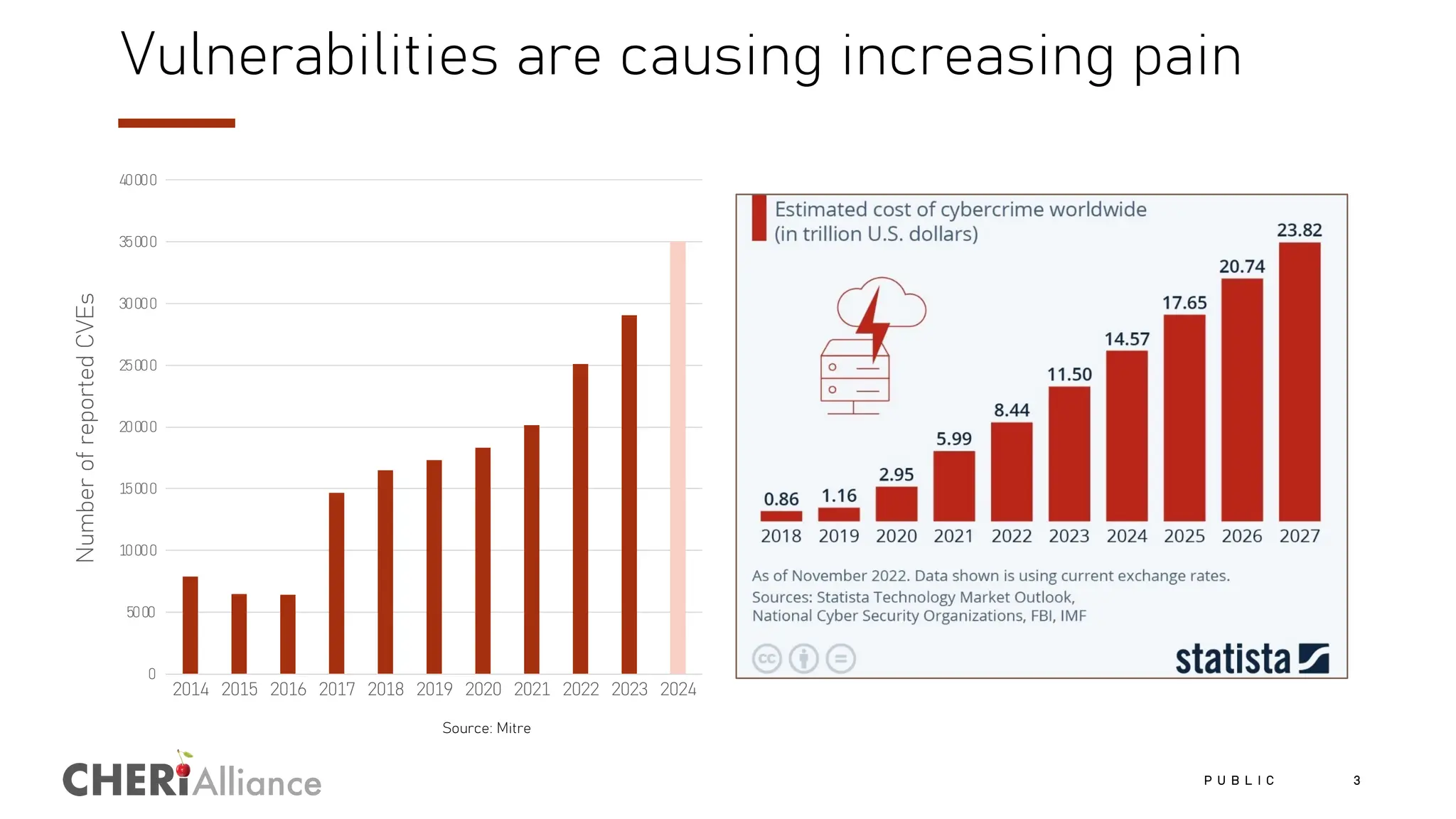
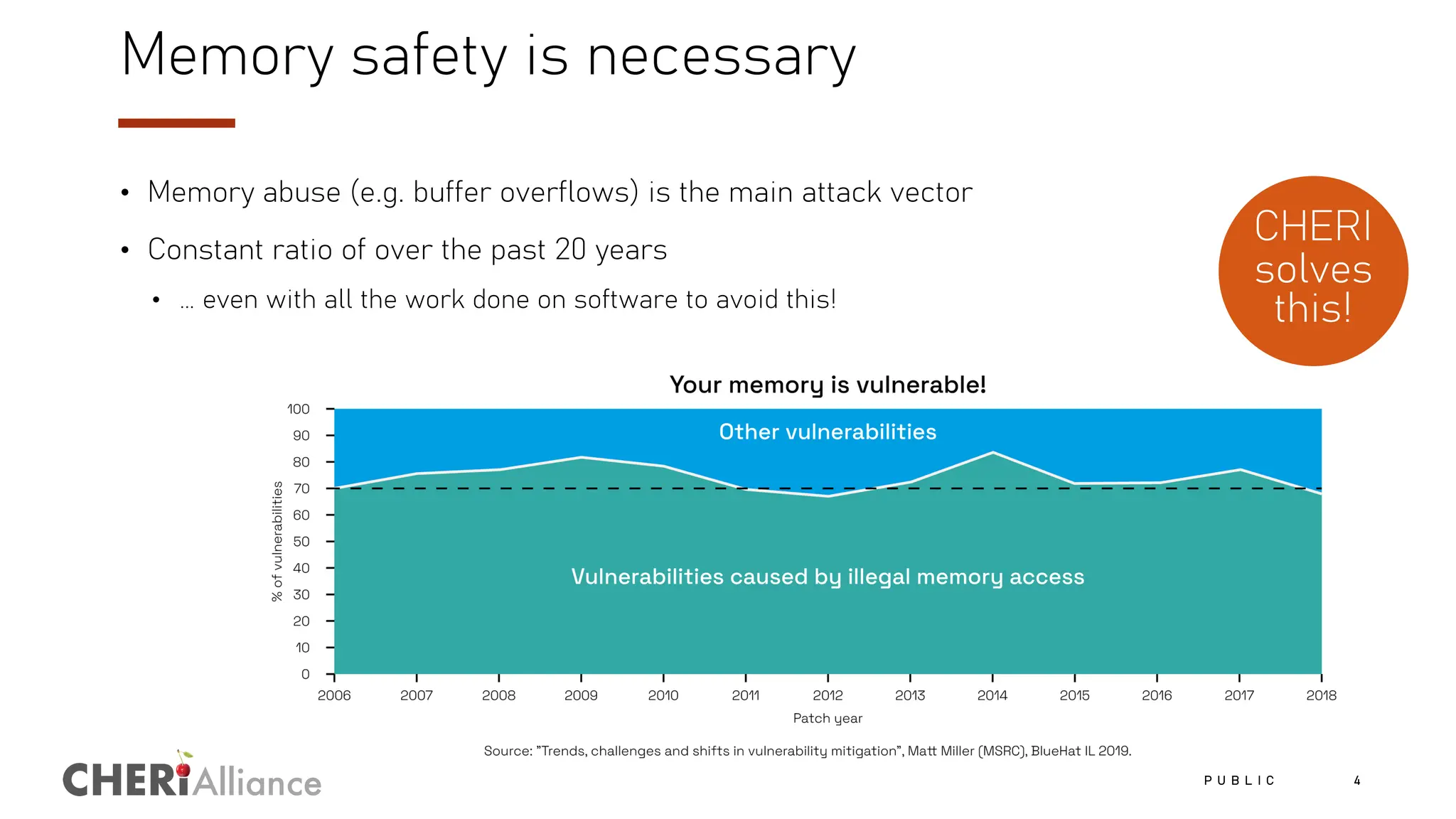
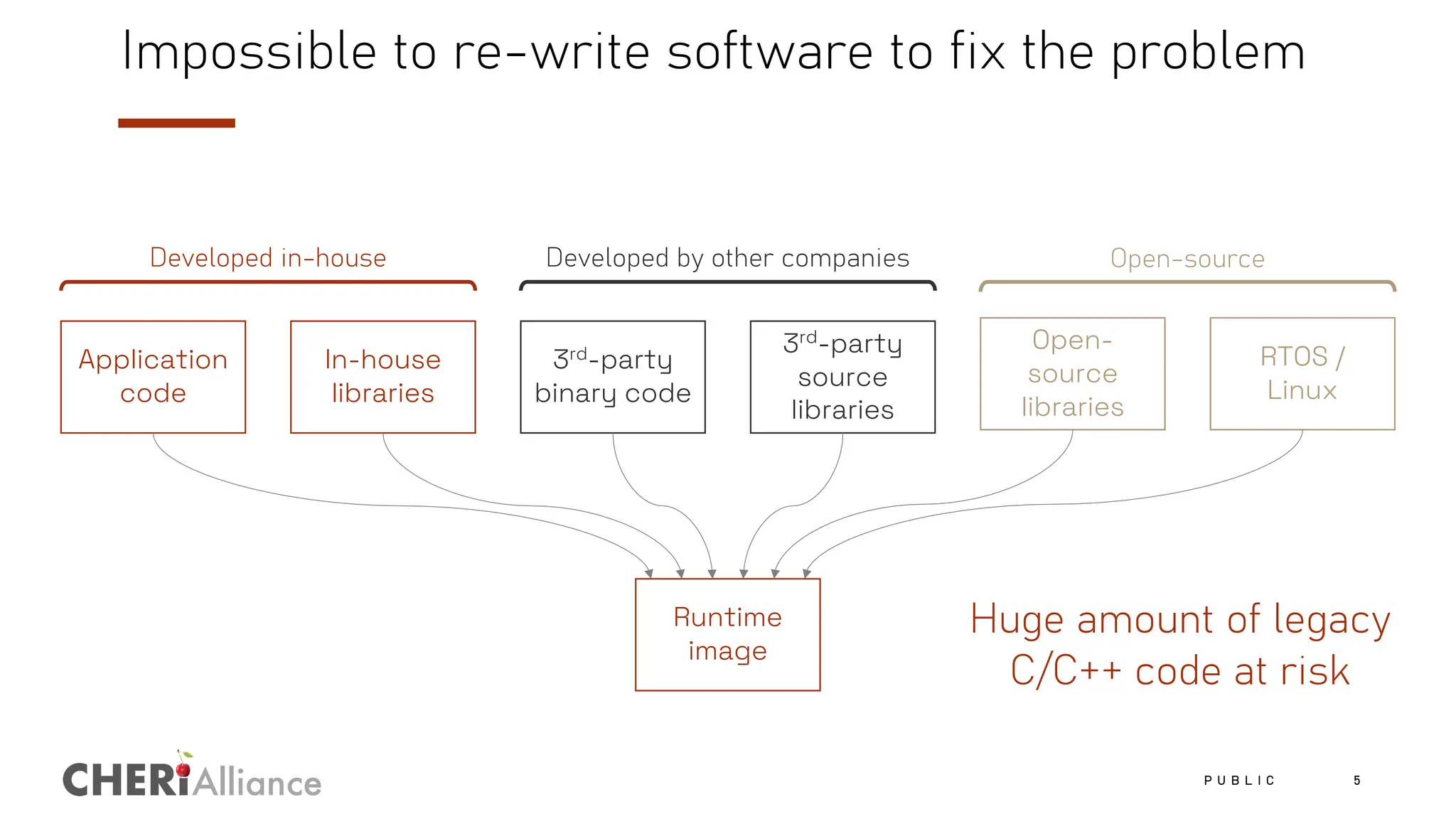
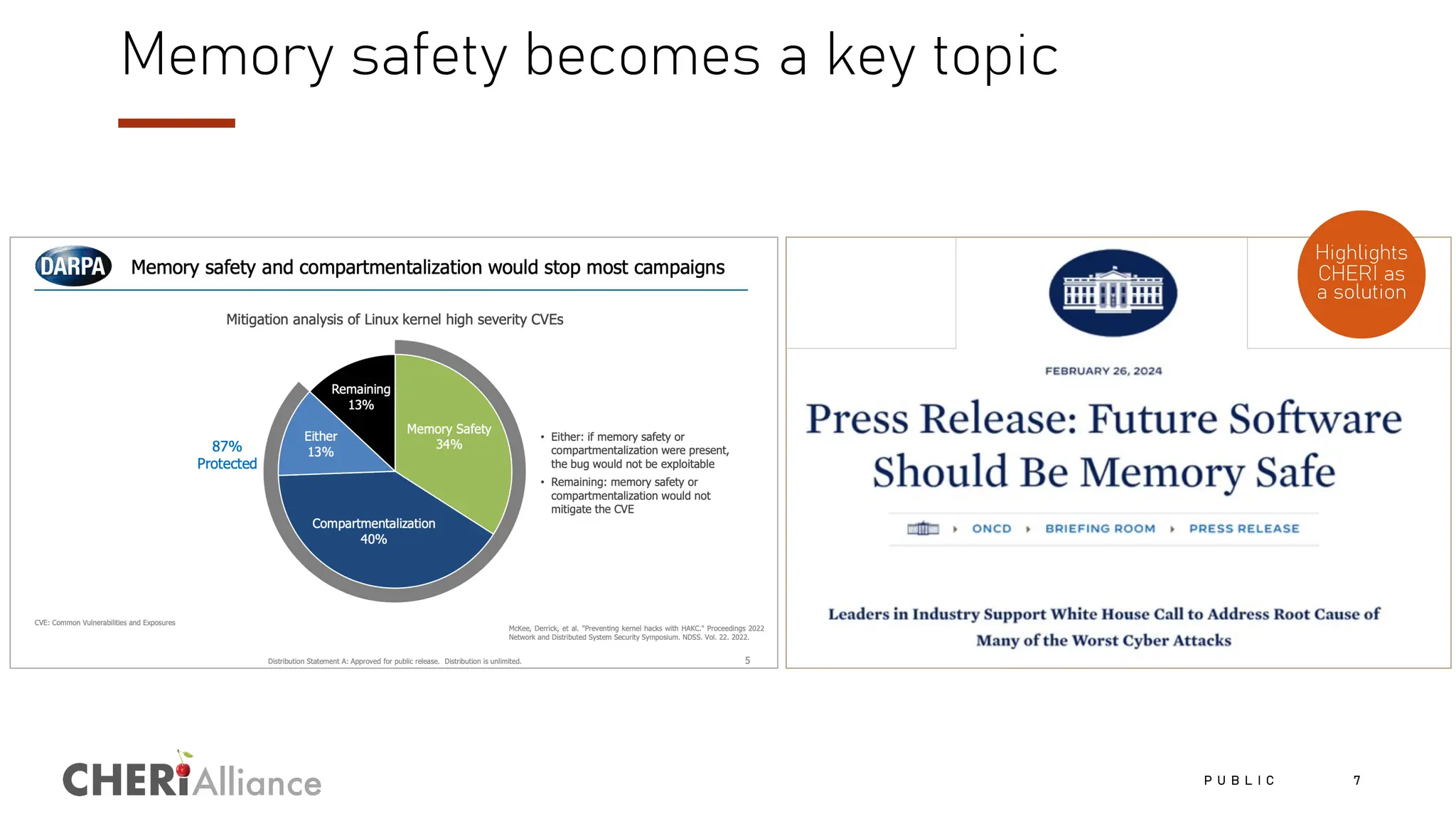
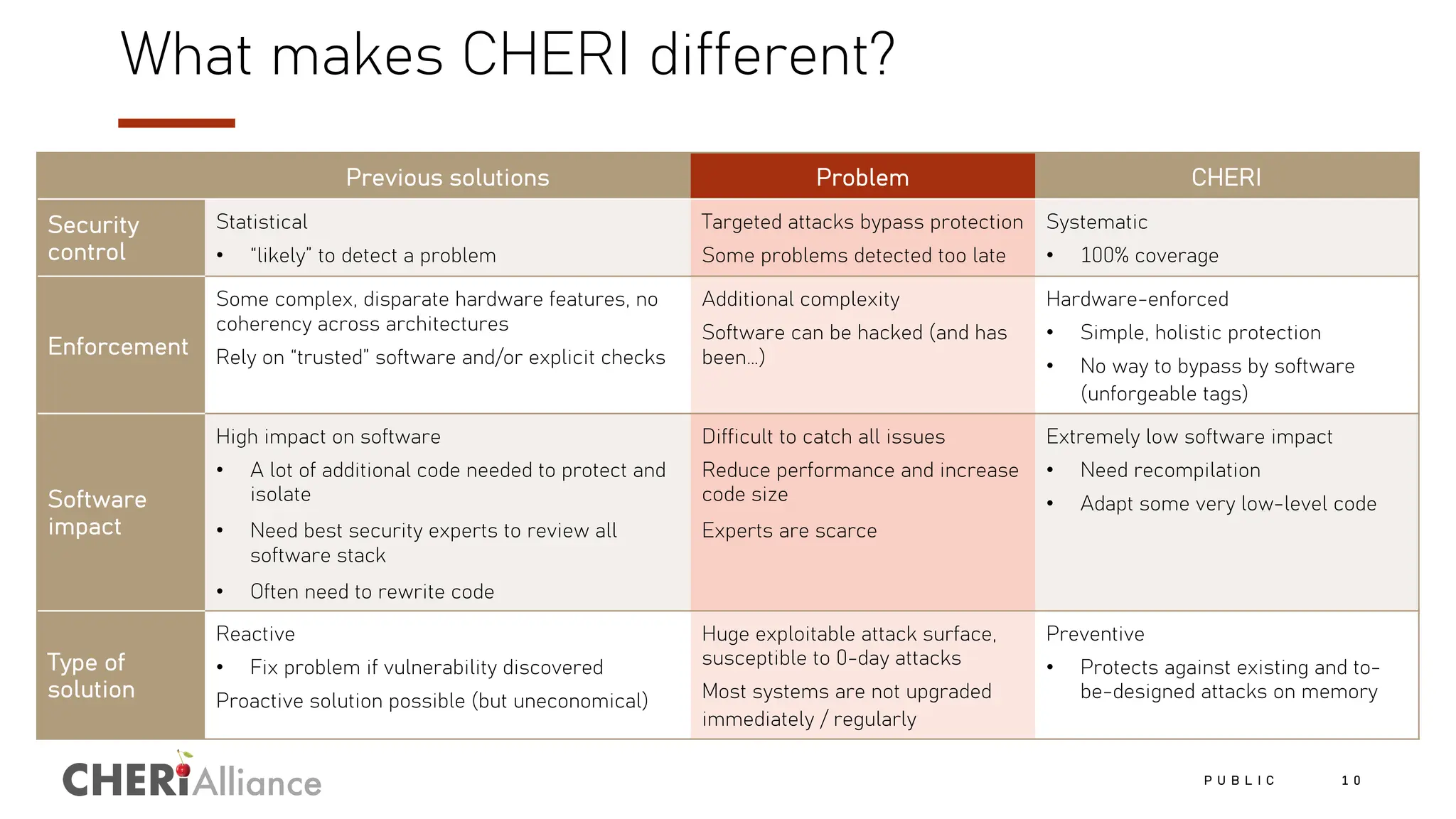
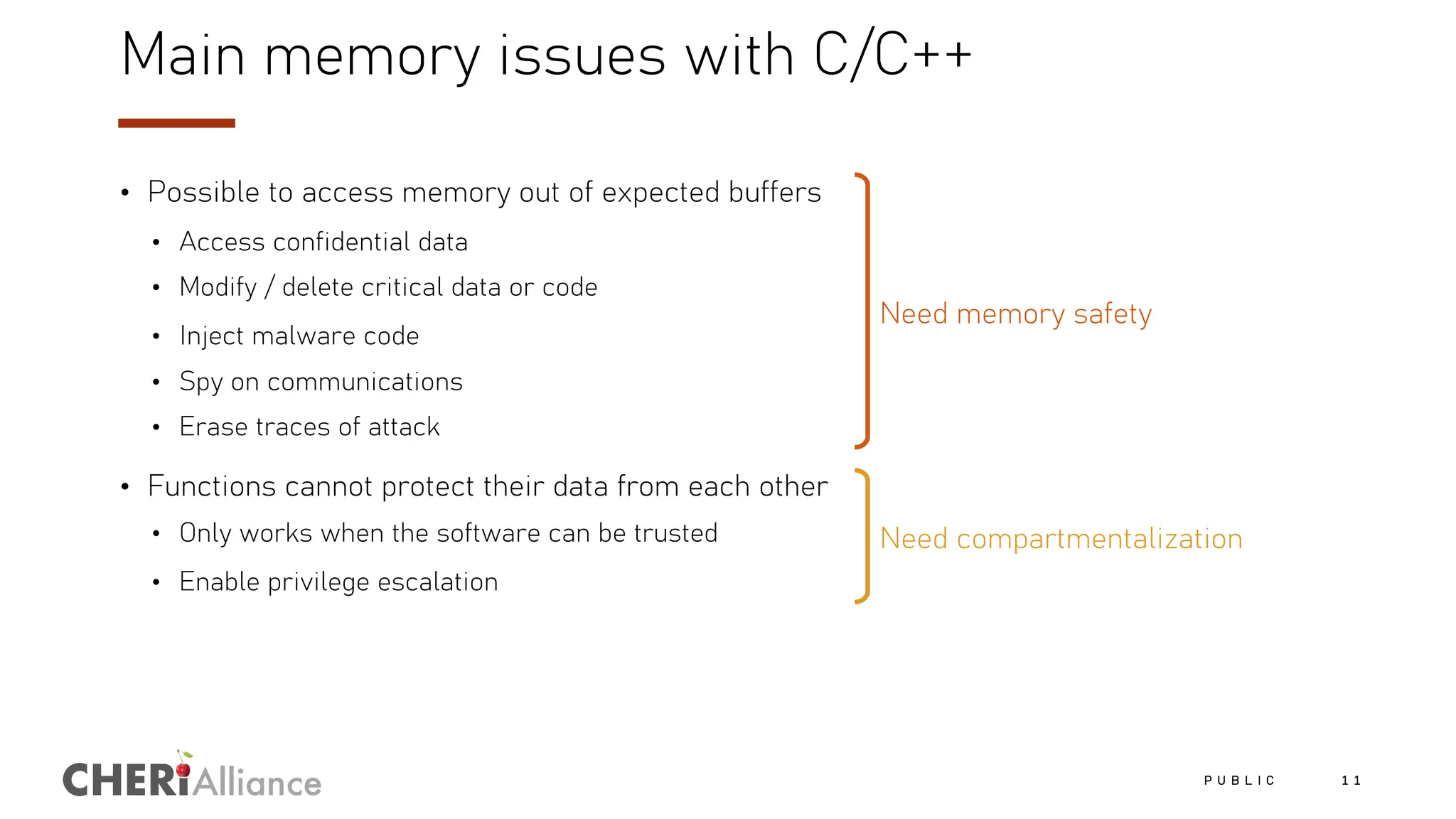
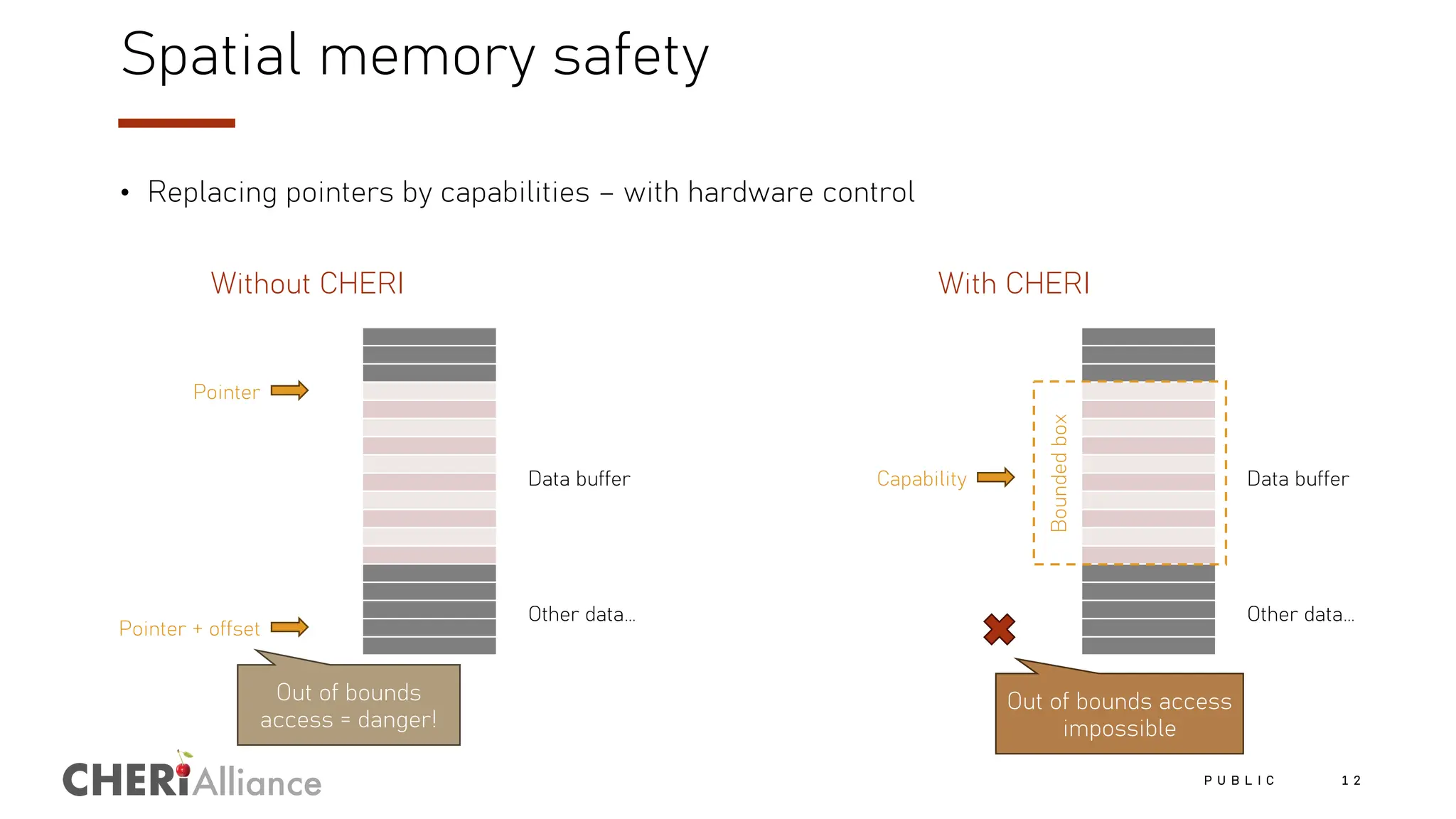
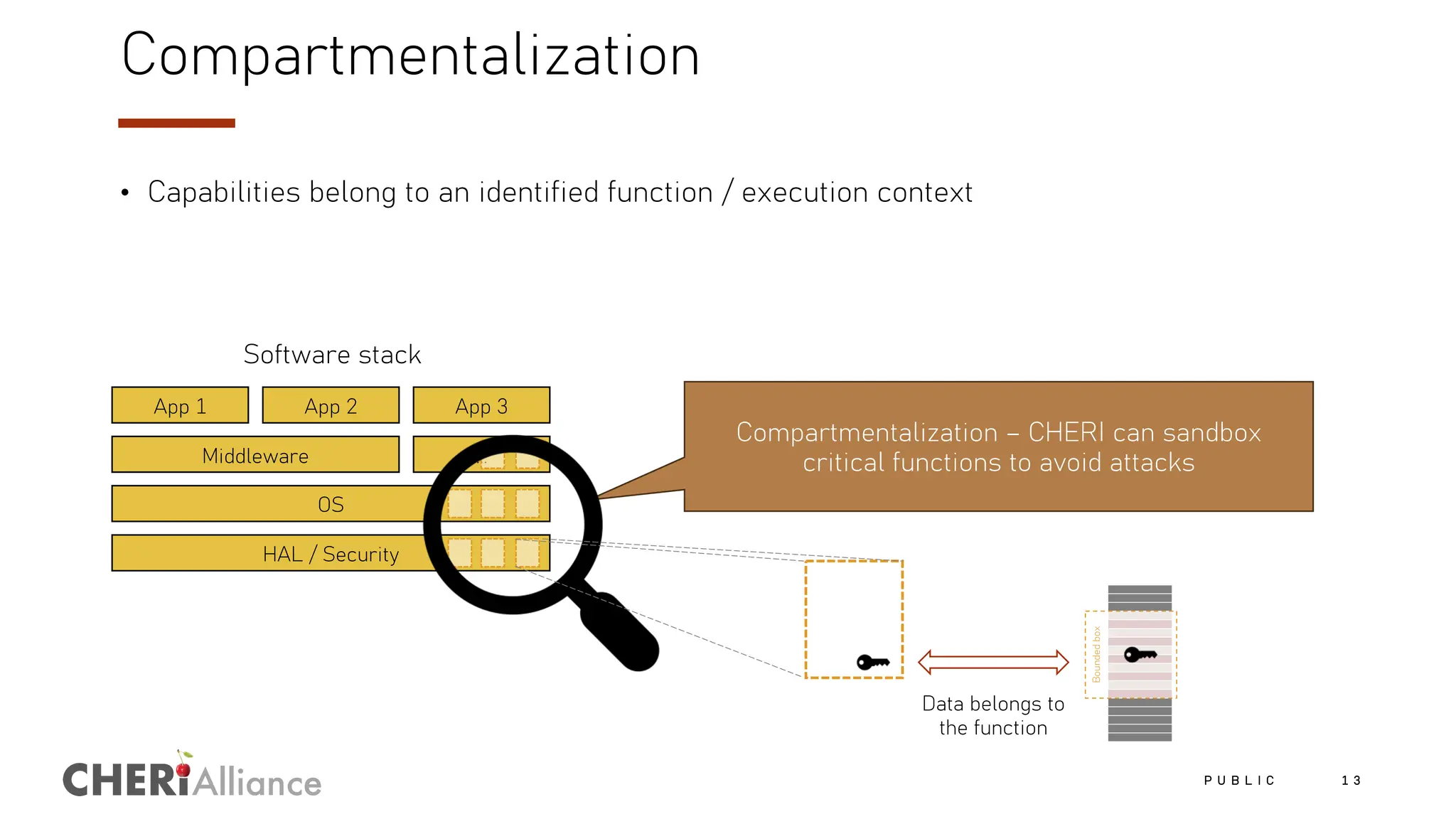
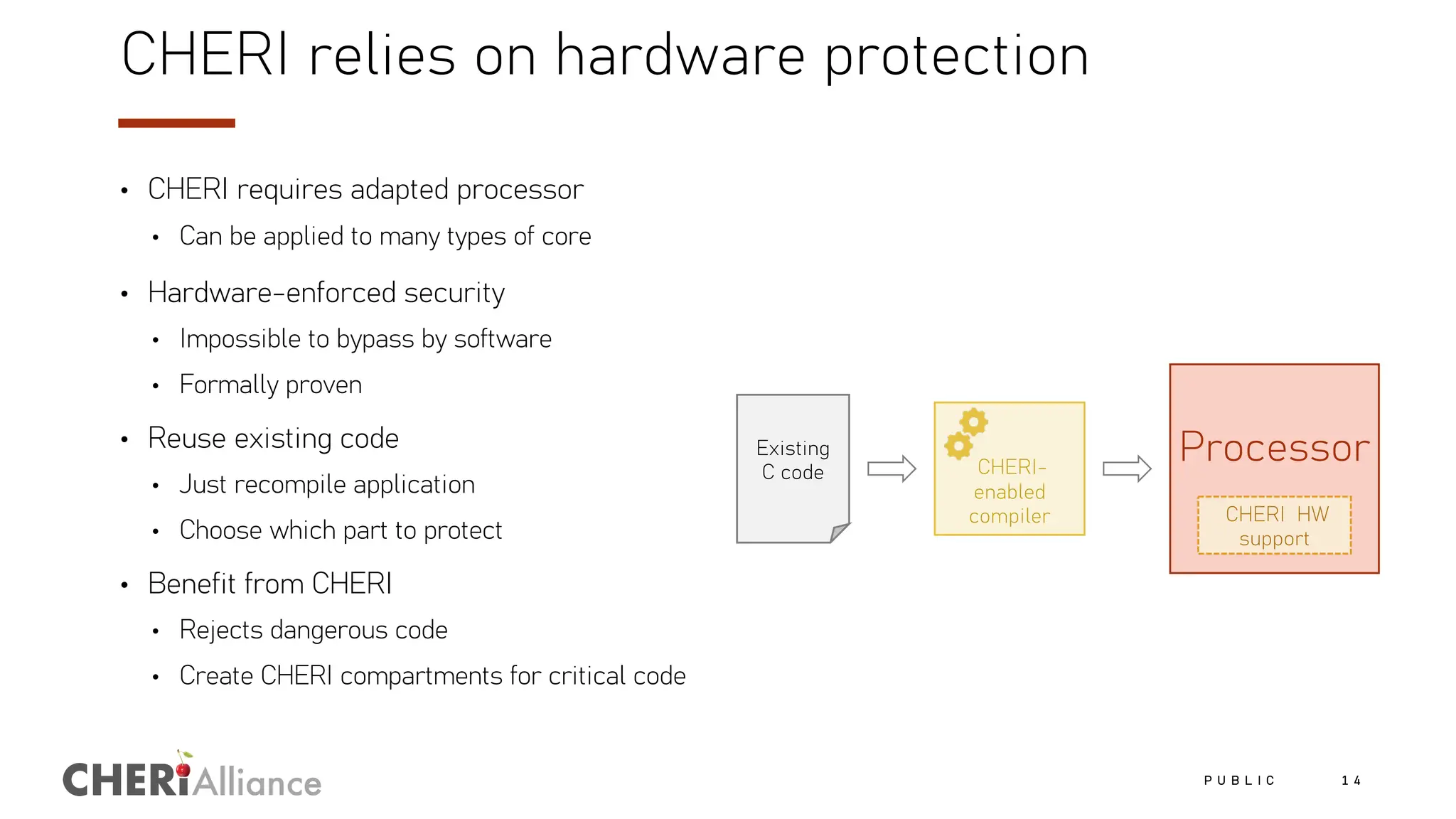
The document discusses the increasing costs and risks associated with cybersecurity vulnerabilities, highlighting the limitations of current memory protection strategies. It introduces CHERI technology as a solution that utilizes hardware-enforced fine-grained memory protection to drastically improve system security. CHERI enables safe compartmentalization, requiring minimal software changes while preventing attacks and ensuring high performance.