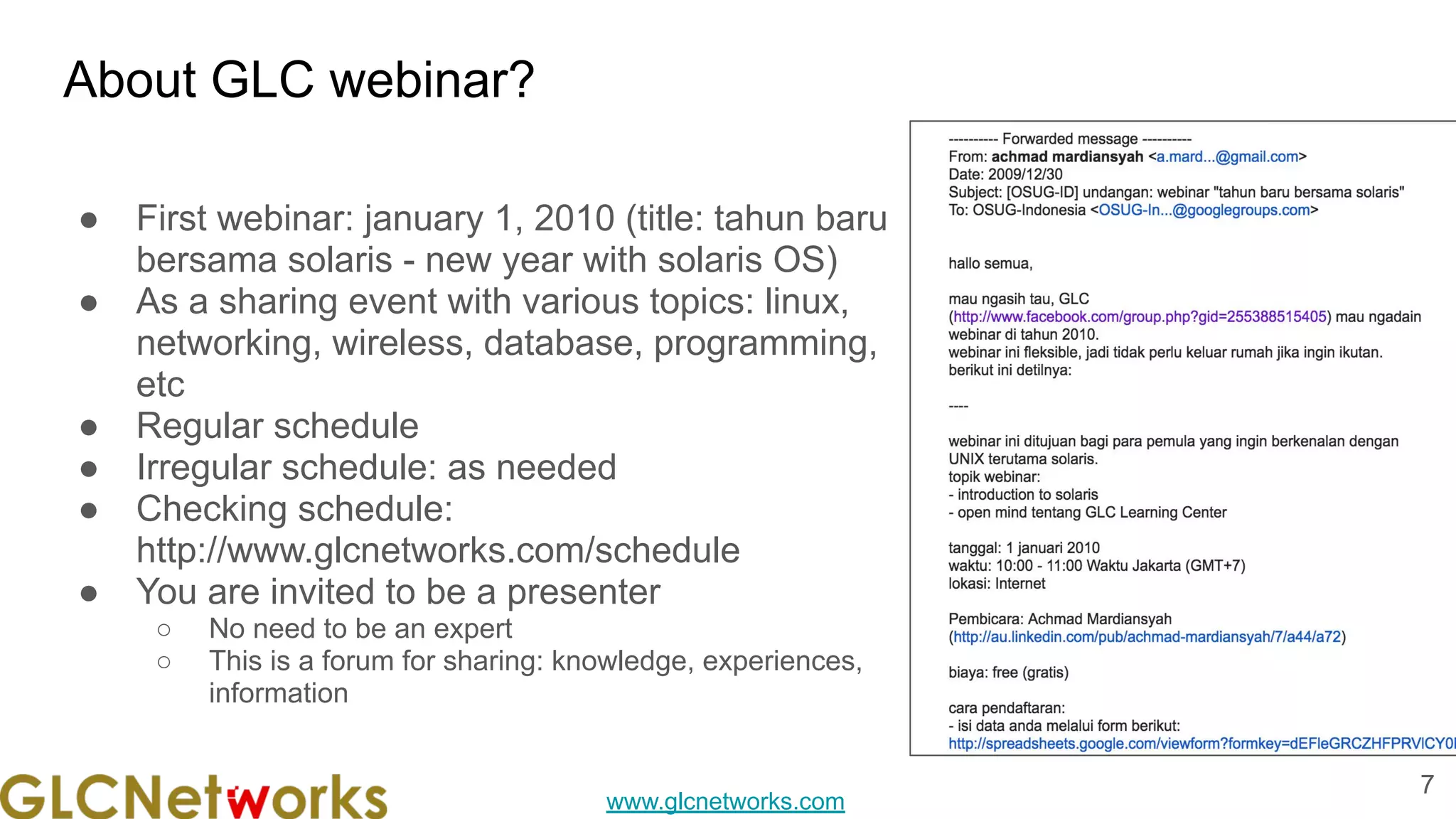
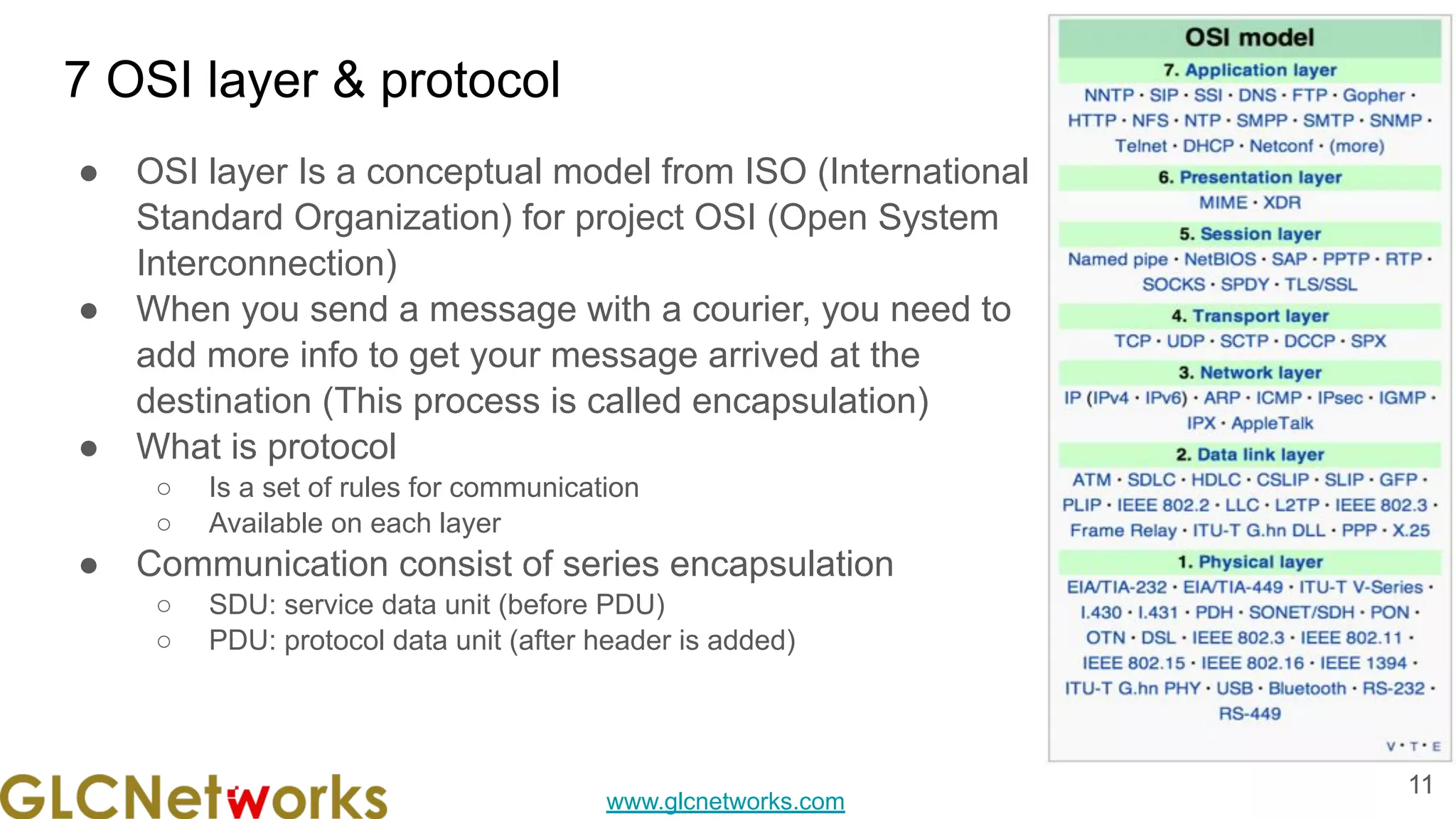
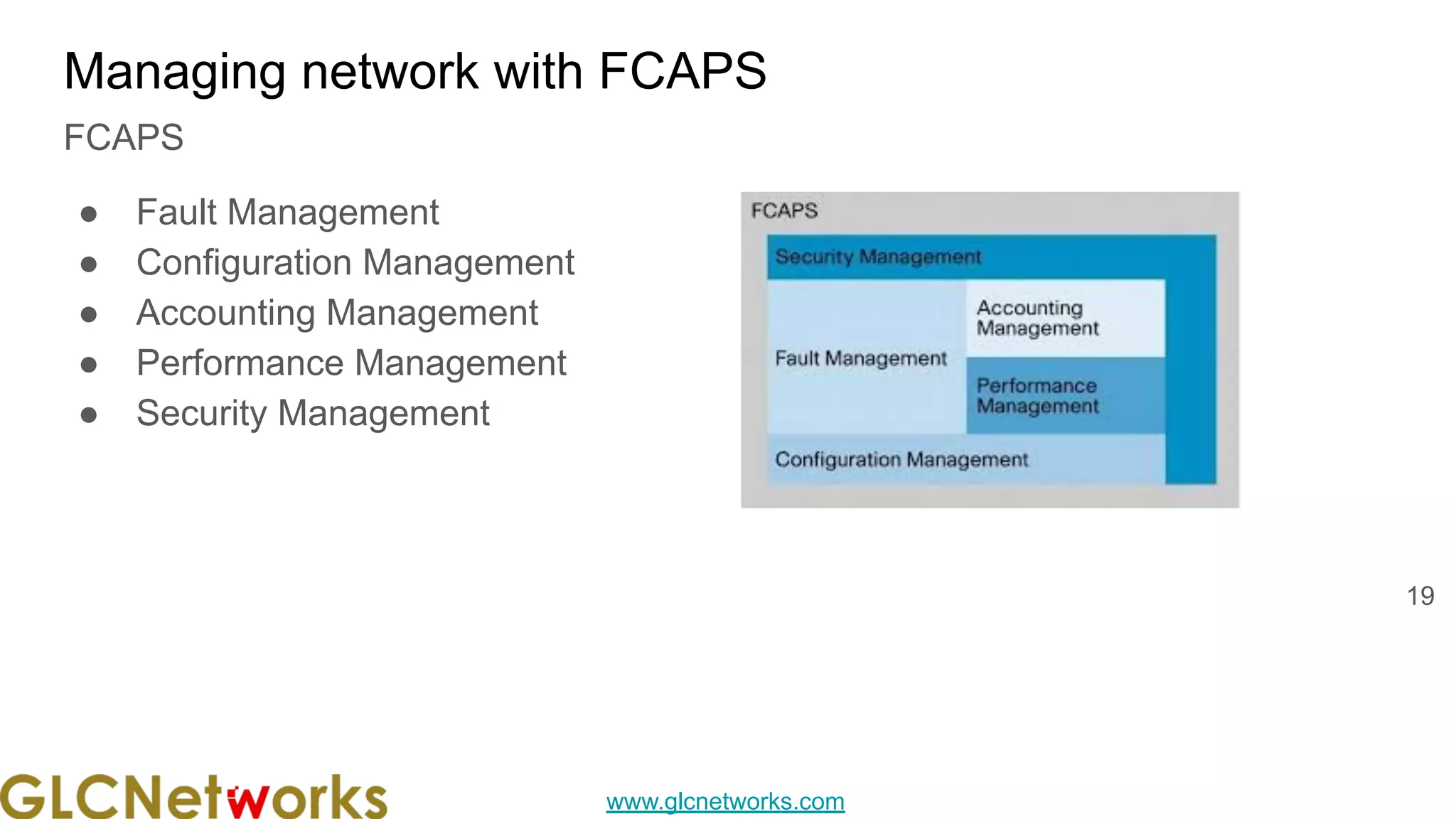
The GLC Networks webinar, held on February 22, 2022, focused on network monitoring using MikroTik's The Dude and featured practical live sessions and Q&A. The training was led by Achmad Mardiansyah, a certified trainer with extensive experience in network support and consulting. The presentation emphasized the importance of network management through various methodologies including fault, configuration, performance, and security management.