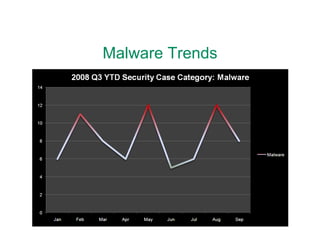
Malware analysis is important for responding quickly to security incidents and keeping costs down. Malware is the number one external threat and is adapting to evade traditional defenses like firewalls and antivirus software. When incidents do occur, organizations should have an in-house capability to analyze malware using free and open-source tools to understand the scope of infections and prevent recurrences.











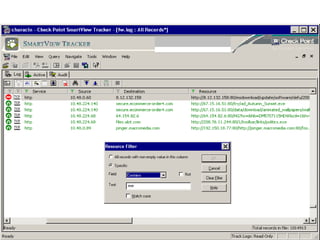

![Snort Rules alert tcp $HOME_NET any -> $EXTERNAL_NET !80 (msg: "LOCAL .exe file download on port other than 80"; flow:established; content: "GET"; depth:4; content:".exe"; nocase; classtype:misc-activity; sid:9000160; rev:1;) alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"LOCAL Obfuscated JavaScript document.write"; flow:from_server,established; content:"document.write“; nocase; pcre:"/document\.write\(\"\\[0-9][0-9]/i"; classtype:trojan-activity; sid:9000110; rev:1;) alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"LOCAL Obfuscated JavaScript unescape"; flow:from_server,established; content:"script>"; nocase; content:"unescape("; nocase; classtype:trojan-activity; sid:9000111; rev:2;) alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"LOCAL Obfuscated JavaScript eval"; flow:from_server,established; content:"script>"; nocase; content:"eval("; nocase; classtype:trojan-activity; sid:9000112; rev:2;)](https://image.slidesharecdn.com/sw-1227301263105648-8/85/Malware-Analysis-Made-Simple-16-320.jpg)