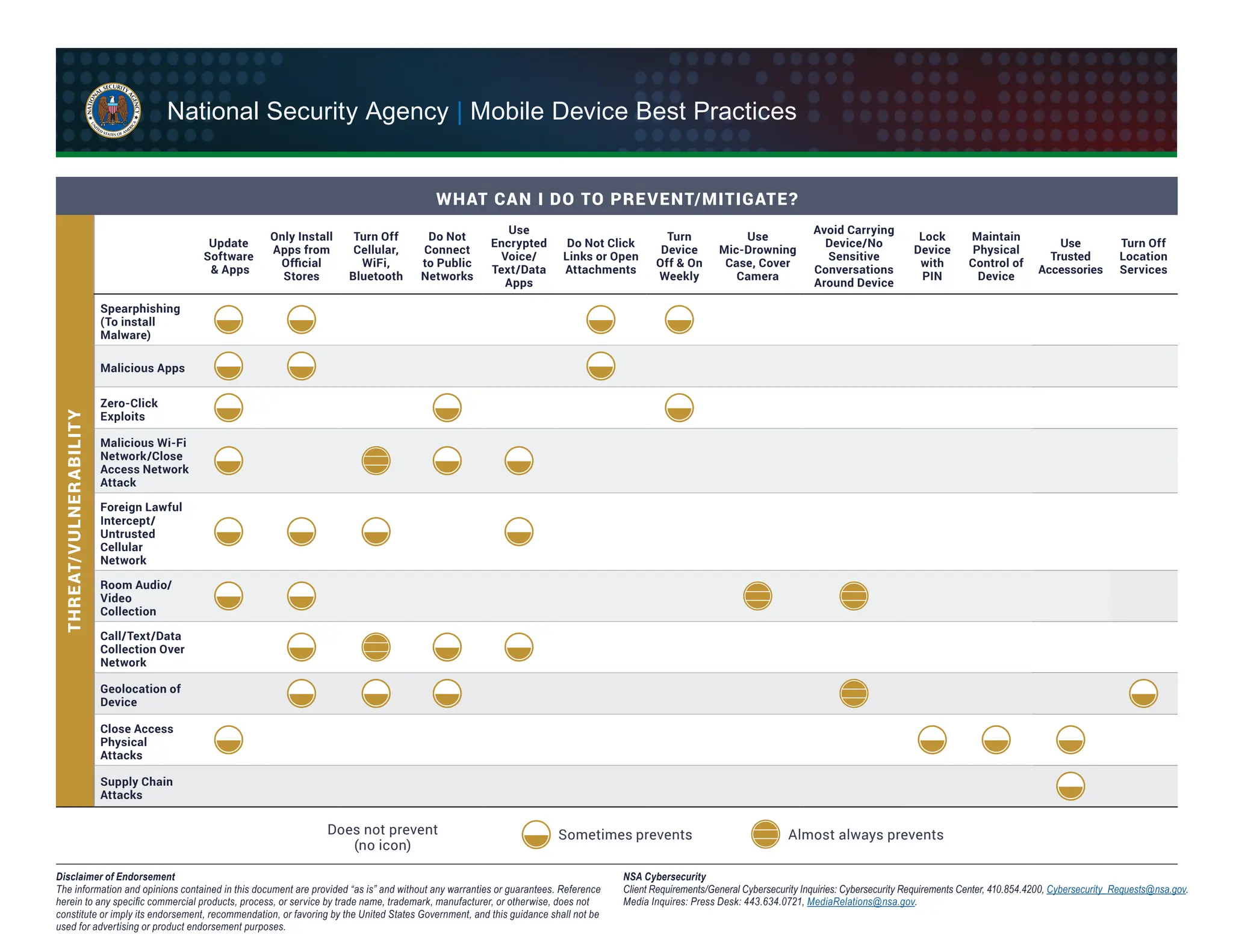
The document provides best practices for securing mobile devices against increasing threats. Key recommendations include disabling Bluetooth and Wi-Fi when not in use, avoiding public networks, using strong passwords, updating software regularly, and being cautious with applications and attachments. It emphasizes the importance of maintaining physical control over devices and protecting sensitive communications.