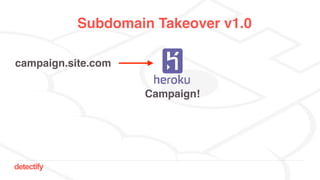
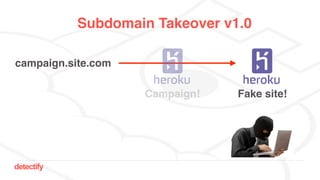
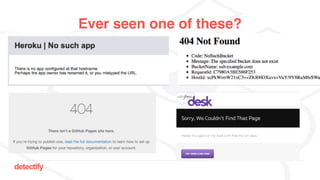
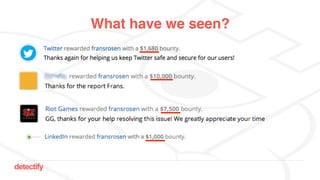
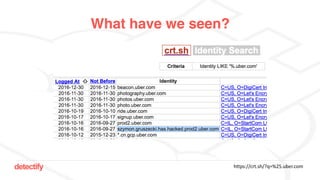
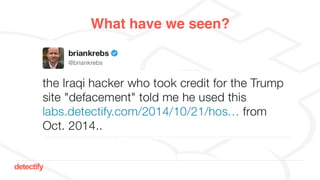
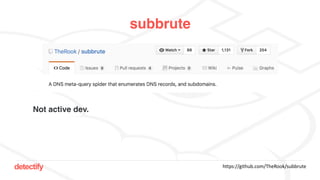
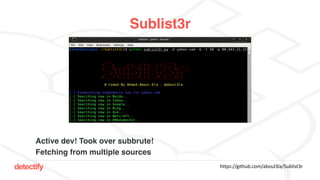
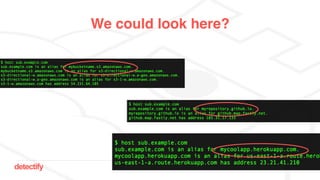
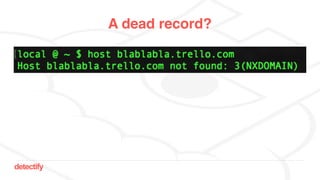
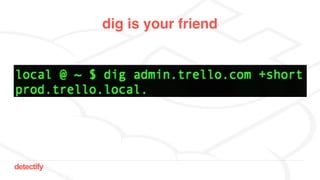
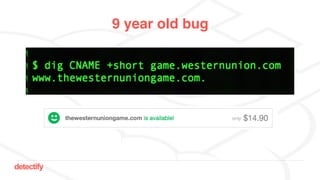
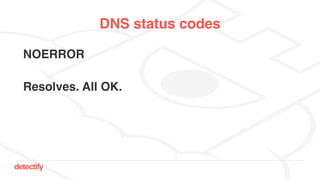
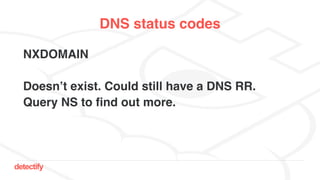
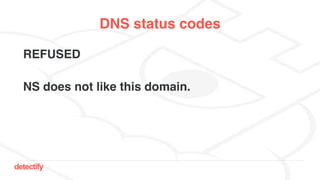
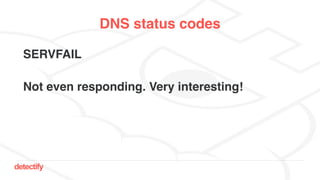
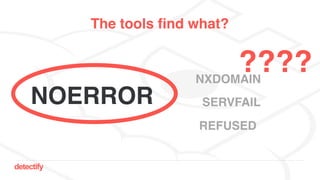
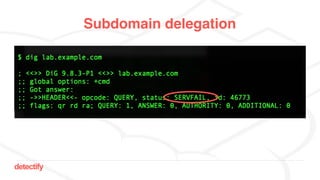
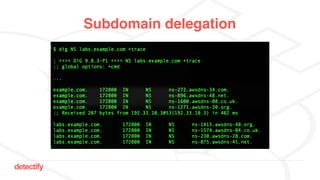
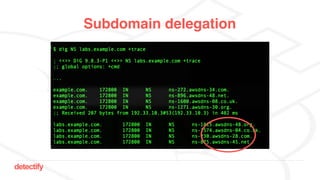
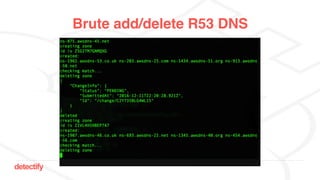
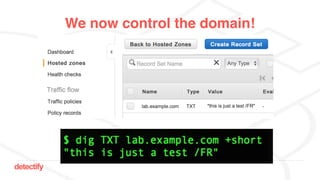
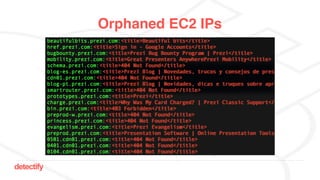
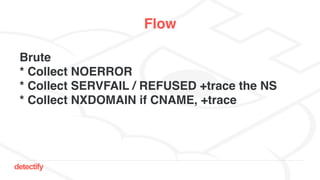
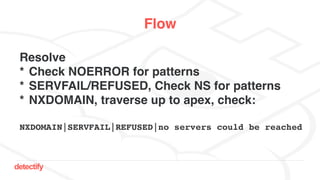
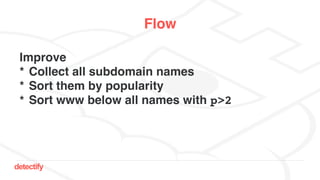
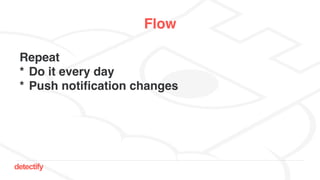
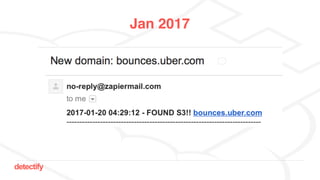
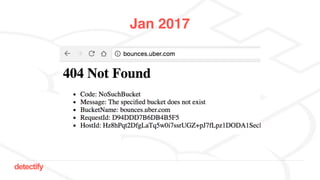
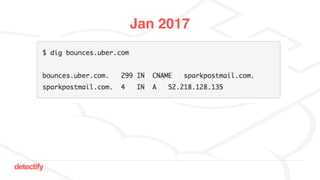
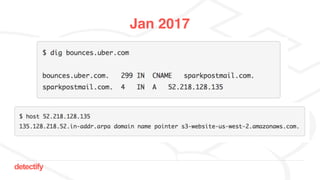
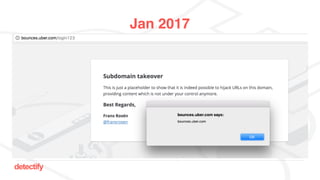
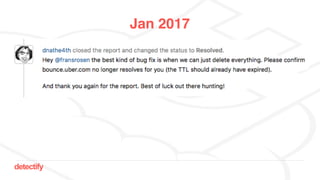
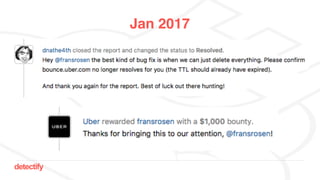
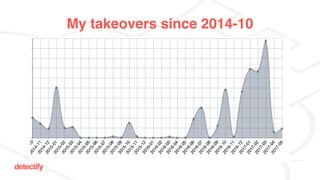
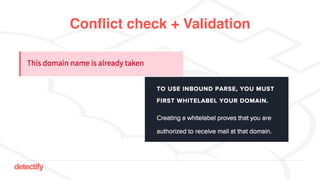
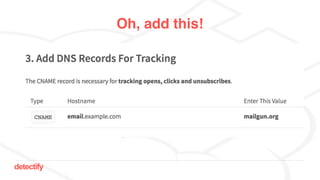
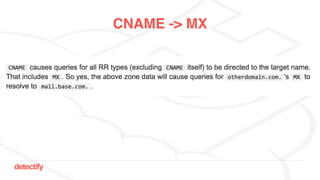
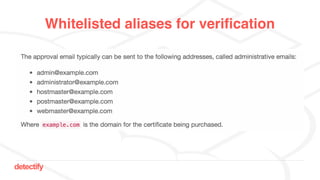
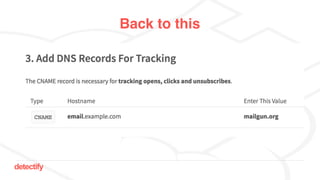
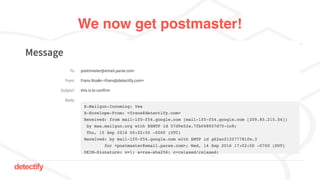
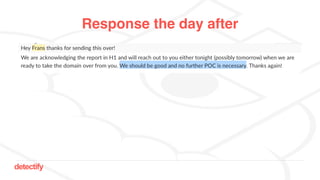
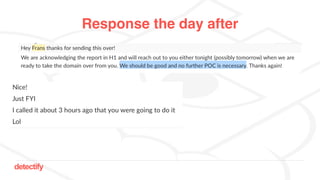
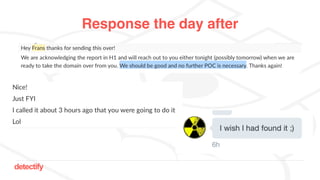
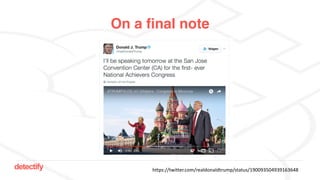
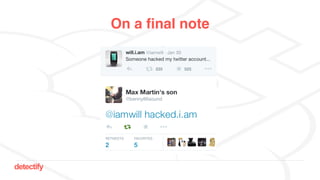
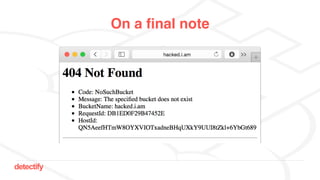
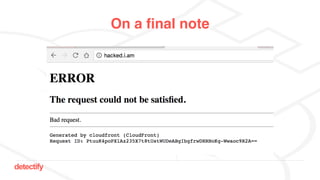
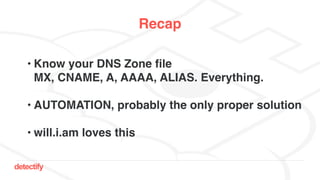
The document discusses DNS hijacking, highlighting tools and techniques used for subdomain takeover and monitoring by Detectify. It outlines past incidents, various response from service providers, and emphasizes the importance of automation and proper DNS management. The presentation includes references to several tools and reports, illustrating the evolution and challenges in combating such security vulnerabilities.