byte[16];
rand.nextBytes(argon2salt); // Generate 128-bit salt
byte[] argon2hash = Argon2Factory.createAdvanced(
Argon2Factory.Argon2Types.ARGON2id).rawHash(16,
1 << 15, 2, password, argon2salt);
Key secretKey = new SecretKeySpec(argon2hash, "AES");](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-35-2048.jpg)
![AES-256-CTR-Argon2-HMAC – Encrypt
36
// AES encryption: {plaintext + IV + secretKey} -> ciphertext
byte[] aesIV = new byte[16];
rand.nextBytes(aesIV); // Generate 128-bit IV (salt)
IvParameterSpec ivSpec = new IvParameterSpec(aesIV);
Cipher cipher = Cipher.getInstance("AES/CTR/NoPadding");
cipher.init(Cipher.ENCRYPT_MODE, secretKey, ivSpec);
byte[] plainTextBytes = plainText.getBytes("utf8");
byte[] cipherBytes = cipher.doFinal(plainTextBytes);
// Calculate the MAC of the plaintext with the argon2hash
Mac mac = Mac.getInstance("HmacSHA256");
Key macKey = new SecretKeySpec(argon2hash, "HmacSHA256");
mac.init(macKey);
byte[] hmac = mac.doFinal(plainText.getBytes("utf8"));](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-36-2048.jpg)
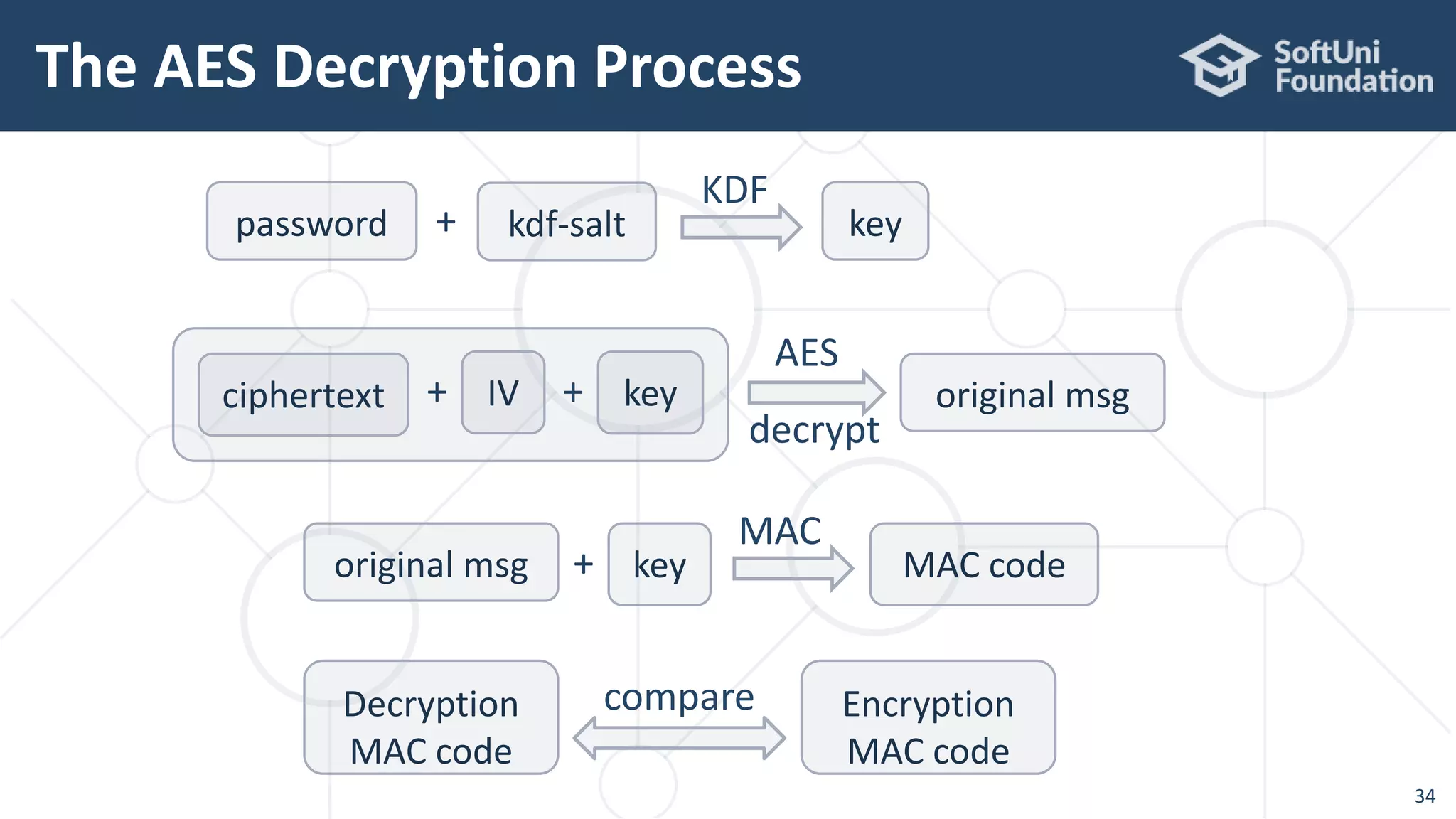
![AES-256-CTR-Argon2-HMAC – Decrypt
38
static String aes256CtrArgon2HMacDecrypt(Map<String, String>
encryptedMsg, String password) throws Exception {
// Derive the secret key from the encryption password with argon2salt
byte[] argon2salt = Hex.decode(encryptedMsg.get("kdfSalt"));
byte[] argon2hash = Argon2Factory.createAdvanced(
Argon2Factory.Argon2Types.ARGON2id).rawHash(16,
1 << 15, 2, password, argon2salt);](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-38-2048.jpg)
![AES-256-CTR-Argon2-HMAC – Decrypt
39
// AES decryption: {cipherText + IV + secretKey} -> plainText
byte[] aesIV = Hex.decode(encryptedMsg.get("cipherIV"));
IvParameterSpec ivSpec = new IvParameterSpec(aesIV);
Cipher cipher = Cipher.getInstance("AES/CTR/NoPadding");
Key secretKey = new SecretKeySpec(argon2hash, "AES");
cipher.init(Cipher.DECRYPT_MODE, secretKey, ivSpec);
byte[] cipherTextBytes =
Hex.decode(encryptedMsg.get("cipherText"));
byte[] plainTextBytes = cipher.doFinal(cipherTextBytes);
String plainText = new String(plainTextBytes, "utf8");](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-39-2048.jpg)
![AES-256-CTR-Argon2-HMAC – Decrypt
40
// Calculate & check the MAC code: HMAC(plaintext, argon2hash)
Mac mac = Mac.getInstance("HmacSHA256");
Key macKey = new SecretKeySpec(argon2hash, "HmacSHA256");
mac.init(macKey);
byte[] hmac = mac.doFinal(plainText.getBytes("utf8"));
String decodedMac = Hex.toHexString(hmac);
String cipherTextMac = encryptedMsg.get("mac");
if (! decodedMac.equals(cipherTextMac)) throw new
InvalidKeyException("MAC does not match: maybe wrong password");
return plainText;
}](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-40-2048.jpg)
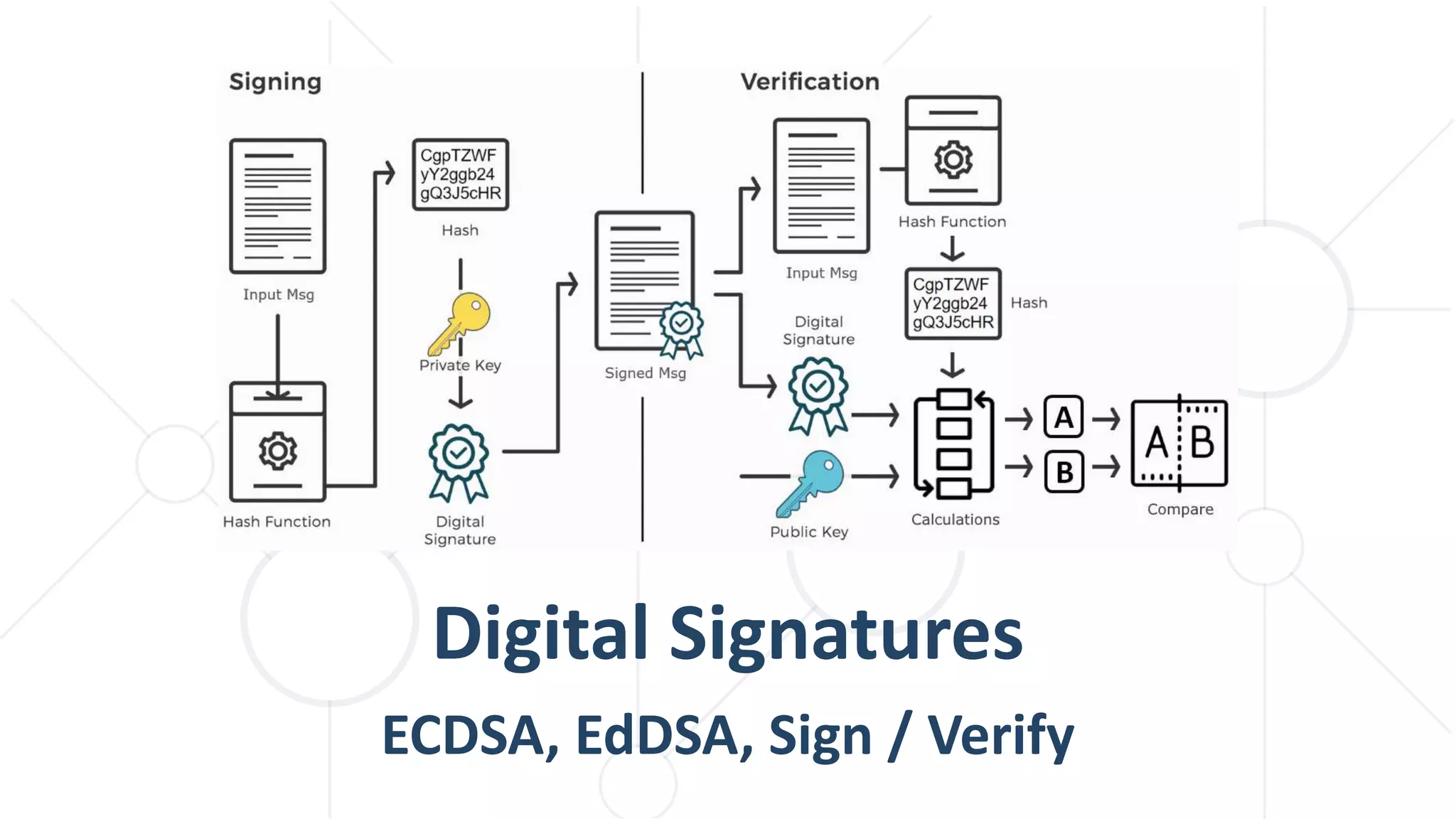

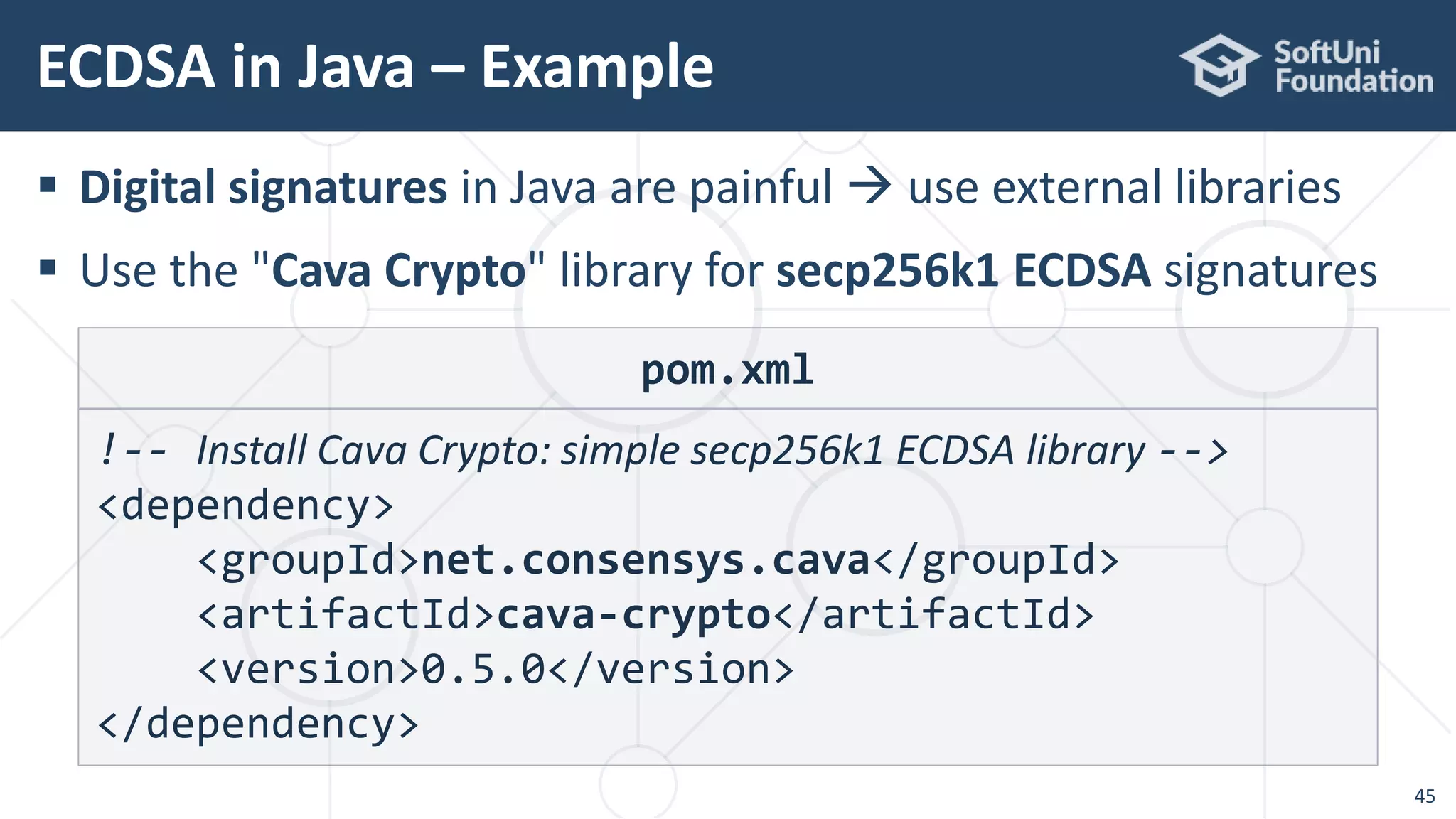
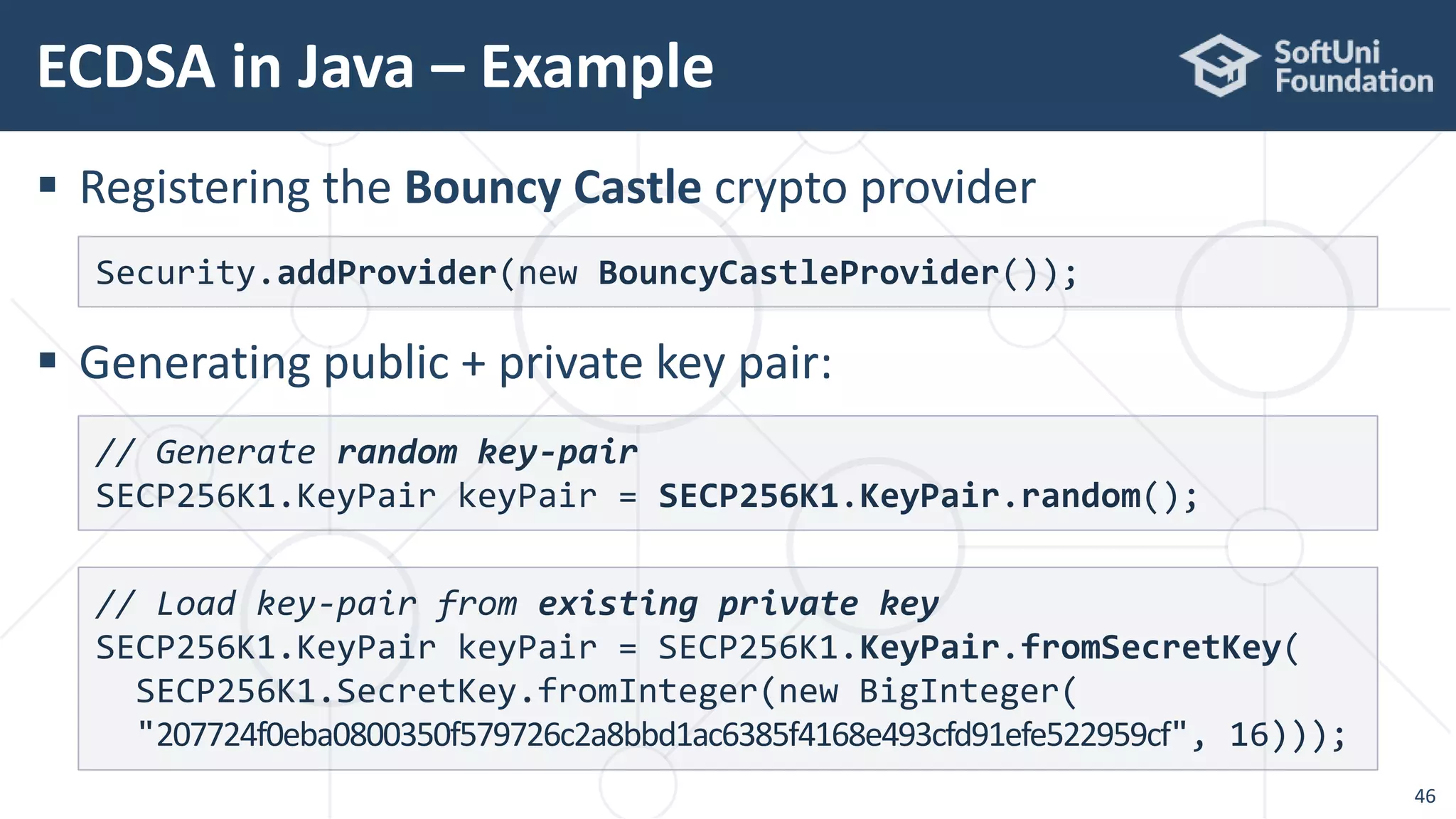
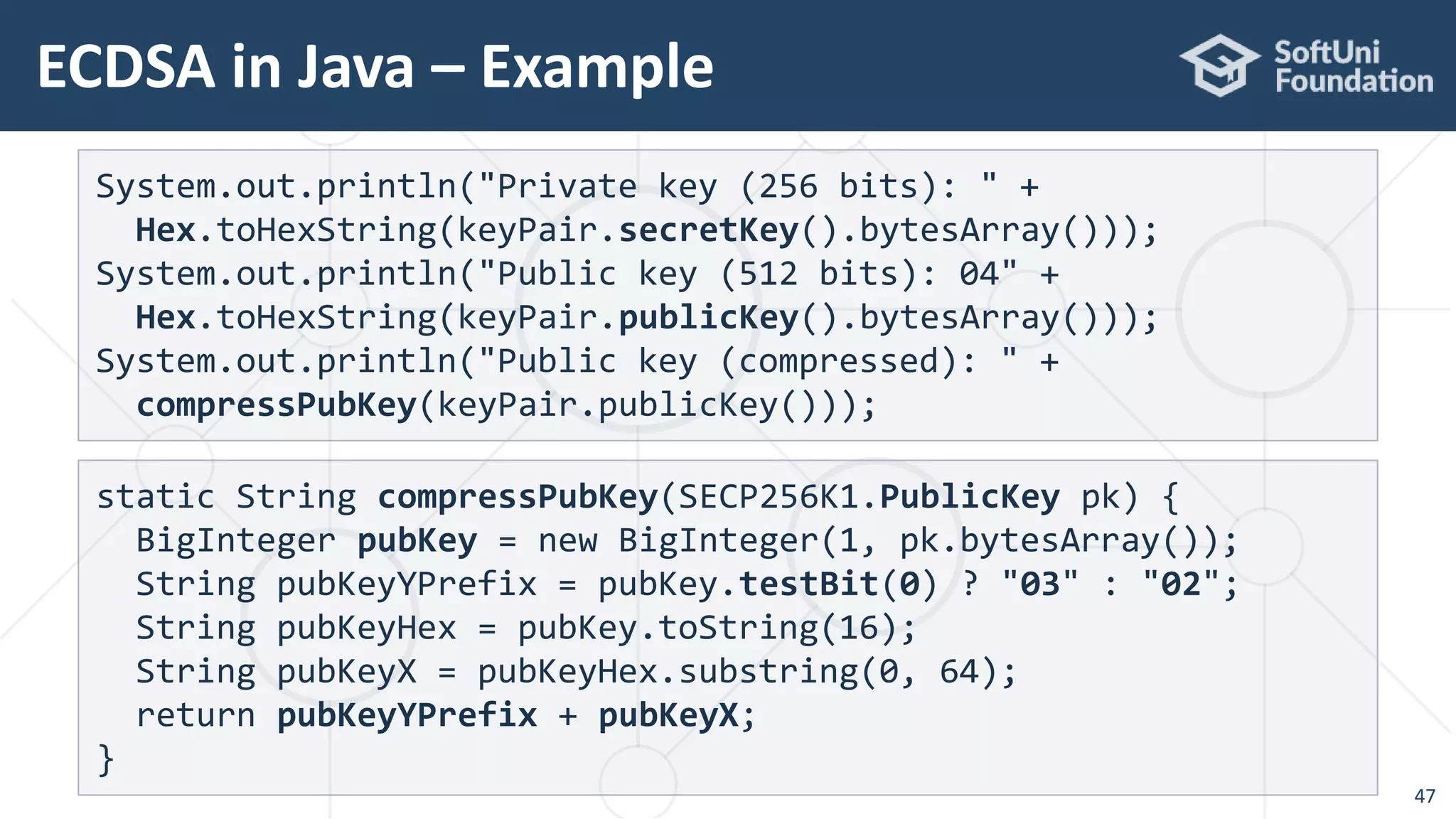
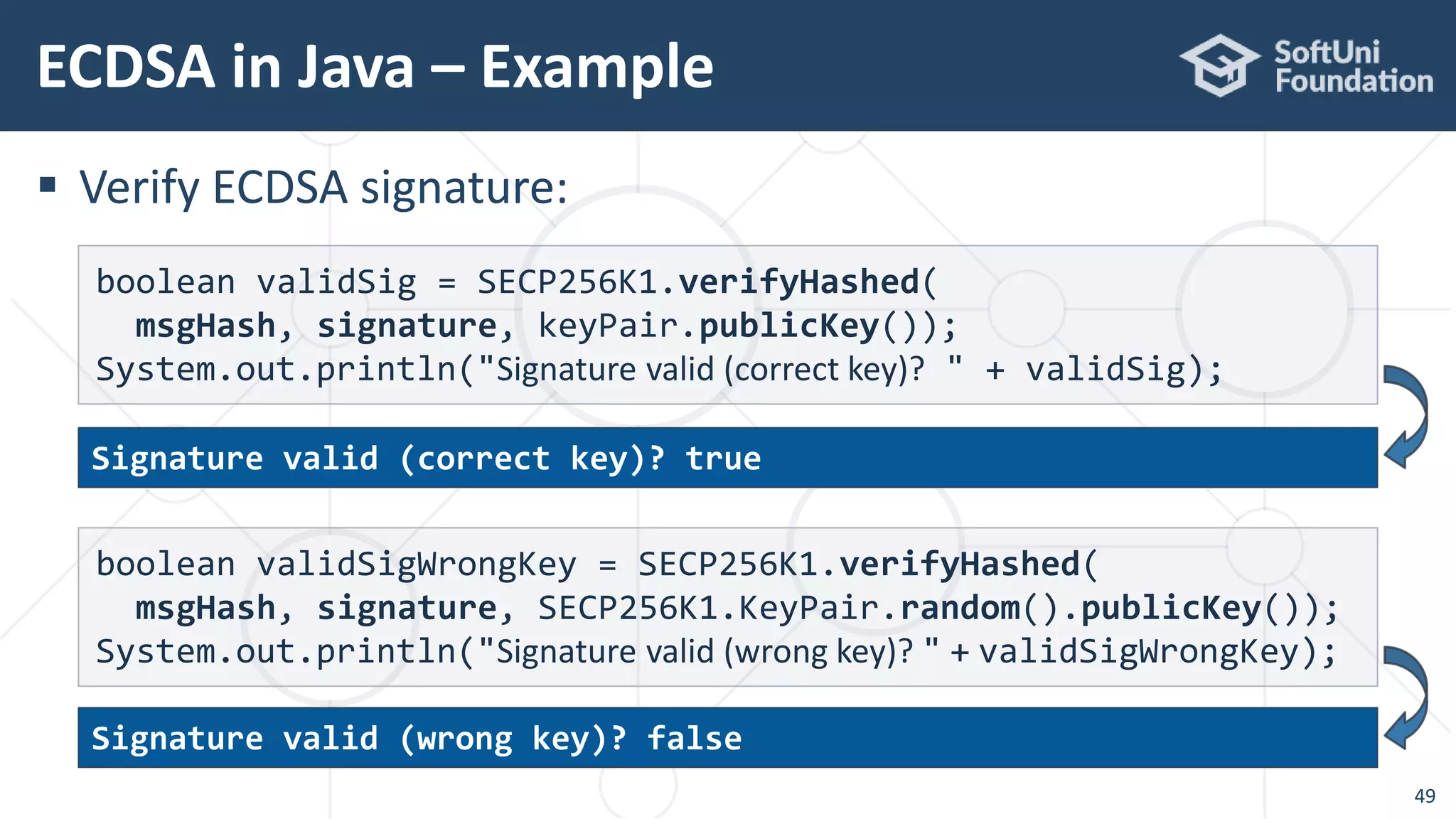
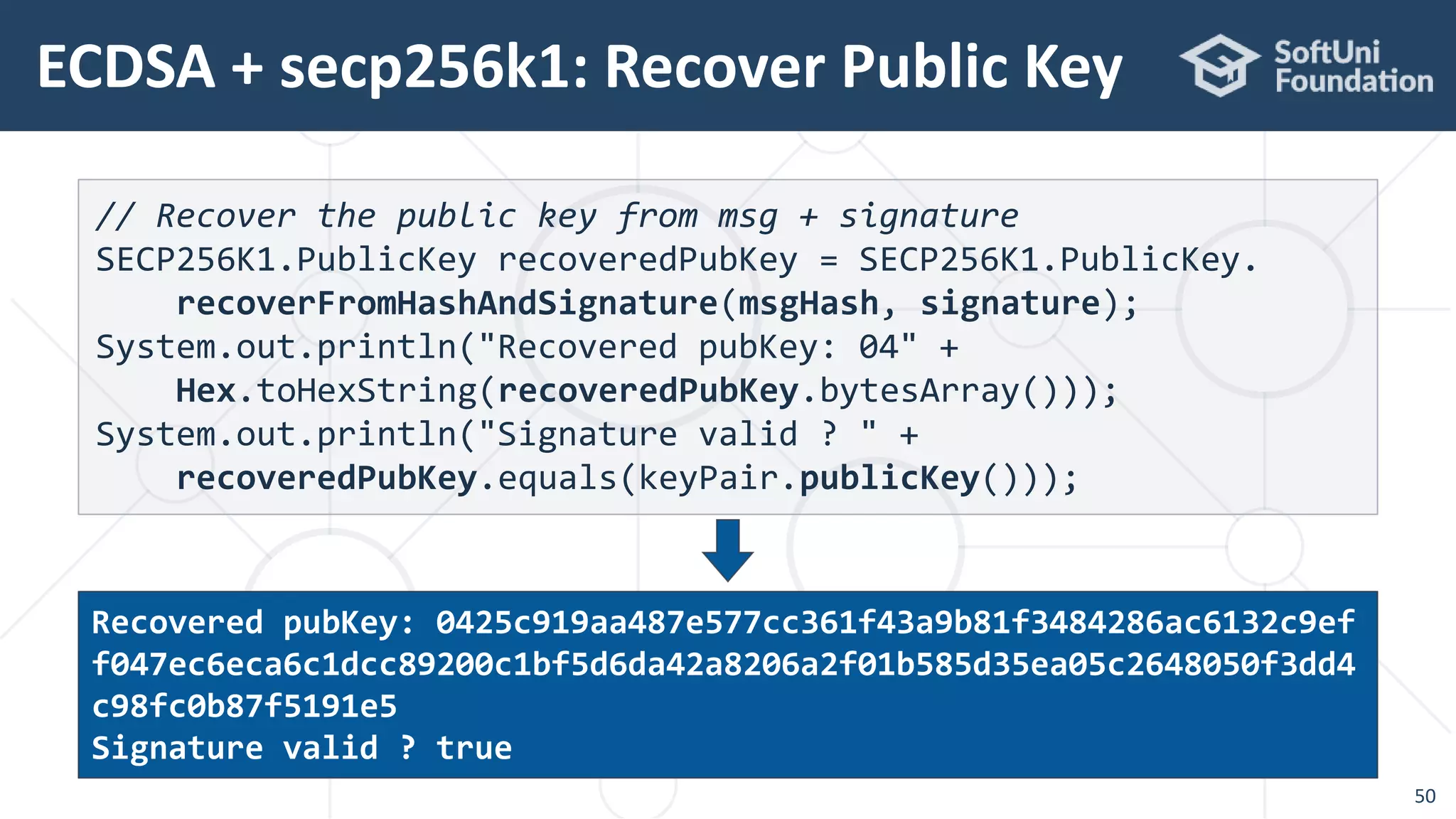
![ Signing a message with SHA256 + ECDSA with secp256k1
ECDSA in Java – Example
48
String msg = "Message for signing";
byte[] msgHash = Hash.sha2_256(msg.getBytes());
var signature = SECP256K1.signHashed(msgHash, keyPair);
System.out.println("Msg: " + msg);
System.out.println("Msg hash: " + Hex.toHexString(msgHash));
System.out.printf("Signature: [r = %s, s = %s, v = %d]n",
signature.r().toString(16), signature.s().toString(16),
signature.v());
Signature: [r = 3ce2c58b02a06f16c849d6ac1d05e9d6dc41b92929ed2733d3
ddf060e2035c20, s = 292d5d83ffd5a46befeef33a9c6e9fc562d412e0d90934
dfb4ed0a7d80caff61, v = 0]](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-48-2048.jpg)
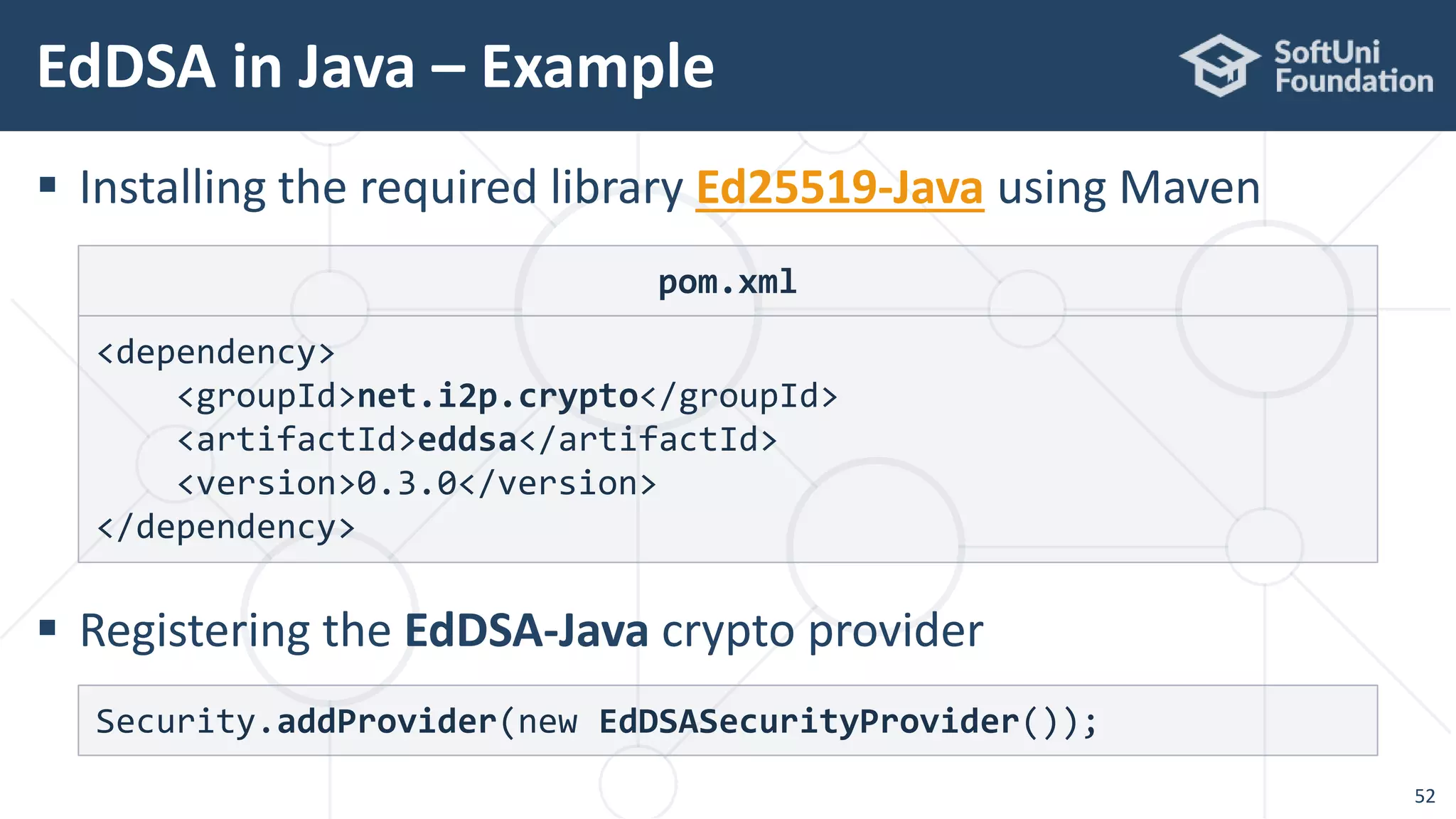
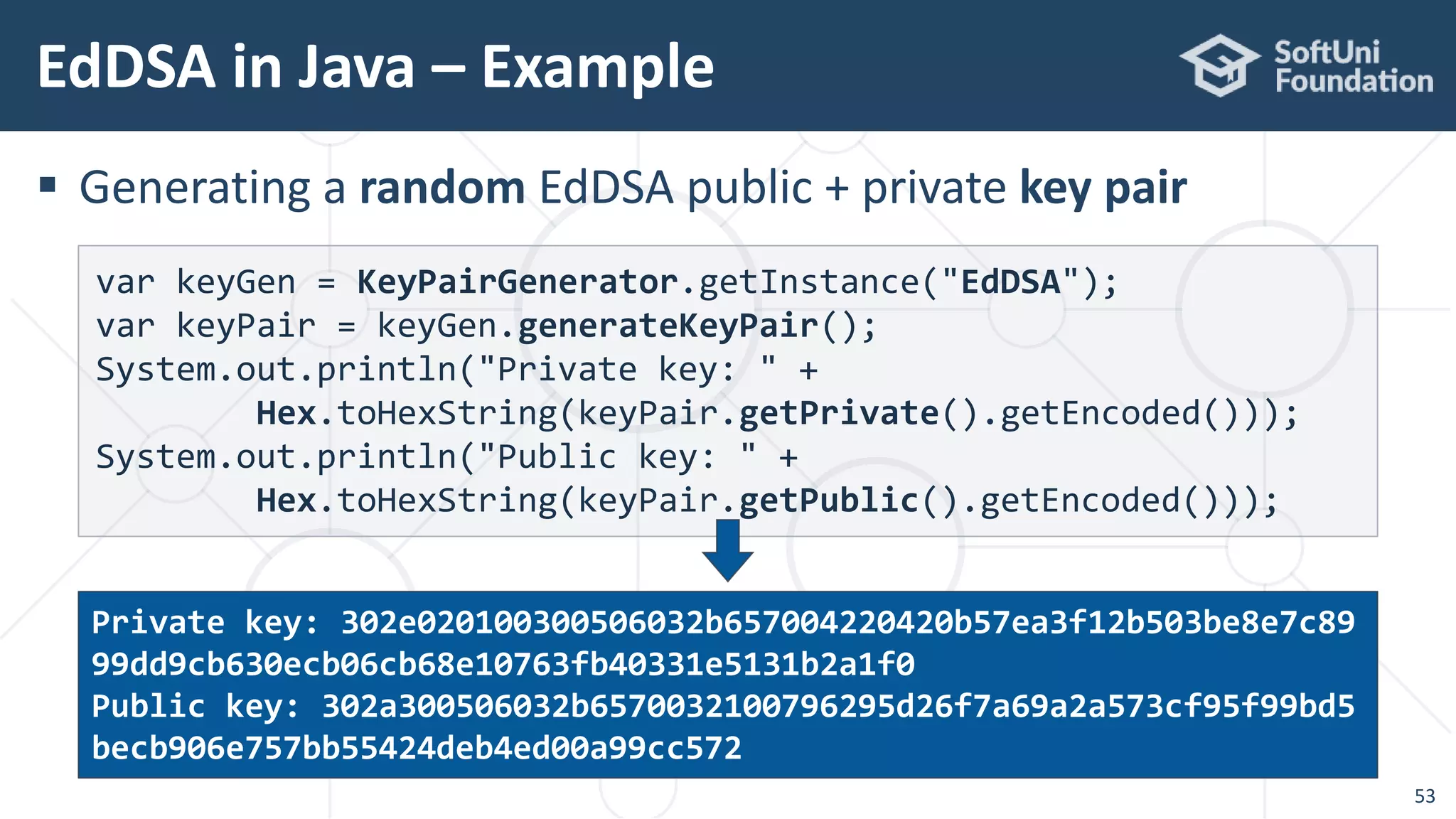
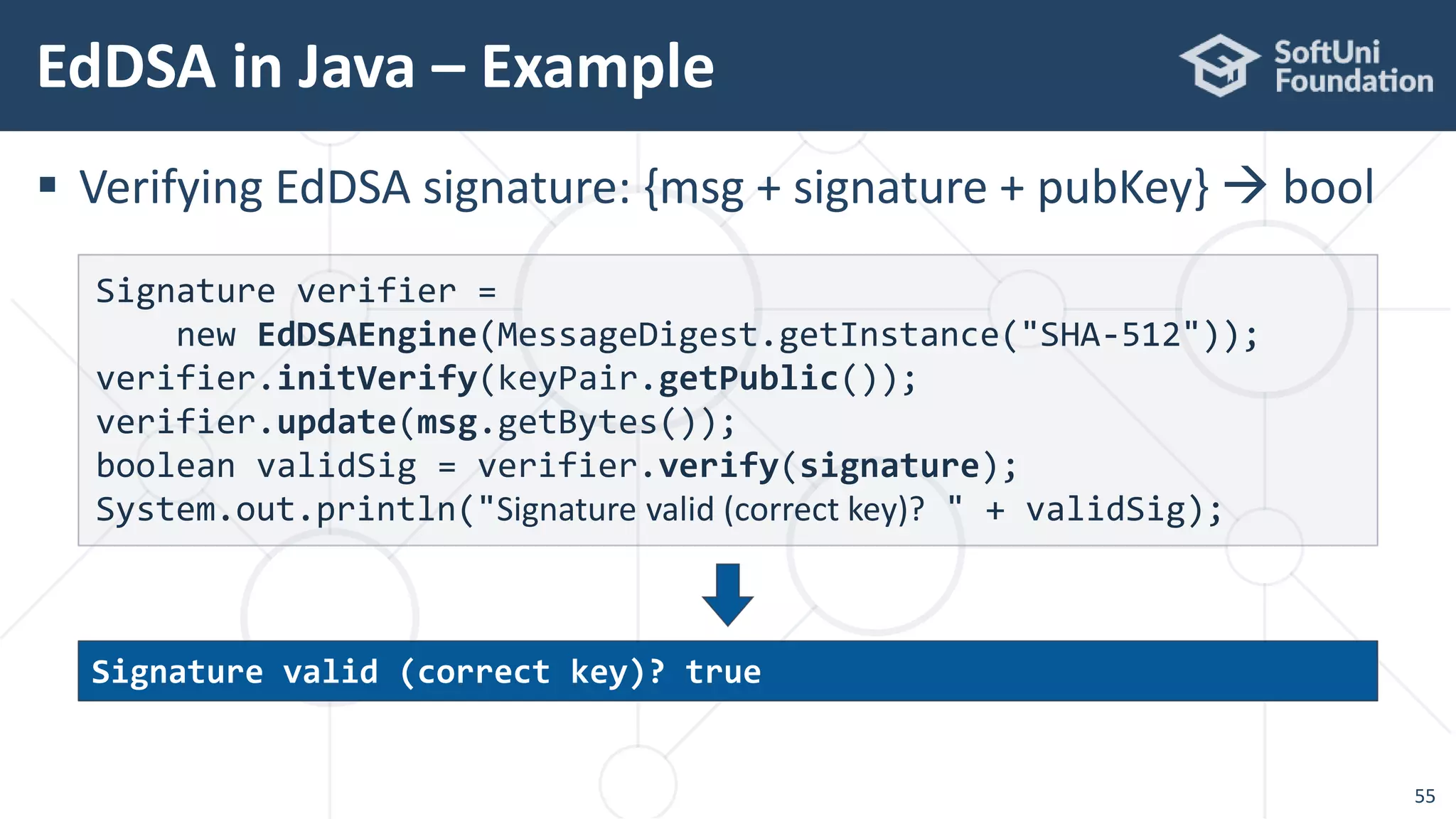
![EdDSA in Java – Example
54
Signing a message with EdDSA
String msg = "Message for signing";
Signature signer = new EdDSAEngine(
MessageDigest.getInstance("SHA-512"));
signer.initSign(keyPair.getPrivate());
signer.update(msg.getBytes());
byte[] signature = signer.sign();
System.out.println("Signature: " + Hex.toHexString(signature));
Signature: 1256d92d27b5b4e633494b86f5f55dc18155ae4eed35d5f596f1dbb
894acef0df7e2b756ef5e5681260d2f46dd1c26e180591e1ec3f9997f213ddf0ca
55c6703](https://image.slidesharecdn.com/cryptography-for-java-devs-nakov-at-jprofessionals-jan-2019-190126160909/75/Cryptography-for-Java-Developers-Nakov-jProfessionals-Jan-2019-54-2048.jpg)