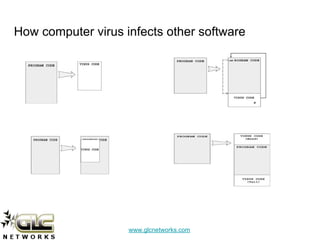
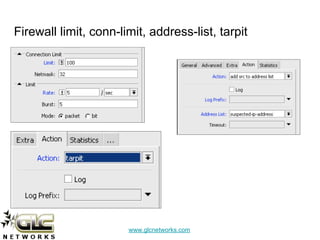
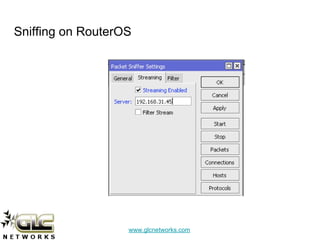
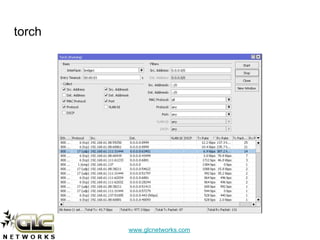
The document details a webinar on detecting network viruses using MikroTik, presented by Achmad Mardiansyah from GLC Networks in Indonesia. It covers various topics including definitions and characteristics of computer viruses, methods for monitoring networks with MikroTik, and countermeasures against viruses. Additional resources and a Q&A session are also included, along with a request for participant feedback.