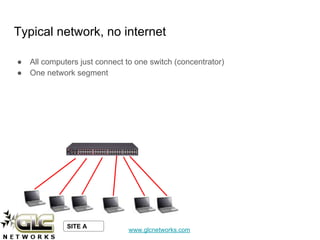
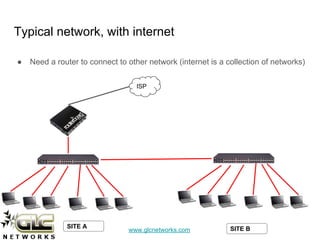
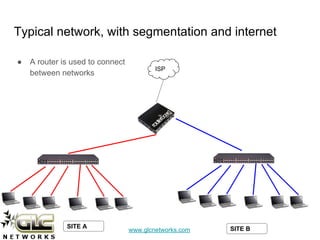
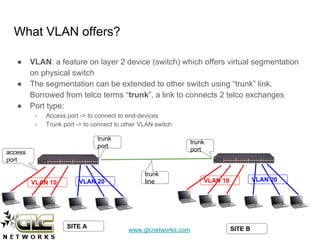
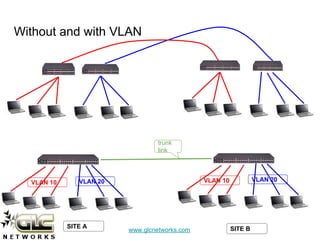
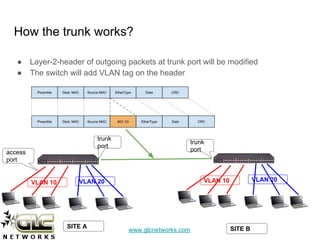
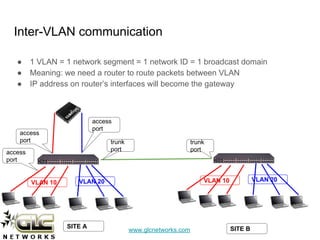
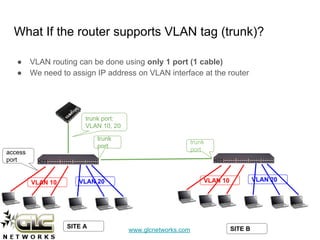
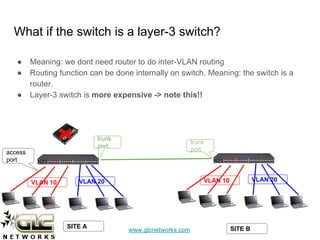
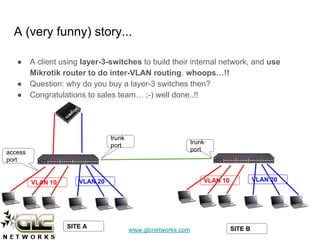
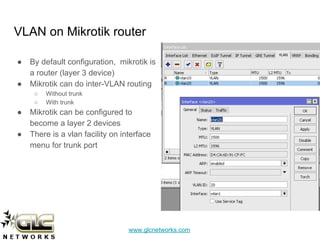
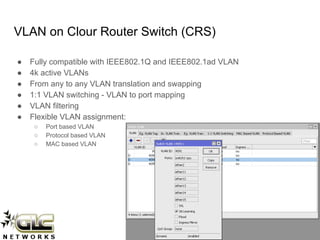
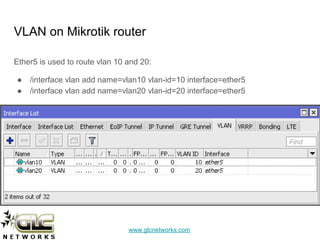
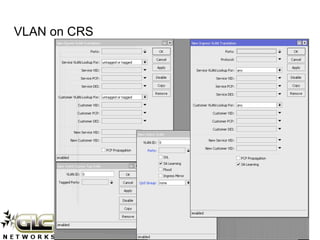
The document outlines a webinar conducted by GLC Networks on VLAN configurations using MikroTik, detailing the structure of typical networks and VLAN's role in network segmentation. It introduces MikroTik products, training certifications, and provides technical insights into VLAN implementation, including trunking and inter-VLAN routing. The session includes a demo on configuring VLANs on MikroTik routers and CRS switch, concluding with a Q&A segment.